Phishing was the most common cybercrime reported to the Internet Crime Complaint Center(nieuw venster) in 2024. We’ve written about what phishing is and given some examples of convincing phishing emails on our blog, but cybercriminals are always adjusting their attacks to maximize their return.
A more effective version of phishing is when attackers target specific people, which is called whaling or spear phishing. While phishing can target individuals or businesses, whaling and spear phishing specifically target those within a business. It’s important to understand the difference between these terms, as well as how to spot them and how to protect yourself against them.
What’s the difference between whaling, phishing, and spear phishing?
Phishing is a method that hackers use to trick you into sharing sensitive information with them. If you’ve ever received a suspicious-looking email from a service like Amazon, Google, or PayPal telling you that your account has been frozen, you’ve been targeted by a phishing attempt. These attacks are broad and aim to get as many responses as possible. You’ll receive them to your personal email address as well as your work email address.
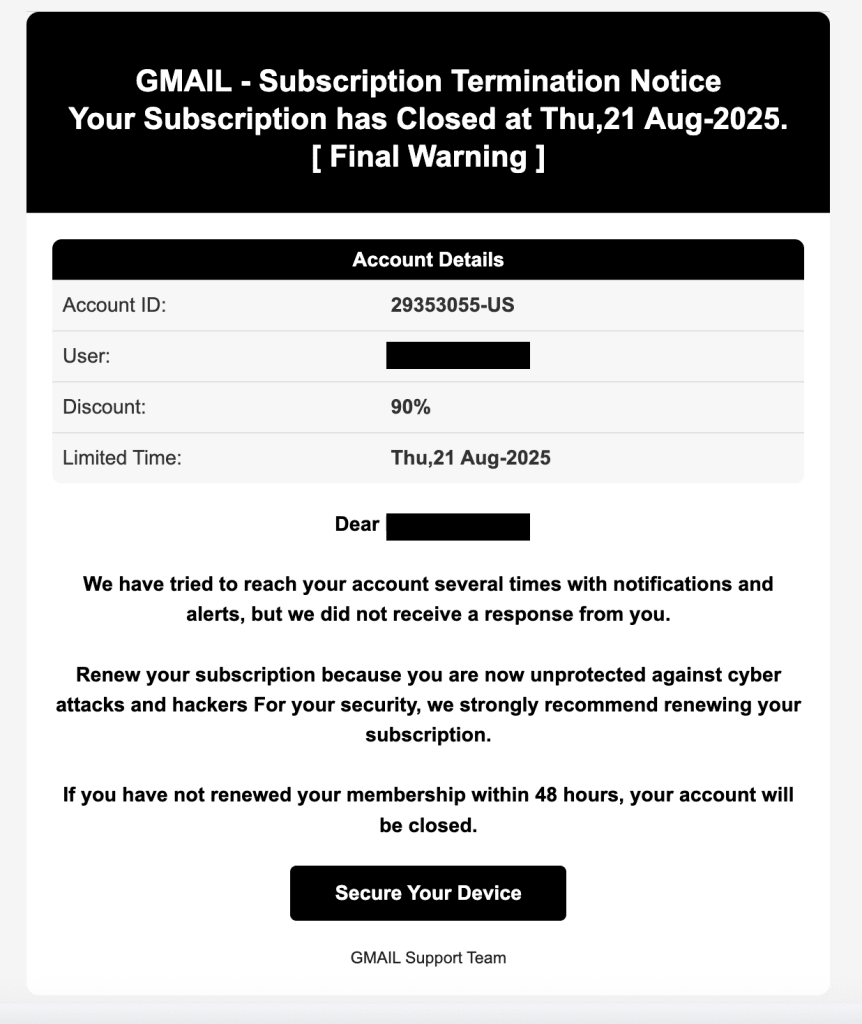
Spear phishing and whaling attacks use the same tactics as phishing, but deploy them on a much smaller and specific set of targets within a business. Both types of attack fall broadly under the category of phishing, but it’s worth understanding how a hacker’s target affects the tactics they use.
What is spear phishing?
Spear phishing takes the same broad techniques used for phishing attacks and tailors them to specific individuals. The individuals targeted by spear phishing often work in legal or finance departments, giving them access to particularly sensitive and valuable data.
According to research published by Barracuda Networks(nieuw venster), more than 80% of spear phishing attacks involve brand impersonation. After analyzing 360,000 phishing emails over three months, the firm found that Microsoft and Apple are the most-impersonated brands, with attacks most likely to occur between Tuesday and Thursday and spike around events such as tax season. This level of planning on the part of the scammers speaks to how closely they study employees and plan their attacks.
The report suggests that the top three subject lines used by spear phishing attacks are some variation of the following:
- Request
- Follow up
- Urgent/Important
It isn’t surprising that the subject lines create either a sense of urgency or the impression that you’ve already been in contact with the sender. There can also be political motivations for spear phishing attacks. In 2024, Microsoft released intelligence(nieuw venster) regarding Iranian interference in the US election. A former senior adviser’s Microsoft Hotmail account was compromised in order to launch an attack targeting a high-ranking official on a presidential campaign.
What is whaling?
Where spear phishing targets several high-level individuals, whaling targets… well, whales. Whaling is effectively spear phishing directed at a very valuable target, such as a CEO or CFO. These attacks are highly personalized and meticulously researched. Cybercriminals stand to make money, as well as potentially gaining access to sensitive data such as IP or investor information, blackmailing their targets, and causing enormous reputational damage.
Whaling attacks take months, if not years, to plan effectively, and criminals target businesses going through turbulent events to exploit the chaos. In 2015, attackers targeted C-level executives at Mattel with an elaborate whaling attack(nieuw venster) while the company was restructuring and changing its payment policy. A finance executive received a note from the business’s new CEO requesting a new vendor payment to China, a country Mattel was trying to expand into. Following the payment policy changes, transfers required approval from two high-ranking managers within Mattel, so the recipient gave her approval, and the transfer was made. Only after the money was gone did the executive mention the payment to the new CEO, who had not made the request.
Thanks to May 1 being a banking holiday in China, Mattel was able to freeze the account that held the stolen funds, and the money was recovered within two days. But this highly targeted attack could have cost Mattel $3 million with a single email.
Whaling vs spear phishing
To sum up the differences between the three types of attacks:
| Phishing | Targets everyone with generic attacks |
| Spear phishing | Targets specific people with specific attacks |
| Whaling | Targets VIPs and business leaders with personalized attacks |
The specificity of the target dictates the amount of research and targeting that go into each attack. But no matter the type of attack, there’s a similar process that hackers will follow for planning and executing.
What is the process of a whaling or spear phishing attack?
- Reconnaissance: The hacker researches their target by examining their online presence to create a profile of their target’s likely triggers for responding. This includes social media profiles, business websites, and any other place their target might appear online. They’ll also use data brokers and potentially the dark web to obtain personal information.
- Crafting the bait: The hacker then puts together a plan of attack. They’ll create an email designed to convince their target that they’re a colleague, a third-party service, or a governmental agency. They’ll collect as much information as possible to fool their target, possibly by phishing more widely within the business.
- Delivery: The attackers will send the tailored email to their target. It could look like an invoice and contain a link to a malicious website, inviting the reader to enter payment details, or a request from the business IT department for logins and passwords.
- Exploitation: The email might be loaded with malware or ransomware, link to a spoofed site, or ask for credentials, sensitive information, or payments. There are multiple ways for hackers to exploit your network once they’ve gained access, such as establishing backdoor access and giving themselves admin privileges.
- Impact: If the attack is successful, the hacker will continue phishing for more access or begin making transactions, downloading data, or taking over accounts. The company faces financial loss, a data breach, reputational harm, or all of the above.
Attacks come in many forms, making it difficult to always be on your guard. In general, the more senior your role or the more sensitive data you have access to, the more important verification becomes.
How can you protect yourself against attacks?
There are two parts to protecting yourself against cyberattacks: Your business infrastructure and your own awareness.
First, let’s look at what you can personally do.
- Trust but verify. If you receive a request regarding a payment or granting access to sensitive data, speaking to the person who allegedly sent you the request is your best bet. If you’ve met the person before, call them or speak to them face to face and confirm the request is legitimate. If you haven’t, verify their identity through trusted channels, such as a colleague with connections or a higher-ranking individual at their business.
- Don’t let urgency push you into making a mistake. Fraudsters use fake urgency to encourage you to make a rapid decision. You won’t regret waiting to verify a request, but you might regret not verifying one.
- Check the sender’s email address closely. When a hacker makes it seem like their email is coming from a legitimate sender, this is called email spoofing. Make sure that the domain name is correct and that there aren’t any spelling errors in the email address itself. Find out more about how to protect yourself from email spoofing.
- Educate your team about the risks of phishing attacks. A single successful phishing email can have devastating consequences for a business.
Being aware of potential threats doesn’t mean being suspicious of every single email you receive, but it does mean ensuring that you’re taking steps to protect both yourself and your workplace.
How Proton helps you reduce your risk
Another effective way of protecting your workplace is by adopting secure, end-to-end encrypted tools that help you retain control of your data:
- Proton Pass is a secure password manager that helps you create, store, and manage business passwords. Giving your team to securely share their credentials helps everyone identify illegitimate requests for logins or data — if someone is asked to email a password rather than share it securely in Proton Pass, they can flag the request as suspicious. You can also ensure that if your data appears on the dark web, you’re immediately alerted so you can take action to prevent phishing attempts.
- Proton Mail is a secure email and calendar that keeps your business emails protected. Our advanced phishing protection PhishGuard defends you against phishing attempts by flagging potentially spoofed email addresses for you. Any suspicious logins or account changes are identified and flagged to you automatically, and link protection helps you see full URLs before you open them to prevent accidentally opening a phishing link.
If you’re ready to protect yourself and your business against whaling, spear phishing, and phishing attacks, start today by seeing which Proton plan is best for you.






