You might have heard about quantum computers, a futuristic kind of computer that can perform certain operations far faster than today’s machines. You might have also heard that quantum computers will soon break encryption and expose everyone’s data.
In reality, quantum computers are already here, but they’re still pretty basic. Quantum computing technology is years or decades away from breaking current encryption standards, and its future applications are hypothetical. For now, your data is safe.
Even so, we take the potential threat seriously. Proton is not uniquely affected by this challenge, but we are uniquely equipped to confront it. We have a decade of experience developing and maintaining innovative open source cryptography. Our encrypted services protect the data of over 100 million accounts, with Proton Mail as the largest end-to-end encrypted email provider in the world. Many other services are built on the cryptographic libraries that we write and maintain. Because the security of our users and their data is our top priority, we’re always on the alert for new threats. Quantum computers are one of them.
To ensure we’re prepared, Proton is leading the standardization of quantum-safe encryption algorithms in OpenPGP, the open standard of encryption that is available for anyone to use via the free and open source libraries that Proton maintains, such as OpenPGP.js and Gopenpgp.
Standardization is important for two reasons. The first is that Proton remains committed to the open web. Email is one of the most successful open standards that has ever existed, and a core part of that success is interoperability. Open standards ensure our users can privately communicate with anyone who supports OpenPGP, and we will preserve this interoperability in the post-quantum world.
The second reason is safety. New cryptography is inherently risky, simply because it has not been battle-tested yet. Even when the underlying math works perfectly, mistakes in the implementation can greatly affect the security. Millions of users trust Proton every day with their communications and data, in some cases with their lives, and that is something that is never far from our minds.
For the last two years, we’ve been working alongside cryptographers from the German Federal Office of Information Security (BSI) and other developers to create a post-quantum public-key algorithm extension for the OpenPGP standard (you can read the proposed draft standard here(новое окно)). The details are quite technical, so this article will explain how the extension works in simple terms. But first, it’s important to understand how quantum computers work and why they might affect the way data is currently encrypted on the internet.
What are quantum computers?
The state of quantum computers
How Proton protects your data against quantum computers
What are quantum computers?
Unlike classical computers, which operate on bits, quantum computers operate on qubits. Bits can only have one value, either 0 or 1. But thanks to the properties of quantum particles, qubits can have a superposition of multiple values. (If you’re interested, the company IonQ has an in-depth visualization of how their quantum computers work(новое окно)).
Algorithms running on quantum computers can leverage qubits to solve some kinds of problems faster than classical computers can. One of these problems is of a sort relevant to the way encryption algorithms work, and you can try it for yourself:
Given 13 times 17, it’s relatively easy to compute the product (221). You could do it manually on a piece of paper. However, given a product (for example, 133), it’s more difficult to find its factors (7 and 19). This second operation requires trial and error until you find the integers that multiply to the desired product. This example uses very small numbers. The difficulty greatly increases when you’re working with 600-digit numbers that protect your data.
However, on a quantum computer, this problem can be more efficiently solved by Shor’s algorithm(новое окно). It speeds up the solution by removing the trial-and-error phase: By using superposition it can essentially check many values at once. If a quantum computer big enough to run this algorithm on 600-digit numbers appeared, it could be used to break widely deployed cryptography, such as elliptic curve cryptography and RSA, both of which we use at Proton and which are also core building blocks of fundamental web technology like SSL/TLS.
Learn more about elliptic curve cryptography at Proton
The state of quantum computers
Currently, quantum computers are not yet capable of breaking cryptography, or even solving the simple example above.
For instance, in 2019 IBM tried to factor the number 35 using its cutting-edge quantum computer and failed due to accumulating error, which stems from the main challenge of developing quantum computers: noise. Qubits need to be implemented using tiny particles, such as photons or ions (and even protons!), and when interacting with these particles, an experimental error is introduced.
Scientists are working on reducing noise, in particular by increasing the amount of qubits in a quantum computer, which makes the average measurement more reliable and reduces experimental error. However, building a larger quantum computer is not as simple as scaling classical computers.
In addition, the number of qubits required to break classical cryptography as it’s deployed today is many orders of magnitude more than what is currently feasible to achieve. To break currently deployed cryptography, scientists estimate a quantum computer would require at least 1 billion qubits. But today’s quantum computers only have a few hundred.
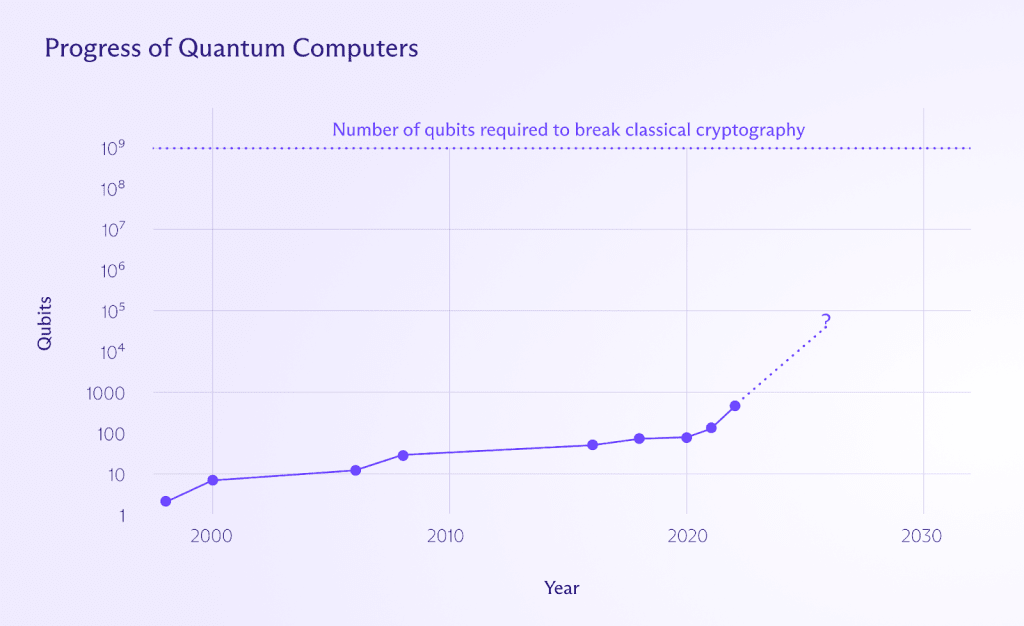
So even though it’s impossible to predict the future with certainty, we are likely many years away from a quantum computer that can break encryption.
But that doesn’t mean we should wait until that day comes to start preparing. We need to develop cryptography that can resist them today. And Proton already has a head start.
How Proton protects your data against quantum computers
At Proton, we use a standard called OpenPGP to secure your emails with end-to-end encryption. OpenPGP is the most widely used email encryption standard because it is battle-tested and safe. But it will need an update for the post-quantum era.
In the OpenPGP extension proposed draft standard(новое окно) we have been working on since 2021, we define how post-quantum encrypted messages should be encoded in an interoperable way. This means we’ll be able to protect all messages, not only between Proton accounts, but with other providers and users of OpenPGP as well.
Post-quantum cryptography has not yet had the amount of public analysis and scrutiny that classical cryptography has enjoyed. For this reason, we will use post-quantum cryptography in combination with classical cryptography. The post-quantum component will use lattice-based algorithms, as they offer good security and performance. For digital signatures, we have selected CRYSTALS-Dilithium in combination with Ed25519. For encryption, we chose CRYSTALS-Kyber in combination with X25519. Using a combination of classical and post-quantum algorithms offers the best of both worlds: Your data will be safe unless the attacker breaks both classical and quantum cryptography.
We will roll this out well before quantum computers become a threat, ensuring a smooth transition for the Proton community and everyone else using OpenPGP.
We are also working on standardizing the use of symmetric keys to encrypt OpenPGP messages in a proposed draft standard for persistent symmetric keys(новое окно).
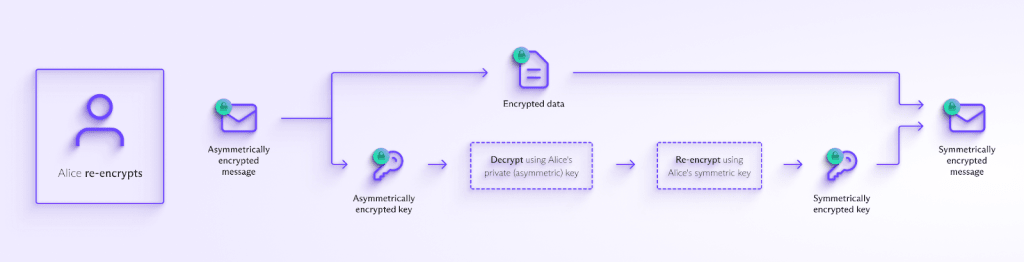
Alice re-encrypts the messages she received in the past to ensure they are safe from quantum computers.
When sending a message, it is necessary to encrypt it using asymmetric (public-key) cryptography, unless the sender and recipient have a shared key or password (such as in the case of password-protected emails). However, once the message has been received it can be re-encrypted symmetrically, using a key derived from the recipient’s password.
Besides being faster and more secure, this will also allow you to remove obsolete keys that are no longer used, without losing access to your messages.
Final thoughts
We don’t yet know when, if ever, quantum computers will appear that are strong enough to break classical cryptography. But if they do, Proton Mail encrypted email will be safe thanks to post-quantum cryptography, as will other Proton services which rely upon the same principles and technology.
We are not standardizing the use of these new algorithms by ourselves. At Proton, transparency and peer review are core values. That’s why we’re collaborating with the community and publishing our draft proposals for anyone to analyze and stress test in diverse applications. If you want to support this, you can find the current draft standard here(новое окно).