Fingerprinting is a way to identify you on the internet and can be very hard to prevent. In this article, we discuss what fingerprinting is, and how to reduce your fingerprint.
- What is browser fingerprinting?
- What is device fingerprinting?
- Combined fingerprinting techniques
- Fraud prevention
- How unique is your fingerprint?
- How to reduce your fingerprint
- Final thoughts
Websites like to know as much about you as they can. This is because the more they know about you, the better they can target ads at you. They are therefore very keen on tracking your activities on the internet to build up a detailed model of your likes, dislikes, hobbies, and more, based on your web browsing history.
They then use the scary amount of personal information collected to target you with highly personalized ads.
There are, however, legitimate reasons for websites wanting to uniquely identify their visitors, such as preventing credit card and bank fraud and eCommerce fraud.
In the past, websites could readily identify you by your IP address(new window) and could track you across websites using third-party cookies(new window). However, increased awareness of privacy issues over the last few years has made this task more difficult. More and more people use a VPN to hide their IP addresses and take measures to block third-party cookies.
Indeed, the Safari, Firefox, and Brave browsers have recently taken the bold move of blocking all third-party cookies by default,
Websites have responded by adopting more sophisticated tracking mechanisms, such as HTTP E-Tags(new window), web (or DOM) storage(new window), and browser history sniffing(new window).
The most common and effective alternative methods used to uniquely identify web users today, however, are browser and device fingerprinting.
What is browser fingerprinting?
Your browser always divulges some information to websites you visit, such as the browser name, operating system, and exact version number of the browser. This is often called passive browser fingerprinting because it happens automatically.
In addition to this, websites can ask your browser for additional information, such as a list of supported data types (so-called MIME types), operating system and version, installed fonts, installed plugins, system colors, screen resolution, browser time zone, and more. This is often called active fingerprinting because the information needs to be requested.
What is device fingerprinting?
Device fingerprinting traditionally works through the browser, and also includes browser fingerprinting. In addition to browser characteristics, it tries to further identify a website visitor using the unique characteristics of their devices, such as screen size, color depth, device IP address, and even audio signals(new window), battery life(new window), and accelerometer calibration(new window) can help identify your device.
An influential 2014 study(new window), “the most extensive sensor fingerprinting experiment done to date”, by researchers at Stanford University, showed that, “the entropy from sensor fingerprinting is sufficient to uniquely identify a device among thousands of devices, with low probability of collision.”
Until recently, fingerprinting wasn’t needed to identify app users, as apps had direct access to a wide range of personal information that could identify your device, anyway, including your IP address, MAC address(new window), IMEI number(new window), and more. However, recent versions of both Android and iOS now prevent app developers from accessing these system-provided identifiers.
It is still possible to use tricks, such as generating a Universally Unique Identifier(new window) (UUID) file that (much like a browser cookie) can be stored on a device, but the unreliability of such methods (for example they will be deleted if the app is uninstalled) means app developers are increasingly turning to device fingerprinting methods of the kind outlined above.
Combined fingerprinting techniques
In 2016, a wide-scale study(new window) of online trackers carried out by researchers at Princeton University found that websites typically use a range of fingerprinting techniques, which when combined, can prove effective against a wide spectrum of anti-tracking measures.
It found that, although popular anti-tracking measures were quite effective against more common kinds of fingerprinting techniques, such as canvas fingerprinting and canvas font fingerprinting (both common forms of browser fingerprinting), “Only a fraction of the total number of scripts utilizing the techniques are blocked (between 8% and 25%) showing that less popular third parties are missed. Lesser-known techniques, like WebRTC IP discovery and Audio fingerprinting, have even lower rates of detection”.
Fraud prevention
Abuse of fingerprinting methods for advertising and analytics purposes understandably draws a great deal of criticism, but these methods are also an invaluable tool for preventing various kinds of fraud and online abuse.
Fingerprinting can help determine if an internet banking session has been hijacked, and can identify credit card fraud. For example, fingerprinting can help determine if multiple requests that appear to be from multiple cards, each with different IP addresses, actually originate from the same device.
Similarly, when combined with other detection methods, fingerprinting can help prevent e-commerce fraud by identifying fraudsters attempting to access a legitimate customer account from unusual devices or browsers.
How unique is your fingerprint?
A 2010 study(new window) by the Electronic Frontier Foundation found that 84% of browsers had a unique configuration, while also accepting there were many factors used by fingerprinting software that it was unable to test for, and which would therefore result in higher real-world detection rates.
Vendors of fingerprinting products, such as FingerprintJS, claim 99.5% accuracy(new window) for browser fingerprinting and over 90% accuracy(new window) in correctly identifying a unique user in the browser when using Android, “and when combined with usage history, fuzzy matching, and probability engines, this accuracy can be further improved.”
The Electronic Frontier Foundation offers Cover your tracks(new window), a free tool that assesses how unique your browser is.
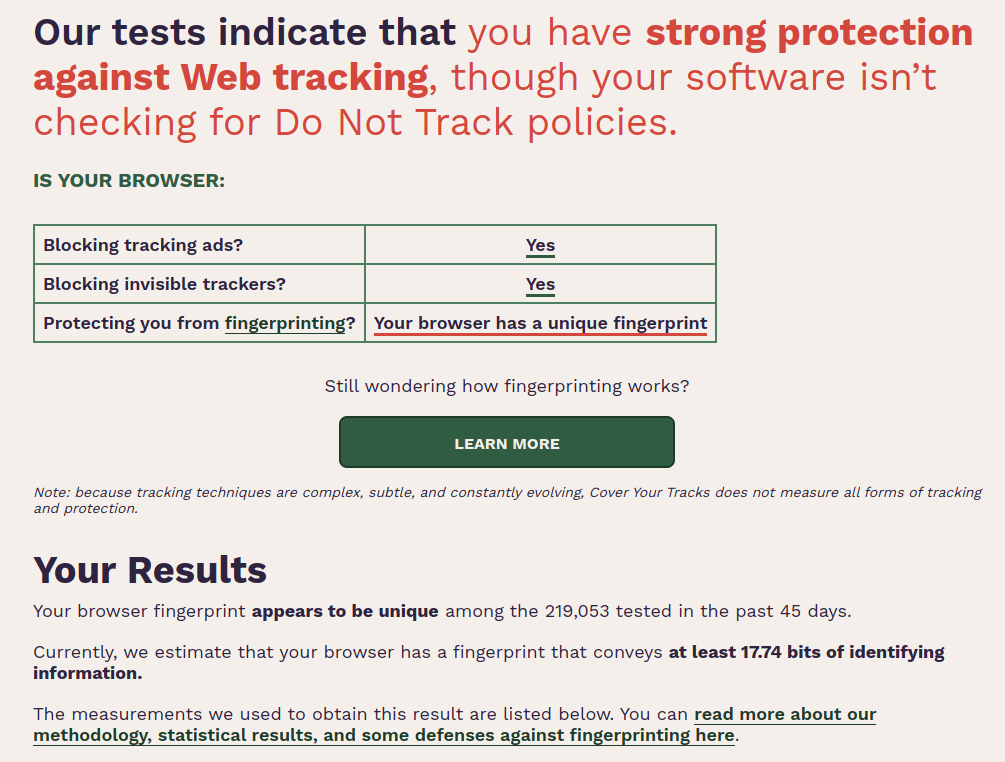 (new window)
(new window)How to reduce your fingerprint
One of the most frustrating aspects of browser fingerprinting is that every time you change your browser, such as installing browser add-ons, you make it more unique.
This means installing add-ons designed to protect your privacy and prevent tracking actually make it more vulnerable to browser fingerprinting (you can see this dynamic in action in the Firefox screenshot above with various privacy-related plugins installed).
Anti-fingerprinting add-ons are available for Firefox and Chrome, but in our tests they proved largely ineffective. Firefox offers an experimental fingerprinting protection feature(new window), but again, this did not prevent Cover your tracks from uniquely identifying our browser.
The EFF notes that add-ons, such as NoScript(new window) for Firefox can be quite effective at defending against fingerprinting, but this is a tool that is not easy to use and requires careful configuration to avoid “breaking” many websites.
In our tests, Safari on macOS and iOS/iPadOS, and Chromium Edge on Windows had unique fingerprints.
However, Brave browser uses a randomization method that was effective at preventing browser fingerprinting on the desktop and on Android, although not on iOS/iPadOS (this is almost certainly because Apple restricts third-party browsers to using the iOS WebKit framework, which severely limits what they can do on the platform).
Tor browser was even more effective at blocking fingerprinting on the desktop at even the Standard security level(new window), although it only provided partial protection on Android with the security level set to Safest.
NetShield (Ad-blocker)
All Proton VPN apps(new window) offer our NetShield (Ad-blocker) feature that blocks DNS requests to malware, ad, and tracker domains. With NetShield (Ad-blocker) enabled, many invasive fingerprinting scripts are blocked, which can substantially reduce your fingerprint(new window).
Learn more about NetShield (Ad-blocker)(new window)
Final thoughts
Like all technological advances, browser and device fingerprinting can be used for good or ill, and they are undeniably a useful tool in the fight against banking, credit card, and e-commerce fraud.
However, their widespread use by websites to track and any spy on their uses for advertising purposes is a clear privacy violation, made all the more insidious because it is so hard to prevent.
The fact that when using the most popular browsers, any efforts you make to improve your privacy actually increases your vulnerability to browser fingerprinting, is all the more galling.
Websites attempt to lay the blame at our feet — claiming the increased use of ad blockers, cookie managers, and other anti-tracking measures means they are unable to make money from advertising, thus forcing them to use increasingly underhanded methods of tracking their visitors.
This, however, amounts to little more than gaslighting their own users. No one asked for, or agreed to, being spied on when using the internet. And now that more and more people are taking matters into their own hands to protect their privacy, there is no excuse for turning to ever more arcane and deceitful methods of undermining the wishes of their visitors.
It is therefore encouraging to see that Brave and Tor Browser have developed effective defenses against what is, when used for advertising and analytics purposes, a pernicious and highly cynical method of invading internet users’ privacy.







