Encryption is a way to hide information so private data is kept that way. Without encryption, anybody could access your communications. In this article, we go over how it works and some of the different types of encryption there are.
The short explanation is that encryption is a way to scramble information so nobody except the people it’s meant for can access it. This scrambling is done by using mathematical algorithms that lock and unlock the information. There’s a lot more to it than that, of course, but before we get to any of that, let’s start with what encryption is used for.
- Why use encryption?
- How encryption works
- What are encryption algorithms?
- Examples of encryption algorithms
- Encryption at Proton
Why use encryption?
The main reason to use encryption is to make sure information stays private, especially as it travels through the internet. Most people will encounter encryption in their daily life when communicating. For example, messaging apps like Signal or Wire (both of them among the best WhatsApp alternatives) will encrypt your chats.
Another good example is email, which, without strong encryption, can be intercepted by government(nova janela) agencies. By encrypting your emails, you’ve rendered them unreadable and thus useless for anybody that intercepts them. Another example is TLS, an encryption protocol that protects web traffic. When you visit a site and it shows the little lock pictogram in the address bar, you’re making use of TLS.

However, it’s not just communication that benefits from encryption: If you want to store files, encrypting them can add a layer of security. For example, our cloud storage app Proton Drive uses state-of-the-art encryption to keep files safe. Even if a cybercriminal were to breach the service, they still won’t be able to actually access the information in the files they’ve stolen.
How encryption works
The most common way to encrypt information is to scramble the readable text, known as plaintext, into unreadable ciphertext using mathematical operations known as algorithms. These algorithms use a cryptographic key, or a set of shared mathematical values usually based on prime numbers, to encrypt a file. Without the correct key, a file cannot be decrypted.

We go into more detail in our article on ciphertext, but think of it as a lock on your door. You lock the door (turning plaintext into ciphertext) to restrict access, and then somebody with the key can unlock it (turn ciphertext into plaintext) whenever they need to.
A basic example is the so-called Caesar cipher, which was used by Julius Caesar to secure messages. It was an advanced form of the kind of encryption you maybe learned in school, where numbers are used instead of letters, so 1-2-2-1 can spell out a Swedish pop band. The Romans took this principle, but then moved the number. For example, they could add a three, so A would be written as a “4” rather than a “1”.

Of course, a cipher like this is pretty easy to crack, and in the millenia since Rome ruled the world cryptography has taken great strides. Any professional encryption nowadays is handled by algorithms, complicated mathematical formulas that can encrypt plaintext and then decrypt ciphertext in milliseconds.
At the same time, different types of encryption have evolved as well. Like we said earlier, your web traffic isn’t encrypted the same way your email is. This has to do with a few factors, like the speed with which a message needs to be encoded and decoded or the level of security needed, among other things.
Roughly speaking, encryption is made up of two types, symmetric and asymmetric, each of which have their own strengths and weaknesses.
Symmetric encryption
Symmetric encryption is the easiest to grasp. In this system, the key that encrypts the plaintext and the key that decrypts the ciphertext are the same — not unlike your front door. In a pre-digital era it was pretty much a given that both sides of a secret conversation used the same key; the Caesar cipher is an example of symmetric encryption.

However, this presents issues, mainly that if an attacker intercepts both the message and also the key, they’ll be able to read your message. If you can’t make sure the means of sending the key is safe, you may have to use symmetric encryption in tandem with another type of encryption, namely asymmetric encryption.
Asymmetric encryption
With asymmetric encryption, the key that decrypts the information is different from the one that encrypts it. The core idea behind asymmetrical encryption lies in the keys used. Where symmetrical encryption uses a single secret key known only to the sender and receiver, asymmetrical uses a public key to encrypt information, and a private one to decrypt it.
Public in this case means exactly what you think: Anybody and everybody can use the public key (which is why you’ll also see it referred to as public-key encryption). Only the receiver has the private key.
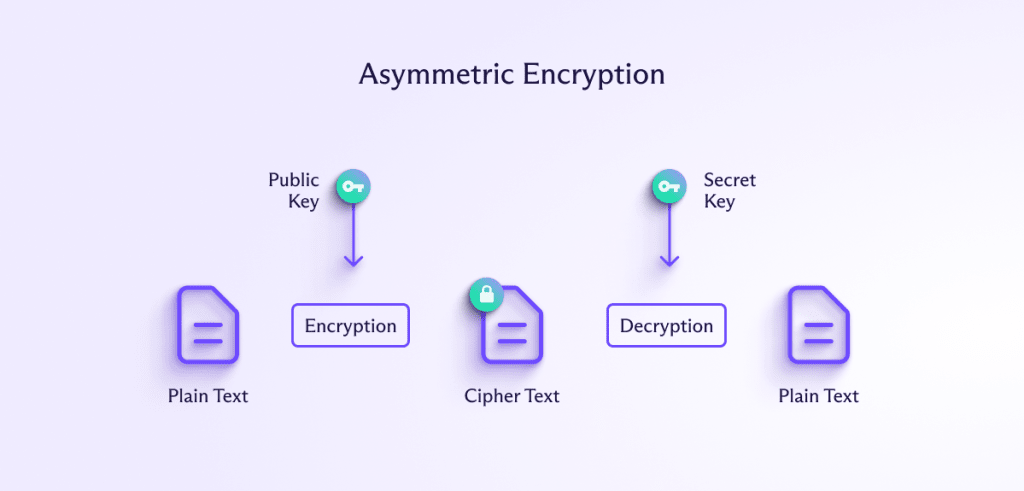
It’s like having a mail slot in your door: Anybody can throw letters in, but you need a special key to open the mailbox and get to them. This allows anyone to send you a message, but without needing to share a key with them in advance.
The math that makes this possible is integer factorization, a process that’s easy to calculate in one direction but difficult in the other. For example, it’s easier for you to compute 12 x 6 (72) than to work backwards from 72 to find the factors. In public-key cryptography, the numbers are a lot larger than 6, 12, and 72. With a large enough integer, it’s practically impossible to crack the factors and unlock an encrypted message if you don’t already know the secret number (your private key).
Because it works so differently from symmetric encryption, asymmetric encryption has a very specific use case, something we talk about more later. It’s also quite a bit slower.
What are encryption algorithms?
When you use a service that encrypts data, the encryption is handled by algorithms, complicated mathematical formulas. These come in all kinds of subtypes, but the most important categories are symmetric and asymmetric algorithms, which can be further specified by the length of the keys they use.
The longer a key is (which is measured in bits), the more information is stored and the harder it is to crack. In computing, a bit refers to a single value that’s either 1 or 0 (since computers rely on binary).
A key that is just one bit long would be very easy to crack as it’s either a 1 or a 0. The maximum number of guesses required to break a 1-bit key is two. But this difficulty grows exponentially. A key with two bits is twice as hard to crack since there are two values that could each be a 1 or a 0, meaning the maximum number of guesses you need to solve it is four. However, a three-bit key is four times as hard to crack.
So a key that’s 128 bits long — a common length for symmetric encryption — would require a maximum number of guesses of 2 to the 128th power, or 340 undecillion (or 340 with 36 zeros behind it). Cracking a key of that length would, theoretically, at least, take a few billion years, at least when using a brute-force attack, which “guesses” a key bit by bit.
Practically speaking, symmetrical encryption keys can be up to 256 bits long, while asymmetric keys can be thousands of bits long. In either case, brute forcing them will take a long, long time.
Symmetric encryption algorithms
Generally speaking, symmetric algorithms like AES, Twofish, ChaCha20 and more, will encode information either bit by bit (called stream ciphers) or gather information in blocks (called block ciphers, unsurprisingly) of several bytes and encrypt those.
The upside to using symmetric encryption is that it’s fast. A good example is when encrypting your hard drive, something which you want to be able to decrypt quickly whenever you need it. As the password that decrypts the key lives in your head, there are no issues with sending the key, either.
Asymmetric encryption algorithms
Asymmetric algorithms, unlike symmetric ones, allow anybody to encrypt a message with the public key. This is useful for communication, like in email. Anybody can send you an email using Proton Mail without having to share the key in advance.
However, asymmetric encryption algorithms like RSA or X25519, in contrast to symmetric algorithms, are a lot slower because they use longer keys, meaning they’re slower to encrypt and decrypt ciphertext. Though the delay can be measured in milliseconds, this adds up when dealing with large files.
Examples of encryption algorithms
Now that you have a grasp of what encryption is and the different types there are, let’s go over some concrete examples of what you may encounter when shopping for an encrypted service, like secure mail, cloud storage, or even a virtual private network. To give you something to hold on to, we’ve put together this selection of the most commonly used encryption algorithms.
Symmetric encryption algorithms
First up are symmetric algorithms, which are popular for their speed and security. There are a huge number to choose from, but these three are among the most important.
DES
First up is Data Encryption Standard (DES), which is mainly notable since nobody uses it anymore. Developed in the 1970s, it features a 56-bit key, which at the time was highly advanced and made it the standard for encryption — hence the name.
DES set several trends, though, which make it worth mentioning. One of the most important was that it was one of the first algorithms to encrypt data in blocks. In this process, data is subdivided into blocks and then encrypted block by block, meaning it encrypts and decrypts faster, but still gives you the same security. Still, with the development of ever-improving computers, 56 bits just wasn’t enough and DES was phased out.
AES
One of DES’s most important successors is AES, or the Advanced Encryption Standard. It was adopted by the United States government as its standard in 2001 and is widely used by all kinds of agencies and the military — it’s the “military-grade” encryption commonly touted in marketing material.
AES is, like DES, a block cipher, but its blocks are double the size at 128 bits, meaning each block has more information in it. It can also encrypt a block multiple times, scrambling the scramble, so to speak, making it extremely hard to crack. AES’s keys are also much longer than DES’s, coming in at 128, 192, or 256 bits. Of these three, AES-128 and AES-256 are the most common — Proton uses AES-256 as a symmetric algorithm.
Blowfish
The Blowfish cipher is another algorithm developed as a successor to DES, and shares some characteristics, most notably the 64-bit block size. However, its key length is a lot more variable, allowing you to set it from 32 bits all the way up to 448 bits.
The issue with Blowfish is that its small block size has made it theoretically more vulnerable. As a result, its designer developed a new version called Twofish, which has a 128-bit block size, and, like AES, limits keys to a maximum size of 256 bits. In most cases, you may want to steer clear of Blowfish encryption, though Twofish has proven secure so far.
Asymmetric encryption algorithms
Asymmetric encryption algorithms are generally a little more complicated to explain as they rely on higher-order math. While the public key is simple enough to transmit, how the private key unlocks the information depends on the algorithm.
RSA
One the most widely used asymmetric algorithms is RSA, which is named after the initials of the surnames of the people who invented it back in the ‘70s (Ron Rivest, Adi Shamir, and Leonard Adleman). It’s used in all kinds of applications, from secure mail to VPN services. However, over time it has proven to be vulnerable to specific types of attacks which can exploit the timing of the decryption process, and it’s not always regarded as being the most secure algorithm.
Also, as RSA and its predecessor, Diffie-Helman, rely on using ever-larger numbers in the equation to keep things safe, the number of bits involved in the keys are massive. It’s not uncommon to see RSA keys of 4096 bits, for example, which slow the encryption process down considerably.
X25519
Another type of asymmetric encryption is elliptic curve cryptography, which we at Proton use. It works on similar principles as other asymmetric algorithms, but uses smaller numbers to achieve the same level of security — read this primer(nova janela) by Ars Technica for more details on the math.
The specific algorithm we use is called X25519, which we chose for a few reasons, not the least of which is because it’s resistant to timing attacks. On top of that it’s also relatively fast, compared to other asymmetric encryption algorithms.
Encryption at Proton
We’ve gone over the basics of encryption and how it works, but you may be wondering how it works for you, a Proton user (or at least a prospective one). Thing is, encrypting a file, email, or even an entire internet connection isn’t as simple as just running an algorithm and calling it done. To make sure your communications stay safe involves some extra steps.
The first step is to determine what type of encryption needs to be used. For example, for a file that just sits on your computer, symmetric encryption is sufficient. However, once we start sending things over the web, you get better results when you combine multiple types of encryption.
At Proton we use the OpenPGP standard, which combines a symmetric algorithm with an asymmetric one. This gives you the flexibility of asymmetric encryption and the speed of a symmetric algorithm. With Proton Mail, that means you can send encrypted emails and attachments to anyone quickly and securely.
OpenPGP is so secure in part because it’s open, meaning any security researcher can analyze it to make sure it’s secure. As a company that believes in transparency and scientific peer review, this is of vital importance. For more details, read our full article on how PGP works.
In addition, we use something called end-to-end encryption. When sending a message or file, normally it will be encrypted and decrypted a few times during transit to make sure it’s going where it needs to go. However, this is inherently less secure, which is why at Proton we encrypt files at all times, from one end of the transmission to the other end — hence the name.
You can read all about the details in our full article on end-to-end encryption, but you can rest assured that whether you’re sending an encrypted email with Proton Mail or a file via Proton Drive to another Proton user, at no point can it be intercepted in an unencrypted state.
This also means that at no point we can see what you’re transmitting, either, unlike other providers. Google is one example, as it will snoop on your files in order to gain private information about you that the company uses for targeted advertising.
Because we make money from community support rather than ads, Proton’s first priority is your security. It’s why we have zero access to your passwords, and why we encrypt your files and data at all times.
As a company founded by scientists from CERN with the express purpose of creating a safer and more private internet, we have taken extreme measures to protect your data. You can learn about some of our security features here.
When you join us by creating a free Proton account, you’re not just joining a movement for a more private internet, you’re making sure you’re on the cutting edge of encryption, too.


