Your privacy, secured by math
Proton Drive’s market leading cryptography ensures that you have the highest level of security and privacy for your data.
End-to-end encryption
for all your files
Thanks to our end-to-end and zero-access encryption, no one can access your files without your permission.
Proton Drive is truly private cloud storage. Our end-to-end encryption means no one, not even Proton, can access your files and folders or see their names without your permission.
Proton Drive also supports end-to-end encrypted file sharing. Only the people you share the link or password with can access your files, keeping you in control.
Encryption made easy
Proton Drive’s advanced end-to-end encryption all happens automatically and in the background. You don’t need any technical knowledge to use Proton Drive, and you don’t need to manage, share, or distribute public and private encryption keys. Simply upload your files and they’ll automatically be encrypted, keeping them private and safe.
Freedom requires privacy
Privacy is the bedrock of democratic freedom. It gives you the peace of mind to lead the life you wish and enables society to function free from manipulation. In today’s world, protecting your data is a core part of privacy.
Use Proton Drive to protect your digital life from unwelcome influence.
Encrypt your files and bypass censorship
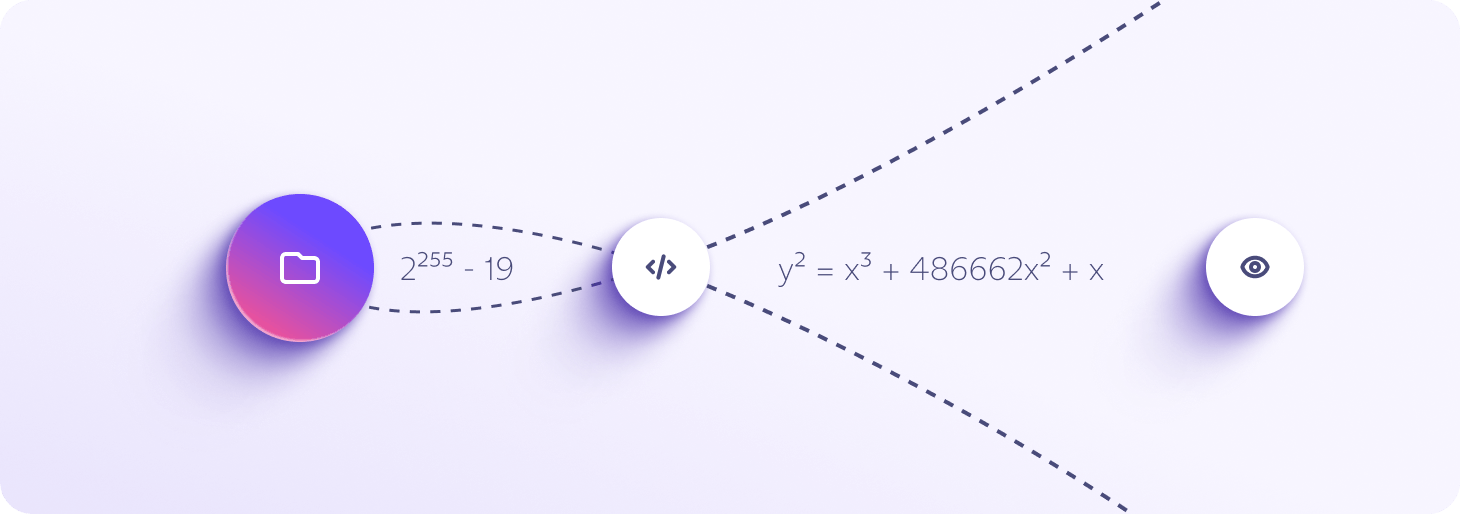
Elliptic curve cryptography
Proton Drive uses the latest, high-performance elliptic curve cryptography (ECC Curve25519) to secure your files. This advanced encryption is secure against all known attacks and requires less computational power.

OpenPGP standard
Proton Drive relies on the open-source and battle-tested OpenPGP end-to-end encryption standard. Each Proton user has a public key and a private encryption key. Your files are encrypted with your public key and can only be decrypted using your private key. Because only you have access to your private key, only you can read your data.
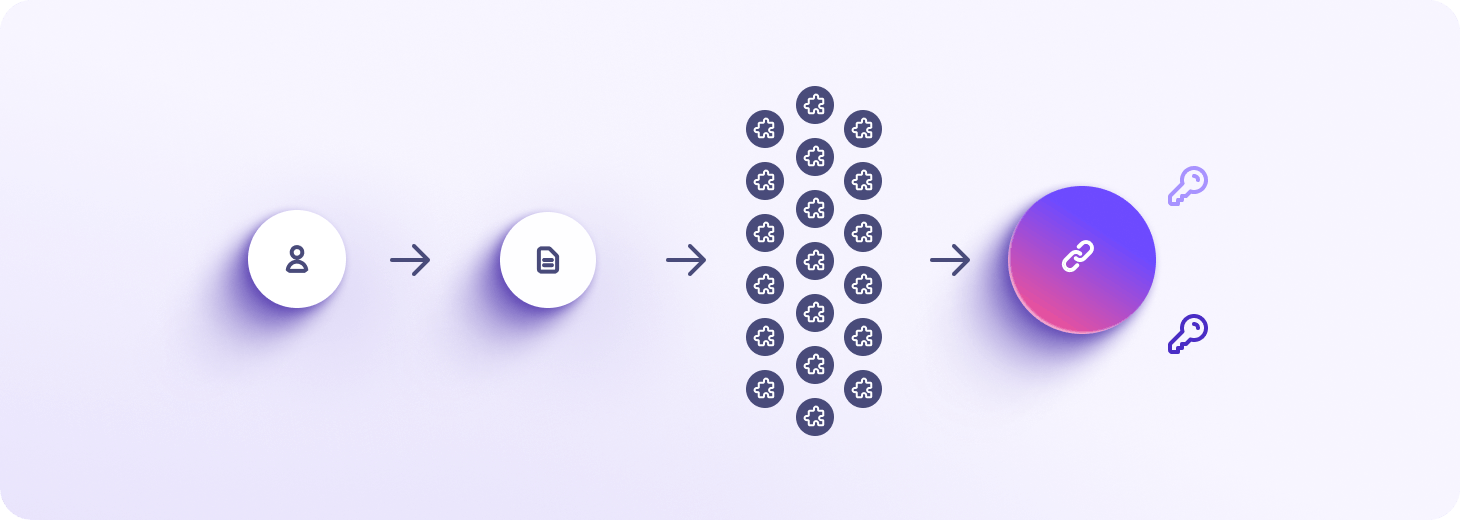
End-to-end encryption for large files
Proton Drive's unique technology enables high-performance, client-side end-to-end encryption with large files by splitting large files into 4 MB chunks. Each chunk is signed with a hash to prevent removal or reordering. When you open or download a file, our file transfer and decryption algorithms ensure your data is rebuilt quickly in the correct order.

Digital signatures
An essential part of maintaining your security is knowing if your data has been tampered with. Proton Drive uses cryptographic signatures to verify the authenticity of your files and folders, meaning that you’ll immediately detect any efforts to tamper with your files.
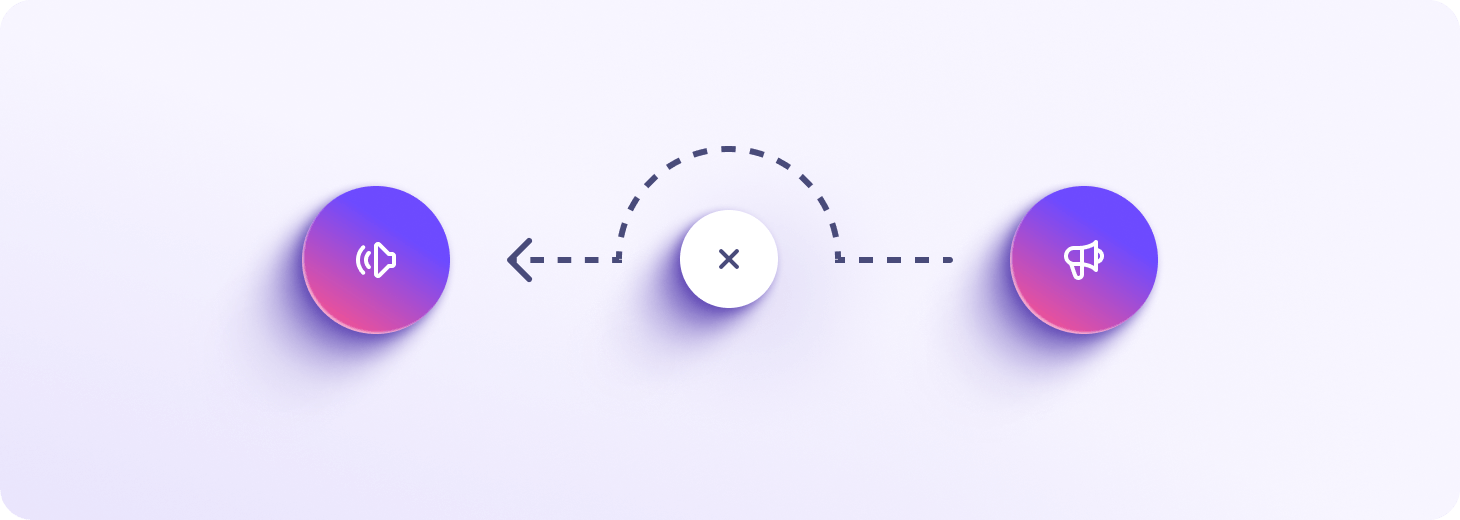
Beat censorship with alternative routing
Protecting digital freedom is central to our mission. Alternative routing lets you access Proton Drive even if it’s being blocked by your government or internet provider. This feature automatically detects when your internet connection is being censored and re-routes your traffic so that you can always access your Proton Account.
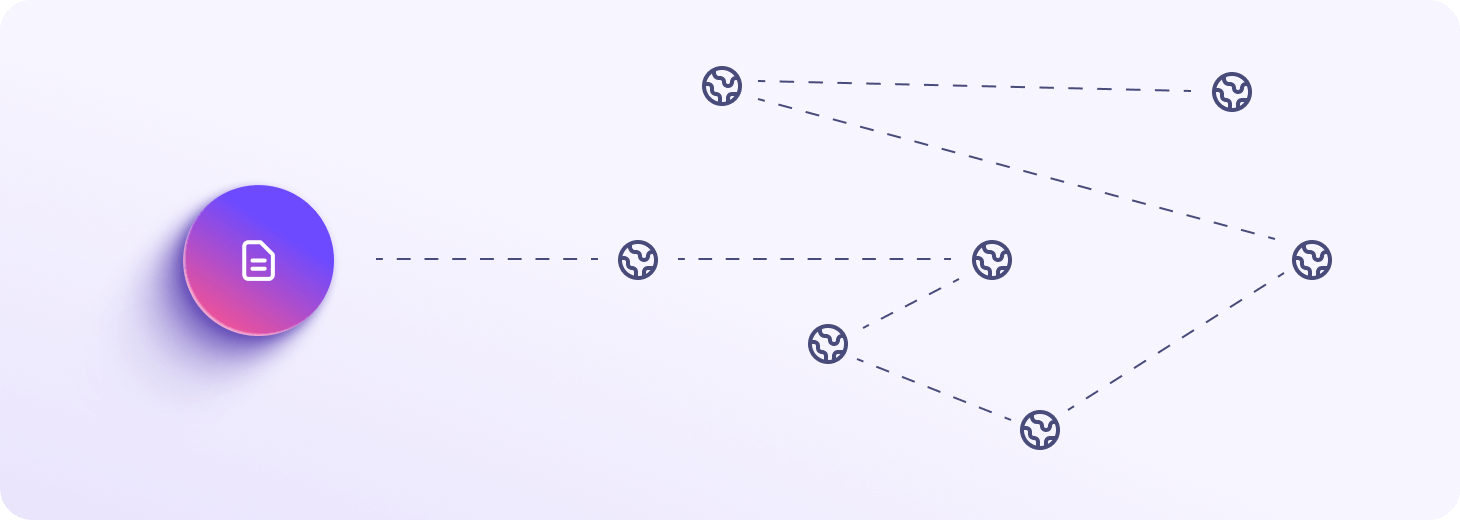
Tor onion site
You can access Proton Drive using the Tor anonymity network to bypass advanced censorship or for extra privacy. You can connect to our Proton Drive onion site using the Tor Browser (or Proton VPN’s Tor over VPN feature), which routes your connection through Tor nodes, further protecting your online activity from surveillance.
Open source and audited for security
As an organization founded by scientists, we believe in transparency and peer review, which is why we’ve made all our apps and encryption libraries open source. This allows researchers and security experts to independently verify our apps and encryption are as secure as we claim.
Bug bounty program
The security of the Proton community is our highest priority, and we operate a bug bounty program to crowdsource security and encryption improvements. By offering rewards for security improvements, we incentivize security researchers worldwide to help improve Proton Drive.
Audited for security
We know not everyone has the time or ability to read through pages of code, which is why Proton routinely has independent experts inspect our apps’ code for vulnerabilities. Proton Drive has been audited by Securitum, a leading European security auditor. We always publish these audit reports so you can see a professional third-party evaluation of our apps.
Learn more about cloud security

Can the cloud be hacked?
How safe your files are depends on the type of encryption used by your cloud service provider.

What is zero-knowledge cloud storage?
Zero-knowledge cloud storage is the most secure way to store your files online.

What is the most secure way to store documents?
There are multiple ways you can store your files. Learn four of the safest methods.

Swiss privacy
Proton is based in Switzerland, which provides us with many legal privacy protections. Switzerland is politically neutral, outside US and EU jurisdiction, and isn’t a member of any Five Eyes or Fourteen Eyes intelligence-sharing agreements(new window). End-to-end encryption is protected under Swiss law, and under Article 271 of the Swiss Criminal Code, Proton is prohibited from sharing data with foreign authorities.
Additional security features
Security is a wide-ranging concept. Alongside our end-to-end encryption, we also apply industry-leading operational security to ensure the encryption of your data in transit and at rest.
Hardware-level security
We have invested heavily in owning and controlling our own server hardware and network in Switzerland and Germany - both countries with strong privacy laws. Our data centers are located at highly secure sites that require biometric access.
On a system level, our servers utilize fully encrypted hard disks with multiple password layers, preserving data security even if our physical infrastructure is breached or stolen.
DNS CAA
To increase the security of your connection. Proton uses DNS Certificate Authority Authorisation. This means certifying authorities will recognize Proton before issuing the certificate to prove your public key’s validity.
This reduces the risk that illegitimate Proton certificates are issued and used to compromise your security.
24/7 security and monitoring
Proton has a global presence in a dozen countries, allowing us to operate 24/7/365. Our security teams continuously monitor our infrastructure for security alerts and take proactive action when we detect attacks against specific user accounts.
This includes warning you if an advanced attacker is targeting your account and automatically locking your account if we suspect somebody other than you has gained illicit access.
Proton Drive was built by the team behind Proton Mail, the world’s largest encrypted email service
Over 100 million people and some of the world’s largest organizations have signed up with Proton.