Email attachments may contain malware that criminals trick you into downloading, often leading to identity theft, credit card fraud, or other cybercrime. Here’s how to check if an attachment is safe.
In 2022, over 300,000 people in the US lost more than $50 million(новое окно) from phishing attacks. And sending you fake email attachments is one way fraudsters can trick you.
We explain the risks of different email attachments and how to tell when they’re safe to open.
Why are email attachments dangerous?
Which email attachments are generally safe to open?
Which attachments are less safe to open?
How to check if an attachment is safe to open
1. Check the sender is genuine
2. Never open suspicious attachments
3. Don’t open attachments marked as spam
4. Check the filename and file type
5. Keep your antivirus and OS updated
6. Use secure file sharing
7. Get email that checks for threats
Stay secure against attachments
Why are email attachments dangerous?
Scammers use malicious attachments or links to trick and defraud their victims in phishing emails. While opening a phishing email is generally not dangerous, responding to the message can be devastating.
Simply clicking on an attachment can run malicious code that compromises the security of your device, often exploiting vulnerabilities in software. If you download and open the attachment, you could automatically install malware(новое окно) like the following:
- Trojans (Trojan horses) may look like legitimate software, but once opened, they can take control of your device or spy on you.
- Viruses can replicate themselves and spread between devices and through networks, causing damage or stealing personal data.
- Ransomware may encrypt or otherwise lock your device and demand a ransom to unlock it.
- Spyware infects your computer or phone and monitors your activity, logging keystrokes and confidential data like usernames and passwords.
Once the malware is downloaded, fraudsters can use it to steal your personal details for identity theft(новое окно), clean out your bank account, or lock your device and demand a ransom.
Which email attachments are generally safe to open?
Before you click, download, or open any attachment, always check the message is from a trusted source. That’s because all files can contain malicious code or malware.
However, some files are less likely to be harmful than others. You can tell whether an attachment is likely safe by checking what type of file it is.
To find the file type, check the filename extension(новое окно) — the three- or four-letter suffix after the period, like document.doc or image.jpeg.
Here are some file types which are usually safe to open:
- Image files like .jpeg, .png, .gif, etc.
- Audio files like .mp3, .m4A, .wav, etc.
- Video files like .mp4, .mov, .avi, etc.
However, even these files can be harmful. Using a technique called steganography(новое окно), malware authors have hidden malicious code in image and audio files(новое окно), too.
Similarly, plain text files (.txt) can contain malicious scripts. But this code can’t be executed on its own, so .txt files aren’t usually dangerous.
Still, you need to watch out for double extensions. Malicious actors may create a filename like cash-for-you.txt.exe to trick you into thinking it’s a safe plain text file. Remember that only the last extension determines the file type, in this case, .exe, which could be dangerous.
Which attachments are less safe to open?
Here are some file types commonly used by scammers to hide their malware:
- Executable files like .exe and .msi: These can run or install software, including malware.
- Archive files like .zip and .rar: Used to compress and package multiple files, these types of files can also hide malicious scripts.
- Document files like .pdf and .rtf and especially Microsoft Office files like Word (.doc, .docx) and Excel (.xls, .xlsx): Be particularly careful with Office files containing macros (like .docm and .xlsm), which can be malicious.
- Batch or script files like .bat, .cmd, or .sh: These contain commands that will be run on your device when you open them.
- Disk image files like .img, .iso, or .dmg: These are used to copy disks and distribute software, including malware.
- JavaScript files (.js): These files contain code used to create interactive web pages but can also be used to run malicious scripts.
Of course, these are common file types, and far from all attachments of this kind will be malicious. That’s why you need to carefully check each attachment you receive before opening it.
How to check if an email attachment is safe to open
Before you open any email attachment, check the message and the attachment for signs of phishing. Here are the main red flags to look out for:
1. Check the sender is genuine
Never open an email attachment unless you’re 100% sure it’s from a trusted source.
Remember that hackers can spoof emails to appear like they’re from someone you know, like a friend or co-worker. If in doubt, call or text the sender to confirm.
Get Proton Mail, which uses digital signatures to verify the sender in end-to-end encrypted emails. A blue lock confirms that the message is from the sender and hasn’t been tampered with.
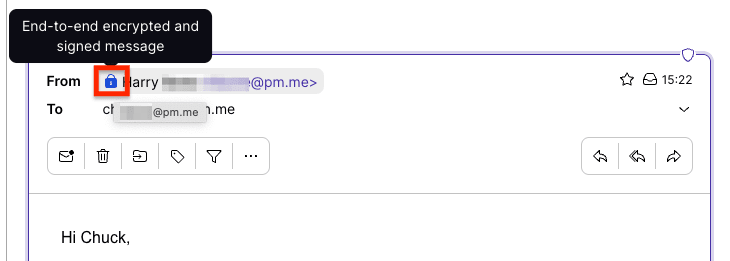
Moreover, Proton Mail warns you if an email shows signs of being spoofed.

If you have a custom email address (@yourdomain.com), Proton Mail has custom domain anti-spoofing to stop scammers from using your domain to spread spam or phishing emails.
2. Never open suspicious attachments
Beware of suspicious emails with urgent or unexpected requests, threats, prizes, or attachments. If you get a message with a “receipt” attached for something you haven’t bought, don’t download or open it.
In short, if you spot any signs of phishing, don’t download or open the attachment.
3. Don’t open attachments marked as spam
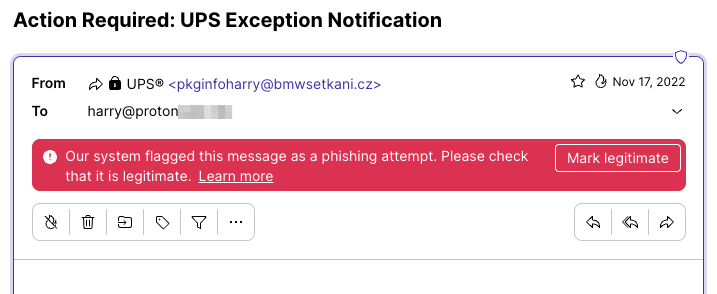
Don’t download or open any attachments if your email provider has flagged the message as spam. Proton Mail has smart spam detection that automatically filters spam into your spam folder.
Proton Mail further protects you with PhishGuard, which flags suspected phishing emails with a red banner.
4. Check the filename and file type
Take a close look at any attachments you receive. First, does the attached file fit the context of the message? Are you expecting “Miami vacation photos” from your friend Emma?
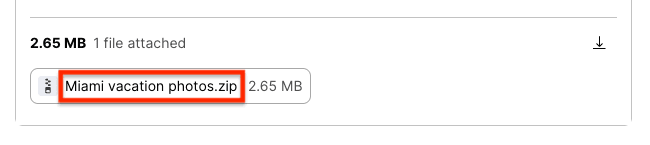
Second, check the file extension. This is a .zip file, a file type commonly used in phishing attacks, so double-check it’s from Emma before opening it.
And watch out for double file extensions like Miami vacation photos.txt.zip. Only the last file extension counts (here .zip), so don’t be fooled by the less dangerous-looking “txt” part of the filename.
5. Keep your antivirus and OS updated
Make sure you install reputable antivirus or internet security software and keep it up to date. Antivirus software can:
- Scan all files that you download, including emails attachments from webmail
- Check email attachments for malware if you’re using a desktop email client
- Make regular scans of your device for malware in case your device becomes infected
Remember that malware can exploit security vulnerabilities in software too. So keep your operating system, browser, and other apps updated to the latest versions with security patches.
6. Use secure file sharing
One way to avoid the risk of email attachments is to avoid using them altogether.
Get Proton Drive secure cloud storage and share end-to-end encrypted files with anyone using a secure link. That way, you can send files of any size to friends, family, or co-workers without worrying about attachments.
7. Get email that checks for threats
Many email providers, including Gmail, check attachments for viruses and malware, catching malicious files before they reach your mailbox. But often this means giving up your privacy as email services scan the contents of your communications.
Choose a private email service you can trust to keep you safe and your messages private.
Stay secure against attachments
Email attachments are one of the main ways fraudsters deliver malware, so beware of any attached files. By following the tips above, you can significantly reduce the risk of harm from malicious downloads.
But it’s easy to click by mistake, and we need all the help we can get to fight scams. We’ve designed Proton Mail to give you robust protection against malicious emails and attachments while keeping your communications private.
With Proton Mail, you get:
- Smart spam detection and custom filters to automatically filter spam
- PhishGuard phishing protection to flag potential phishing attacks
- Link confirmation to let you check potentially malicious links before clicking
- Address verification with digital signatures to verify senders in end-to-end encrypted emails
- Domain authentication warnings to flag possible spoofed addresses and custom domain anti-spoofing to protect your domain from being spoofed
- Aliases to hide your personal address from fraudsters
Proton Mail also includes Proton VPN(новое окно) and end-to-end encrypted Proton Calendar and Proton Drive, so you can share files securely without sending attachments.
In short, beware of attachments, get Proton Mail free, and stay secure!







