Czym jest szyfrowanie end-to-end (E2EE) i jak działa?
Szyfrowanie end-to-end sprawia, że Twoje informacje pozostają prywatne, więc tylko Ty i osoba, z którą się komunikujesz, możecie je zobaczyć. Dowiedz się, jak to działa i dlaczego jest ważne dla Twojej prywatności.

Co to jest szyfrowanie end-to-end?
Szyfrowanie end-to-end (E2EE) szyfruje Twoje dane na Twoim urządzeniu i odszyfrowuje je dopiero na urządzeniu odbiorcy. W „end-to-end” jeden koniec to źródło (Twoje urządzenie), a drugi to cel (urządzenie odbiorcy) podróży Twoich danych.
Bez E2EE Twoje dane mogą zostać odszyfrowane po drodze – na przykład na serwerach firmy – co czyni je podatnymi na ataki hakerów, inwigilację i niewłaściwe wykorzystanie. Dzięki E2EE nikt pośrodku nie może odczytać, zeskanować ani udostępnić Twoich poufnych informacji, nawet dostawca usług.
Jak działa szyfrowanie end-to-end?
Szyfrowanie end-to-end wykorzystuje kryptografię asymetryczną, aby zagwarantować, że tylko zamierzony odbiorca może odszyfrować Twoje dane. Każdy użytkownik ma klucz publiczny (który można bezpiecznie udostępnić) i klucz prywatny (przechowywany w tajemnicy na jego urządzeniu).
Kiedy wysyłasz dane, Twoje urządzenie szyfruje je kluczem publicznym odbiorcy, tworząc nieczytelne zaszyfrowane dane zwane tekstem zaszyfrowanym. Ten tekst zaszyfrowany może przechodzić przez wiele serwerów i sieci bez ryzyka, ponieważ tylko pasujący klucz prywatny może go odszyfrować.
Przykład szyfrowania end-to-end
Wyobraź sobie, że wysyłasz znajomemu zamkniętą skrzynkę, którą otworzyć może tylko jego klucz.
Zamykasz zawartość w skrzynce przed wysłaniem jej pocztą, a ona pozostaje zamknięta podczas podróży przez każdy punkt kontrolny – czyli „serwery”.
Każdy, kto zajmuje się skrzynką, może ją zobaczyć, ale nie może zajrzeć do środka ani podmienić zawartości. Tylko klucz Twojego znajomego może ją otworzyć.
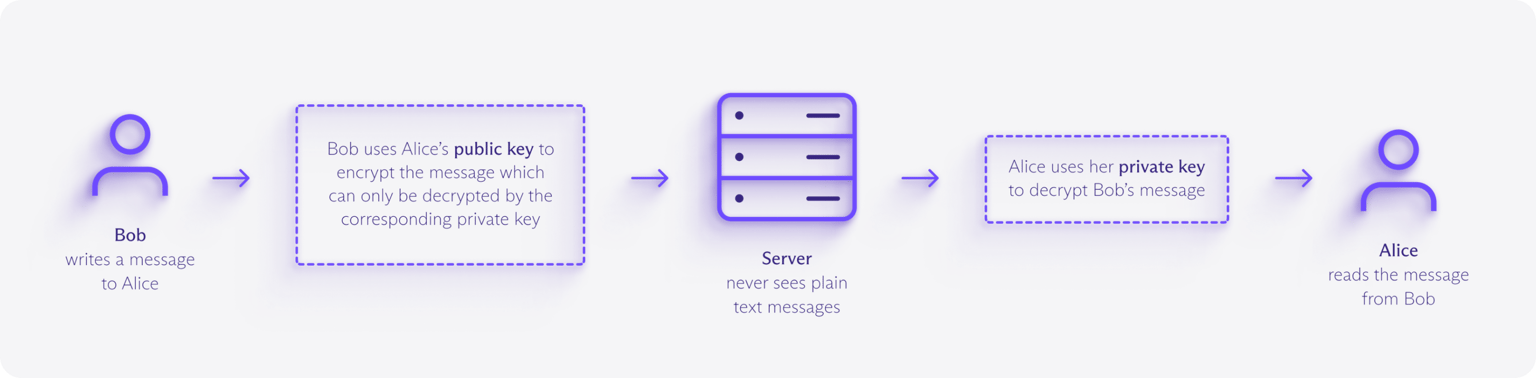
Czym różni się szyfrowanie end-to-end od standardowego szyfrowania?
Usługi online tradycyjnie używają szyfrowania w transporcie, takiego jak TLS (technologia stojąca za HTTPS), aby szyfrować Twoje dane podczas ich przesyłania między Twoim urządzeniem a ich serwerami.
Działa to dobrze przy przeglądaniu stron internetowych lub przesyłaniu formularzy, ponieważ hakerzy lub dostawcy Internetu nie widzą poufnych informacji, które wprowadzasz lub odbierasz.
Ale gdy Twoje dane dotrą na serwery firmy, są odszyfrowywane i przechowywane przy użyciu kluczy, które ona kontroluje. Oznacza to, że mogą je przeczytać, udostępnić lub przekazać rządom bądź organom ścigania, jeśli zostaną o to poproszone.
Dzięki E2EE firma nigdy nie ma kluczy prywatnych, więc nie może czytać, skanować ani udostępniać Twoich treści, nawet gdyby chciała.
Jakie są korzyści z szyfrowania end-to-end?
Prywatność
Szyfrowanie end-to-end chroni Twoje wiadomości, zdjęcia, dokumenty i inne pliki przed skanowaniem, profilowaniem lub nieautoryzowanym dostępem. Dostawcy internetu, reklamodawcy, brokerzy danych i systemy inwigilacji nie mogą monitorować Twoich treści, co daje Ci kontrolę nad Twoimi danymi osobowymi.
Bezpieczeństwo
Ponieważ usługa przetwarzająca dane nie ma klucza do odszyfrowywania, nie musisz jej ufać, że nie przeczyta, nie sprzeda ani nie przeanalizuje Twoich treści. Nawet jeśli dojdzie do naruszenia bezpieczeństwa serwerów, skradzione dane pozostają nieczytelne. Szyfrowanie end-to-end zachowuje również integralność danych – Twoje treści docierają dokładnie tak, jak zostały wysłane – i jest zgodne z surowymi regulacjami dotyczącymi prywatności, takimi jak GDPR i HIPAA.
Wolność
Prywatna komunikacja wspiera wolność słowa. Szyfrowanie end-to-end chroni przed cenzurą, inwigilacją i prześladowaniami politycznymi, dzięki czemu możesz bez obaw dzielić się pomysłami i informacjami. Każdy potrzebuje tej ochrony, a zwłaszcza dziennikarze, aktywiści i obywatele w restrykcyjnych reżimach.
Przejmij kontrolę nad swoimi danymi
Proton został stworzony, aby chronić Twoje dane od samego początku. Dzięki szyfrowaniu end-to-end, aplikacjom open-source i niezależnym audytom, Twoje informacje pozostają Twoje.
Wiadomości, które wysyłasz do innych użytkowników Proton lub na adresy obsługujące PGP (otwarty standard dla E2EE), są zaszyfrowane end-to-end, włącznie z treścią wiadomości i załącznikami.
W innych przypadkach możesz dodać ochronę hasłem. W ten sposób tylko Ty i osoba, do której piszesz, możecie odczytać Twoje wiadomości.
Wydarzenia w kalendarzu, które tworzysz, są zaszyfrowane end-to-end, włącznie z tytułami, opisami, lokalizacjami i listami gości.
Nawet gdy udostępniasz swój harmonogram lub wysyłasz zaproszenie, nikt inny – nawet Proton – nie widzi, dla kogo ono jest.
Hasła, nazwy użytkownika, adresy internetowe, notatki, karty płatnicze, szczegóły tożsamości i inne dane, które zapisujesz, są chronione szyfrowaniem end-to-end.
Gdy udostępniasz sejfy, zarówno zawartość, jak i udostępnione linki są zaszyfrowane end-to-end, więc tylko zaproszone przez Ciebie osoby mogą zobaczyć, co jest w środku.
Wszystko, co przechowujesz i udostępniasz w chmurze, jest szyfrowane end-to-end, włącznie z zawartością plików, nazwami plików, nazwami folderów, podglądami i udostępnianymi linkami.
Tylko Ty i osoby, którym zdecydujesz się udostępnić dane, macie dostęp do Twoich plików – nawet Proton nie może ich zobaczyć.
Dowiedz się więcej o szyfrowaniu
Słowniczek pojęć związanych z szyfrowaniem