Cybersecurity attacks are on the rise, and small businesses are being targeted.
Cybercrime is a multi-billion dollar industry that encompasses a broad range of threats, from fraud to credential theft. Most of these attacks originate with phishing attacks — scams that try to trick you into revealing sensitive data or downloading malware. The Anti-Phishing Working Group (APWG) recorded over 1 million phishing attacks(новое окно) in the fourth quarter of 2023 alone — an unprecedented total.
Small businesses may think they are too small to be a target, but they’re increasingly vulnerable due to increases in automated cyberattacks, according to Forbes(новое окно). Cybercriminals use software to scan the internet for easy targets, often finding small businesses with less secure networks. The financial fallout could be devastating. In 2023, the Internet Crime Complain Center (IC3) reported that it received 21,489 business email compromise complaints with adjusted losses over (новое окно)$2.9 billion(новое окно).
This article offers simple, easy-to-implement strategies to protect your small business against cyberattacks, which could save you money in the long run.
How to prevent phishing, the biggest threat to your business
Effective prevention requires employing a range of security measures to protecting your business. This includes strong anti-malware defenses, robust security policies (with appropriate education and training for staff), and continuous monitoring of your systems.
Proton provides multiple tools to help businesses manage their cyberdefenses:
- Proton Mail is a privacy-first encrypted email service that can help protect your team against some of the most common email-based cybersecurity threats.
- Proton Pass is an end-to-end encrypted password manager that can be deployed seamlessly into your business network to improve collaboration and help your team work securely.
Use hide-my-email aliases

An effective way to defend against email attacks is to limit the number of people who know your real email addresses.
Proton allows you to create multiple email addresses (including email addresses using your company’s custom domain with a Proton business plan). Additionally, hide-my-email aliases in Proton Mail and Proton Pass protect your identity, control spam, and prevent phishing.
Hide-my-email aliases are unique, randomly generated email addresses you can share publicly instead of your real email address, meaning you can create accounts, receive emails, and reply in your Proton Mail mailbox without revealing your identity.
When you create an account for an online service, for example, you can provide a hide-my-email alias to avoid being tracked or attacked by hackers if your email address is ever exposed in a data breach. If an alias is exposed in a breach, you can simply deactivate it without affecting your other accounts.

Proton Pass for Business and Proton Business Suite gives you an unlimited number of aliases to create as many as you need. You can create up to 10 hide-my-email aliases with a Proton Mail Essentials plan and 20 with a Proton Mail Professional plan. You’ll find your hide-my-email aliases in either our new Security Center in Proton Mail or your Proton Pass account.
Learn about hide-my-email aliases with Proton Mail and Proton Pass.
Confirm links

One strategy attackers use is embedding malicious links in emails that appear to come from reputable sources.
There is a simple but effective phishing defense in all our apps. Our apps ask you to confirm that you wish to open an external link from an email. We strongly advise that you always take this opportunity to read the full link to see whether it’s genuine.
Learn more about link confirmation
Address verification
This advanced feature is like sharing a magic word or secret handshake with your colleagues, customers or business contacts, that confirms they are who they say they are. This prevents hackers from manipulating encryption keys to intercept messages.
Your Proton Mail account allows you to manually trust a “secret handshake” — or PGP key — for specific contacts.
Learn more about address verification
Lock icons
Proton Mail makes it easy to tell whether an incoming email is encrypted and secure. End-to-end encryption and zero-access encryption ensure no cybersecurity attack against Proton servers can reveal your emails, files, contacts, and other data.
You can identify the encryption status of emails you receive by paying attention to the lock icons shown on each email.
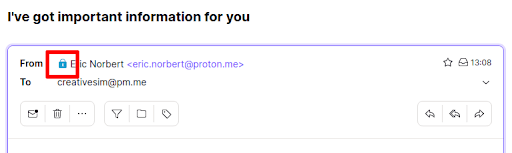
- A blue lock means the secure email was sent from a Proton Mail address. It is not possible to spoof emails from Proton Mail accounts.
- If your organization uses Proton Mail, this also provides a guarantee that someone within your organization sent the email.
- A green lock denotes a PGP-signed message. A PGP signature guarantees that the sender is genuine and that the message hasn’t been tampered with.
- A blue or green lock with a checkmark shows that you have manually chosen keys to trust with this contact (Address verification).
Learn more about how to check encryption status using lock icons
Learn more about how to protect yourself from phishing attacks
Protect your passwords
Hackers often target and steal databases full of user passwords, which can prove damaging to a small business with limited resources.
If your employees are reusing passwords across different accounts, one breach can lead to multiple accounts being compromised, including a business account that contains invaluable information. One leak can cause irreversible damage.
A reliable password manager can help prevent this from happening. With Proton Pass, you and your employees can generate strong, unique passwords for each account to limit the chances of a breach happening. A Proton for Business account gives you access to Proton Pass, which includes 50 vaults and unlimited aliases.

If hackers do somehow steal your login credentials, however, having two-factor authentication (2FA) adds an extra layer of security to keep your business safe by requiring not only a password but a second factor — such as a one-time passcode on your phone — to access an account. Proton Pass includes a built-in two-factor authenticator.
And Proton Pass for Business users can even enforce 2FA for their entire team, allowing business owners to enforce a higher security standard.
Proton Sentinel
Everyone with a Proton Mail Professional or Proton Business Suite plan account gets access to our high-security Proton Sentinel program, which works for both Proton Mail and Proton Pass and has blocked thousands of account takeover attacks since it was launched in August 2023.
Proton Sentinel prevents attackers from getting your data even if they have managed to steal your Proton username and password. This is a feature you won’t find using other popular email providers.
Using artificial intelligence and human expertise, Proton Sentinel swiftly detects and blocks suspicious attempts to take over accounts, leveraging insights Proton developers discovered while building anti-abuse systems that protect over 100 million accounts.
Learn more about Proton Sentinel
How to prevent data breaches
A data breach occurs when sensitive information held by a company is made available in an unauthorized way. Data breaches can result in competitors gaining access to what should be privileged information about the internal workings of your company. However, the most devastating, high-profile, and common data breaches are when a company leaks personal details belonging to users and customers.
For example, in July 2022, Uber admitted to a 2016 data breach(новое окно) that affected 57 million passengers and drivers and that it paid the attackers $100,000 to keep the breach secret. Even more dramatically, T-Mobile suffered a data breach in 2021 that affected some 76 million users, resulting in a $350 million settlement to a class action lawsuit(новое окно). But there are several steps you and your employees can take to safeguard your data and prevent similar breaches from happening on a smaller scale.
Use encryption whenever possible
Emails sent between Proton users are end-to-end encrypted (E2EE). It is also possible to send E2EE emails to non-Proton users using PGP or Password-protected Emails. This means they are encrypted on your device and can only be read by the intended recipient. No one else, including us, can read them.
We have no control over how non-E2EE emails sent to people who don’t use non-Proton Mail are stored on their provider’s servers, but when stored on our servers, they are secured using zero-access encryption. That is, they are encrypted using your public key, so only you can decrypt them. Again, no one else, including us, can read them.
Unlike other email services that can decrypt data on their servers, Proton does not keep decryption keys, meaning if there were a data breach no hacker could get anything but encrypted files, which are useless without your password.
Learn how encrypted email works(новое окно)
Learn more about how to prevent a data breach
Train employees
None of the steps in this article will have impact if your employees are not trained to implement them. Your employees are the first and last line of defense against cybersecurity attacks.
Building up your staff with useful, clear guidelines that detail penalties for violating company policy is essential for any effective cybersecurity plan. That means all employees should be well versed in not only phishing attacks, but strong password best practices, encrypted services, and whom they should contact for support.
At the very least, using Proton Mail for your organization’s business communications and Proton Pass for its passwords are easy solutions to safeguard your team and valuable data.
To learn how Proton can help protect your business, contact our sales team at enterprise@proton.me.
Keep your business safe with Proton
While other companies are built to create value for advertisers, our business model is quite different. All our revenue comes from subscribers who upgrade for more storage and additional features. This business model requires us to prioritize the privacy and security of our community above all else, and we’ve designed the entire platform to reflect that. Every feature was built to protect your valuable data.
Proton was not born in Silicon Valley. It started as a crowdfunded project led by scientists who met at CERN (the European Organization for Nuclear Research) with a mission to fight for an internet that’s private by default.
We built Proton to serve that mission, which includes helping you protect your small business with easy-to-use tools that can prevent devastating attacks from threatening your existence. at can prevent devastating attacks from threatening your existence.