Confidențialitate securizată matematic
Criptografia lider de piață de la Proton Drive vă asigură că aveți cel mai înalt nivel de securitate și confidențialitate pentru datele personale.
Criptare de la un capăt la altul
pentru toate fișierele dvs.
Datorită criptării noastre bilaterale și cu acces zero, nimeni nu vă poate accesa fișierele fără permisiunea dvs.
Proton Drive este cu adevărat stocare privată în cloud. Criptarea noastră în ambele sensuri înseamnă că nimeni, nici măcar Proton, nu poate să vă acceseze fișierele și folderele sau să le vadă numele fără permisiunea dvs.
Proton Drive acceptă, de asemenea, partajare de fișiere criptată de la un capăt la altul. Doar persoanele cărora le partajați legătura web sau parola vă pot accesa fișierele, păstrându-vă controlul.
Criptarea simplificată
Criptarea avansată în amabele sensuri la Proton Drive are loc automat și în fundal. Nu aveți nevoie de cunoștințe tehnice pentru a utiliza Proton Drive și nu trebuie să gestionați, să partajați sau să distribuiți chei de criptare publice și private. Pur și simplu încărcați fișierele și acestea vor fi criptate automat, păstrându-le private și în siguranță.
Libertatea necesită intimitate
Confidențialitatea este temelia libertății democratice. Vă oferă liniștea sufletească de a trăi viața pe care o doriți și permite societății să funcționeze liberă de manipulare. În lumea de astăzi, protejarea datelor dvs. este o parte esențială a confidențialității.
Utilizați Proton Drive pentru a vă proteja viața digitală de influențe nedorite.
Criptați fișierele și ocoliți cenzura
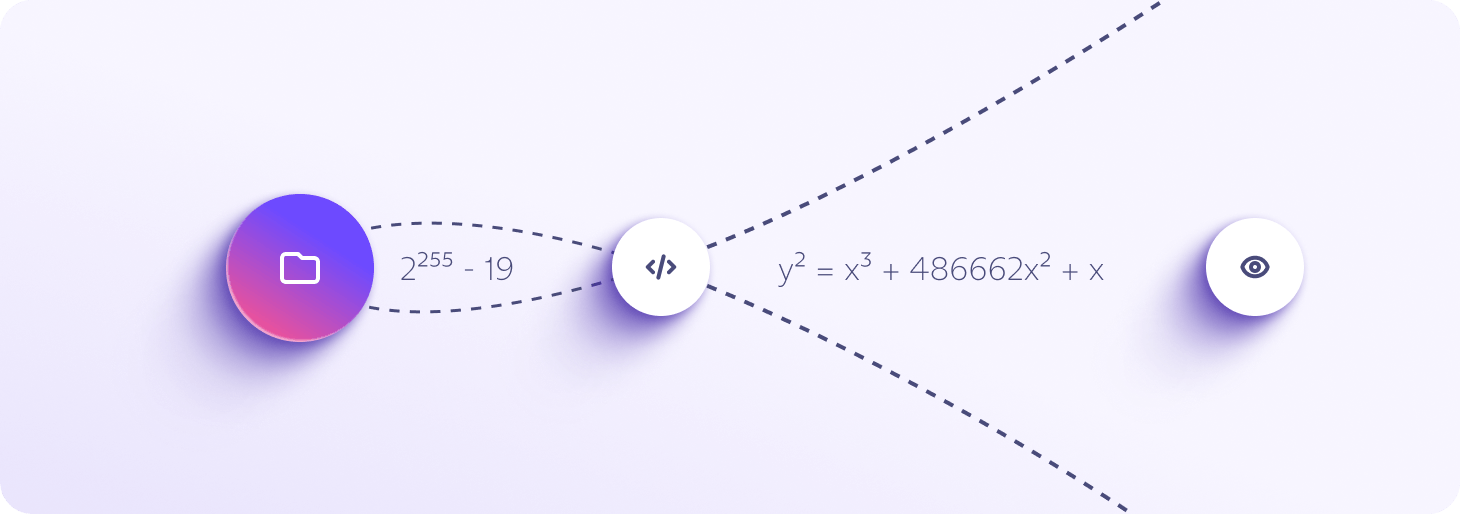
Criptografie bazată pe curbe eliptice
Proton Drive utilizează cea mai recentă criptografie de înaltă performanță cu curbe eliptice (ECC Curve25519) pentru a vă securiza fișierele. Această criptare avansată este sigură împotriva tuturor atacurilor cunoscute și necesită mai puțină putere de calcul.

Standard OpenPGP
Proton Drive se bazează pe standardul de criptare de la un capăt la altul OpenPGP, cu cod sursă public și testat intens. Fiecare utilizator Proton are o cheie publică și o cheie de criptare privată. Fișierele dvs. sunt criptate cu cheia dvs. publică și pot fi decriptate doar folosind cheia dvs. privată. Deoarece doar dvs. aveți acces la cheia dvs. privată, doar dvs. vă puteți citi datele.
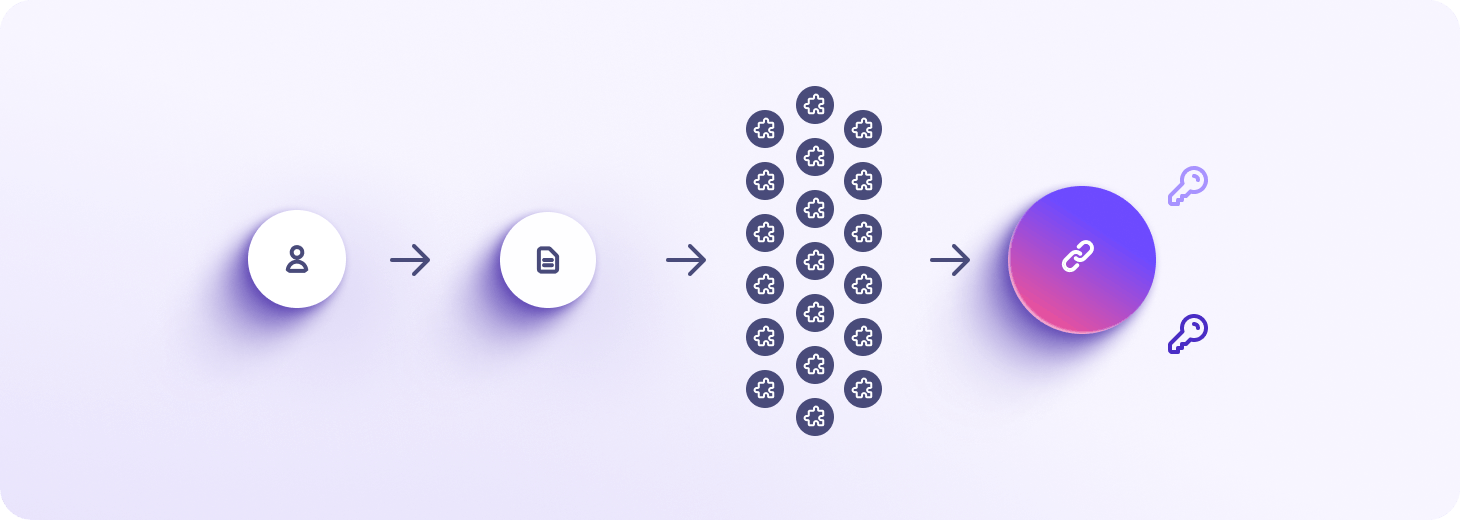
Criptare bilaterală pentru fișiere mari
Tehnologia unică a lui Proton Drive permite criptarea de înaltă performanță, bilaterală la client, cu fișiere mari, prin împărțirea fișierelor mari în bucăți de 4 MB. Fiecare bucată este semnată cu un hash pentru a preveni eliminarea sau reordonarea. Când deschideți sau descărcați un fișier, algoritmii noștri de transfer și decriptare de fișiere se asigură că datele vă sunt reconstruite rapid în ordinea corectă.

Semnături digitale
O parte esențială a menținerii securității este să știți dacă datele dvs. au fost falsificate. Proton Drive utilizează semnături criptografice pentru a verifica autenticitatea fișierelor și folderelor dvs., ceea ce înseamnă că veți detecta imediat orice încercare de a falsifica fișierele dvs.
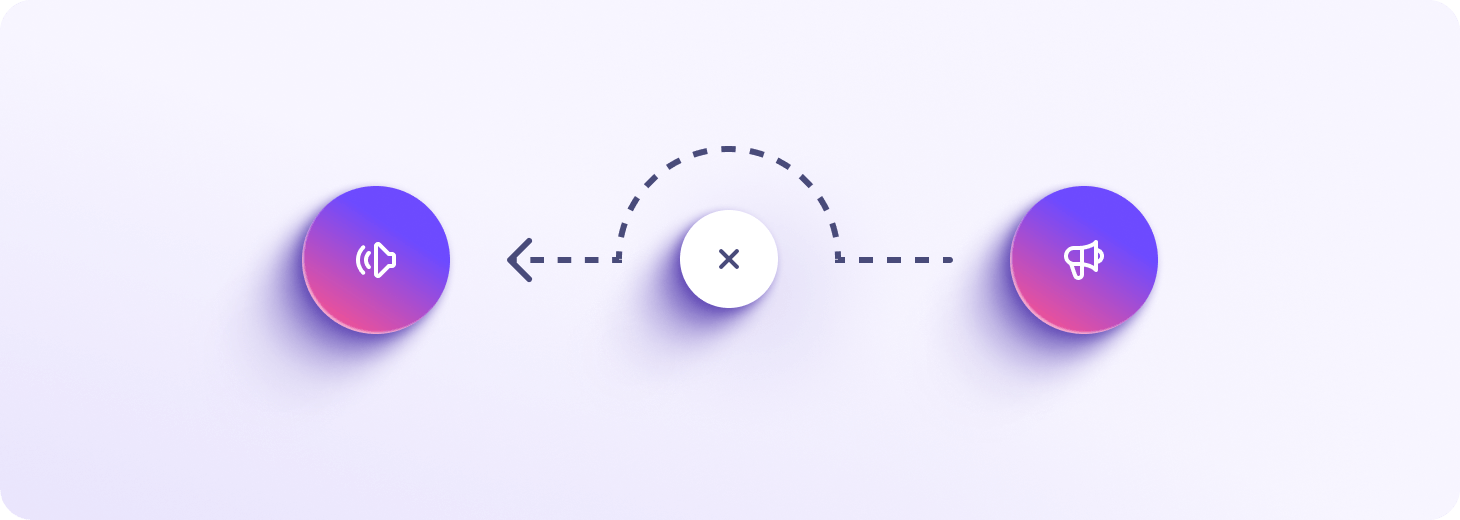
Învingeți cenzura cu direcționarea alternativă
Protejarea libertății digitale este esențială pentru misiunea noastră. Dirijarea alternativă vă permite să accesați Proton Drive chiar dacă este blocat de guvern sau de furnizorul de internet. Această funcție detectează automat când conexiunea la internet este cenzurată și vă redirecționează traficul, astfel încât să vă puteți accesa întotdeauna contul Proton.
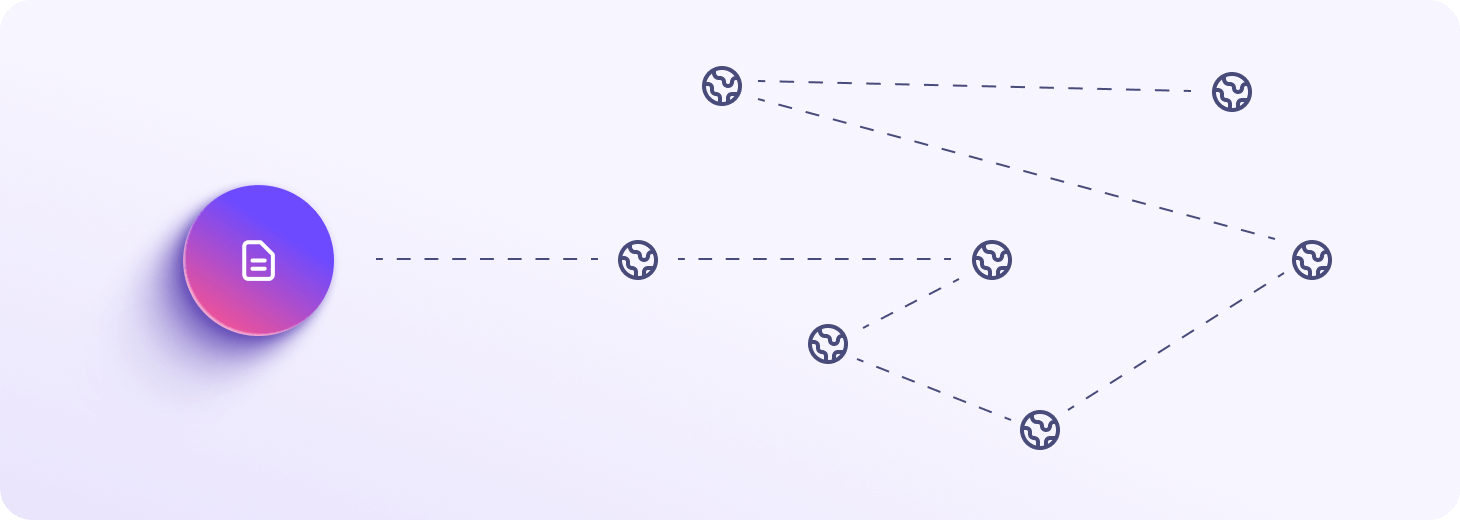
Site onion Tor
Puteți accesa Proton Drive folosind rețeaua de anonimitate Tor pentru a ocoli cenzura avansată sau pentru confidențialitate sporită. Vă puteți conecta la site-ul nostru onion Proton Drive folosind browserul Tor (sau caracteristica Tor over VPN a Proton VPN), care vă direcționează conexiunea prin noduri Tor, protejându-vă și mai mult activitatea în timp ce sunteți conectat de supraveghere.
Cu sursa publică și auditat pentru securitate
Ca organizație fondată de oameni de știință, credem în transparență și evaluare inter pares, motiv pentru care am făcut ca toate aplicațiile și bibliotecile noastre de criptare să aibă cod sursă public. Acest lucru permite cercetătorilor și experților în securitate să verifice independent dacă aplicațiile și criptarea noastră sunt la fel de sigure precum susținem.
Program de recompensă pentru găsirea de erori
Securitatea comunității Proton este prioritatea noastră cea mai mare și operăm un program de recompense pentru remediere erori pentru a obține îmbunătățiri de securitate și criptare de la comunitate. Oferind recompense pentru îmbunătățiri de securitate, motivăm cercetătorii în securitate din întreaga lume să ajute la îmbunătățirea Proton Drive.
Auditat pentru securitate
Știm că nu toată lumea are timpul sau capacitatea de a citi paginile de cod, motiv pentru care Proton are în mod obișnuit experți independenți să inspecteze codul aplicațiilor noastre pentru vulnerabilități. Proton Drive a fost auditat de Securitum, un important auditor european de securitate. Publicăm întotdeauna aceste rapoarte de audit, astfel încât să puteți vedea o evaluare profesională de la terți a aplicațiilor noastre.
Aflați mai multe despre securitatea în cloud

Poate fi atacată stocarea în cloud?
Cât de sigure vă sunt fișierele depinde de tipul de criptare utilizat de furnizorul personal de servicii cloud.

Ce este stocarea în cloud cu informații zero?
Stocarea în cloud cu informații zero este cea mai sigură modalitate de a stoca fișierele online.

Care este cel mai sigur mod de a stoca documente?
Există mai multe moduri în care vă puteți stoca fișierele. Aflați patru dintre cele mai sigure metode.

Confidențialitate elvețiană
Proton are sediul în Elveția, ceea ce ne oferă multe protecții legale de confidențialitate. Elveția este neutră politic, în afara jurisdicției SUA și UE, și nu este membră a niciunui acord de partajare a informațiilor Five Eyes sau Fourteen Eyes(fereastră nouă). Criptarea în amble sensuri este protejată de legea elvețiană, iar în conformitate cu articolul 271 din Codul penal elvețian, lui Proton îi este interzis să partajeze date cu autoritățile străine.
Funcții suplimentare de securitate
Securitatea este un concept vast. Pe lângă criptarea de la un capăt la altul, aplicăm și o securitate operațională de top pentru a asigura criptarea datelor dvs. în tranzit și în repaus.
Securitate la nivel de hardware
Am investit enorm în deținerea și controlul propriului nostru hardware de server și rețea în Elveția și Germania - ambele țări cu legi puternice privind confidențialitatea. Centrele noastre de date sunt situate în locații foarte sigure care necesită acces biometric.
La nivel de sistem, serverele noastre utilizează hard disk-uri complet criptate cu mai multe straturi de parole, păstrând securitatea datelor chiar dacă infrastructura noastră fizică este încălcată sau furată.
DNS CAA
Pentru a crește securitatea conexiunii dvs. Proton folosește Autorizarea autorității de certificare DNS. Acest lucru înseamnă că autoritățile de certificare vor recunoaște Proton înainte de a emite certificatul pentru a dovedi valabilitatea cheii dvs. publice.
Acest lucru reduce riscul ca certificatele Proton ilegitime să fie emise și utilizate pentru a vă compromite securitatea.
Securitate și monitorizare 24/7
Proton are o prezență globală într-o duzină de țări, permițându-ne să operăm 24/7/365. Echipele noastre de securitate monitorizează continuu infrastructura noastră pentru alerte de securitate și iau măsuri proactive atunci când detectăm atacuri împotriva conturilor de utilizator specifice.
Aceasta include avertizarea dvs. dacă un atacator avansat vă vizează contul și vă blocăm automat contul dacă bănuim că altcineva a obținut accesul la acesta.
Proton Drive a fost creat de echipa care a creat Proton Mail, cel mai mare serviciu de e-mail criptat din lume
Peste 100 de milioane de oameni și unele dintre cele mai mari organizații din lume s-au înscris la Proton.