Anti-spoofing for custom domains (SPF, DKIM, and DMARC)
While there are great benefits to email’s open and decentralized nature, this freedom also makes email easy to abuse. For example, any server connected to the internet can send an email to your friend pretending to be from you, an attack known as email spoofing.
We strongly recommend that everyone who uses a custom domain with Proton Mail set up SPF, DKIM, and DMARC to ensure your emails are properly delivered.
Read on to see how we can protect your custom domain from these kinds of attacks.
SPF
The Sender Policy Framework (SPF) record basically tells the world which hosts or IPs are allowed to send email for your domain. When email servers receive an email that claims to be from your domain, they can look up your SPF record to see if the sending server is included.
While not required, we strongly recommend that you set up an SPF record that includes Proton Mail.
This will not only make your email seem more legitimate and thus less likely to be sent to spam folders, but it will also help protect your domain from attackers who send emails with forged headers pretending to be from you.
In your browser, log in to your Proton Mail account, go to Settings → All settings → Domain names, and click Review next to the domain you want to add an SPF record for.
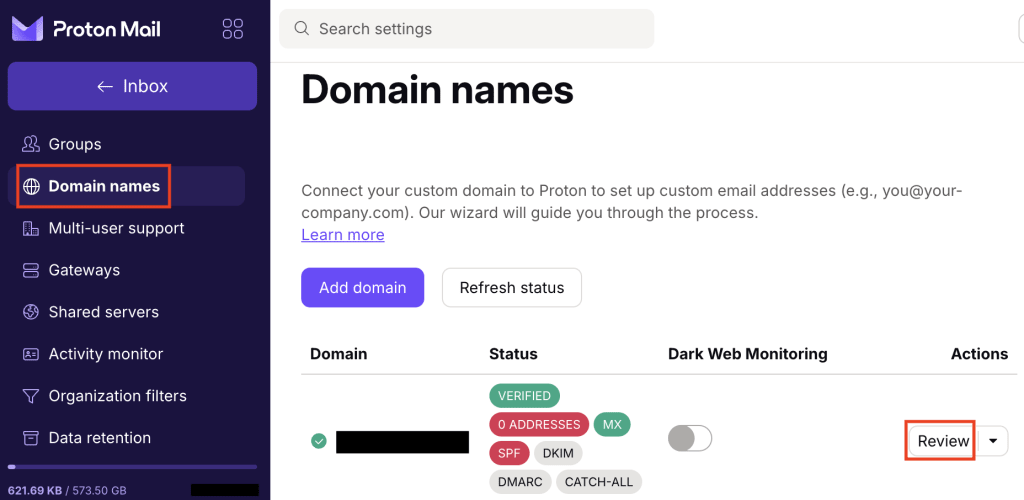
Select the SPF tab. This shows the recommended SPF record to add to your registrar’s domain management portal. You can click on the small icon to the left of the entry to Copy it to your system’s clipboard.

The “include:_spf.protonmail.ch” part of the text string means that you allow Proton Mail servers to send on behalf of your domain. If you want to keep an existing SPF record, simply add the “include:_spf.protonmail.ch” text string to it right of your existing record, after the “v=spf1”. The “mx” also includes your domain’s MX records.
The “~all” part means that if the email is sent from any servers not included in the text string, it will be treated as a SoftFail. This means that the receiving mail server will accept the email delivery but will mark it as SPF failed. The alternative is to use the “-all” (HardFail) parameter.
This will cause the email to be rejected, which can cause delivery problems for legitimate emails. For example, SPF often fails during email forwarding, where you send to address A, which automatically forwards to address B. Once we detect your domain’s SPF record includes Proton Mail, the SPF tab will show a green tick icon.
DKIM
Domain Keys Identified Mail (DKIM) is a method of email authentication that cryptographically verifies if an email was sent by trusted servers and has not been tampered with.
Basically, when a server sends an email using your domain, it will calculate an encrypted hash of the email contents using a private key (that only trusted servers know) and add it to the email headers as a DKIM signature.
The receiving server will verify the email contents by looking up the corresponding public key in your domain’s DNS records, decrypting the encrypted hash, and calculating a new hash based on the email contents it received. It then compares the decrypted hash to the new hash. If there is a match, then the email has not been tampered with, and so DKIM passes. Otherwise, DKIM fails, and the email is treated with suspicion.
Learn more about DKIM management(neues Fenster)
We use CNAME records to manage automatic DKIM key rotation, which is an accepted security best practice. We ask you to add and keep three CNAME records. This ensures there is always an active key used to provide an uninterrupted service while the other keys are automatically retired and recreated on a regular basis for improved security.
It all sounds complicated, but implementing DKIM for your domain is simple in Proton Mail. It will take a couple of hours to verify your custom domain when you first change its DNS records for use with Proton Mail. Once your custom domain is verified, Proton Mail will generate the host names and values you will need for your domain’s DNS portal. It will then create the CNAME records necessary for automatic DKIM key rotation.
We will send you an email notification informing you that your custom domain, host names, and values, are ready.
New users
In your browser, log in to your Proton Mail account and go to Settings → All settings → Organization → Domain names → Actions column → Review button next to the domain you want to add a DKIM record for.
Select the DKIM tab. Here you will see the three host names and values that you will need to add to your domain’s DNS settings.

Once you have added these records, Proton Mail will handle the rest for you. Following current security best practices, we will generate a new 2048-bit key every six months and use it to sign your emails.
The CNAME records you add to your domain’s DNS settings must be an exact match with the ones shown in your setup wizard. Once we detect these records in your DNS, the DKIM tab will show a green tick icon. We will then notify you and start signing outgoing emails from your custom domain with DKIM, just like we do for other Proton Mail addresses.
IMPORTANT: Some registrars do not accept CNAME values with a period at the end (while others require it). If your registrar does not accept your CNAME records, delete the period at the end of each CNAME value and try again.
Users that currently use manual DKIM key rotation
We strongly advise everyone that currently uses manual DKIM key rotation to upgrade to the new automatic key rotation system. Not only will this remove the need for you to rotate your keys manually, but it will also automatically upgrade your key strength (if you were using 1024-bit keys).
If you have previously configured manual DKIM key rotation for your domain using a TXT record, you need to remove this record from the DNS settings before entering the CNAME records.
You need to reconfigure your DNS settings with CNAME records because they allow us to set up automatic key rotation, while your current TXT record does not.
Once you have deleted this TXT record, you can follow the instructions for new users. DKIM will stop signing your emails once you delete the TXT record. To maintain DKIM protection, you should enter your CNAME Host Names and values into your DNS settings immediately.
DMARC
While learning about SPF and DKIM (above), you may have wondered how the receiving server deals with an email that fails the checks. This is where Domain-based Message Authentication, Reporting, and Conformance (DMARC) comes in.
DMARC allows the domain owner to specify what happens with failed emails and get feedback when they arrive. Basically, there are three actions receiving servers can take if BOTH SPF and DKIM checks fail: none, quarantine, and reject.
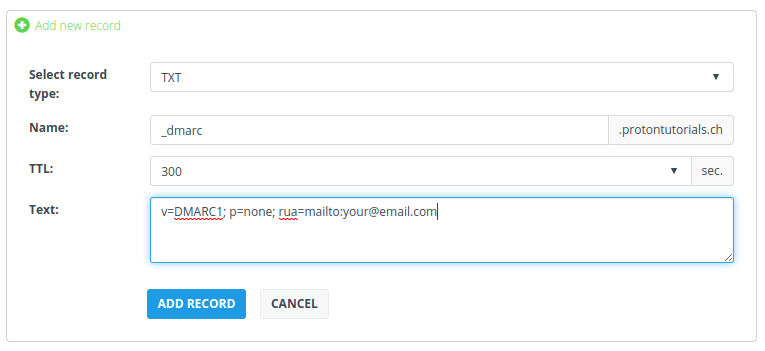
In your browser, log in to your Proton Mail account and go to Settings → Go to settings→ Organization → Domain names → Actions column → Review button next to the domain you want to add a DMARC record for.

Copy the DMARC TXT host name and value string and add it to your domain in your registrar’s domain management console.

The “p=” value specifies the action to take for emails that fail DMARC. Here are the available actions:
- p=quarantine: asking the recipient platforms to mark the unauthorized emails as spam or quarantine them.
- p=reject: asking the recipient platforms to reject the unauthorized emails.
- p=none: do not quarantine or reject unauthorized emails. Usually, people only use this policy to troubleshoot or test.
The default setting is none. However, to improve your security we recommend setting this value to p=quarantine.
Once you are confident that your legitimate emails are passing DMARC, you may want to set it even more aggressively to p=reject. We recommend doing so if you think you are likely targeted for email spoofing. For example, Yahoo, PayPal, and eBay use p=reject to prevent spammers from impersonating them.
Another parameter is rua=, which specifies an email address where other email services can send aggregate reports so you can see how many of your emails are failing DMARC.
Please keep in mind, however, that there are risks in choosing more aggressive DMARC actions. For instance, when you email a mailing list that then forwards to individual recipients, this will break SPF. Annoyingly, some mailing lists also change the contents of the email, which breaks DKIM and causes DMARC to fail, creating delivery issues if you have set DMARC to quarantine or reject. This is why DMARC is set to none by default.
Test email
Once you have a custom domain set up, you can test it by sending an email using Mail Tester(neues Fenster).
Simply send an email using your custom domain address to the unique address shown on the Mail Tester web page. Then check your spammyness score.

If you have both SPF and DKIM set properly, you should be able to score 10/10!