Everything you need to know about cloud computing.
Before the internet, your computer performed all its computing tasks locally. Your computer’s CPU and memory (etc.) were used to process information that was also stored locally (for example, on your computer’s hard disk).
“The cloud”, on the other hand, refers to computers (known as cloud servers) that you can access over the internet and run software or store data for you remotely. These cloud servers, which are typically located in facilities known as data centers, perform tasks that your computer traditionally performed locally.
In many ways, “the cloud” is just a synonym for “the internet”, and the term actually originated from how the internet is often depicted in infographics.
Personal vs. business cloud computing
Although conceptually the same thing, the way businesses use cloud computing is very different from how individuals use the cloud. Personal uses of the cloud include:
- Email services
- Streaming media content (for example, from YouTube or Netflix)
- Social media
- Online productivity software (for example, Google Docs or Microsoft 365)
- Storage (such as Dropbox, Google Drive, or our own end-to-end encrypted Proton Drive(nové okno)).
For businesses, cloud computing offers many advantages over self-hosted solutions. It is very scalable, meaning that if more server power is needed, the company can simply rent more server space. It also saves on costs since it removes the need for expensive in-house IT departments and the need to buy expensive hardware.
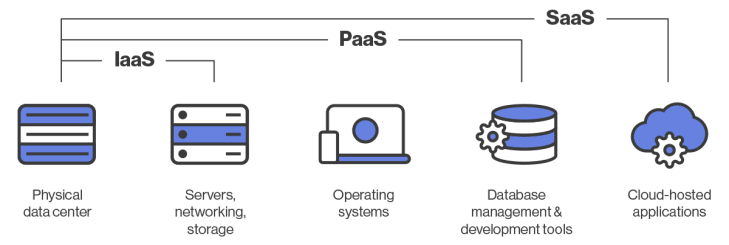
Popular cloud computing models used by businesses include:
- Software-as-a-Service (SaaS) — Applications are hosted on a remote server (for example, Slack or Mailchimp)
- Infrastructure-as-a-Service (IaaS) — Companies rent server space rather than using their own in-house servers.
- Platform-as-a-Service (PaaS) — Companies rent all the tools needed for building applications and the infrastructure required to run them (Microsoft Azure is a good example of this model)
Advantages of the cloud
Cloud computing offers a number of distinct advantages over traditional local computing:
Enables automatic backup of data
This is especially useful on devices that are easily lost, such as automatic photo backup to the cloud on smartphones.
Synced across devices
Your data is readily available on any of your devices, no matter where you are (so long as you have an internet connection).
Removes single point of failure
If a device fails, a hard disk is corrupted, a laptop is stolen, etc., and you don’t use the cloud, you will lose all the data on that device. However, if you save your data in the cloud, you can just pick up where you left off on another device.
Removes the need for high-end hardware
With most of the processing happening on remote computers, local hardware requirements are much lower.
Low-cost Chromebooks, where the entire operating system is basically just a browser that allows access to the internet, are arguably the most successful expression of this idea, but services such as XBOX Cloud Gaming and GeForce NOW allow you to play games that usually have very high hardware demands on low-end hardware.
Removes the need for expensive local storage solutions
Hard drives and other local storage solutions have become cheaper over the years, but they still cost money. More elaborate setups, such as network-attached storage(nové okno) devices, remain quite expensive for personal use.
For companies, the costs are even higher. Not only do they often need to buy physical servers and the infrastructure needed to run them, but they often also need to pay qualified staff to operate and maintain them.
In the long term, however, it’s probably still a good idea to have a local copy of your data.
Disadvantages of the cloud
Is data stored in the cloud safe from being lost?
It’s natural to be nervous about entrusting a third party to look after your data, but the risk is minimal. Server failures can and do occur, but most cloud services have multiple failsafe and redundancy mechanisms to ensure data is not lost, even if you experience some downtime.
It’s also worth bearing in mind that local solutions, such as hard drive storage, will inevitably fail at some point, so backing your data up to multiple locations is always a good idea.
Denial of service(nové okno) (DoS) attacks pose no threat to your data per se, but they are fairly common(nové okno) and might prevent you from accessing your data for potentially hours at a time. That said, situations where users are inconvenienced in this way remain rare.
The internet isn’t always available
One of the big benefits of cloud computing is that your data (or the service, etc.) is available any time and anywhere. But this is only true if you have an internet connection, which isn’t always the case.
Is data in the cloud secure?
Almost every cloud service in existence will secure your data with TLS when transferring it to and from their servers. They will also almost certainly encrypt it while stored on their servers to protect it from criminal hackers.
Imagine your data is placed in a strong box and secured with a lock. The lock will deter outsiders from accessing your data but won’t prevent whoever has the key to the lock from opening the strong box and accessing your data whenever they feel like it. Now think of the lock as encryption, which can be opened with the correct encryption keys.
Most cloud services encrypt your data using encryption keys they hold, which means they can access your data. Many cloud services routinely scan your data, often so they can fund nominally “free” services by selling your data for advertising purposes.
Google no longer scans your emails for advertising purposes, but it does scan them to offer features, such as Smart Labels and adding travel details to your Google Calendar. It also keeps a detailed list(nové okno) of your buying habits based on receipts sent to your Gmail account, even when your purchases are not from Google.
Even when data is not routinely scanned, if a cloud provider holds the encryption keys for your data, it can be compelled to hand your data over to third parties.
End-to-end encryption
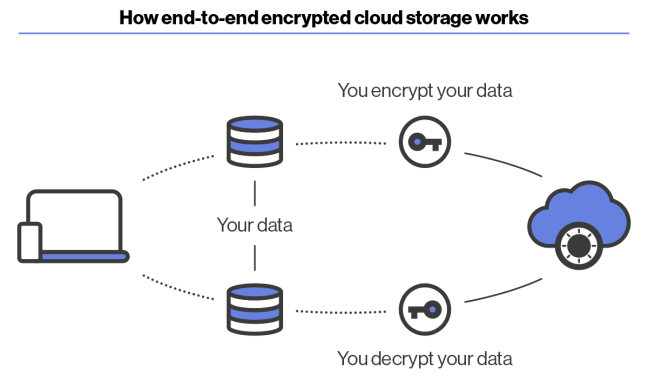
So how do you stop cloud services from being able to access your data in this way? The answer is to use end-to-end encryption (E2EE), where you encrypt your own data on your own device before uploading it to the cloud.
Files encrypted using strong end-to-end encryption are secure, even when stored on insecure platforms. If you use an insecure cloud storage service, such as Google Drive or Dropbox, it is a good idea to encrypt your data using trustworthy open-source software, such as VeraCrypt(nové okno) or Cryptomator(nové okno), before uploading it to the platform.
Proton Mail is currently the world’s most popular end-to-end encrypted email service, and we also offer Proton Calendar(nové okno), an E2EE cloud calendar service, to everyone who uses Proton Mail.
Learn more about Proton Calendar beta
In addition to this, we offer Proton Drive, a cloud storage service that transparently encrypts files on your device before uploading them to our cloud servers. This means we can never access your files, which can only be decrypted on your device using your private key (although you can share files and folders using a URL).
Learn more about the Proton Drive security model
You can sign up to Proton Drive for free. To access more storage and support our fight for a better internet, you can upgrade to a paid account.
How to backup to the cloud
Every cloud storage service has its own software that allows you to back up your files to the cloud. Proton Drive currently supports manual drag-and-drop backup in our web app — simply drop your files or folders into the browser window to upload them to the cloud.

You can also upload files using the Upload button and your usual file manager. Going forward, the Proton Drive app will support automatic folder syncing, with online-only access to follow.
Final thoughts
The day when most computers are simply low-end clients designed to run software and store data in the cloud is yet to come, but (as the popularity of Chromebooks shows) it is most likely the direction computing is heading.
For many, this is not always a good thing. The SaaS business model means you are actually renting software instead of owning it outright, which removes your control over what runs on your own system.
Cloud storage solutions work similarly. Instead of storing your data on your own hardware, you are entrusting it to third parties. This means these third parties have access to your data, allowing them to abuse it, monetize it, or hand it over to other parties should they wish.
These concerns are valid, but the benefits of the cloud are very compelling. Importantly, you can mitigate at least some of these concerns by using end-to-end encryption to ensure you always stay in control of your own data.
FAQ
3-2-1 backup is a popular strategy for ensuring data remains safe. It involves making three copies of all data:
– One copy is stored locally on your computer’s hard drive or SSD drive.
– Another copy is also stored locally but on different media, such as an external hard drive or an on-premises network-attached storage device. This protects your data if your computer is infected by a virus or affected by a disk failure.
– A third copy is backed up to the cloud to protect your data against fire, robbery, or any other event that results in data stored locally being destroyed.
As cloud storage becomes increasingly reliable and cheap, there is a strong argument that step two is no longer as necessary as it once was.
Unlike traditional software, which you install and run locally on your own computer, software as a service (SaaS) is software that is run “on the cloud”. In other words, it is run on third-party servers and delivered to your desktop over the internet through a client app (typically inside your browser window).
Although the SaaS business model is primarily used to sell software to businesses, Google Docs and Microsoft 360 are popular examples of SaaS products used by everyday people.