Email is a great way to stay connected with the people and organizations you care about, but it is also a technology prone to data breaches and cyberattacks. In 2017, the email provider Yahoo revealed that over three billion user accounts were compromised(nouvelle fenêtre) in major breaches between 2013 and 2016.
As unencrypted emails pose a great risk to online security and privacy, more people are turning to encrypted emails as a secure form of communication. In this article, we explain what email encryption is, how it works, and what encryption protocols are available to keep your emails safe.
What is email encryption?
An email can be sent in two ways:
- As plain text
- In an encrypted format
Plain text emails use regular text without formatting and encryption technology. Sending an email in plain text is similar to sending an open-faced postcard in the mail — anyone who gets a hold of it can read its contents. If a third party intercepts your plain text email, its contents will be immediately exposed and your information put at risk.
When you encrypt an email, the message and its contents are scrambled so that it takes on a unique appearance, rendering it unreadable to those who do not have permission to access it. Only someone who has the correct encryption key, be it the intended recipient or an email service provider, can decrypt this scrambled data. In other words, email encryption ensures your data cannot be read by others.
Why is email encryption important?
Privacy
Email encryption plays a crucial role in securing your online privacy. It is the first line of defense against data theft and one of the most effective ways to prevent your email provider from reading your emails. Since your emails contain plenty of sensitive information about you, you are less likely to be targeted for ads, spam, and malware attacks when you keep them safe. By using email encryption, you are also protecting your emails from being modified and tampered with.
Compliance
Encryption lets industries that require a high level of confidentiality, like healthcare, take advantage of email’s convenience and popularity while still protecting sensitive information. In fact, using end-to-end encryption (E2EE) is an easy way for companies and organizations to comply with privacy regulations, such as HIPAA and GDPR.
Authentication
The year 2020 saw the largest ever number of data breaches and cyberattacks(nouvelle fenêtre) on governments and organizations. With the number of phishing and spoofing attacks still climbing, encryption can help verify the authenticity of the email by using digital signatures. Digital signatures prove the authorship of the sender and ensure that the email has not been tampered with in transit.
Learn more about digital signatures
The different kinds of email encryption
When you send an email, its level of security and privacy depends on the method of encryption you use to protect it.
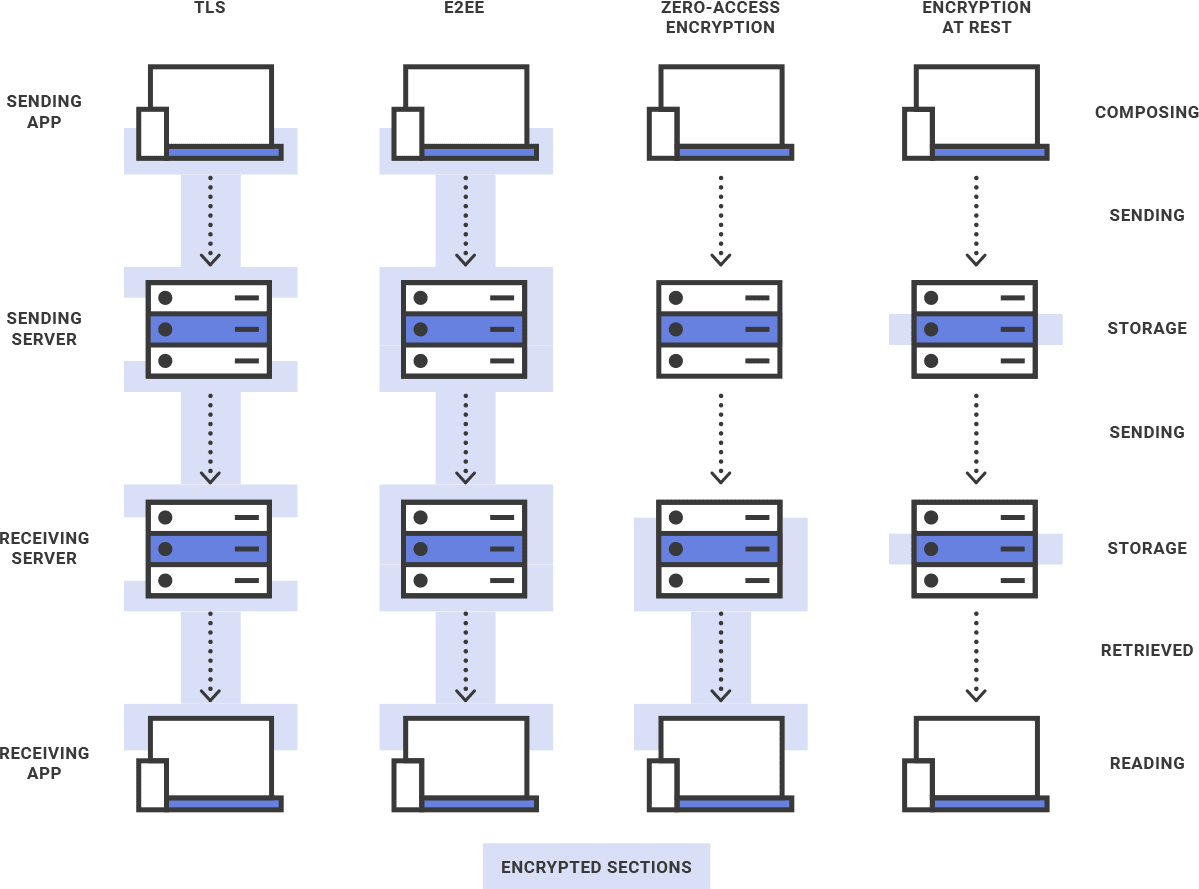
TLS
Transport Layer Security (TLS) is a cryptographic protocol used to secure web communications across a network.
Due to the versatility of TLS, it is used widely in various technologies, such as the opening of websites or web apps, instant messaging, and email. TLS is useful because it prevents third parties from eavesdropping and tampering with your messages while they are in transit.
In the case of email, TLS encryption is applied to a message multiple times when it is sent. It is encrypted and decrypted between the sender’s device and the sending server, between the sending server and the receiving server, and between the receiving server and the intended recipient’s device.
However, used alone, TLS does not provide adequate security for your emails. Once they arrive at the receiving server, they are decrypted, and it is up to the recipient email provider to encrypt and secure your messages.
Standard encryption at rest
Most email providers encrypt your emails using keys they retain control of, meaning they can decrypt your emails at any time. This puts your emails at risk if there is a data breach and is the reason why zero-access encryption and end-to-end encryption are both necessary.
Zero-access encryption
Zero-access encryption is an encryption method that effectively protects your data at rest by making the data inaccessible to the service provider.
With zero-access encryption, when you receive an email from an unencrypted email service, your email provider will briefly have access to the message after the TLS encryption is undone. It is then immediately encrypted using your public key. The encrypted data can only be decrypted locally on your device with your private encryption key.
Since your email provider does not have access to your private encryption key, it cannot be decrypted by anyone besides you. Every time you want to view your data, you download the encrypted files from the server and decrypt the data on your device with your private encryption key.
End-to-end encryption
Compared to other encryption methods, end-to-end encryption (E2EE) provides the most complete level of privacy. It ensures that your email is encrypted on your device and is not decrypted until it reaches your intended recipient’s device. E2EE prevents the sending server and the recipient server from having access to the email at any point in its journey.
There are two primary encryption protocols that provide E2EE: S/MIME and PGP.
S/MIME
S/MIME is an acronym for Secure/Multipurpose Internet Mail Extensions and provides end-to-end encryption. S/MIME works using symmetric encryption and asymmetric encryption involving a pair of mathematically related keys: a public key and a private key. When a sender sends an email using a S/MIME certificate, the email is encrypted using the recipient’s public key. The recipient can only decrypt the email using the private key associated with the public key.
While S/MIME certificates encrypt your emails and prove that you wrote and sent them, only a certificate authority (CA) can issue S/MIME certificates. This means you would have to contract your own CA to validate your digital identity.
PGP
Pretty Good Privacy (PGP) is another method of implementing end-to-end encryption and is one of the world’s most widely used email encryption systems. PGP relies on a combination of symmetric and asymmetric encryption to secure emails.
PGP works by first generating a random session key using symmetric encryption. This key is unique and used to encrypt the contents of the email. The session key itself is then encrypted using the recipient’s public key and sent to the recipient along with the encrypted email. Once the email arrives, the recipient decrypts the session key using their private key. The session key can then be used to decrypt the email.
While PGP may seem complicated, it is an extremely robust encryption protocol that has been battle-tested and is continually being improved. When implemented properly, PGP works seamlessly while providing a high level of security, privacy, and authentication for your emails.
Why Proton Mail provides the best encryption for emails
As a privacy-first company, we are committed to our vision of making privacy the default online. We believe that everyone should be able to choose how their data is used, which is why we use a combination of TLS, zero-access encryption, and end-to-end encryption to secure as much data as possible.
We also use PGP to ensure that our users can communicate with other PGP users privately by sharing public keys, even if the person you are communicating with does not have a Proton Mail account.
All emails sent and received via Proton Mail are automatically encrypted:
- If you use Proton Mail and send an email to someone who uses Proton Mail, your emails are end-to-end encrypted using PGP.
- If you use Proton Mail to send an email to someone who doesn’t use Proton Mail, you can end-to-end encrypt your emails using PGP if you have your recipient’s public key or by using our Encrypt for Outside feature.
- If you use Proton Mail and receive an email from someone who does not use Proton Mail but has used your public key to encrypt the email, it is protected using end-to-end encryption. (Responses to emails you send using Encrypt for Outside are also end-to-end encrypted.)
- If you use Proton Mail and receive an email from someone who does not use Proton Mail or PGP, your emails are protected with zero-access encryption.
This ensures all your emails are confidential and cannot be intercepted or tampered with by anyone. Not even Proton Mail can read or access your end-to-end encrypted emails.
Last but not least, we are also based in Switzerland, a country known for its strong data privacy laws. Our users benefit from Swiss jurisdiction and are fully protected by Swiss laws. If you believe that your emails should be end-to-end encrypted and privacy should be the default online, sign up for a free email account.
FAQ
When your email is encrypted end to end, the contents become scrambled into indecipherable text using your recipient’s public key. This ensures that nobody except your intended recipient can read the email. To decrypt the email, your recipient must use their private key associated with their public key to decode it. Even if hackers gained control of the encrypted email, they would not be able to decrypt it unless they had the right private key.
End-to-end encrypted emails are one the safest ways to transmit sensitive information over the internet. Emails that have been encrypted properly not only protect valuable data from being leaked online but also prove the authorship of the sender. To start sending end-to-end encrypted emails, sign up for a free Proton Mail account(nouvelle fenêtre).
There are a few reasons why email encryption is not widely used. Firstly, end-to-end encryption can be difficult to implement, especially in a way that is easy to use. Secondly, most email providers pay for your free email account by displaying targeted ads to you or scanning your emails and selling your information to advertisers. Since encryption makes all of your emails unreadable, some email providers are unwilling to switch to end-to-end encryption as they will no longer be able to read your emails and profile you.
At Proton Mail, we employ zero-access encryption and end-to-end encryption to secure your emails. We do not have the technical ability to read end-to-end encrypted emails and we apply zero-access encryption to non-end-to-end encrypted emails as soon as possible.
Feel free to share your feedback and questions with us via our official social media channels on Twitter(nouvelle fenêtre) and Reddit(nouvelle fenêtre).
UPDATE 6 July 2021: Clarified the language in the FAQ regarding how end-to-end encryption and zero-access encryption work.