A cyberattack on national public employment service France Travail has exposed the personal data of as many as 43 million people(nowe okno).
The latest breach is the second major cybersecurity attack to happen in France in the past month, raising concerns about the threat of phishing – a common scam hackers use to trick people into sharing sensitive data or downloading malware that can lead to identity theft, credit card fraud, or other cybercrime.
In this article, we will explore what you need to know about the attack on France Travail and ways you can protect yourself and your private data from potential phishing scams.
- What to know about the France Travail attack
- How can your data be used after an attack?
- How to protect yourself
- Stay private with Proton
What to know about the France Travail attack
When it happened: On March 13, France Travail announced(nowe okno) it had fallen victim to a cyberattack that unfolded sometime between February 6 and March 5.
How many people were impacted: The National Commission for Information Technology and Liberties (CNIL) estimated that the attack led to the theft of personal data tied to nearly 43 million citizens. Passwords and bank details were not stolen in the breach, according to CNIL, but other sensitive information about job seekers was compromised.
What data was exposed: First and last names, social security numbers, dates of birth, email addresses, postal addresses, phone numbers.
How to know whether you were impacted: You may have been affected in the France Travail cyberattack if you are currently registered as a job seeker on France Travail, you have registered in the last 20 years, or you have a candidate page on their website.
Context: The recent attack on France Travail came a few weeks after a cybersecurity breach targeted third-party payment providers for mutual insurance companies in France. Hackers seized very similar data in a breach that impacted as many as 33 million people.
How can your data be used after an attack?
Every piece of personal information has a use in the toolbox of a hacker looking to commit cybercrime. The first step in defending yourself from such attacks is understanding how your own data can be used against you.
- Email address: An exposed email address is enough to fill your inbox with spam. Most of these unwanted messages are harmless, simply requiring you to clear your inbox. But some spam is more dangerous, as attackers use them in phishing scams to embed malicious links that appear to come from reputable sources.
- Name and telephone number: Used together, your name and phone number in the hands of a hacker can lead to fraudulent messages and calls. For example, you might receive a call or text from someone pretending to be a France Travail employee trying to inform you of a problem with your bank details that’s holding up your unemployment benefits. By clicking a link or downloading a document, you can download malware without knowing it.
- Postal address: A leaked postal address could play a role in a more elaborate scam where a scammer might call or email you and reference a fraudulent piece of mail they actually sent to your mailbox.
- Social security number and date of birth: These are keys that can give a hacker just enough credibility to gain access to your accounts.
How to protect yourself
If you have fallen victim to a data breach, don’t panic. Having the right frame of mind and following a few simple tips can help reduce the risks of further damage.
Check for suspicious senders
When you receive an email, the sender’s name that appears in the “From” field is not always information you can trust. In the example below, the sender’s email address is suspicious.
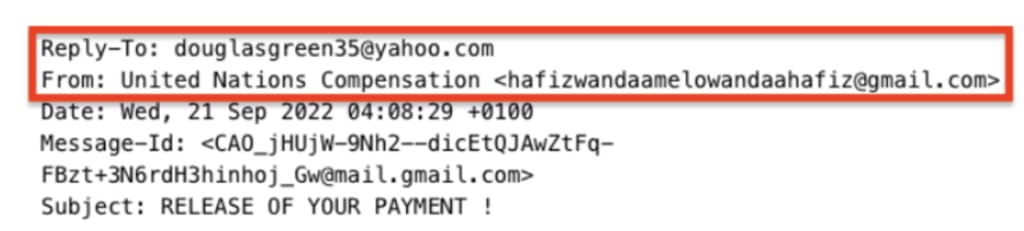
The gibberish Gmail address is a red flag that the intentions behind this email could be malicious, aiming to steal your data or money.
Confirm links
When you have the option to click on a link in an email, the URL is usually hidden behind a button or a phrase that links to a web page.
If you’re using a computer, however, you can hover your cursor over the link without clicking to check the URL. You can also right-click on the link and select “Copy link address” to paste it elsewhere.
You might notice, for example, that the URL in the email you received regarding an urgent delivery problem is www.post.fr/probleme/livraison instead of the official URL www.laposte.fr/outil/ used to track shipments. This is another warning signal that someone is targeting you in a scam.
Proton Mail makes this even easier on the web, your iPhone, and Android devices with a built-in link confirmation tool, which displays the full URL of links and asks you for confirmation before opening them.

Use email aliases
An effective way to defend against email attacks is to limit the number of people who know your real email addresses.
Proton Mail has launched hide-my-email aliases to help you keep your real email address private. A hide-my-email alias is simply another address that will automatically forward all emails sent to it to your main mailbox. You receive all messages, but your real email address and identity remain hidden.

If you buy something online and need to create an account or provide an email address to complete the order, you can use an alias instead of your real email address. If the alias is ever exposed in a data leak, you will be able to disable it while sparing your real email address. You might even use a different alias for each online service or account, so you can pinpoint exactly which ones have been compromised.
Stay private with Proton
Proton started as a crowdfunded project led by scientists who met at CERN (European Organization for Nuclear Research) and agreed their mission would be to create a better internet where privacy and freedom come first and everyone has control over their digital lives.
Proton uses end-to-end encryption to protect your emails, calendar, files stored in the cloud, passwords and login credentials, and your internet connection(nowe okno). Our security architecture is designed to keep your data invisible even to us, as our business model gives you more privacy, not less.
By migrating to an email service you can trust, you can help build a better internet where privacy is the default.





