Proton Authenticator is an open-source two-factor authentication (2FA) authenticator app that generates time-based, one-time password (TOTP) codes on your device, letting you access online services with an extra layer of security. It uses the same well-tested encryption that secures the rest of the Proton ecosystem. Proton Authenticator is unique in that it was designed from the ground up to be available on almost every platform while preserving your privacy and giving you total ownership over your data.
Unlike other authenticator apps, Proton Authenticator secures your data with end-to-end encryption, even when you enable device sync.
This means Proton Authenticator prevents anyone, including Proton itself, from knowing which online services you have accounts with. This information, much like your emails or browsing history, can reveal a lot about you, and protecting it is essential to maintaining your privacy.
Proton Authenticator’s end-to-end encryption guarantees that all cryptographic operations, including key generation and data encryption, are performed locally on your device. This means that your unencrypted data cannot be accessed by Proton or shared with any third parties. Proton servers never have access to your unencrypted data, including your Proton Account password.
Encryption model
Proton Authenticator takes a comprehensive approach to ensuring maximum security and privacy for all user data. All cryptographic operations occur locally on your device, and any data transmitted to the server is always encrypted. Proton never has access to the plaintext keys required to decrypt user data, making it impossible for us to decrypt stored data, even if requested by third parties.
Proton Authenticator uses the same advanced encryption we use for authentication in Proton Mail. This includes using a hardened version of the Secure Remote Password (SRP) protocol that offers stronger security guarantees against man-in-the-middle (MITM) attacks. Our implementation means that even an attacker who can arbitrarily read, modify, delay, destroy, repeat, or fabricate messages between Proton and a user in an undetectable fashion is limited to checking only a single password guess per login attempt, the equivalent of trying to log in directly. This way, even if Proton is compromised and acts maliciously, password-equivalent information is never revealed.
Read more about Proton’s authentication encryption
Data encryption
Proton Authenticator allows you to securely store your 2FA codes, even if you don’t have a Proton Account. This means that the initial encryption process must be done entirely on your local device. Then, if you decide you want to use your Proton Account to sync your codes across devices, we can use the cryptographic keys stored on Proton servers to perform the sync.
Proton encryption begins with the Proton server providing the encrypted version of the root key that the Authenticator app uses to encrypt the user’s data. Each Proton user has an asymmetric User Key, and Proton encrypts this User Key on your device as follows:
- Accounts that use a single account password: Proton encrypts the User Key with a bcrypt hash of the account password and the account salt.
- Accounts that use our multiple account passwords feature: Proton encrypts the User Key with a bcrypt hash of the key password and the account salt.
Proton Authenticator uses bcrypt and an account salt to hash your password as an extra layer of protection against brute-force attacks. Even if a malicious actor got access to the Proton database, your account keys would be safe against brute-force attacks.
Once you enable sync, Proton Authenticator generates a 32-byte random Authenticator Key. This key is encrypted and signed with your User Key, ensuring only you can decrypt it — nobody (not even Proton) can read or create a new Authenticator Key. Once you have access to the Authenticator Key, all entries in Proton Authenticator are encrypted using 256-bit AES-GCM.
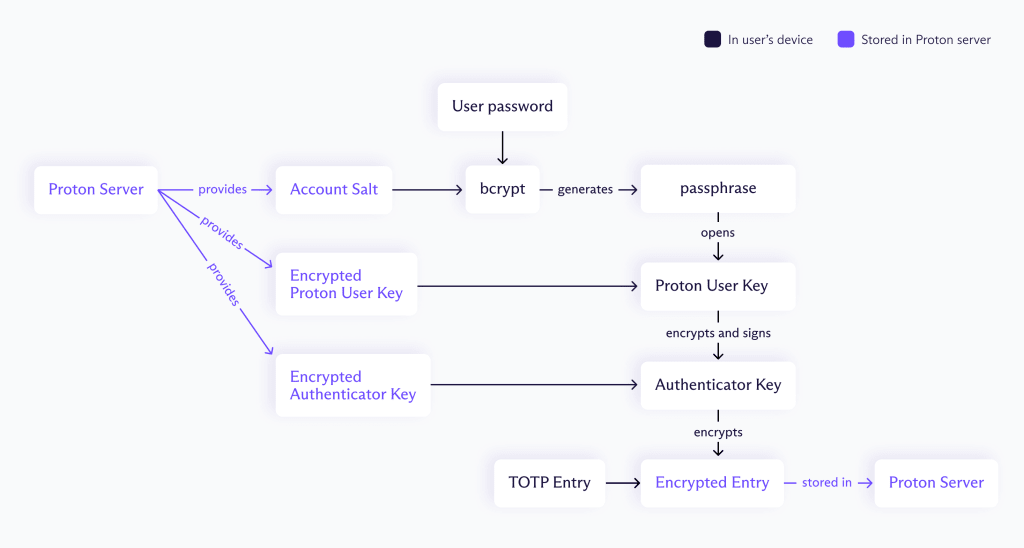
As Proton Authenticator doesn’t require a Proton Account, we also need a separate encryption schema that safely stores your data when it only exists on your device. In the end, the easiest way to implement this is by treating the Proton Account as a separate key provider. In the end, it looks like the following:

For the local key storage on your device, we rely on each system’s secure key storage providers:
- Android: We securely store the key in the Android Keystore(nouvelle fenêtre), which is then used to encrypt a Local Random Key that we store in the app’s protected filesystem. That key is used to symmetrically encrypt all Proton Authenticator entries on your device.
- iOS/iPadOS/macOS: We generate a Local Random Key and store it in the Keychain service(nouvelle fenêtre). That key is used to symmetrically encrypt all Proton Authenticator entries on your device.
- Windows: We generate a Local Random Key and store it in the Windows Credential Manager(nouvelle fenêtre). That key is used to symmetrically encrypt all Proton Authenticator entries on your device. If the connection to WCM is unavailable, we allow the user to encrypt their Local Random Key with a password.
- Linux: We generate a Local Random Key and store it in the available DBUS Secret Service. That key is used to symmetrically encrypt all the Proton Authenticator entries on your device. If no DBUS secret service is configured, we allow the user to encrypt their Local Random Key with a password.
Backup encryption
One of Proton Authenticator’s main strengths is that you always control your data. This includes allowing you to periodically back up your codes to your local device and set a password that encrypts this sensitive data.
To implement this secure local backup, we use the password you provided to derive a secure encryption key using Argon2 as a KDF (Key-Derivation Function). A KDF is used to generate cryptographic keys from secret inputs, like user-entered passwords, and its main purpose is to improve security by making it harder and more time-consuming for attackers to crack passwords. Using this encryption key generated from your password, we serialize all your entries and encrypt them to ensure your data remains securely encrypted, even if the backup is leaked. And by using well-known and open technologies, you are able to decrypt your data without using Proton Authenticator, allowing you to remain in control even if you decide to move to another authenticator app.
Security through transparency
Like all Proton services, Proton Authenticator is open source. Anyone can consult our source code to verify our security model. As with our other services, Proton Authenticator will also undergo regular independent security audits, and we will share these audit reports publicly as soon as they are available.
Finally, for interested security researchers, Proton Authenticator is eligible for Proton’s Bug Bounty program that offers awards of up to $100,000 for the discovery of bugs in Proton’s software.
