Google is one of the biggest obstacles to privacy. The Big Tech giant may offer quick access to information online, but it also controls vast amounts of your personal or business data.
Recently, more people are becoming aware of the actual price you pay for supposedly free services and looking for alternatives. A movement has emerged, known as deGoogling or de-Googling, to stop using Google services over concerns about privacy and the effects of a single company controlling so much information.
To help our community transition away from data exploitation, this article explores how to deGoogle your life or your workplace and take back control of your data.
Why should I deGoogle?
Over 3 billion people use Google products to search the internet, send emails, navigate roadways, and more. But Google’s business model revolves around targeted advertising, the success of which depends on surveillance and data mining.
These techniques include tracking your search queries, monitoring your interactions with online products and services, and even keeping tabs on your physical movements while using Google Maps. Each data point is funneled into a vast user profile, which is used to strategically present ads, an easy money grab that one industry executive described as a “newfound religion.”
This extensive surveillance apparatus has been the center of numerous privacy and courtroom disputes around the world. Google, however, has bought its way out of them with settlements and fines costing a tiny fraction of the revenue they generated with your data.
Despite the name recognition (Google is a verb(nové okno), after all) and convenience, there are many reasons to consider switching away from Google:
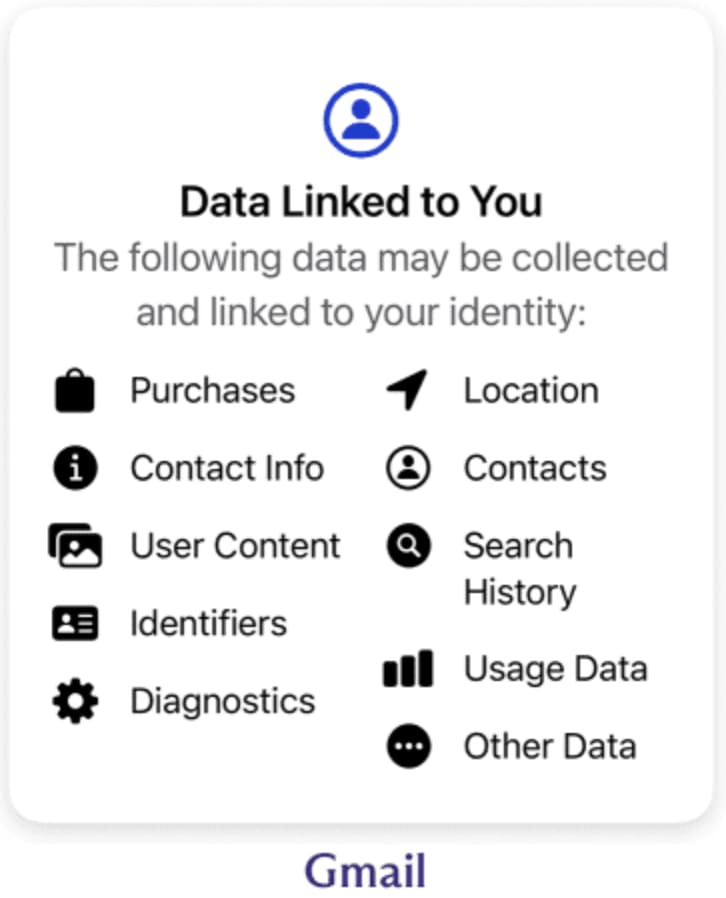
Data collection
As mentioned above, Google collects a wide variety of personal data. This presents both privacy and security risks, as leaked data is a major problem. Even data which is not used for ads, such as Gmail data, is still collected and could therefore be leaked in a breach or government data request.
Government surveillance
Google has the ability to access and analyze vast amounts of your personal information — from the emails you send to the appointments you make. This data can be shared with third parties, including law enforcement, without telling you. Under laws like Section 702 of the Foreign Intelligence Surveillance Act, Google and other tech giants can be compelled to hand over user data to government agencies without a warrant. This effectively turns corporations into data sources for government surveillance.
Manipulation and influence
Since Google’s business model rests on targeted advertising, they care primarily about serving companies’ interests rather than yours. That’s why they appear to manipulate search results(nové okno) and display information designed to influence you without your knowledge.
Training artificial intelligence
Google may use your data to train its AI systems, such as its spell check and autocomplete features. There is no way to opt out of having your personal data used this way. Google claims it anonymizes data before using it and doesn’t show you personalized ads based on the content you have in Google Drive, Docs, Sheets, Slides, or Photos.
Walled garden
Google seeks to trap you into using only their services, essentially removing your freedom of choice. For example, a Google Account, which automatically comes with a Gmail address, is required to use the Google Play Store. And if you want to link your Google Account to a different email address, you have to dig through several menus to do so manually. This inconvenience is by design, because using Google wants access to your communications and wants to keep you logged in while you use Search.
Yes, using Google might be convenient, but it is not free. You pay with your digital identity.
All of this is intolerable when you consider there are simple alternatives that let you own your data and give you the freedom to make your own online choices. The next sections explain how to switch.
How to deGoogle your digital life
Here are some simple steps you can take now.
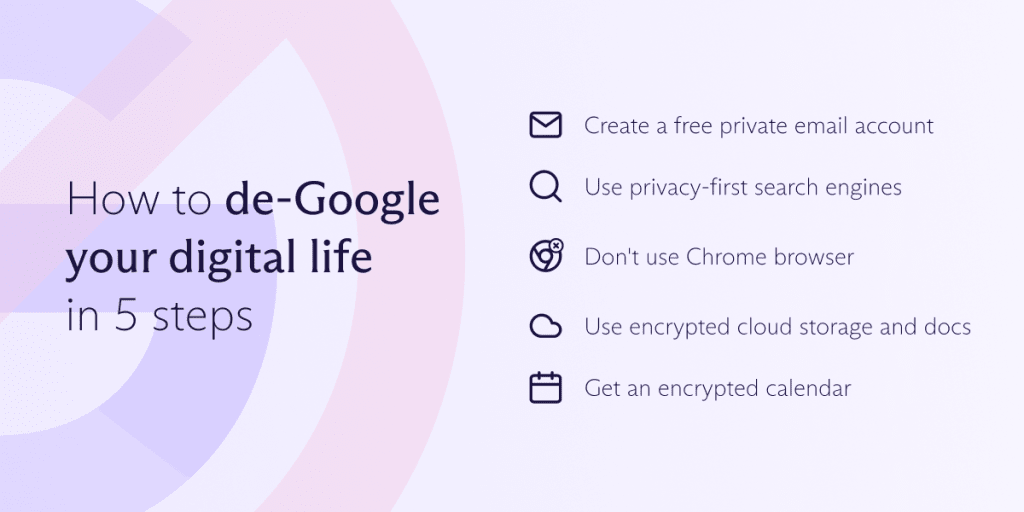
Start with email
One of the easiest changes you can make is to leave Gmail. We built Proton Mail as a privacy-first alternative offering end-to-end encryption to ensure only you and your recipient can read your emails. This tutorial about how to delete your Gmail will help you get started.
Here’s what Proton Mail offers to anyone who creates an account:
- Privacy first: Unlike Gmail, Proton Mail’s revenue model does not rely on advertising. Our security architecture keeps your data hidden even to us.
- End-to-end and zero-access encryption: Proton Mail secures your emails with end-to-end encryption and zero-access encryption, which means multiple protections are in place to ensure only you — the owner — keep your data.
- Free plan option: Everyone has the right to privacy, which is why we make Proton Mail available for free. You can upgrade to a paid account to access more features and support our fight for a better internet.
- Easy Switch tool: Our Easy Switch tool makes transitioning to Proton Mail simple, allowing you to back up your data and import existing emails, contacts, and calendars from Yahoo straight to Proton Mail.
Switch search engines
Google records every move you make online when you use its search engine, collecting mass amounts of personal data(nové okno). Privacy-focused search engines like Brave Search(nové okno), Qwant(nové okno), and Kagi(nové okno) don’t track you or collect your personal data to target you with ads.
Switch browsers
While Google Chrome is popular, it’s also known for collecting significant amounts of user data. Alternative browsers like Brave(nové okno), Tor Browser(nové okno), and Mozilla Firefox(nové okno) will allow you to keep your online activity private.
Use encrypted cloud storage and docs
It’s easy to move your data away from Google Drive to services like Proton Drive, which automatically secures your files with end-to-end encryption. That means no one can access them but you — not even Proton. With our Google Drive alternative, you remain in control even after you share a file with others by limiting who can access it with password protection.
And instead of Google Docs, you can use Docs, our online document editor built into Proton Drive. Our Google Docs alternative provides real-time collaboration features, version history, and more.
Switch calendars
When you use Google Calendar, the company can see all your events throughout the day, keeping a record of your life. Proton Calendar will help you manage your schedule, business meetings, and events, including on mobile devices. Your event data will be fully encrypted and protected.
Protect yourself with Proton
At Proton, giving you the ability to easily protect your privacy and most sensitive, valuable information is central to what we do. This contrasts greatly with Big Tech companies like Google, which exploits your personal data for profit. Over 100 million people trust us to secure their data.
Based in Switzerland, Proton is protected by some of the world’s strongest privacy laws, which are designed to safeguard your data from unauthorized access, including from governments.
Proton also goes beyond Google when it comes to account security. Along with 2FA and authentication logs, we also provide our high-security Proton Sentinel program with certain paid plans.
And if you’re a freelancer or operating a business, Proton has multiple plans to keep your business data secure. We offer a suite of end-to-end encrypted business solutions to protect your entire workspace, however big or small your business.
Making the move to Proton takes a few simple steps. Easy Switch is one of our unique features that allows you to seamlessly transition to your new Proton Mail inbox, back up your data, and import existing messages, contacts, and calendars from other email services, such as Gmail.
When you switch to Proton Mail, you are both protecting your most valuable data and helping build a better internet where privacy is the default.