If you’ve used Proton Pass recently, you’ve already experienced some of the speed and stability that Rust provides. With Proton Authenticator, we took a significant leap forward, moving more of the core logic to Rust to ensure strong data security, fast performance, and cross-platform consistency. Here’s a look into why and how we did it.
Why Rust?
Rust is a programming language that provides developers with safety guarantees. Safety is a necessary component to ensure security and stability. With features like a powerful memory management system and concurrent access guarantees, Rust allows us to build our products with the high degree of quality we aim for.
Apart from its safety guarantees, Rust also provides high performance and a powerful cross-platform capability, all of which are critical for Proton to seamlessly deliver privacy-focused services for all major devices. Rust also makes it easier to adapt our services to run on new platforms in the future, such as platforms without a GUI or new operating systems.
We evaluated many technologies in the process, and in the end, we found that Rust:
- Has the best tooling and developer experience, one of the best for our needs.
- Offers the best support for the platforms we’re currently focused on.
- Has a good ecosystem of third-party libraries that we can build upon.
By using of the cross-platform capabilities Rust offers, we can code things once and run them directly on every platform we support (Android, iOS, Windows, Mac, and Linux). By having a single common implementation, we can guarantee consistency, speed, and fewer bugs than if we coded the same features multiple times. Imagine if your TOTP codes were different on every device, that would be a disaster!
We started prioritizing Rust in all our new work a while back, and we haven’t regretted that choice at all!
What Rust powers in Proton Authenticator
If you’re interested in the current state of Proton Authenticator’s Rust code, feel free to take a look at it. We’re committed to keeping our client code open source so that anyone can inspect it or even build our authenticator apps themselves if they want. You can find the common Rust libraries for Proton Pass and Proton Authenticator in our GitHub repository(nieuw venster). There you will see how Rust powers Proton Authenticator.
Importers
A critical feature for Authenticator was enabling users to transfer their 2FA data from existing applications. We implemented importer logic entirely in Rust, ensuring a smooth migration experience across all Proton Authenticator clients on desktop, Android, and iOS. You can now import your data from other authenticator services regardless of which platform you are using. If we decide to support more platforms in the future, we simply need to add them to the shared Rust codebase, and all clients will be compatible immediately.
Sync engine
Proton Authenticator is designed to work offline and without access to a Proton Account (in other words, anyone can use it). However, if you have a Proton Account, you can use it to synchronize the data associated with your time-based one-time passwords (TOTPs) across all your devices (for example, editing the title you gave a TOTP). If you enable device synchronization, Proton Authenticator must reconcile the data on all your devices.
We built a robust synchronization engine using Rust, which guarantees consistent behavior across all platforms in any situation. This means your TOTPs will sync efficiently, even if you update data on another device or are in an area with limited connectivity.
Data validation, serialization, and encryption
We built the core logic for Proton Authenticator using Rust, providing high security standards for data validation, serialization, and encryption of your data. By centralizing these critical functions, we can ensure interoperability, consistency, and security, regardless of the client platform.
Thanks to this, we can ensure that all the TOTPs you set up and use are 100% compatible with all your devices, be it your Steam 2FA while you are on your phone or your Proton TOTP while accessing your inbox on your laptop.
Thanks to this shared implementation, if you use your Proton Account to sync your codes across your devices, the transition from one device to another will be seamless. All your codes will be there, already available to you. As all the data that travels to Proton servers is encrypted before it leaves the device, our servers cannot guarantee that no malformed data is generated, so by relying on our Rust implementation, we can make sure that all Proton Authenticator apps generate and encrypt data that others can read.
For symmetric encryption, we rely on a battle-tested and audited AES-GCM implementation by RustCrypto(nieuw venster), which gives us a cross-platform, safe, and secure encryption mechanism that we can use in all of our clients.
TOTP generation
Proton Authenticator uses a common Rust implementation for its TOTP generation logic in order to guarantee consistency across platforms. This ensures that your codes always match, regardless of which device you’re using.
We’re using the same underlying base for TOTP generation as we use in Proton Pass, so in the future, we’ll be able to enhance the TOTP capabilities in Proton Pass thanks to the advances we’ve made for Proton Authenticator.
Data export and backup
We want to emphasize the fact that with Proton Authenticator, you’re always in control of your data. The key to that is data portability. Proton Authenticator provides robust import and export functionalities, and by handling exports with Rust, we maintain a standard, backwards-compatible format across all devices.
How we structured our Rust implementation
We structured the Proton Authenticator Rust library around the concept of clearly bounded Rust crates, promoting modularity, maintainability, and ease of integration:
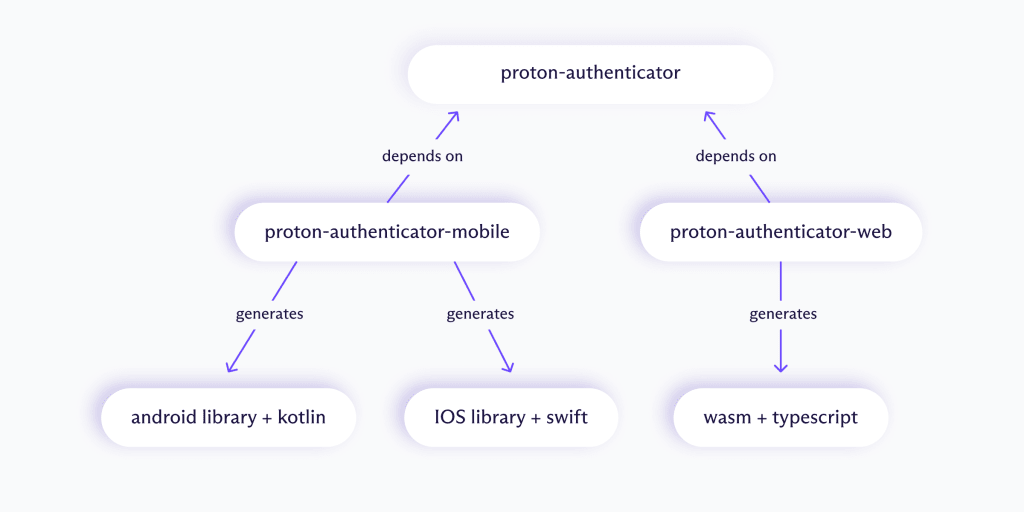
Crate structure
- proton-authenticator
- Pure Rust, platform-agnostic code
- Extensively tested
- Contains core domain logic: cryptography, data validation, serialization, TOTP generation, and more
- proton-authenticator-mobile
- Thin binding layer for mobile platforms
- Uses native build toolchains to build the libraries used by the mobile clients
- proton-authenticator-web:
- Similar to the mobile crate, but targets WebAssembly.
- Uses wasm-pack to build a wasm binary artifact that can be loaded in places like the browser or other wasm runtimes
By keeping the core crate fully independent of the client crates, we can ensure it contains pure functions and prevent side effects. This separation provides a major benefit — we can use the core crate to model all of a client’s input-output cases as a unit test. If any of our apps encounter a bug or strange behavior, it’s easy to reproduce that situation in a standalone test, completely independent from any client interaction. This makes debugging fast and focused and helps us maintain the core as a reliable foundation for all our clients.
Bindings
- Mobile: Leverages Mozilla’s UniFFI framework for seamless bindings between Rust and native mobile languages
- Web: Utilizes wasm_bindgen and tsify to generate TypeScript bindings that can interact with the wasm artifact we generate
This structure gives us a lot of flexibility. By separating the main core library from the final artifacts, we can evolve it independently, adding internal features and testing them until we are confident about their quality. Then, we can offer these new features in the clients by exposing the new functions in the mobile and web libraries, making them easily available for our users. And also, by having the main core library be a pure Rust crate, we can use it as a direct library in other projects (stay tuned for exciting news about this!).
Expanding Rust at Proton
Our journey with Rust is just beginning. Proton is moving towards having a single shared implementation written in Rust for each of our services. We’re also creating a comprehensive set of libraries to move even more functionality, such as database access, session management, encryption, and HTTP requests, to Rust. This strategy will streamline product development, foster robust interoperability among Proton services, and eventually enable us to provide even more powerful components to our community so that they can build their own solutions on top of the Proton ecosystem.
Choosing Rust for Proton Authenticator represents a significant milestone in Proton’s technical evolution. Rust’s inherent safety, performance, and cross-platform capabilities allow us to deliver a secure, consistent, and user-friendly 2FA product. Stay tuned as we continue to push the boundaries of privacy and security with Rust.
