If you’ve ever gotten a suspicious text that looked like it was from your cell phone provider, bank, or postal service — but it wasn’t — you’ve probably been the target of a smishing attack.
What does smishing mean?
A portmanteau of “phishing” and “SMS”, smishing is a social engineering attack. In both phishing and smishing attacks, scammers pretend to be someone else, usually a company or service provider, to trick people or businesses into sharing sensitive information, downloading malware, or even sending money.
According to the World Economic Forum’s 2025 Global Security Outlook report(new window), 72% of respondents surveyed reported cybercrime like smishing as a business threat. Additionally, cybercrime like smishing and phishing grew in both frequency and complexity in 2024, posing a threat to businesses worldwide, affecting airlines, banks, broadcasters, healthcare providers, retail payment systems, ATMs, supply chains, and more.
Examples of smishing attacks and how to spot them
Virtually anyone with a smartphone is at risk of smishing, meaning it’s important to know how to spot it so you don’t fall victim to a smishing attack.
Smishing is carried out using SMS or text messages, and the scammer typically impersonates another entity to trick victims into clicking on fake links, calling a fraudulent number, or replying to a text that will lead to mining for your personal details.
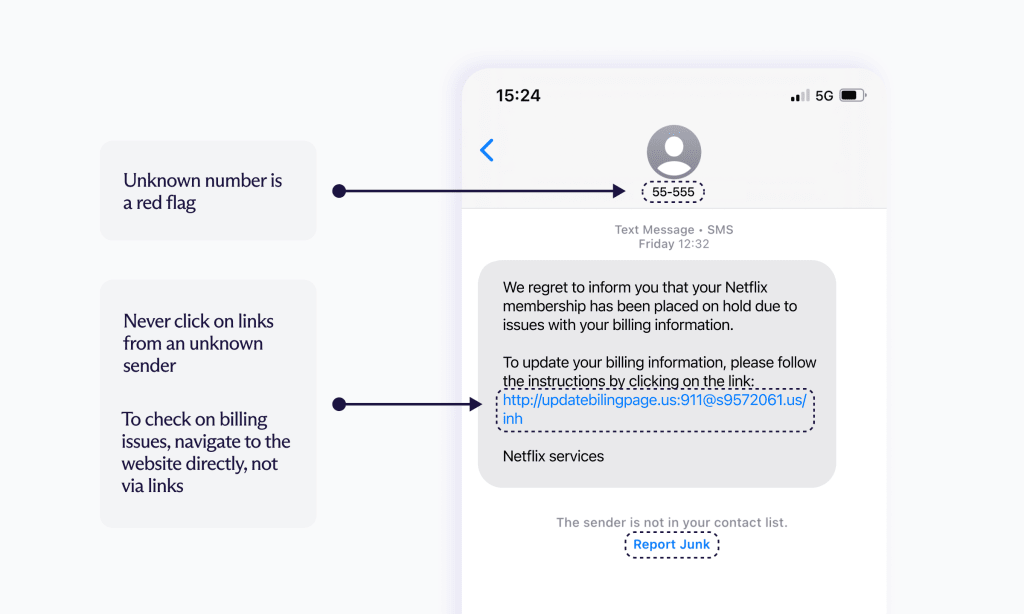
You’ll be less likely to fall for a smishing attack once you familiarize yourself with the following common approaches:
- Impersonate your bank: Attackers send a text pretending to be your bank alerting you to a fraudulent charge, which includes a nefarious link that may ask for your account, routing, or PIN numbers, allowing criminals access to your bank accounts.
- Impersonate a shipping company: Attackers impersonate the postal service, UPS, or another shipping service with an SMS notice about a package that couldn’t be delivered. The text will often include a fake phone number to call or a link that leads to a webpage asking the victim to enter their personal information to retrieve their package.
- Pose as the government: Scammers posing as government entities like the IRS or Department of Transportation will ask you for your Social Security number or other sensitive details. These smishing scams often attempt to scare the victim by tricking them into thinking they owe the government money.
- Impersonate a friend: If the scammer has access to your personal details, like what can be found on your social media accounts, they could impersonate a friend and pretend to be locked out of their account or ask you for money.
- Pretend to message a wrong number: Some scammers will purposely send you a message that’s clearly meant for someone else. The objective is to keep the conversation going and a serendipitous “friendship”. As time passes, they’ll ask more and more personal questions or try to build your trust so they can request money.
How can you stay safe from a smishing attack?
SMS apps often have filters that can help prevent smishing attacks from reaching you. But some will inevitably get through. You should treat all incoming messages from numbers not in your contacts with suspicion.
Follow these tips:
- If a text message or SMS comes from a number you don’t recognize, pause and don’t respond immediately.
- Don’t click any links sent from someone you don’t know.
- Check phone numbers and SMS phrasing with an online search. You may find that the text you received follows a common scammers’ template.
- Don’t engage. If you suspect someone is trying to steal your data or money, you might feel inclined to respond aggressively. Any level of engagement signals to the scammer that your phone number is active, which might lead them to attempt another smishing attack later.
- Block unknown numbers that seem suspicious or ask for personal information.
- Set social media profiles to private so scammers can’t mine your profile and friends for information about you.
- In the US, the US General Services Administration offers a guide(new window) to help you report the smishing attempts to the correct organization. In the EU, Europol provides a helpful directory(new window) showing who to contact depending on where you live.
- If the text is coming from a business or professional entity, like your bank, check the phone number on the company’s website to confirm if the message is real.
You can also protect yourself from smishing with Proton Pass. Attackers often send messages using familiar-looking URLs, tricking victims into thinking they are on an official website. For example, if you use PayPal, they might send a link to pay-pal.com. By only offering to fill in login credentials for known URLs, Proton Pass won’t ever offer to autofill your credentials on a fake website, so you’ll never hand over your login details or sensitive data by accident (but be aware some phishing attacks now use legitimate domains).
Proton Pass helps you defend against more traditional phishing attacks too. You can use hide-my-email aliases to protect your true email address and segment who has what information. If you know that you used a specific alias to sign up for a newsletter but then get an email to that alias from another organization, that’s a clear indicator of a phishing attempt.
Text with caution, not fear
Now that you’re familiar with different kinds of smishing attempts, you can implement steps to protect yourself from smishing attacks. Like phishing attacks, the scammer wants to fool their victim or manipulate their emotions so they share personal information or money. You can still use SMS safely — you just need to exercise caution, especially if you receive an unexpected or suspicious text.
Protect your data with Proton
If you’re concerned about your cybersecurity, Proton offers a number of protections via our suite of advanced, end-to-end encrypted products. More than 50,000 businesses, including some of the world’s largest public and private organizations, trust Proton’s services, like Proton Mail and Proton Pass, with their sensitive information. When you sign up for Proton, you’re not just protecting your data — you’re joining a movement that strives for a better internet where privacy is the default for everyone.






