Email headers are the hidden part of emails containing vital information to identify and authenticate messages. Learn how to read them to spot spam and stay secure.
Have you received an unexpected email from a strange address? Is it actually from someone you trust, or is it just spam or a phishing attempt? Email headers can help you find out.
We explain what email headers are, what they contain, and how to read them to keep your inbox spam-free and secure.
- What is an email header?
- What do email headers contain?
- Why are email headers important?
- When to check email headers
- How to view email headers
- How to read an email header
- Reading Proton Mail email headers
- Check email headers, stay secure
- Email header FAQs
What is an email header?
An email header is a hidden snippet of code in an email that contains detailed information about the sender, the recipient, and how the message was routed and authenticated.
Emails typically display the Subject, From, To, and Date fields in the visible header at the top.
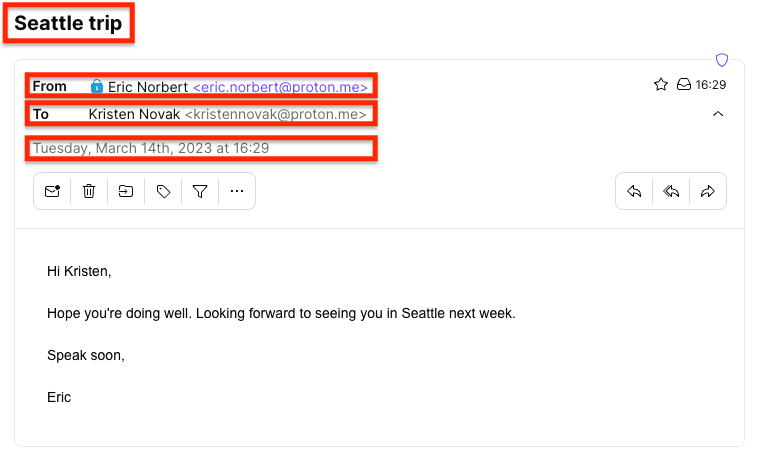
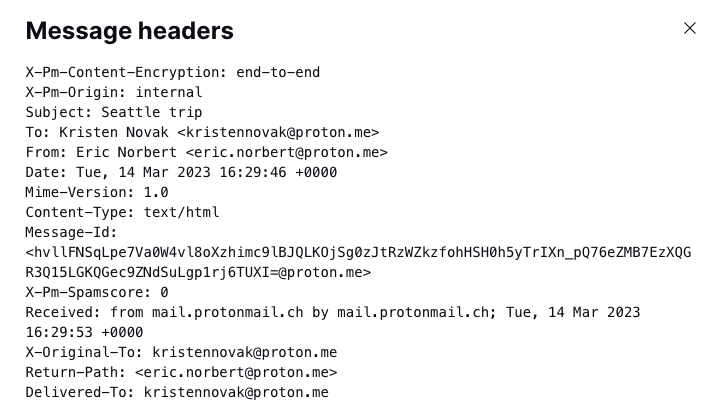
However, spammers or fraudsters can spoof the displayed From field so the sender appears to be someone you trust. By viewing the hidden full email header of the original message (shown below), you can check the sender’s address and other delivery information to verify it’s legitimate (see how to read an email header below).
What do email headers contain?
An email’s header contains information about the sender, the recipient(s), and how the mail was delivered, including the following mandatory fields:
- From: the sender’s name and email address
- Date: the time and date the message was sent
- To: the recipient’s address (or addresses if the email includes CC or BCC)
Most emails typically contain many other fields, such as:
- Subject: the title as displayed in the Subject line
- Reply-Path: the return address of the email if it fails
- Received: the SMTP servers that the message has passed through. Emails typically pass through multiple servers, each adding a new Received header.
- Authentication-Results: the results of checks to see if the email originated from the stated sender.
For details about these and other common header fields, see how to read an email header below.
Why are email headers important?
Email headers contain essential information for the correct delivery, authentication, and filtering of messages. With email headers, you can:
Identify the sender and recipients
While an attacker can spoof an email’s display names, the email header helps you trace the sender’s original address and the delivery details. That way, you can check if a sender is genuine and block them if necessary.
Trace email routing
When you send an email, it passes through various servers or mail transfer agents (MTA). Each MTA adds a Received header with its IP address(новое окно) and other details about that hop of the email’s journey to the recipient. By viewing the header, you can check for suspicious routing.
Show message authentication
When you receive an email, you want to verify that the sender is genuine. Email headers usually show whether the message passed authentication checks like SPF, DKIM, and DMARC (see below for details).
Spot spam and phishing
Email services use the message details in email headers to determine whether a message is spam or a phishing attack. Typically, the results of spam filters are also included in email headers.
When to check email headers?
You don’t need to check the headers of every email you receive. But here are some situations where checking email headers can be useful:
Check suspicious email
If you receive a message that looks like spam or a phishing email, you can check the header to investigate whether it’s legitimate. Tracing the sender’s address, domain, IP address, and other details can help you determine whether it’s genuine or a phishing attempt.
Investigate email tampering
If you suspect that someone is intercepting your emails or has gained access to your account, checking email headers can help you investigate. By checking the source of the message and each of the email servers it passed through, you can trace any interception or unauthorized access.
Identify email delivery issues
If you’re having problems sending or receiving emails, checking the headers can help you find the cause. For example, headers may contain error messages or show that spam filters have rejected a message you’ve sent.
How to view email headers
The header at the top of most emails only contains the main display fields, like Subject, From, To, and Date. Here’s how to reveal the full email header of the original message in popular email services.
View Proton Mail email headers
1. Log in to your account at mail.proton.me(новое окно) and open an email.
2. Click on the More menu (three horizontal dots), and select View headers.
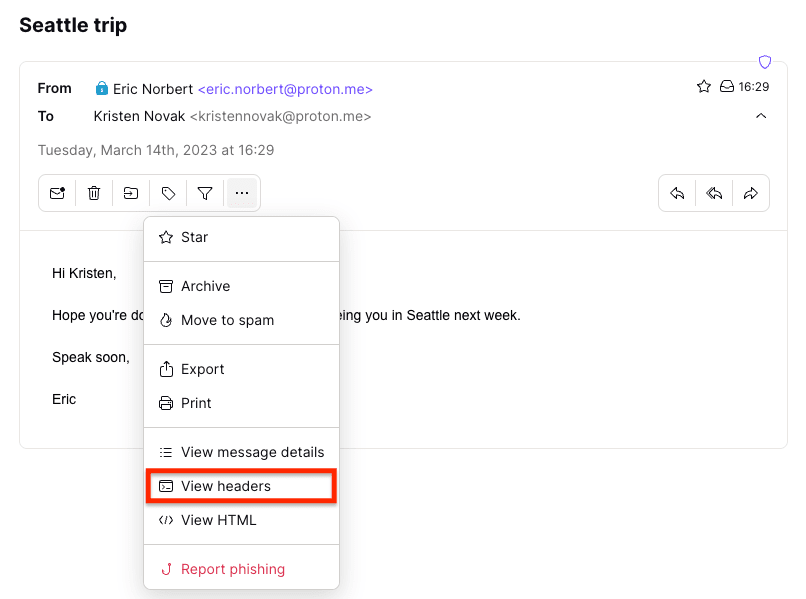
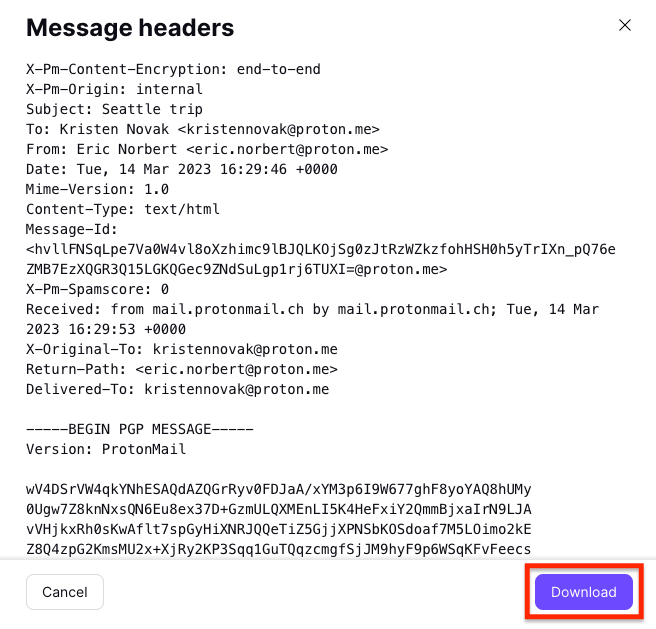
The email header will display in a popup window. You can then download it as a .txt file by clicking Download.
Learn how to check email headers in the Proton Mail web and mobile apps
View Gmail email headers
- Log in to your account at account.gmail.com(новое окно), and open an email.
- Click on the More menu (three vertical dots), and select Show original.
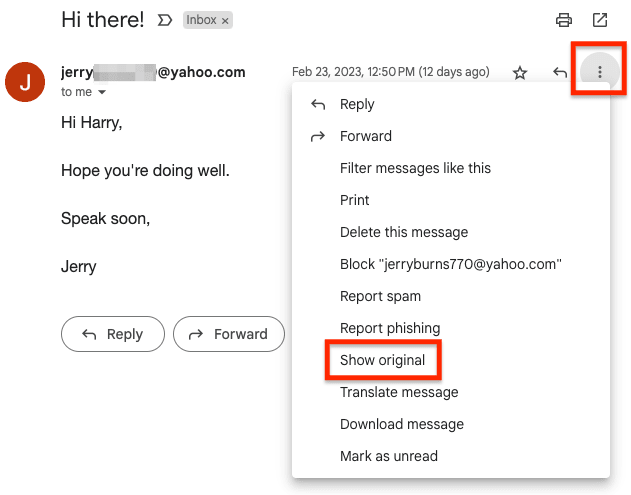
- Click Copy to clipboard to copy the email header or Download Original to download it.
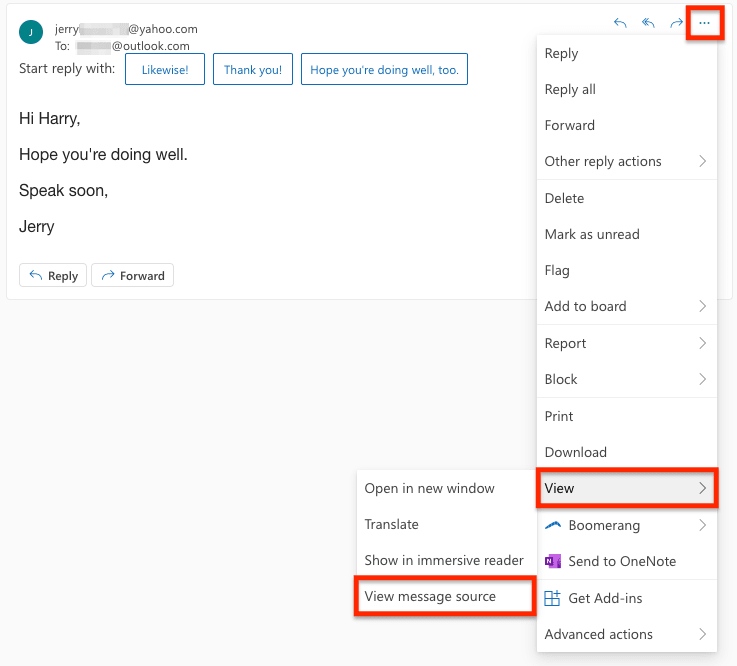
View Outlook email headers
- Log in to your account by going to outlook.com(новое окно) or the Microsoft 365 login page(новое окно).
- Click on the More actions menu (three horizontal dots), and go to View → View message source.
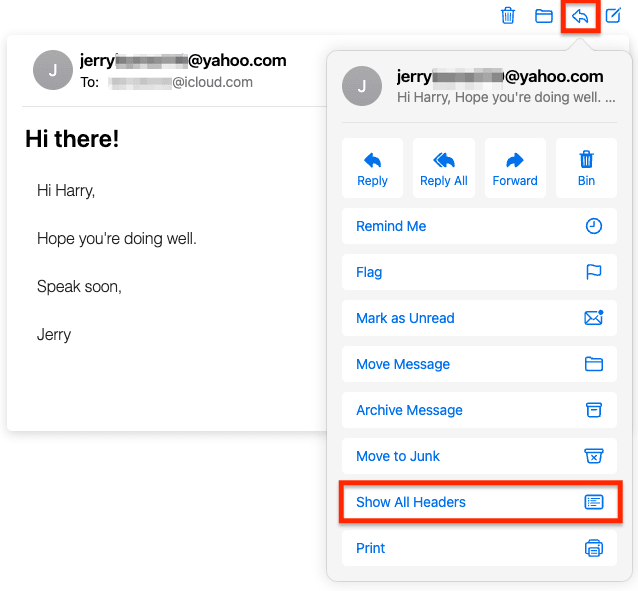
View Apple iCloud email headers
- Log in to your account at icloud.com/mail(новое окно), and open an email.
- Click on the Reply icon, and select Show All headers.
How to read an email header
After opening an email header, you’re faced with a daunting block of code — a list of fields that show essential information (metadata(новое окно)) about the message, like where it came from and how it was routed and authenticated.
To find specific information in an email header, you can search using the keyboard shortcut Control + F (Windows/Linux) or Command + F (Mac). For example, search for “Authentication” to find the Authentication-Results fields in the email header below:
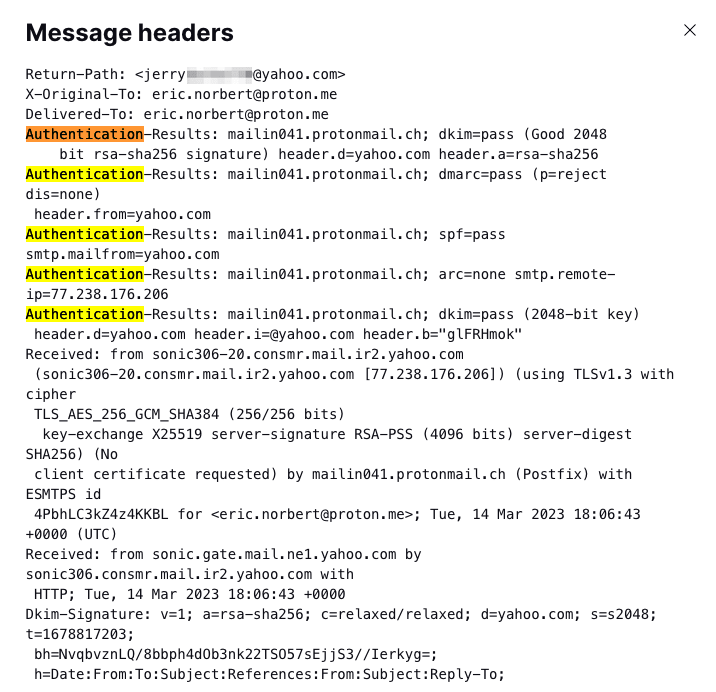
But which fields should you look at and why?
Email header fields explained
Here are the main types of metadata to look for in email headers and what they mean.
| Metadata | What it means |
|---|---|
| From | The address the message was sent from. Note that this can be spoofed. |
| To | The display names and email addresses of all the recipients, including CC and BCC addresses. As above, these details can be spoofed. |
| Subject | The title of the email as displayed in the Subject line of the email. |
| Date | The timestamp showing the day and date an email was sent; for example, Wed, 8 Mar 2023 06:07:58 +0000 |
| Received | The names and IP addresses(новое окно) of all the email servers the message passed through to get to the recipient(s). A Received header is added automatically to the top of the list after a server accepts an email. So read from the bottom up — check the bottom Received field to find the original sender’s IP address. |
| Return-Path | The address to which an email that can’t be delivered should be returned, like a return address in regular mail. |
| Reply-To | An optional address for recipients to reply to. If there is no Reply-To field, the Return-Path address is used. |
| DKIM signature | A DKIM (DomainKeys Identified Mail) signature is an authentication method that cryptographically verifies that the email hasn’t been changed since it was DKIM signed, which helps to detect spoofed emails. The Authentication-Results field should read dkim=pass with header d=[sender’s domain]. |
| SPF | SPF (Sender Policy Framework) is an authentication protocol that checks that an email was sent from an authorized IP address(новое окно). Like DKIM, the Authentication-Results field should show spf=pass. |
| DMARC | DMARC (Domain-based Message Authentication Reporting and Conformance) is an authentication protocol that prevents email spoofing by combining the results of DKIM and SPF checks. DMARC allows senders to define what happens to their emails if they fail DKIM and SPF checks. |
| Authentication-Results | Shows the results of authentication checks like DKIM, SPF, and DMARC (see above). |
| ARC-Authentication-Results | ARC is a way to preserve the authentication results (DKIM, SPF, and DMARC) of an email when it is forwarded. ARC should show dkim, spf, and dmarc=pass. |
| Message-ID | A unique identifier created for each email message. |
| Spam-Action/ Spam-Status/ Spamscore | Various spam ratings depending on the anti-spam platform used. For example, the Spam-Action field may display inbox (for non-spam), spam, or phishing. |
| Content-Type | Shows the email format, such as text/html to indicate an HTML message (rich text) or text/plain for plain text (no formatting). |
| Message-Body | The main content of the message. In Proton Mail end-to-end encrypted emails, this appears as unreadable ciphertext. |
Email header analyzers
Rather than searching the text of an email header manually, an easier way to find key fields is to use an email header analyzer, like the one by MxToolbox or Mailheader.org.
Copy and paste an email header into the analyzer tool and hit the analyze button. They not only locate the main fields for you but may also show if the message was authenticated.
Reading Proton Mail email headers
The headers in Proton Mail end-to-end encrypted messages differ slightly from those in regular emails. We include minimal metadata, so the headers are shorter, and the body of the message appears as unreadable ciphertext (starting from BEGIN PGP MESSAGE).
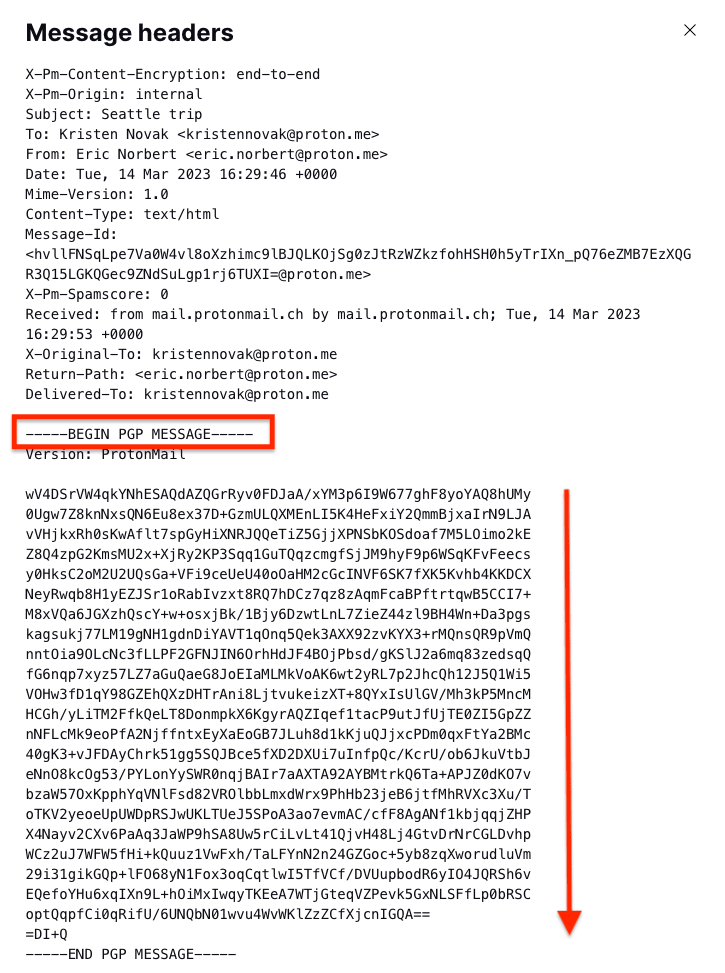
As with all emails, you can check the origins of a message in the email header if you think it looks suspicious.
Check the displayed sender and email addresses
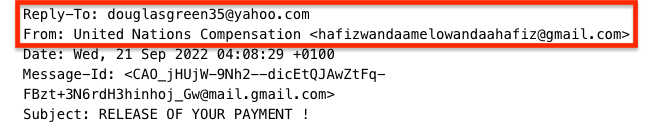
First, does the displayed sender’s name match the corresponding email addresses? In this phishing email pretending to be from the UN, the displayed name “United Nations Compensation” is clearly very different from the random @gmail.com sender address and the @yahoo.com Reply-To address.
Is the sender’s address from a domain that you trust? For example, the message below was from a Proton Mail address (@proton.me) and was delivered by mail.protonmail.ch (a trusted Proton Mail domain).
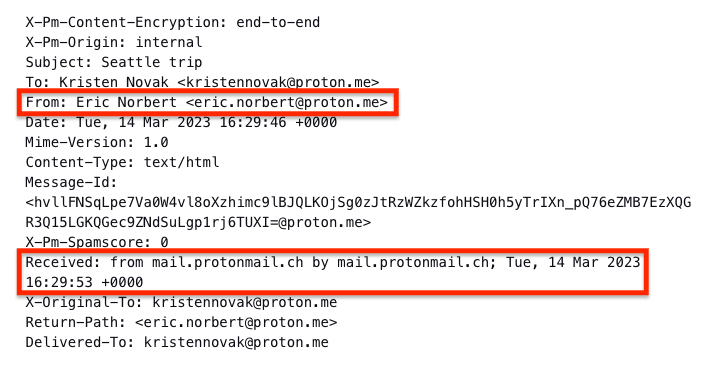
Check the Received fields
Most emails (like messages sent between Proton Mail and non-Proton Mail users) pass through several SMTP servers. Each server adds a new Received field to the top of the email header with a timestamp and server IP address(новое окно).
Reading from bottom to top, you can trace each “hop” of the email’s journey to its final destination. If there are long delays between hops or any record of the message being redirected to another address, the message may have been spoofed or tampered with.
In Proton Mail headers, we add the topmost Received field, so you can be sure it’s genuine.
Spam filtering and phishing
Finally, email service providers may include details of spam filtering in email headers. But at Proton Mail, we use a multi-tiered anti-spam system, so the spam fields in an email header won’t give you the complete picture.
You don’t need to check headers for spam because we automatically filter known spam into your Spam folder and clearly flag suspected phishing emails.
Check email headers, stay secure
Email headers contain vital details about the routing and authentication of messages. By viewing an email’s header, you can investigate a suspicious sender and check whether the message is genuine.
Yet message headers can only tell you so much. You need an email service with comprehensive anti-spam features, like Proton Mail, to beat spammers and stay secure. With Proton Mail, you get:
- Smart spam detection that automatically filters spam, custom filters, a block list
- PhishGuard advanced phishing protection that flags potential phishing attacks
- Anti-spoofing measures, like DKIM and DMARC, to protect you if you use a custom domain
Sign up for a free Proton Mail account, and you get encrypted Proton Calendar, Proton Drive, and Proton VPN(новое окно) included to protect your privacy and security. Stay secure!
Email header FAQs
Can email headers be spoofed?
You can’t spoof whole headers but can spoof individual fields in headers. Hackers can use an SMTP server to edit many header fields, like From, Reply-To, and Return-Path, to make a fake email appear to be from a legitimate sender.
The best email providers, like Proton Mail, have comprehensive spam filtering and phishing protection to flag potentially malicious messages. Still, you can investigate a suspicious message yourself by checking the email header.
What are X-headers in email headers?
X-headers are fields added to email headers in addition to standard headers like From, To, Date, etc. For example, email providers add X-headers to include authentication results and spam filtering information.
X-headers like the X-Originating-IP field, which shows the sender’s IP address, can provide useful clues when investigating suspicious messages.
Why are there so many Received fields in email headers?
When you send an email, it passes through various servers or mail transfer agents (MTA) in a series of hops. The SMTP server of each MTA adds a new Received field to the top of the email header with a timestamp and server IP address(новое окно).
Starting from the bottom Received header, you can check the sender’s email address and trace each hop of the email’s journey in the Received headers.
Can you trace an email to a specific person from the email header?
You can’t trace an email to an individual just by looking at the email header.
However, email providers, internet service providers (ISPs), and law enforcement agencies may be able to identify you from your public IP address and other metadata(новое окно). Learn more about how emails can be traced.

