Advertisers, political organizations, and other entities are quietly monitoring your email activity through tiny pixel trackers embedded in the messages you receive. These trackers can reveal when you open an email, where you’re located, and what device you’re using.
While many people don’t realize this tracking is happening, it’s yet another reason to consider moving away from free email providers like Google, which rely on ad-driven revenue. If the service is free, chances are your data and online activity are the real product being sold to advertisers.
In this article, we’ll find out what pixel tracking is and how it works, how to identify emails that contain these hidden trackers, and how Proton Mail is raising the bar for email privacy.
- What is pixel tracking?
- How pixel tracking works
- How to tell which emails track you with pixels
- Keep your inbox more private with Proton Mail
What is pixel tracking?
Also known as a web beacon or spy pixel, pixel tracking is a method used to monitor and gather data about how users interact with digital content. It does so by embedding a small, often invisible graphic (typically 1×1 pixel) in websites, emails, or advertisements.
Tracking pixels often serve one of two purposes:
- Retargeting pixels for tracking users who have visited a website but did not complete a desired action, like making a purchase. They help marketers create targeted ads and re-engage users across different platforms.
- Conversion pixels for monitoring specific actions, such as purchases or sign-ups, to measure how effective marketing campaigns are.
How pixel tracking works
When someone opens a webpage or email, a pixel tracker is “loaded” from a server, which allows the server to log this interaction. Here’s what happens:
- Embedding the snippet: A small snippet of HTML or JavaScript code containing the pixel URL is embedded in the webpage or email — usually graphics.
- Triggering the snippet: When you open the page or email, your browser or email client automatically requests the image from the server.
- Collecting data: The request logs your information, such as IP address(nuova finestra), device type, operating system, email open time, time of visit, session duration, clicks, scrolls, and sometimes geographic location.
How to tell which emails track you with pixels
To find out if an email uses pixel tracking, you can try the following methods:
1. Check email headers
Email headers contain detailed information about the email’s journey from sender to recipient, including signs of pixel trackers.
In Gmail, for example, you can click the three-dot menu next to the reply button and select “Show original” to view the full header information.
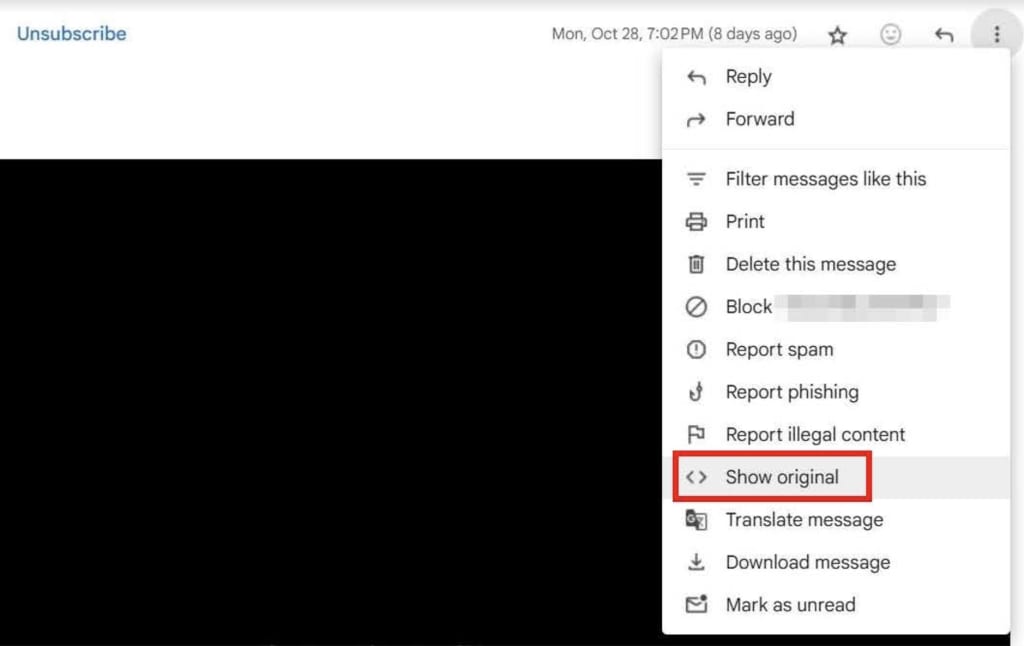
Look for terms such as “track” or “pixel” in the header. Any reference to a 1×1 pixel image hosted on an external server indicates that tracking is in place.

2. Use browser extensions
Extensions like Trocker or Ugly Email are designed to identify and block pixel tracking in emails, displaying an icon when tracking is detected. However, they only work on desktop browsers, so they won’t detect trackers if you’re checking email on mobile devices or using native email apps.
3. Use Proton Mail for enhanced tracking protection
Proton Mail has enhanced tracking protection enabled by default, which blocks known tracking pixels on all your devices. We pre-load other remote images on your behalf using a proxy with a generic IP address and geolocation. This hides your personal information and the exact time you opened the email.
The Proton Mail web app removes tracking parameters from URLs, so you can safely click links knowing that the sender can’t monitor your behavior. Additionally, you can view the number of blocked trackers and cleaned links for each email.
Keep your inbox more private with Proton Mail
If you want to take your email privacy to the next level by blocking tracking pixels and safeguarding your online activity, consider switching to Proton Mail, a secure, free email service that features end-to-end encryption.
Besides enhanced tracking protection, Proton Mail provides hide-my-email aliases that allow you to sign up for online services or subscribe to newsletters without exposing your real email address.
By using aliases, you can receive fewer emails with tracking pixels, limit your exposure to spam and phishing attempts, and keep your inbox more private. Plus, the link confirmation feature, which is enabled by default, asks you to confirm before opening an external link.
Moving your email account to Proton Mail is simple with the Easy Switch feature, which syncs your emails, calendars, and contacts securely in one click.
Making the move to Proton Mail is just the first step if you want to deGoogle your life, as Proton Mail is part of a larger encrypted ecosystem designed to protect your data, including passwords, internet connections(nuova finestra), cloud storage(nuova finestra), calendar, and digital assets.