June 2022: This post has been updated to better reflect how Proton’s encrypted contacts manager works in 2022.
Today we’re launching a new contacts manager, the first one in the world that includes both zero access encryption and digital signature verification.
Starting with Version 3.12 of Proton Mail, we have rolled out a brand new version of Contacts for Proton Mail. The new Proton Mail Contacts was in development for over a year and is an essential next step in our broader security road map.
In addition to adding a much more powerful contacts functionality to Proton Mail, our new contacts manager provides the world’s first tool for securely managing your contacts.
What is an encrypted contacts manager?
Proton Mail’s contacts manager is not a stand-alone app. It is instead built into our other products (notably Proton Mail(nova janela) and Proton Calendar(nova janela)) so that you can easily access your contacts when performing a task. For example, when writing an email or inviting someone to an event.
The name and address fields are not encrypted (although they are digitally signed – see below). This is so that we can actually send and receive the emails. Everything else is fully end-to-end encrypted to ensure that only you can read the contact details.
Learn more about how encrypted email works
In our encrypted contacts manager, contact details protected by end-to-end encryption are shown with a lock icon when you edit a contact.
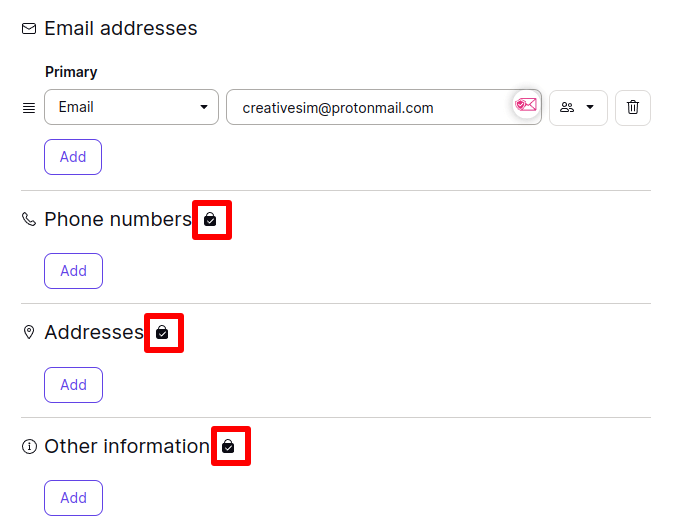
End-to-end encrypted contact fields brings many security benefits. For example, if you are a journalist with a confidential source, it is very important to protect the phone number or address of that source.
Using the notes field in contacts, you can also add other information about the contact that will be protected with end-to-end encryption.
In order to do email filtering, we do not encrypt email addresses – doing so also does not significantly improve privacy because as an email service, we necessarily must know who you are emailing in order to deliver the message.
Digitally Signed Contacts
The new Proton Contacts does more than just protect contact data fields with end-to-end encryption. We also use digital signatures to verify the integrity of contacts data. Digital signatures are used for all contact fields, including the email address itself.
The concept of digital signatures is technically complex. But in simple terms, what digital signature verification does is provide a cryptographic guarantee that nobody (not even Proton Mail) has tampered with your contacts. Thus, you can be absolutely sure that the contacts data is precisely what you entered.
Learn more about digital signatures
This is a big security benefit for many reasons. For example, if an attacker wanted to intercept the communications between you and a sensitive contact, one way to do it could be to secretly change the email address or phone number you have saved for that contact, For example, changing john.smith@proton.me to john.snnith@proton.me, which might escape your notice.
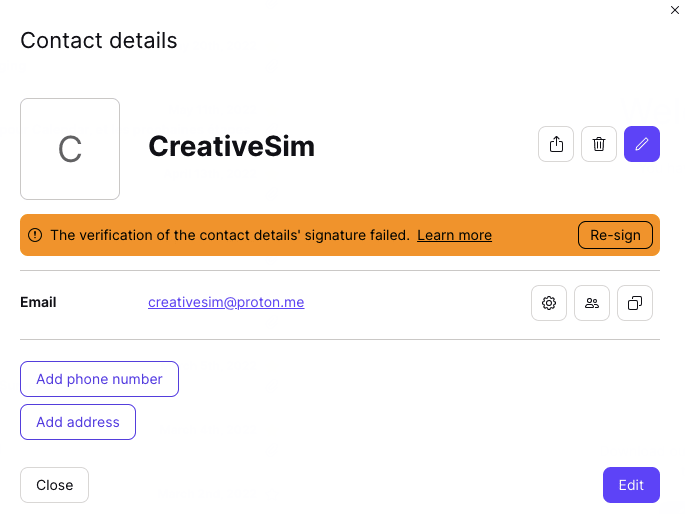
However, because Proton Contacts are now digitally signed, any attempt to tamper with your contacts will result in the following error message being displayed.
How does it work?
For those who are technically inclined, this section discusses how Proton Mail’s encrypted contacts manager is implemented. For each email account, we generate a new private and public key pair that is used exclusively for encrypting contacts.
The private key is generated on the client side and encrypted using a derivative of your password which we don’t have access to, meaning that we can never access your contacts private key.
Encrypted contact fields are encrypted with your contacts public key and therefore can only be decrypted with the corresponding private key which only you have access to.
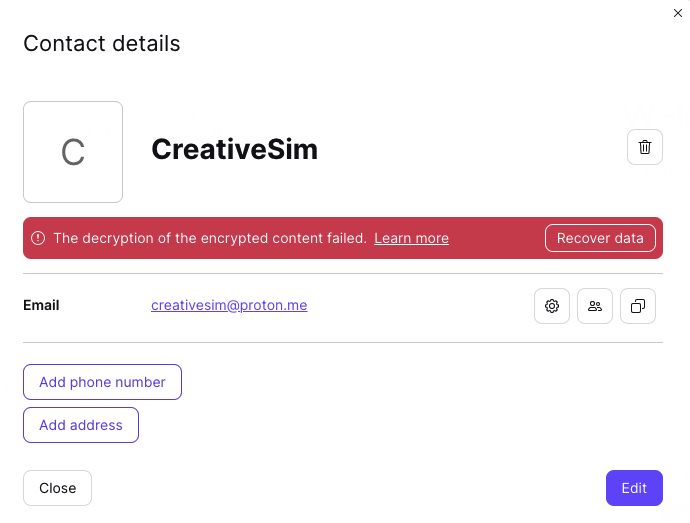
If you change your account password, Proton will not be able to decrypt your contact details. You can, however, reactivate your encryption keys to gain access to your contacts
Digital signing is done by signing the data with your private key which allows the authenticity of the data to be conclusively verified on each subsequent data access. For full implementation details, it is possible to check out our source code(nova janela).
Always improving
The immediate security benefits of encrypted and digitally signed contacts are quite obvious. However, since its release in 2018, we have worked hard to improve our contacts manager with new features and security enhancements.
For example, our contacts manager can now store public keys, which is an essential component for both sending PGP messages to people who don’t use Proton Mail; verifying the integrity of the keys themselves, and verifying the authenticity of received messages via digital signatures.
We have also rolled out the encrypted contacts manager to our iOS and Android encrypted email apps, where you can easily import your phone contacts into Proton Mail. Please note that doing this gives Proton access to your contact names and email addresses.
On our road map is contact synchronization between your mobile device and the rest of the Proton ecosystem.
You can read the encrypted contacts press release here.
You can get a free secure email account from Proton Mail here(nova janela).
We also provide a free VPN service(nova janela) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan. Thank you for your support!






