DMARC is an email authentication method that verifies a message came from a legitimate sender. Learn how it works and why you need it to improve the deliverability of your emails and protect your domain.
Building on the DKIM and SPF authentication protocols, DMARC helps prevent your email domain from being forged (spoofed) and used for spam or phishing attacks.
We explain DMARC, how it works together with SPF and DKIM, and why you need it to protect your domain and make sure your emails are delivered.
What is DMARC?
What is DMARC used for?
How DMARC works with SPF and DKIM
How does DMARC work?
What is a DMARC policy?
What is a DMARC record?
Why use DMARC?
Protect your domain
Improve email deliverability
Troubleshoot emails
Easily set up DMARC with Proton Mail
What is DMARC?
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an open standard for email authentication that helps to prevent fraudsters from forging (spoofing) your domain.
Spammers and scammers can forge the From address of emails so they appear to come from a sender at your domain (for example, name@yourdomain.com).
DMARC checks that the From field matches the domain in DKIM and SPF authentication checks, helping internet service providers (ISPs) and email providers spot spoofed addresses. DMARC also tells email servers how to handle messages that fail these checks and allows recipients to receive reports on emails that fail authentication.
What is DMARC used for?
Email providers and ISPs use DMARC with SPF and DKIM to identify spoofed addresses, helping them spot and prevent spam and phishing emails. For example, at Proton Mail, DMARC is one tool we use for anti-abuse and account security.
Email platforms also use DMARC to monitor and troubleshoot emails. With DMARC, you can request reports on messages that have failed SPF and DKIM to help you identify why emails aren’t being delivered. DMARC reports also show who is sending email from your domain to alert you to potential fraudsters abusing your domain.
How DMARC works with SPF and DKIM
DMARC works in conjunction with SPF and DKIM to verify that the sender of an email is genuine. Here’s how the three authentication methods work together:
- SPF (Sender Policy Framework) verifies that an email has been sent from an IP address authorized to send emails from the sender’s domain.
- DKIM (DomainKeys Identified Mail) cryptographically verifies that the sender’s address and message contents haven’t been changed in transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance) ensures that the domain in DKIM and SPF checks matches the sender’s domain in the From field. It also specifies how email servers should handle a message that fails both DKIM and SPF — accept, reject, or mark it as spam.
Although DMARC only requires either SPF or DKIM to work, we strongly recommend that everyone who uses a custom domain set up both SPF and DKIM with DMARC to ensure your emails are properly delivered.
Learn how to set up SPF, DKIM, and DMARC with Proton Mail
How does DMARC work?
DMARC works with SPF and/or DKIM to authenticate an email’s sender (From field) and tells mail servers how to route messages that fail both those checks. Here’s how it works:
After setting up SPF and/or DKIM, you must publish a DMARC record, which contains a DMARC policy. The DMARC policy tells email servers what action to take with messages that fail both SPF and DKIM checks. There are three options:
| DMARC policy | Server action |
|---|---|
| None | Take no action — the message continues to the recipient’s inbox. |
| Quarantine | Move the message to spam or another folder instead of the inbox. |
| Reject | Block the message — the message isn’t delivered |
Whatever DMARC policy you set, email services may adapt their actions to optimize deliverability. For example, since there are still cases where legitimate emails fail DMARC, at Proton Mail, we don’t block messages with a “reject” DMARC policy but send them to the spam folder with a warning to the user.
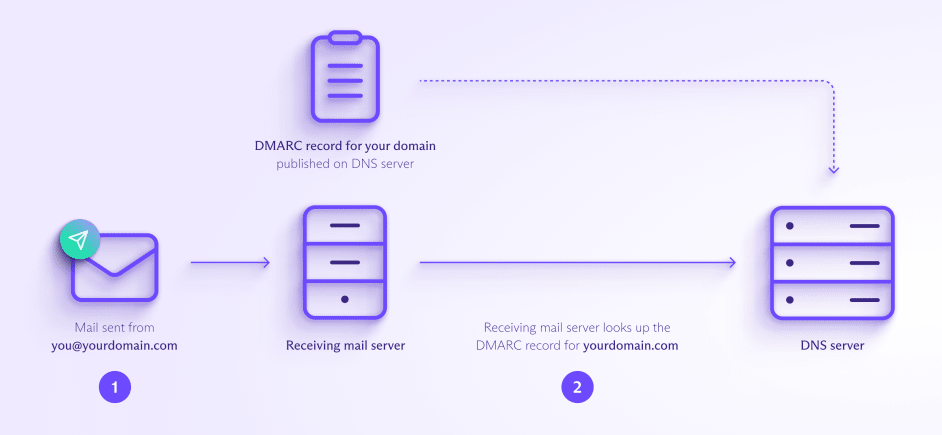
Once you’ve published your DMARC record, you’re ready to send emails with DMARC as follows:
- You send an email, for example, from the address you@yourdomain.com.
- The receiving mail server looks up your domain’s DMARC policy in your DMARC record on the DNS server.
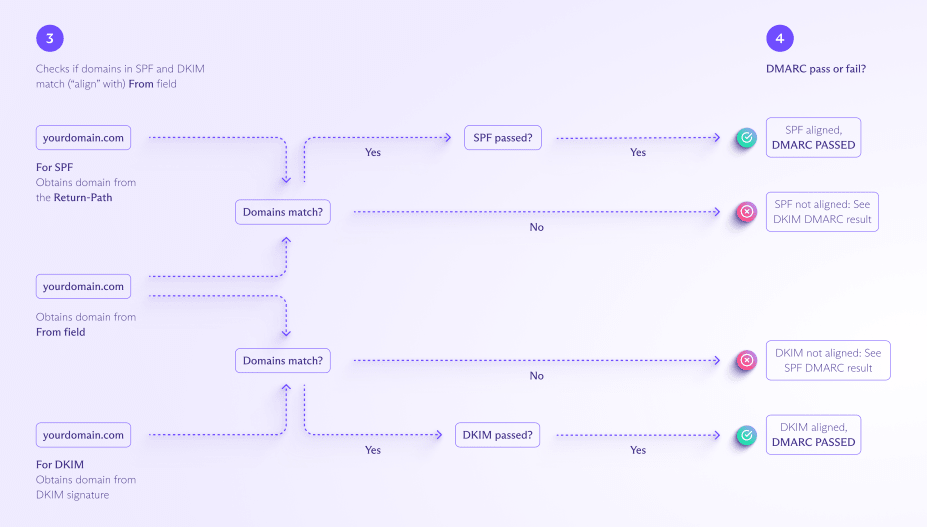
- Following the DMARC policy, the receiving mail server does the DMARC, SPF, and DKIM authentication tests, checking that the domain in the message’s From field is “aligned with” (matches) the domain in SPF and DKIM.
- For SPF, the From field should align with the domain in the Return-Path field in the email header.
- For DKIM, the From field should align with the domain (d) in the DKIM signature.
- If the message passes both the authentication and the alignment test for either SPF or DKIM, then it passes DMARC. If it fails either the authentication or the alignment test for both SPF and DKIM, it fails DMARC.
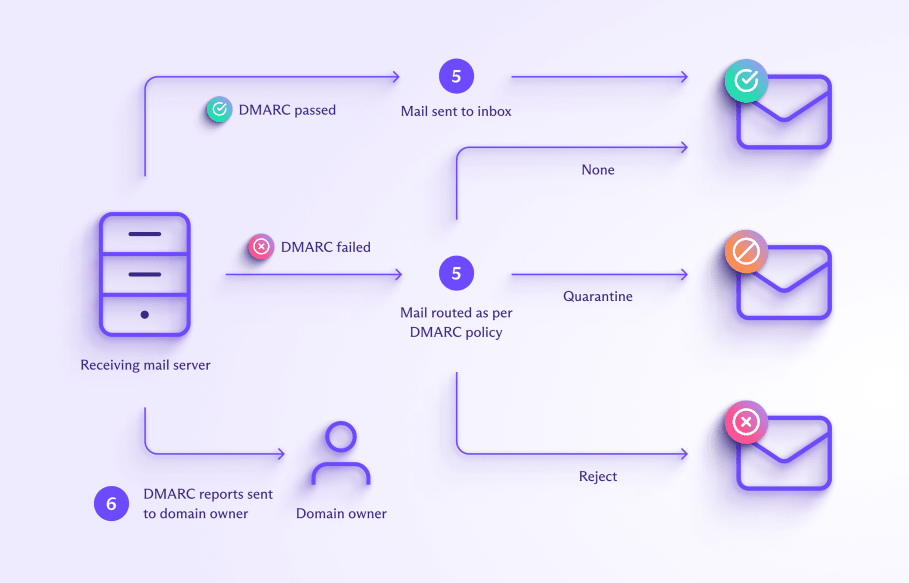
- When a message fails DMARC, the mail server routes it according to the DMARC policy (none/quarantine/reject).
- Mail servers receiving messages from your domain send regular emails with authentication results to you, the domain owner (assuming you’ve included a reporting address in your DMARC record and the mail server is set up to send DMARC reports).
What is a DMARC policy?
A DMARC policy enables a domain owner to specify what a receiving mail server should do with emails that fail DMARC, in other words, fail both SPF and DKIM.
There are three options for DMARC policies, which are indicated by the “p=” tag in a DMARC record:
- p=none: Take no action, so all messages that fail authentication will be delivered.
- p=quarantine: Send failed messages to the spam folder.
- p=reject: Block failed messages, so they won’t be delivered.
p=none may be useful when you have a new domain and want to check that your legitimate emails are being delivered. With p=none, all messages are delivered regardless of authentication, and you receive email reports that you can use to spot authentication issues.
However, once you’re confident your email is configured correctly, we recommend switching to p=quarantine, which sends failed messages to the spam folder.
If you think you’re likely to be the target of email spoofing, set p=reject. For example, sites like PayPal and eBay use p=reject because they’re targeted by spammers and scammers impersonating their domains.
What is a DMARC record?
A DMARC record is a type of DNS text record(nova janela) that tells receiving mail servers that a domain is protected by DMARC authentication. Typically, DMARC records include:
- A DMARC policy, which tells receiving mail servers what to do when an email fails SPF and DKIM authentication
- An optional email address where mail servers can send DMARC reports about the authentication of emails sent from that domain.
A DMARC record consists of a series of tags, like v=DMARC1, p=quarantine, etc.
DMARC record example
Here’s an example of a DMARC record with an explanation of what the tags mean below:
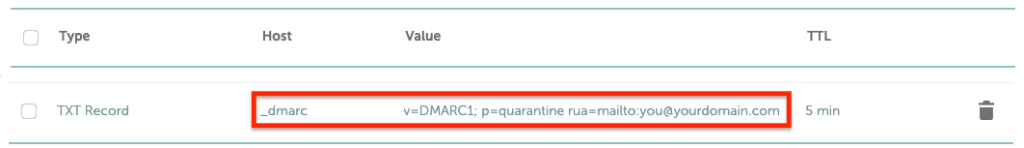

- v=DMARC1: The DMARC version number. Every DMARC record must begin with this tag.
- p=quarantine: The DMARC policy, which instructs the receiving mail server to send messages that fail DMARC to the spam folder. This value can also be p=none or p=reject (learn more about DMARC policies above).
- rua=you@yourdomain.com: Specifies the address to receive DMARC aggregate reports, which give you a statistical overview of all your domain’s email traffic. You can also use the tag ruf= (for example, ruf=you@yourdomain.com) to receive more detailed, forensic DMARC reports about the authentication status of your emails.
There are 11 different tags that can be added to a DMARC record, but only v and p are required.
Other common tags are adkim and aspf, which specify how strictly the domain in the From field must align with the domain in DKIM and SPF checks (see how DMARC works above for details). The value can be either “strict” (s), which requires an exact match, or “relaxed” (r), which permits subdomains.
For example, if you set the value adkim=s for your domain (yourdomain.com), only emails sent from @yourdomain.com will pass DMARC. But if you change this value to adkim=r, emails sent from subdomains, like @news.yourdomain.com or @info.yourdomain.com, will also pass.
If you want to maintain strict alignment and allow subdomains, you can simply add a separate DMARC record for each subdomain.
Why use DMARC?
If you have your own domain, we strongly recommend setting up DMARC, together with SPF and DKIM. Here’s why:
Protect your domain
DMARC authenticates the sender’s address in your emails, making it harder for fraudsters to impersonate your domain. So implementing DMARC helps prevent attackers from using your domain for spam or phishing attacks.
Improve email deliverability
Emails sent with DMARC look legitimate and can be easily verified. So implementing DMARC reduces the chances of your emails ending up in the spam folder. And the more you send authenticated emails, the more you build your domain’s sending reputation with email service providers over the long term.
Troubleshoot emails
With DMARC, you can receive regular reports letting you monitor the authentication of your emails and track who is sending emails. That way, you can fix any authentication issues and spot spammers or fraudsters abusing your domain.
Easily set up DMARC with Proton Mail
Using DMARC with SPF and DKIM is the most effective way to prevent your domain from being abused for spam or phishing attacks. However, setting up DMARC can be tricky, as it depends on the successful implementation of SPF and/or DKIM to work.
That’s why we’ve created a simple wizard to show you how. Get a Proton Mail paid plan, and we take you step by step through setting up your custom domain and configuring SPF, DKIM, and DMARC correctly.
Get Proton Mail Plus for a single domain or Proton Unlimited with support for three domains, 15 addresses, 500 GB of storage, and more.
If you have a business, you can easily set up DMARC to protect your brand’s domain with Proton for Business. Or if you’re just looking to try secure, private email, get Proton Mail for free.
All Proton plans include end-to-end encrypted Proton Mail, Proton Calendar, Proton Drive, and Proton VPN(nova janela). So join us, and stay secure!







