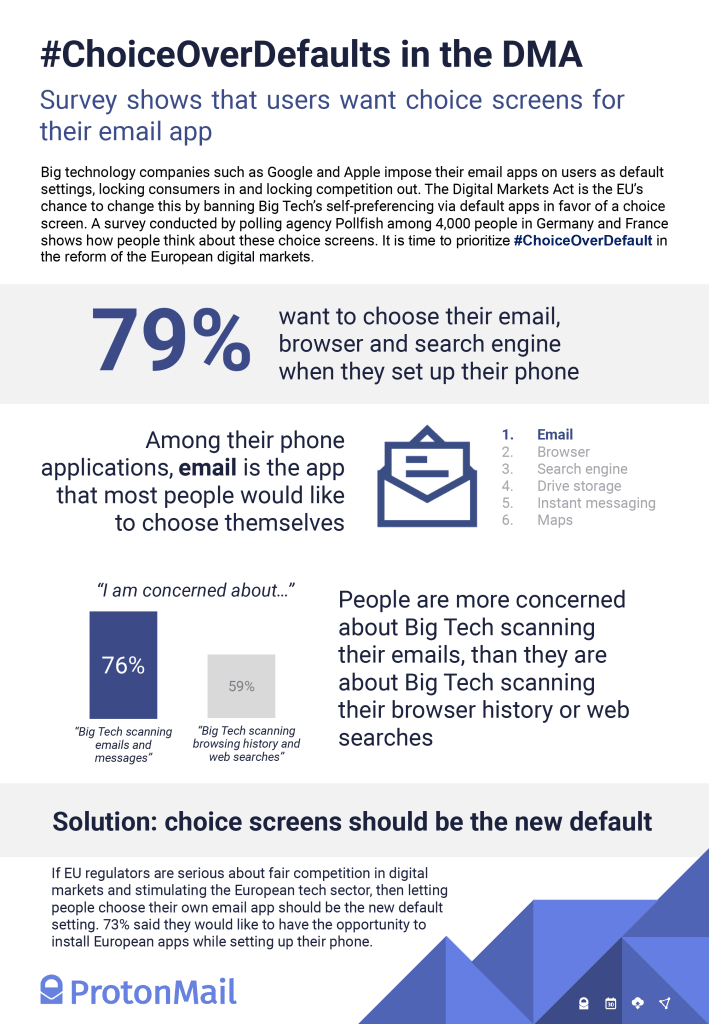
The Digital Markets Act (DMA) is the EU’s chance to ban Big Tech’s self-preferencing via default apps in favor of a choice screen when setting up a new device. By letting you choose the core apps such as email on your device, the amendments on defaults in the DMA can stop Big Tech from locking in consumers and locking out competition.
In collaboration with Pollfish, we surveyed 4,000 people in Germany and France. The results showed that people overwhelmingly want choice when it comes to deciding which apps they use on their phone.
 (nytt fönster)
(nytt fönster)When presented with the choice, people choose privacy. Adopting these amendments to the DMA and making choice the new default is another step towards a more private internet for everyone.
