Zero-knowledge cloud storage is the most secure way to store files and folders online. It uses strong encryption protocols, including end-to-end encryption, so that no one but you can access your data.
Many popular cloud storage services, such as Google Drive and Dropbox, don’t use zero-knowledge encryption and retain access to your files. Therefore, to protect your privacy and improve your security, we recommend cloud storage services that use zero-knowledge encryption by default.
This article explains how zero-knowledge cloud storage works and why it’s more secure than alternative storage methods. We also describe the benefits, use cases, and what to consider when choosing a cloud storage service.
What is zero-knowledge encryption?
How zero-knowledge cloud storage works
Is this the same thing as zero-access encryption?
Benefits of zero-knowledge cloud storage
How to choose a cloud storage service
The Proton Drive security model
What is zero-knowledge encryption?
Zero-knowledge encryption is a method of storing data in the cloud so that only the owner of the data can access it. It’s named “zero-knowledge” because it makes it impossible for the service provider to access, decrypt, or otherwise interact with the files it handles and stores on its servers — they have zero knowledge about those files. When applied to cloud storage providers, the benefit is that they can never scan your files.
This is different from the encryption systems that many well-known cloud storage providers use. Google Drive, Dropbox, and others encrypt your files while they’re being uploaded and while they’re stored, but they always have the ability to decrypt your files. They may hand them over to third parties (such as to law enforcement) or use your data to profile you for advertising purposes.
You can use zero-knowledge encryption for different applications, including cloud storage, email, calendars, and password managers.
Zero-knowledge encryption doesn’t refer to a specific protocol but rather to a cryptographic system that ensures the data is encrypted on the user’s device before being sent to the server and can only be decrypted on the user’s device. Different providers may use various combinations of encryption standards and protocols to accomplish zero-knowledge encryption, depending on their specific use case. For example, you may want to send data to others or simply store it in the cloud as a file backup.
Broadly, there are two scenarios when data needs to be protected: when it’s in transit and when it’s at rest.
Data in transit
Data in transit is information on the move: It’s traveling across the internet on its way from server to server until it reaches its destination. You may be sending an email to a colleague or uploading a file to the cloud. Either way, the data must be encrypted before it leaves your device so that no one on the same network can access it.
To be “zero-knowledge” this must be accomplished with end-to-end encryption so that no other parties can access the data except you and anyone you choose to share your files with.
Data at rest
Data at rest is information stored on a server. This includes your emails stored in your webmail provider, files in your cloud drive, and logins in your password manager. This data can be zero-knowledge encrypted or not, depending on whether the service provider has the keys to decrypt your data on its servers.
Services that use zero-knowledge encryption secure your data in such a way that only you can decrypt it using your private key. For example, Proton uses public-key cryptography to ensure we never have access to your plaintext data.
How zero-knowledge cloud storage works
With zero-knowledge cloud storage, your data is encrypted on your computer or mobile device before it’s transmitted to the server.
Most cloud storage providers use multiple forms of cryptography that work together to secure files and to allow you to securely share with others. To illustrate the concept, we’ll use a simplified scenario with PGP, a common encryption standard.
Let’s say you want to upload a small document to a cloud server without the server having access to it.
- To accomplish this, your cloud storage service first generates a pair of numerical keys on your device when you create your account. One is a public key that anyone can access, and one is a private key that no one has but you (your account password unlocks it). The keys are mathematically related so that only the private key can decrypt what its corresponding public key has encrypted.
- Next, your service provider uses your public key to convert your document into unreadable ciphertext. Once this happens, only your private key can decrypt the document back into readable plaintext.
- Now the encrypted document can be transmitted to the server for storage. If you want to access it later, you can log in to your account and retrieve the document, decrypting it on your device using your private key.
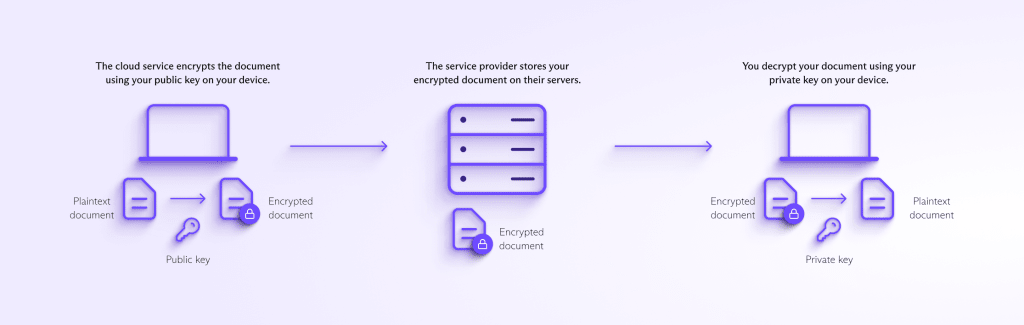
With modern cloud storage providers, all of this happens automatically in the background. You don’t need to worry about manually encrypting and decrypting your documents or managing your keys. The service will take care of this for you.
This is an oversimplification
In reality, the computational power required to encrypt and decrypt even a small document is too much for PGP to do the job alone at scale. Cloud storage providers typically only use your public and private keys to control security for another key, which can more quickly encrypt and decrypt large files.
We go into more depth about the Proton Drive security model below if you’re interested in the details.
Is this the same thing as zero-access encryption?
Proton Drive uses zero-knowledge encryption. Additionally, you may see us refer to zero-access encryption, which is a term we use at Proton to describe one of the ways we secure data at rest, including emails sent to Proton Mail accounts from non-PGP sources, such as Gmail or Outlook.
Because these email providers do not use end-to-end encryption, incoming data from those services is not encrypted. Upon receipt, Proton instantly applies zero-access encryption to the data by encrypting it in your account using your own public key. After that, only you can decrypt it using your secret private key.
Benefits of zero-knowledge cloud storage
Cloud storage has many benefits over local storage, but it also presents privacy and security challenges. However, using strong encryption can mitigate most of these issues.
Protection against data breaches
While rare, a cloud storage data breach can be devastating. The kinds of data people store tend to be sensitive and personal, such as photos or financial documents. End-to-end encrypted cloud storage prevents any data breach from affecting you on the server side. (Client-side breaches are more common, and you can mitigate that risk with good account security.)
Keep your files private
Google, Microsoft, Dropbox, and many other cloud storage providers have access to your files and regularly scan them. If you believe companies should respect your privacy and not have access to your photos, documents, and other files, you may want to consider switching to an end-to-end encrypted storage provider. Another solution is to join a growing movement of users learning how to deGoogle their lives.
Take action now: DeGoogle your life for $1
Secure collaboration and file sharing
You can use end-to-end encrypted cloud storage to securely share files and folders with your colleagues. For example, if you are working with a lender to secure a loan, instead of sending highly sensitive financial documents via email, you can create an encrypted folder in the cloud where both parties can upload and access the relevant files. You can also transfer large files with link sharing.
Regulatory compliance
Privacy regulations in many parts of the world effectively require companies to use encryption. If you’re obliged to comply with laws like HIPAA or the GDPR, you may need to use encrypted cloud storage.
How to choose a cloud storage service
Unfortunately, many Big Tech companies force you to use their own cloud storage services. For example, the iPhone may automatically back up your files in iCloud, and Gmail automatically uploads large attachments to Google Drive.
If you decide to actively take control of your data, choosing your own cloud storage provider is a good place to start. There are several factors you should consider:
- Storage space — Depending on how much storage space you need, you’ll want to look at the storage limits for the various providers.
- Privacy and security — Most popular storage providers do not use end-to-end encryption or zero-access encryption. And unfortunately, they don’t always make that clear. If you don’t see explicit promises on a provider’s website that it uses end-to-end encryption, then it’s safe to assume it doesn’t.
- Price — Remember, if the service is free, then you’re the product. However, many cloud storage providers, such as Proton Drive, offer a certain amount of storage space for free, after which you need to upgrade to increase your data limits.
- Other perks — At Proton, your drive subscription automatically comes with email, calendar, VPN, and (soon) a password manager. It’s worth considering the value of any extra services the company offers.
The Proton Drive security model
In this section, we’ll give a slightly more in-depth explanation of how cloud storage encryption works. Given that all cloud storage providers use different systems to secure users’ data, we are most qualified to explain how Proton Drive works. So what follows is an overview of how Proton Drive secures your data.
If you want an even more technical description, read our Proton Drive security model.
Proton Drive is designed to prevent anyone from accessing or modifying your folders, files, and the associated metadata, such as file names, file types, and file sizes. Even Proton cannot access your data. To ensure this, Proton Drive generates all keys and passphrases on your device and never sends them in plaintext to the server.
To secure each file or folder (what we call the “payload”), Proton Drive first uses a symmetric key to encrypt the payload on your device. Unlike the PGP key pairs described earlier, with symmetric key cryptography, the same key can both encrypt and decrypt the payload. To restrict access to the file, the symmetric key is then itself encrypted using PGP as described above. Proton Drive uses one of your public keys to encrypt the symmetric key, meaning only you can decrypt the file by unlocking the symmetric key with your secret key.
This makes sharing files easy. To grant someone else permission to a payload, Proton Drive simply encrypts the symmetric key with that person’s public key.
As you can see, maintaining zero-knowledge encryption of a cloud storage service requires some extra effort on the part of the provider. Each of these operations requires computing power, so designing an efficient system is one of the main challenges.
But it’s worth it because we believe you should have complete control over your data. By joining Proton, you can become part of our mission to build a better internet where privacy is the default.
