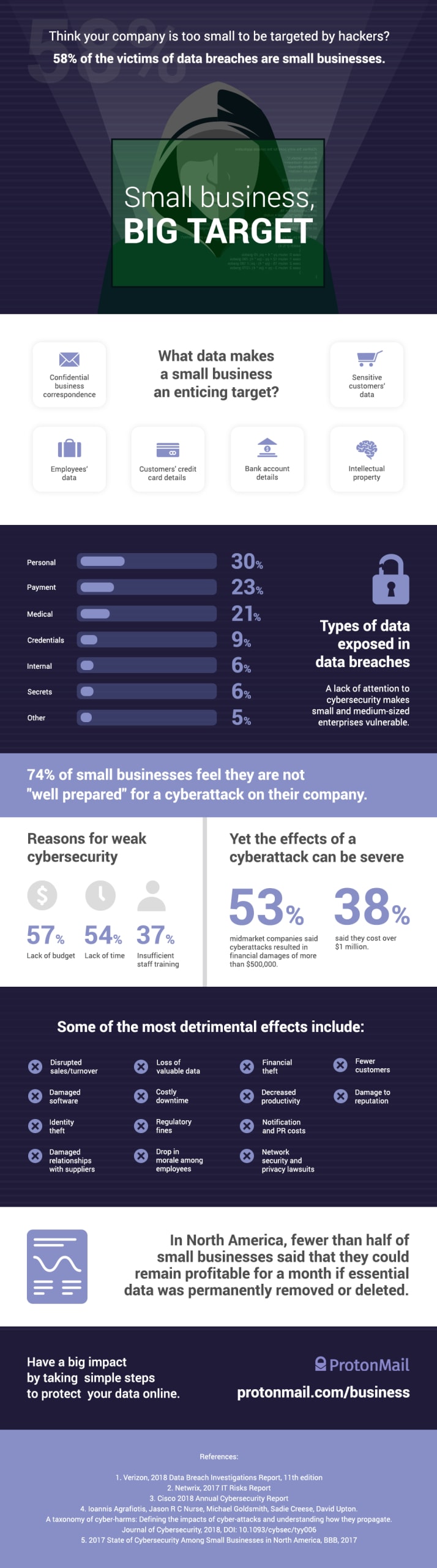
Small businesses are big targets for hackers, but they still aren’t prepared.
Data breaches that make the news usually involve massive corporations with vast datasets. But small businesses must also prevent cyberattacks and data breaches, and most don’t feel prepared.
“We lost $10,000 due to a cyberattack on our mainframe in which a hacker was able to access financial data.”
“An email was sent from a banking institution which was opened and a ransom note was given. Shut down all my computer systems and I lost all data.”
“I lost money to a cyberattack due to a corrupt employee who stole my information.”
These are just a few of the horror stories the Better Business Bureau compiled in a recent survey(nowe okno) of small businesses. Hackers disproportionately target small businesses, perhaps because small businesses are less equipped to prevent cyberattacks and manage the fallout.
Three-fourths of small businesses don’t feel “well prepared” for cyber security threats, and 17% of data breaches(nowe okno) occur because someone made a mistake (like clicking on a phishing email). Yet the consequences of an error could not be higher. Most small businesses say they could not remain profitable for a month if they lost their data, leaving them extremely vulnerable to ransomware attacks.
Infographic small businesses and data breaches
The infographic below is a warning shot for small and medium-sized businesses: The hackers are after you. Are you ready for them?
Sign up and get a free secure email account from Proton Mail.
We also provide a free VPN service(nowe okno) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan or donate. Thank you for your support.