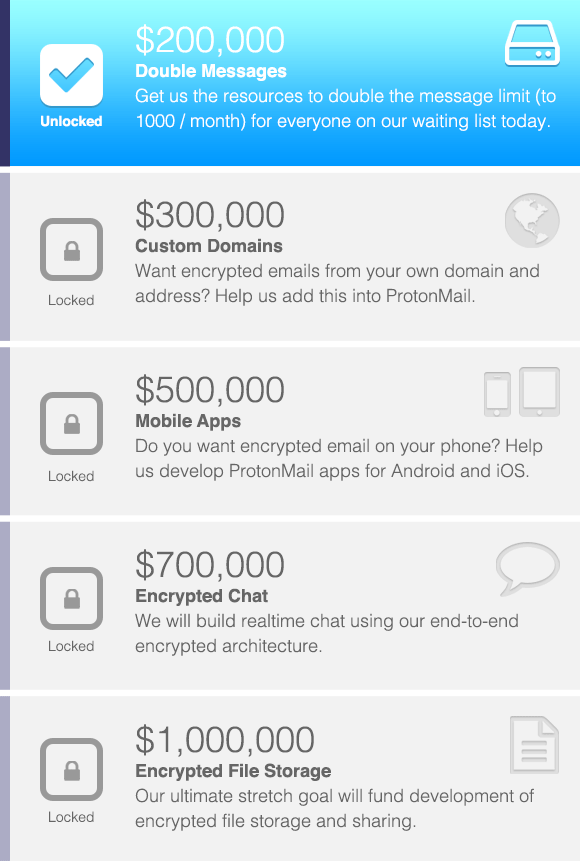
Now that the Proton Mail Campaign(nieuw venster) has raised over $250,000 for protecting online privacy, some people have asked us, how much do we need to raise to accomplish our stretch goals?
In the table below, we have outlined our goals, and the amount of money that would be necessary to turn these goals into reality.
We hope to get enough funding to at least build out the Android and iOS versions of Proton Mail. This would require us to raise double our current funding of $250,000. The money would go towards the additional servers we need to support the load from app users, and hiring additional developers to join our team to speed up development of the apps. We intend to build these features even if the funding targets are not met, but with more funding, we’ll be able to build in all these features faster and help everyone better protect their privacy.
Ensuring security and privacy for all requires constant innovation as every day, there are powerful organizations working on new ways to deprive us of this fundamental human right. Any additional funding we receive puts us in a much stronger position to meet these challenges.
As history has shown time and time ago, freedom and privacy go hand in hand, as one simply cannot have one without the other. Please share our campaign, and let people know why privacy matters.