The dark web is much like the regular World Wide Web we’re all familiar with, except that the dark web provides much greater privacy.
The dark web has a reputation for being a place where you can find and contact drug dealers and hitmen. There’s truth to this, but the dark web also offers a welcome refuge from overbearing government surveillance and the ubiquitous corporate capitalism that tracks your every move online.
The dark web isn’t called “dark” because it’s inherently bad; it’s called dark because it provides privacy (that can be used for good and ill).
The extra privacy afforded by the dark web is undoubtedly abused by criminals to scam people, sell drugs, host illegal content, and more. The high-profile rise and fall of the Silk Road marketplace(новое окно) for illicit drugs is the best-known example of this.
But despite sensational media coverage(новое окно), many highly reputable websites have a dark web presence, including The New York Times(новое окно), The Guardian(новое окно), and even Facebook(новое окно). Indeed, Proton offers an onion dark web version of our website so that people in some of the most repressive parts of the world can access our services.
We explain what the dark web is, how you can access it, and what sites you might find useful on it.
- What is the dark web?
- Tor Onion Services
- I2P
- Freenet
- How to access the dark web
- What’s on the dark web?
What is the dark web?
The internet can be divided into three parts:
1. The clear web
Also known as the “surface web”, the clear web is the World Wide Web(новое окно) we’re all familiar with. It’s a collection of websites connected to each other via hyperlinks that are easily searchable using search engines such as Google.
Learn more about search engines that respect your privacy
However, the clear web makes up only a small fraction of all content on the World Wide Web.
2. The deep web
The deep web, also known as the “invisible web”, is often incorrectly conflated with the dark web. In reality, the deep web is all internet content that’s not indexed by search engines, the vast majority of which is innocuous content, such as financial databases, web archives, and any page that is password-protected (such as your medical records or bank account pages).
An often-quoted paper from the University of Michigan(новое окно) states that “public information on the deep web is currently 400 to 550 times larger than the commonly defined World Wide Web”. However, this paper was published in 2001, meaning these figures should now be taken with a heavy pinch of salt. The point, however, stands — the deep web is much, much larger than the clear web.

3. The dark web
The dark web, also called the “hidden web,” is a small portion of the deep web. It is made up of websites and other online resources that can only be accessed using special software, configurations, or authorization.
Tor Onion Services(новое окно) are by far the most well-known and popular dark web. However, there are other dark webs. The best known are I2P(новое окно) and Freenet(новое окно), but there are also numerous smaller dark webs, such as GNUnet(новое окно), ZeroNet(новое окно), and dn42(новое окно).
How to access the dark web
To access the dark web, you need special tools that can vary depending on which dark web you want to use.
Tor Onion Services
Tor is a tool specifically designed to provide a high level of true anonymity when using the clear web. When you connect to the internet through the Tor network, your connection is routed through at least three random nodes, with your data being re-encrypted each time it passes through a node.
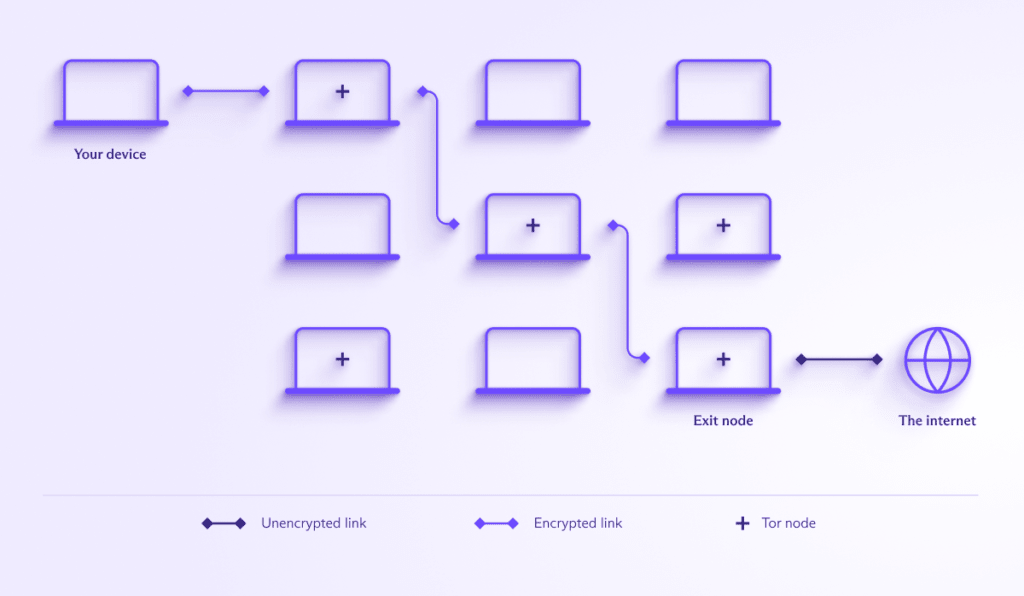
The “entry node” can see your real IP address but has no access to the content of your data or what you do on the internet, while the “exit” node” onto the internet decrypts and encrypts your data (and can therefore see it) and can see which websites you visit. But it has no idea what your real IP address is.
Although it remains probably the best way to achieve true anonymity on the regular internet, this system has a major weak point — the exit node. While it can’t know your real IP address, it can see your unencrypted data, which may reveal your true identity (although HTTPS still protects you).
It also comes with some vulnerabilities. If a powerful adversary was able to take over a very large number of Tor nodes(новое окно), they might be able to to deanonymize you by performing a timing attack (matching your connection time to the Tor network with known activity from a compromised Tor exit node).
Another problem is that Tor makes the IP addresses of all public Tor exit nodes public(новое окно), making them very easy for governments to block.
Tor Onion Services was developed to overcome the exit node problem by removing the exit node. Onion Services are websites that exist within the Tor network and can only be accessed from the Tor network. Since these websites are themselves Tor nodes, there’s no need to use an exit node that could be blocked or monitored.

I2P
I2P(новое окно) is designed to improve upon Tor’s onion routing system with its garlic routing(новое окно) (a somewhat tongue-in-cheek name). One key difference between Tor and I2P is that I2P bundles its data packets together into “cloves” before sending them through its network as messages rather than sending them one by one as Tor does.
Usually, each message contains one clove, but sometimes they contain two. This makes it harder for attackers to deanonymize you with timing attacks.
Another important difference is that connections aren’t unidirectional. So (unlike Tor), outgoing and incoming traffic use different paths, making it much harder to trace a connection back to a user.

On a purely technical level, I2P offers some real security and privacy advantages over Tor. However, interest in I2P has waned badly in recent years (which itself impacts I2P’s security), so many I2P “eepsites” and forums are now abandoned.
Freenet (recently renamed Hyphanet)
Strictly speaking, Freenet is a fully distributed, peer-to-peer anonymous publishing network that offers secure data storage. When you join the Freenet network, you agree to share a percentage of your local disk space. This space is securely encrypted, and other Freenet members download parts of files that are stored on it (in a way not dissimilar to BitTorrent(новое окно)).
However, on top of this basic file-hosting framework, volunteers have developed applications that allow for websites, message boards, and more. A limitation of this system is that websites cannot be dynamic (so they’re always simple static HTML pages).
An advantage is that web pages (and other data) can be available long after the original host has disappeared. However, if no one accesses data for a long time, it can disappear (this works much like BitTorrent, where files that aren’t actively seeded become de-indexed over time).
Freenet bundles packets together and routes them through a varying number of nodes to confuse timing attacks.
The network can be used in two “modes” — opennet and darknet. With opennet, you connect to random peers. With darknet, you only connect to trusted friends who you’ve previously exchanged public keys and node references with. It’s these darknets that makes Freenet uniquely secure, as it completely blocks outside access to data shared within a darknet group.
Because of their closed nature, these darknets also make it impossible to know how many people actually use Freenet.
How to access the dark web
Each dark web is mutually exclusive and requires its own tools to access. For example, you can’t use Tor Browser to access I2P eepsites. Since Tor Onion Services is by far the most popular (and therefore most generally useful) dark web, we’ll focus on that here.
The usual (and most official) way to access Tor Onion Services is by using Tor Browser for Windows, macOS, Linux, and Android(новое окно). This is a hardened version of Firefox that, by default, automatically routes all your connections through the Tor network. If you have an iPhone or iPad, you can install Onion Browser(новое окно), which while unofficial, is recommended by the Tor Project(новое окно).
For even greater security, you can use TAILS(новое окно). This is a Live Linux distribution that you boot directly from a USB stick so that it leaves no trace on the host computer. TAILS routes all connections (not just those from the browser) through the Tor network.
Once you’ve established a Tor connection, you can connect to onion dark websites. These are just like regular websites but use the special .onion domain name.
Proton VPN and Tor
With Proton VPN, you can route your connection through our VPN servers to the Tor network(новое окно). To do this, simply connect to one of our special Tor servers that can be identified by their onion icon.

We offer this feature primarily as a convenient way to access onion sites using your regular browser, and it does offer some security advantages over using Tor Browser. Still, if security is important to you, we strongly recommend reading through the Tor Project’s official advice on using Tor and VPNs together(новое окно).
What’s on the dark web?
The illicit uses of the dark web are well documented: assassination services, ecommerce sites for buying guns and drugs, and so on (many of which are simply scams, anyway).
However, there are plenty of legitimate reasons to use the dark web. You can read ProPublica(новое окно) or The New York Times(новое окно), check your email in Proton Mail, or browse your Facebook wall(новое окно). All of these mainstream websites offer dark web access because of the privacy and freedom of information advantages it offers.
See our pick of the best onion sites on the dark web(новое окно)
One of the biggest advantages of the dark webs is that it’s difficult to block. Common forms of censorship that rely on internet service providers blocking website IP addresses aren’t effective against dark webs. (As a result, some authoritarian governments have tried to block Tor itself(новое окно).)
For similar reasons, the dark web is more resistant to surveillance. Whistleblowers, journalists, and other professionals at risk of targeted surveillance use the dark web to communicate sensitive information. For example, whistleblower Edward Snowden used TAILS(новое окно) to help stay one step ahead of the NSA.
Many organizations, including Human Rights Watch(новое окно) and the Electronic Frontier Foundation(новое окно), also support the use of and access to the dark web.
A major drawback of all dark webs is that they are very slow. With Tor, for example, your connection is routed through at least three random locations around the world (any of which might have very poor internet access), which necessarily slows your connection.
For day-to-day use, a VPN provides a high level of privacy while also having minimal effect on your internet experience. But when you need it, the dark web can be vitally important: When Turkey temporarily blocked Proton Mail for some users, our onion site was one of the few ways people could access their emails.
So yes. Bad stuff happens on the dark web, but it’s also a vital privacy tool. As governments work to weaken encryption(новое окно) with backdoors and corporations gain greater access to everything we do, privacy and security technologies like those used to create dark webs must be vigorously defended. And that starts with understanding them beyond sensational headlines.






