Proton ile basın özgürlüğünü savunun
Gazeteciler saldırı altında. Proton, sizi ve kaynaklarınızı güvende tutmak için e-postalarınızı, kişilerinizi, belgelerinizi ve diğer verilerinizi uçtan uca şifreleme ile korur.
Güncelleme: Eşi benzeri görülmemiş tehditlere karşı koymak için haber kuruluşlarına yönelik Proton for Business tarifelerinde indirimler sunuyoruz.
Sınır Tanımayan Gazeteciler tarafından önerilmektedir ve gazeteciler tarafından her yerde güvenilir bulunmaktadır.
Kullananlar
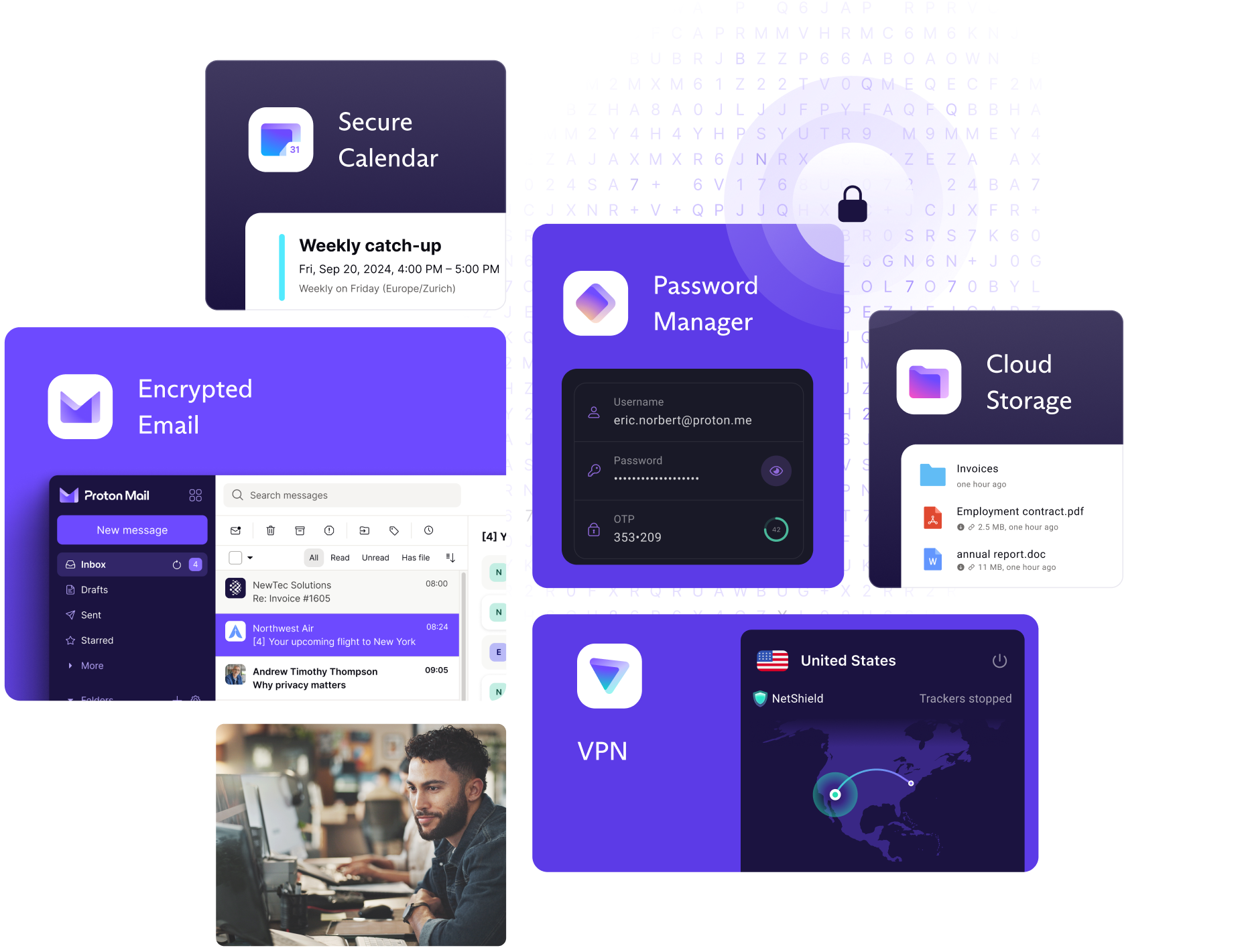
Proton, gazetecilerin güvenli bir şekilde çalışmasını ve güvenli bir şekilde iletişim kurmasını sağlar.
Güçlü şifrelememiz ve İsviçre yargı yetkisinde bulunmamız, verilerinizi her zaman elinizde tutmanızı sağlar. Uçtan uca ve sıfır erişim şifrelemesini otomatik olarak uyguladığımızdan, e-postalarınız, takvim etkinlikleriniz, dosyalarınız, belgeleriniz ve parolalarınız verilerin ele geçirilmesine ve izlenmesine karşı güvendedir. Ayrıca İsviçreli bir şirket olarak, yasal olarak herhangi bir yabancı mahkeme celbine uymamız gerekmiyor.
Her yıl, yüzlerce gazeteci haberlerinden dolayı öldürülüyor veya hapse atılıyor. Binlerce kişi izleme, sansür ve hükümet yetkililerinden veya aşırılık yanlısı gruplardan gelebilecek tepkilerin korkusuyla karşı karşıya. Amacımız, güçlü ve kullanılması kolay dijital güvenlik araçlarıyla sizi korumaktır.
Proton gazetecileri nasıl korur
Proton güvenliği, uçtan uca şifreleme ile başlar. Kimse — hatta Proton bile — e-postalarınızı, takvim etkinliklerinizi, dosyalarınızı ve sunucularımızda bulunan diğer verilerinizi göremez.

Ekibinizle ve kaynaklarınızla güvenli bir şekilde iletişim kurun
Proton Mail, e-postalarınızı taramaz (ve tarayamaz) veya üçüncü taraflarla paylaşamaz. Anonim kaynaklarla iletişim kurarken veya gizli bilgileri işlerken, iletilerinizi yalnızca hedeflediğiniz alıcılar görebilir.

Önemli dosyaları güvenli bir şekilde depolayın ve paylaşın
İhbarlardan araştırma belgelerine kadar, şifrelenmiş Proton Drive bulut depolama alanı dosyalarınızı güvende tutar. Dosyalarınızın yetkisiz erişime karşı tam olarak korunduğunu bilerek önemli verilerinize farklı aygıtlardan erişin ve paylaşın.

Şifrelenmiş belgelerle hikayeler üzerinde işbirliği yapın
Not alırken veya bir yazı taslağı hazırlarken, Proton Drive Docs uygulaması diğer kişilerden gelen verileri ve düzenlemeleri bir arada toplayan tek çevrim içi belge düzenleyicisidir. Bu işlem tam uçtan uca şifreleme ile gerçek zamanlı olarak yapılır.

Engellenen içeriğe erişin ve internet üzerinde gizliliğinizi koruyarak gezinin
Gazetecilerin güvendiği VPN hizmetiyiz. Proton VPN, IP adresinizi gizler ve internet trafiğinizi şifreleyerek izlenmekten korur. İzleyicileri engeller ve sansürü aşarak internete istediğiniz her yerden özgürce erişmenizi sağlar.
Parolaları ve kimlik doğrulama bilgilerini güvenli bir şekilde yönetin
Proton Pass, ekibinizin önemli kimlik doğrulama bilgilerini uçtan uca şifreleme ile korur. Yetkisiz erişim veya verilerin ele geçirilmesi riskini azaltır. Hesaplar veya veri tabanları için parolaları kolayca kaydedin ve paylaşın.

Ekibinizi organize edin ve programınıza uygun kalın
Şifrelenmiş takvim ile ekibinizle toplantılar ayarlayabilir, video bağlantılarını paylaşabilir veya kaynaklarla görüşmeleri düzenleyebilirsiniz. Kimse nerede olduğunuzu veya ne yaptığınızı göremez, bu da ekibinizin güvenliğini artırır.
On yılı aşkın süredir basın özgürlüğüne destek oluyoruz
2014 yılındaki kuruluşumuzdan bu yana Proton, dünya çapında bağımsız gazeteciliği sürekli olarak desteklemiştir. Kâr amacı gütmeyen Proton Vakfı aracılığıyla, Charter'97, The Markup, Freedom of the Press Foundation ve Uluslararası Gazeteciler Federasyonu’nun Güvenlik Fonu gibi medya kuruluşlarını doğrudan destekledik.
İsviçre merkezli
İsviçre merkezli bir şirket olarak, geçerli bir İsviçre mahkeme kararı olmadan verilerinizi kimseyle paylaşamayız. Verileriniz güçlü gizlilik yasalarıyla korunur ve Birleşik Devletler veya Avrupa Birliği yargı yetki alanlarının dışındadır.
Açık ve şeffaf
Uygulamalarımız açık kaynaklıdır ve bağımsız olarak denetlenir. Böylece herkes kodumuzu kontrol edip güvenli olduğuna emin olabilir. Şeffaflık, temel değerlerimizden biridir.
Topluluk destekli
2014 yılında bir topluluk desteği kampanyası ile kurulan Proton, %100 topluluğumuz tarafından finanse edilmektedir. Yatırım sermayesi veya reklam finansı kullanmıyoruz.

Proton ile haber odanızı koruyun
Medya kuruluşları için özel fırsatımızdan yararlanın. Ekibinizin gereksinimleri ve büyüklüğüne göre tarifenizi özelleştirin.



