Sharing pictures online can be joyful, nostalgic, and a beautiful way to stay connected with loved ones. But family photos are different. They’re deeply personal records of everyday life, milestones, and the people closest to us.
When you share a family photo album, you’re not just posting your moments online but may be exposing your children, parents, and grandparents to the internet, too. And not everyone is comfortable with that level of visibility — especially young children, who can’t give informed consent and may not fully understand the long-term implications of having their lives documented online.
In this guide, you’ll learn how to share family photos privately, stay in control of who sees what, and understand the privacy risks of popular photo sharing platforms — so you can make informed choices for your family. You’ll also see how Proton Drive is built to protect your memories, not exploit them.
- Why privacy matters when sharing family photos
- How to share family photo albums safely
- The risks of using popular tools to share family photos
- Keep family memories protected with Proton Drive
Why privacy matters when sharing family photos
When you upload family photos online, they become digital data that needs protection from hackers and other threats. Most platforms use encryption to scramble your data so others can’t read it: in transit (when photos are being uploaded or downloaded) and at rest (when they’re stored on the company’s servers).
However, few services use end-to-end encryption, which means the company itself can still access your photos — and sometimes share it with its partners. Without end-to-end encryption, your photos can be:
- Scanned and analyzed by AI systems to extract faces, locations, and objects
- Used to train facial recognition models — including government or corporate surveillance tools
- Shared with third parties, such as marketing platforms or data brokers
- Stored indefinitely(new window), even if you delete them
- Accessed in the event of a breach, leak, or internal misuse
- Repurposed without your knowledge, especially under vague or evolving privacy policies
The risks are even greater for children, who can’t consent to being included. So-called sharenting(new window) can have long-term consequences, such as creating permanent digital footprints and exposing kids to identity theft, facial recognition profiling, or worse(new window).
How to share family photo albums safely
Here’s how you can organize and share private family photos without exposing the people you love:
Choose a platform that keeps your photos private
Many platforms store your photos with standard encryption, but that still allows the company behind the service to access, scan, and share your content. If you’re sharing sensitive moments like family gatherings or pictures of your kids, that level of access shouldn’t be acceptable.
Proton Drive is secure, private cloud storage that uses end-to-end encryption to protect your photos and metadata, so no one can see your data — not even us. In the unlikely event of a data breach, your images would remain unreadable to anyone but you and the people you’ve chosen to share them with.
Organize photos before sharing
Before you start sending out dozens of pictures, take a moment to organize them. Here’s how you can do it right:
- Group by event, date, or theme: Whether it’s “Sunday picnic,” “Back to school,” or “Grandma’s Birthday,” clear organization helps viewers follow the narrative and find the moments they care about most.
- Cut the clutter: Rather than sharing everything, skip over blurred shots, photos with poor lighting, or near-duplicates.
- Make light edits if needed, like cropping out distractions or adjusting brightness. But avoid overdoing it and try to keep the style consistent across the album.
- Keep everyone in the loop. Before sharing, check that the people in your photos are comfortable with it — especially if the image is close-up or unflattering. A quick message asking for permission can help avoid misunderstandings later.
Proton Drive automatically detects the type of photos you upload — like RAW files, Live Photos, or Bursts — so you can quickly filter and view them. You can also mark favorites for easy access and organize everything into albums before sharing.
Gather more pictures from your family
Some of the best moments aren’t always captured by you, such as candid photos, behind-the-scenes shots, or phone snapshots. Getting photos from everyone involved in the event helps you build a more complete album for reunions, group trips, or birthdays where everyone has a different perspective.
Proton Drive lets you share family photo albums or folders with edit access, allowing recipients to upload their own pictures.
Decide who you want to share with
Not every photo is meant for everyone. Thinking ahead about who should see your family pictures helps you avoid oversharing and keeps things more personal. It also makes it easier to choose the right sharing method, like sending a private album to close relatives or selecting just a few photos for a wider group.
With Proton Drive, you can organize your photos into multiple albums — and assign the same photo to more than one. That way, a single picture from a family trip can appear in both “Vacation Highlights” and “Grandma’s Favorites,” without duplicating files.
Control who gets access to each album
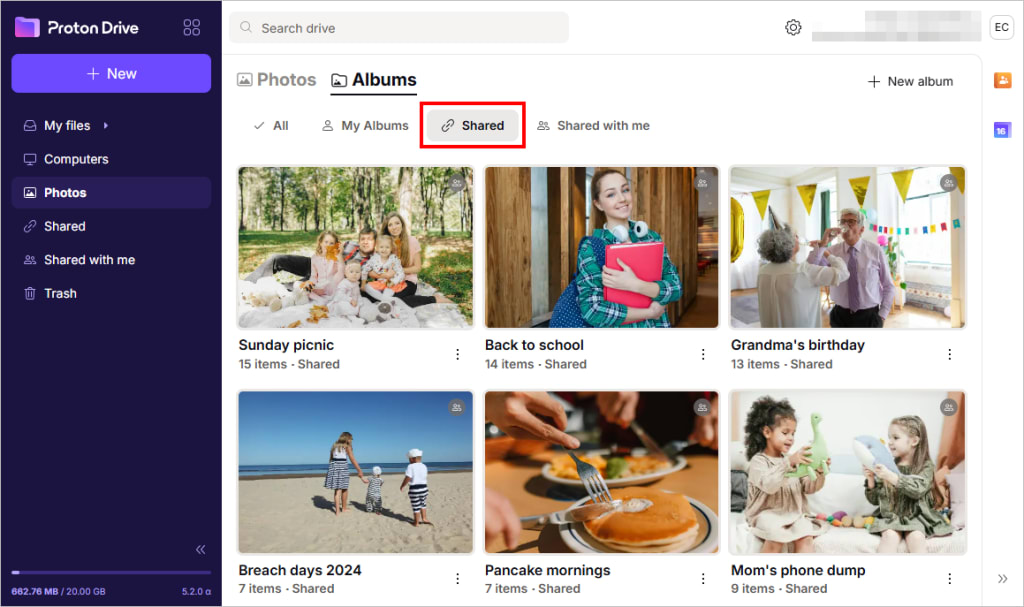
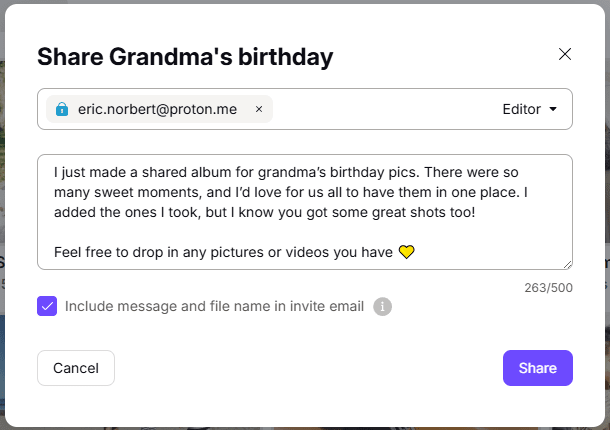
Even after you’ve decided who to share with, how you share matters just as much. Some platforms make it hard to keep track of shared links or to control who can view, download, or add to your photos — and once a link is out there, it’s often impossible to take it back.
With Proton Drive, you can share each album with specific people or groups via email — and easily manage everything afterward. All your shared photos and albums appear in one dedicated space, where you can update permissions or revoke access anytime.
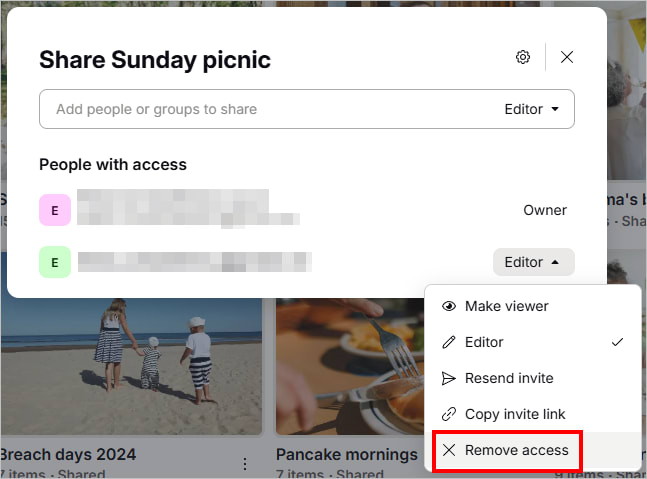
ou can also update albums over time, with all changes instantly visible to the people you’ve shared them with — which works well for growing collections like baby photos, family vacations, or ongoing events.
Already using Proton Drive?
The risks of using popular tools to share family photos
Here’s what to keep in mind before uploading your family memories through widely used photo sharing tools:
Google Photos
Google Photos provides smart organization, but its privacy protections fall short. Your photos are encrypted in transit and at rest, but not end-to-end. AI systems tag faces, locations, and objects, and it’s unclear whether your images are excluded from AI training.
Even if you pay for Google One, you’re buying cloud storage — not privacy. Plus, there’s no easy way to see or revoke shared links, and past incidents show that misinterpreted photos can lead to account loss without recourse.
iCloud Photos
Apple’s iCloud offers optional end-to-end encryption through Advanced Data Protection (ADP) for certain types of data, including photos, but this feature is turned off by default. Plus, enabling ADP only secures your photos if the people you share them with have ADP turned on too — if they don’t, Apple can still access the shared images.
Even when ADP is active, Apple retains access to certain metadata like file size, creation date, and how often a photo is viewed. And the company has already shown it’s willing to disable these protections under government pressure, as it did in the UK in 2025.
For families looking to share personal photos securely, iCloud may feel safe, but it doesn’t offer the kind of end-to-end privacy the ads imply, especially as Apple increasingly mirrors Google’s ad-driven business model. It’s also built for the Apple ecosystem — so if someone in your family uses Android or Windows, sharing becomes much more limited.
Dropbox
Dropbox is one of the oldest and most widely used cloud storage services, but it falls short on privacy. While it offers end-to-end encryption, that feature is reserved for business users on advanced plans — not families or individuals.
Without E2EE, files stored in Dropbox can still be accessed by the company, which collects a significant amount of personal data, including metadata, device info, and file activity. Even more concerning, Dropbox has a track record of security breaches and has openly shared user data with third parties and law enforcement, sometimes without a warrant.
Meta’s Facebook, Instagram, and WhatsApp
Meta’s platforms are designed to make photo sharing fast and social — but not necessarily private. By default, posts on Facebook and Instagram are public unless you adjust your settings. While private groups and follower-only modes offer some control, everything you upload still feeds Meta’s massive data machine(new window).
Internal documents and testimony from Meta engineers reveal that even the company itself doesn’t fully understand where all your data is stored or how it’s used. That includes data collected from posts, captions, photo locations, and even metadata from WhatsApp, which shares message timing, recipient info, and device data with Meta. Despite WhatsApp’s end-to-end encryption, Meta still knows who you’re sending to and when.
Flickr
Flickr was designed for open photo sharing and community building — and by default, your photos are visible to the public. While it does offer privacy settings(new window) like “friends,” “family,” or “private,” setting an album to “private” doesn’t mean it’s just for your eyes.
Flickr itself retains access, and past reports(new window) show the company has contacted users about content in their private albums. According to its privacy policy(new window), the platform also uses image recognition to scan, tag, and organize your photos, and shares your data with third parties.
Most concerning, images from Flickr — including personal family photos — were used without consent in the creation of the MegaFace facial recognition dataset(new window), later accessed by tech giants and government agencies.
Amazon Photos
While Amazon Photos advertises(new window) encryption that ensures only you and those you choose to share with can see your pictures, the reality is less private. Your photos are encrypted in transit and at rest but not end-to-end, so Amazon can still access them once they’re on its servers.
By default, Amazon uses facial and object recognition(new window) to scan your images and organize them into albums. Although you can turn off this feature, the company still reserves the right to use your file data to improve services or share with third parties.
Like other Amazon services, Photos also uses your personal data(new window) for personalized ads, though it’s unclear whether that includes photo content.
Keep family memories protected with Proton Drive
Sharing family photos shouldn’t mean handing them over to companies that treat them like data. Proton Drive is the safest way to share photos — your pictures stay fully under your control, protected by end-to-end encryption and Swiss privacy laws.
You can organize albums, share with specific people, and collect photos from others using any device through iOS, Android, macOS, Windows, and web apps — with automatic backups on mobile to make sure nothing gets lost.
Proton Drive is part of a secure ecosystem that doesn’t show ads, track you, or collect your data. All Proton apps are open source, independently audited for transparency, and backed by a community that believes privacy should be the default.
Start building your private family archive with 5 GB of free, encrypted cloud storage for 1,000 high-resolution photos — and share it with the people who matter.





