With Proton Mail version 3.14 we introduce PGP support, which includes import of PGP keys into Proton Contacts for encrypted communication with external PGP users, address verification with trusted keys, and several other improvements.
PGP Sending
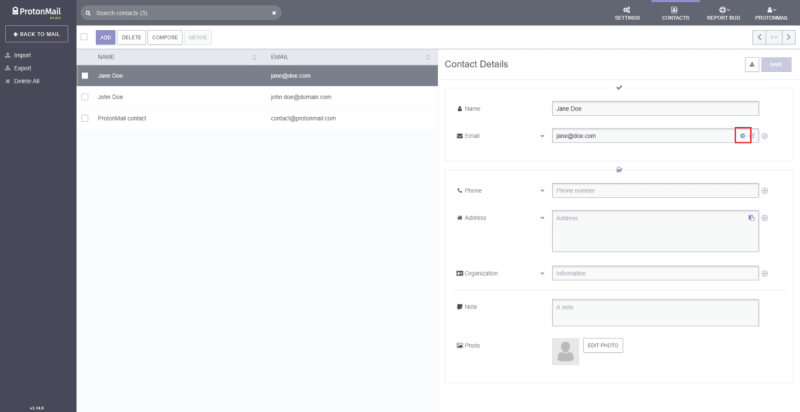
All Proton Mail users can now associate public keys with individual addresses in their contacts to enable encrypted communication with addresses that use other PGP services. For this reason, we have added an Advanced Settings button next to each address as shown in the image below:
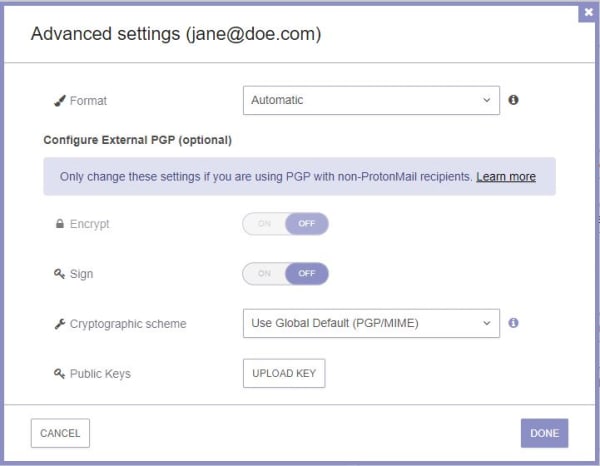
This opens a new modal with settings that can be personalized for each address individually:
Address verification
Proton Mail also allows you to trust public keys for each contact in order to enable address verification. Using trusted keys, a user can ensure that specific keys are used to encrypt the message for each contact. Because the contacts are signed, the server cannot tamper with these keys. (new window)
(new window)
Manage address keys
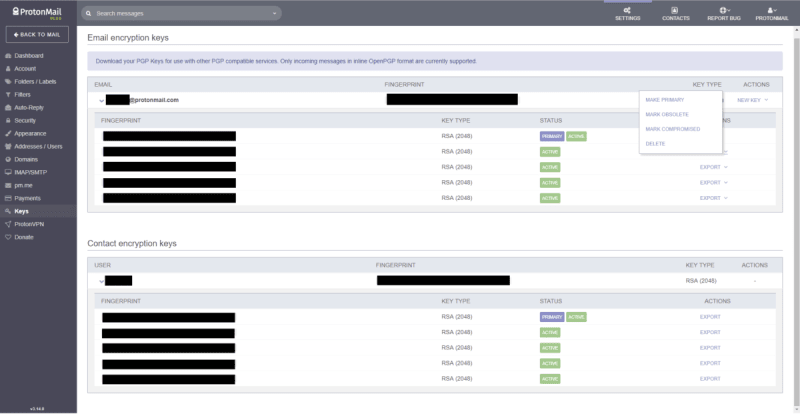
Previously, Proton Mail only provided the option to export your existing public keys. With Proton Mail 3.14, it is now possible to export both public and private keys for addresses, to generate new keys, to mark existing ones as obsolete or compromised, or to delete them.
Improved session management
We have also added a new feature for managing your active sessions. In the Security tab in Settings (on the web version), there is now a Session Management section which shows the active sessions for the account. Here you can see which client was used to log in on the account and when. Individual sessions can be revoked, which will forcibly log out that session:
Option for reporting phishing messages
We are always working to improve our user experience by making sure the messages you receive are legitimate. However, there are cases when malicious messages do end up in our users’ mailboxes. For this reason we have added a new warning and a new report system for potential phishing messages. If a message is detected as a potential phishing attempt, a red banner is displayed, asking users to be cautious. Even if this banner does not show, but a message appears to be a phishing attempt, you can report it under the More menu with the new “Report phishing” option.
New modal for expiring messages
The latest version of Proton Mail also brings an improvement to expiring messages(new window). If an expiration time is set, but it is not supported by some of the recipients, we display a new modal that lists required actions to enable expiration for all recipients. It is also possible to send the message without expiration.
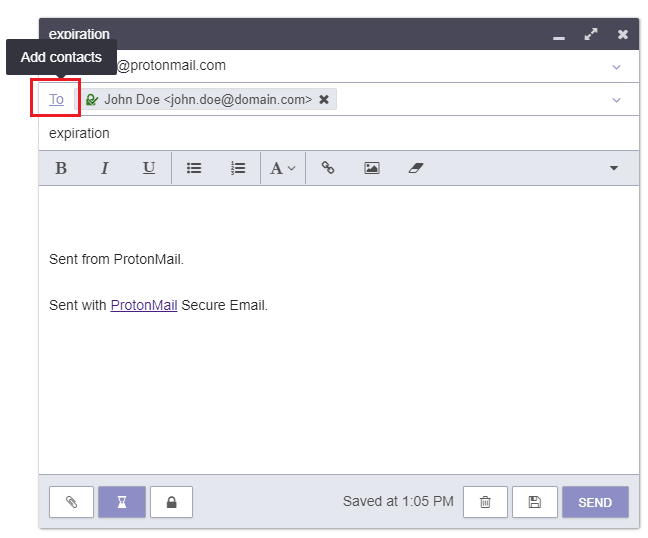
Add multiple recipients from the composer
For easier use, we have added another feature enabling users to quickly add multiple recipients right from the composer. To do this, simply click on the “To”, “CC”, or “BCC” text in front of each corresponding field. This opens a modal with a list of contact, which makes it possible to search and select multiple addresses and add them to the respective fields.
Detect nonexistent Proton Mail addresses
Another improvement to the composer is the detection of nonexistent Proton Mail addresses. In this case, the nonexistent address will be marked with a red rectangle as shown in the image below.
Option to remove a contact if you mark a message as spam
Messages from addresses saved as a contact are always delivered in the Inbox if no other custom filters(new window) are set up. This may cause spam messages(new window) to arrive in the Inbox if a contact’s account has been compromised or if the spamming address has been saved by mistake.
For this reason, it is now possible to mark a message as spam and have the option to also remove the sender from the contacts list.
As always, your feedback is very welcomed and appreciated. Feel free to let us know your thoughts on Twitter(new window) or Reddit(new window). If you have found a bug, please let us know through the Report Bug feature.(new window)
We wish you a productive day!
Sign up and get a free secure email account from Proton Mail.
We also provide a free VPN service(new window) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan or donate. Thank you for your support!