This article was refreshed in September 2025 to reflect the latest changes and updates to the services discussed. We’ve also added SimpleX Chat to the list.
Learn about the best end-to-end encrypted messaging apps to replace WhatsApp with that ensure your online chat remains private.
Tens of millions of WhatsApp users have flocked to more private messaging apps ever since the app revealed it shares personal data with Meta (Facebook)(neues Fenster), its owner. And there are other security and privacy concerns around WhatsApp.
Here we look at apps similar to WhatsApp that genuinely respect your privacy.
- What’s wrong with WhatsApp?
- What to look for in a WhatsApp replacement
- End-to-end encryption
- Minimal metadata logged
- Open-source transparency
- Best apps like WhatsApp
- Signal
- Telegram
- Threema
- Wire
- Element (was Riot.im)
- Olvid
- Session
- SimpleX Chat
- Choose a chat app for privacy
- WhatsApp alternatives: FAQs
What’s wrong with WhatsApp?
WhatsApp uses end-to-end encryption, which means the messages are encrypted on your device and can only be decrypted on the device of the intended recipient. So the actual messages are secure on the platform.
But this does nothing to protect your metadata. That’s information about who you communicate with, from where, at what time, how often, and from which device.
Since WhatsApp changed its privacy policy in 2021, it now shares its users’ metadata and transactional data with Meta, a company notorious for disregarding privacy. If you’re still on WhatsApp, it’s time to switch to something more private.
In 2025, WhatsApp announced it would begin showing ads on its Status screen(neues Fenster) (the WhatsApp version of Instagram’s Stories). While Meta, WhatsApp’s parent company, said the ads won’t use personally identifiable data to target the ads, like your phone number, messages, or groups, it will look at the country and language you have in your settings and the channels you subscribe to.
Learn more about how safe WhatsApp is to use
What to look for in a WhatsApp replacement
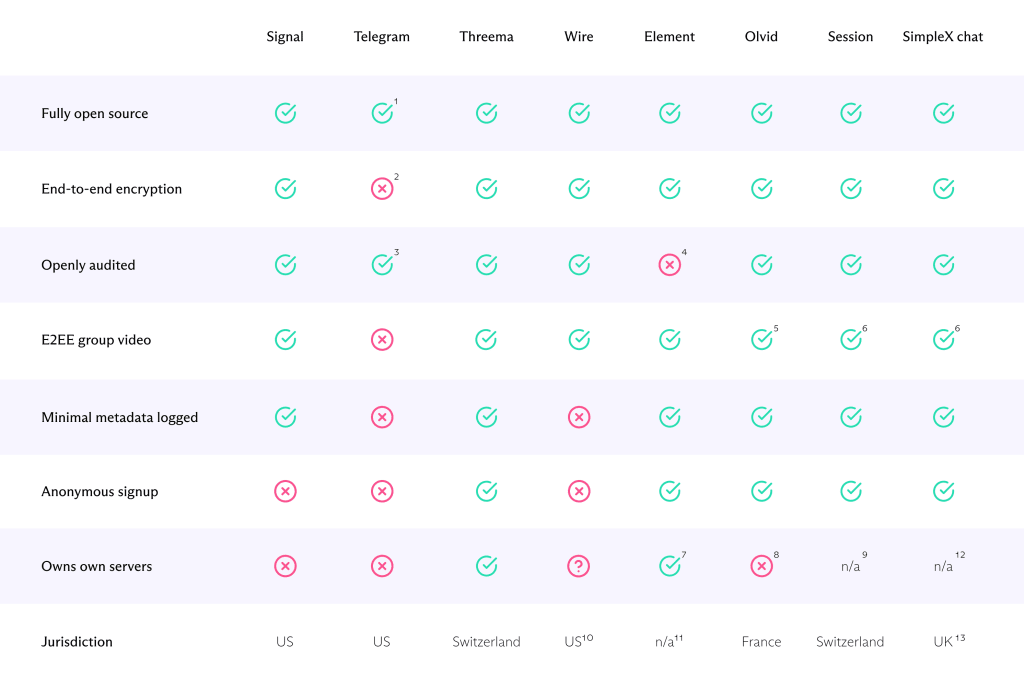
Look for the following three characteristics when choosing a private messaging app:
End-to-end encryption
End-to-end encryption is a core requirement for any messenger app that claims to be secure and private. With end-to-end encryption, only you and the person you send a message can read it.
Minimal metadata logged
All messaging apps need to collect some metadata to operate. Choose an app that records minimal metadata and check what it shares with third parties.
Open-source transparency
If an app makes its code public, anyone can examine it to ensure the app is secure. We believe open source is one of the best indicators that an app can be trusted.
Best apps like WhatsApp
Here’s our pick of the best WhatsApp alternatives, in no particular order. We’ve limited our choice to open-source messaging apps that use end-to-end encryption (E2EE).
Signal
Pros
- Free
- Very good encryption
- Collects almost no metadata
- Protocol independently audited
- Disappearing messages
- E2EE text, voice, and video group chat
- Easy contact discovery
- Encrypted cloud backups (alpha, optional)
- Usernames can be used to message without sharing your phone number
Cons
- Requires a valid phone number to sign up (but you can now hide it from others and instead use a username)
- Hosted on Amazon Web Services (AWS)
Signal uses an end-to-end messaging protocol developed by the Signal Foundation(neues Fenster), a non-profit organization founded by cryptographer and privacy activist Moxie Marlinspike.
The Signal Protocol is open source, professionally audited for security vulnerabilities(neues Fenster), and widely admired(neues Fenster) for its cryptographic strength.
Because the protocol is so good, it’s used by various third-party messaging apps to provide secure end-to-end encryption for messages. These include WhatsApp, Facebook Messenger, and Skype. But unlike WhatsApp and other third-party apps that use the protocol, the Signal app is 100% open source.
Crucially, Signal keeps almost no metadata related to the app’s usage. Only “the date and time a user registered with Signal and the last date of a user’s connectivity to the Signal service”. This is a claim that has been proven in court(neues Fenster).
However, the app itself has not been audited, and some security concerns(neues Fenster) exist around Signal’s reliance on Intel Software Guard Extensions (SGX). In theory, this could result in users’ metadata and data (but not messages) being compromised at the server level. This is a particular concern because Signal uses Amazon Web Services to host its infrastructure, which is subject to legal demand from the US government.
Signal has withdrawn SMS support for Android devices, which removes one of its more unique selling points. But its argument that this will improve user security is a valid one.
One of the main criticisms of Signal is that users must register with a valid phone number to match contacts. However, since 2024, you can create a username and hide your phone numbers from others, even in group chats. It should also be noted that contacts are stored locally only and cannot be accessed by the Signal Foundation. This setup also makes it relatively easy to find other people you know who use Signal.
In addition to messages, Signal supports disappearing messages, E2EE group voice chats, and now group video chats between up to 40 users. It is also testing optional encrypted cloud backups(neues Fenster), which will be available to free users, but also as enhanced premium tier.
Signal is a non-profit organization that relies on donations to operate.
Learn more about how safe Signal is
Telegram
Pros
- Free
- Channels for broadcasting messages
- Bots for managing groups
- Syncs across multiple devices (not E2EE)
- Polls, stickers, sharing live location, identity management
- E2EE group text, voice, and video chat
Cons
- Encryption concerns
- Only Secret Chats are E2EE for text conversations
- Group chats (text or voice) are not E2EE
- Collects lots of metadata
- Requires a valid phone number to sign up
- Headquartered in the UAE, which is not known for human rights or privacy from the government (despite having some strong privacy laws(neues Fenster))
With over one billion(neues Fenster) monthly active users, Telegram(neues Fenster) is a very popular WhatsApp alternative. A big part of this popularity is the widespread perception that Telegram is highly secure, a perception only heightened by a number of governments, notably Indonesia, Russia, and Iran, trying to block or ban the app.
There are, however, some big caveats regarding Telegram’s security. Regular default “cloud-based messages,” which can be accessed on any of a user’s devices, are encrypted in transit and when stored on Telegram’s servers. But they’re not end-to-end encrypted. For text messages, only client-to-client “secret chats” are end-to-end encrypted. Secret Chats are not available for groups or channels. However, as of April 2015, group voice and video calls are E2EE by default(neues Fenster).
Security experts have criticized(neues Fenster) the open-source in-house MTProto encryption used to secure communications in Telegram (whether E2EE or otherwise), although the new version (MTProto 2.0(neues Fenster)) has been formally verified(neues Fenster) to be cryptographically sound. The Telegram API and all Telegram apps are open source, but its server-side backend is not.
Another issue is that Telegram may collect a great deal of metadata(neues Fenster) from users: “We may collect metadata such as your IP address, devices and Telegram apps you’ve used, history of username changes, etc.”
On the other hand, Telegram has built its own secure cloud infrastructure distributed across the globe. The encryption keys used to secure the Telegram Cloud are split into pieces and never stored in the same place as the information they protect.
Security considerations aside, a key feature that contributes to Telegram’s popularity is “channels”. Users can create and post to channels that any number of other users can subscribe to. This has proved especially popular in repressive countries like Iran, where Telegram has over 40 million users despite government attempts to block the service.
You can create public channels using an alias and a URL that anyone can subscribe to, making Telegram a powerful tool for organizing resistance and disseminating information.
Other features that help make Telegram popular include polls, stickers, sharing live locations in chats, and an online authorization and identity management system for those who need to prove their identity. A bots feature assists with managing groups and channels.
Telegram is funded mainly by public donations (notably from its own founder, Pavel Durov(neues Fenster)), although its apps now offer in-app purchases. As of April 2025, owners of large channels can earn revenue(neues Fenster) from these ads, paid exclusively in Telegrams’ own crypto-currency (Toncoin).
Learn more about how safe Telegram is(neues Fenster)
Threema
Pros
- Requires no phone number or email to sign up
- Keeps almost no metadata
- Independently audited
- Swiss-based with own servers
- GDPR compliant
- E2EE group text, voice, and video chat
- Group polling and distribution lists (Android ans iOS/iPadOS)
- Can be purchased with Bitcoin
Cons
- Not free
- Relatively small user base
Like Proton, Threema(neues Fenster) is based in Switzerland, a country with strong data privacy laws and independent from the United States and European Union. It also owns its own server infrastructure located in Switzerland.
All of Threema’s apps use the open-source NaCl cryptography library(neues Fenster) to end-to-end encrypt its messages and have been audited by security professionals(neues Fenster).
You don’t need an email address or phone number to register an account, and it’s possible to purchase Threema for Android anonymously using Bitcoin. Threema claims this allows you to text and make calls anonymously, and it goes to lengths to ensure that it collects minimum metadata(neues Fenster).
The fact that the app is not free is likely to be a pain point for some, but at around US$4.99 (one-time purchase), it’s unlikely to break the bank for most. This may contribute, however, to one of Threema’s biggest downsides: its relatively small user base.
The mobile apps feature distribution lists, allowing you to send messages to multiple recipients. In addition to fully E2EE group text, voice calls, and now video calls with screensharing (for up to 16 people), Threema offers a group polling feature.
Note that Threema also offers a Threema Work app, which is beyond the scope of this article.
Wire
Pros
- Free option
- E2EE text, voice, and video group chats
- Syncs across up to eight devices
- Advanced video conferencing features
Cons
- Collects quite a lot of metadata (and possibly stores it in plaintext)
- Requires phone number or email address to sign up
Wire(neues Fenster) is another service based in privacy-friendly Switzerland. A phone number or email is required to register. To facilitate syncing across multiple devices, however, Wire keeps quite a lot of metadata.
For years, Wire kept a list of all users a customer has contacted(neues Fenster) in plaintext on their servers until an account is deleted. Its privacy white paper(neues Fenster) now simply states that “server-side logs are only kept for a maximum of 72 hours, for the sole purpose of facilitating troubleshooting, improving the service, and preventing abuse”.
The functional benefit of this is that it allows Wire to work across multiple devices in a way most E2EE messenger apps (including Signal) do not. It’s also worth noting that Edwa(neues Fenster)r(neues Fenster)d Snowden recommends Wire (or Signal)(neues Fenster).
Wire uses the Proteus protocol to provide end-to-end encryption for text messages. Proteus is an early fork from the code that later became the Signal Protocol. Proteus(neues Fenster) and all Wire apps(neues Fenster) have been publicly audited.
Voice calls (up to 25 participants) and video calls (up to 12 for free users) are end-to-end encrypted using DTLS(neues Fenster) with an SRTP(neues Fenster) handshake.
The app also has advanced video conferencing features that will appeal to business users, including screen sharing, screen recording, and advanced meeting scheduling.
Wire is keen to push users toward its premium Pro and Enterprise products, but a free version is available with similar features to the Pro app.
Element (was Riot.im)
Pros
- Free option
- Server federation via the Matrix protocol
- “Bridges” for interoperability with other apps
- E2EE text chat
- Requires no phone number or email to sign up
Cons
- Questions over Matrix server network reliability
- Not fully audited
All the other messenger apps discussed in this article rely on a centralized server network to function (although, as in the case of using AWS, this can be a highly distributed network).
Element(neues Fenster) is instead built on the idea of federation. Users can set up their own servers using the Matrix communications protocol(neues Fenster) or connect to Matrix servers that other users have set up. Federation has received the support of Edward Snowden(neues Fenster) but remains controversial due to the potentially unreliable ad-hoc peer-to-peer nature of such a network.
Matrix servers are interoperable, so any user of any Matrix client(neues Fenster) (Element is the most popular) can communicate with any other Matrix user. Matrix “bridges” even allow for communication with the users of other popular messaging platforms, such as Signal, Slack, or even WhatsApp.
Matrix (and thus Element) uses the Olm implementation of the Double Ratchet algorithm(neues Fenster), with Megolm used for group communications. All Element apps, plus the Matrix protocol itself, are open source but haven’t been formally audited. But Olm and Megolm have been audited(neues Fenster).
An email or phone number is not required to register with Element, although you can add them to make contact matching easier. By default, messages are hosted on a large public server run by Matrix, but you can connect to any Matrix server or set one up yourself in seconds.
All text chats and 1:1 voice and video calls are end-to-end encrypted. Group voice and video calls (which also allow screen sharing) now use Element X and Jitsi, with partial E2EE support(neues Fenster). The Element app is free, but premium plans are available for Element-managed Matrix servers.
Olvid
Pros
- Requires no phone number or email to sign up
- Encrypts most metadata is encrypted
- Independently verified and certified E2EE encryption
- Group chats with voice calls, multiple profiles, ephemeral messages, and remote deletion
- Most features available to individuals for free
- Advanced enterprise features
- Extensively audited
- End-to-end authentication
- Video calls for up to three participants
Cons
- Relatively small user base
- Outgoing voice calls require a premium subscription
- Centralized servers can log IP address (but don’t)
- No contract discovery
Winner of the 2020 Les Assises Innovation Prize(neues Fenster), Olvid(neues Fenster) is an open-source messenger app (the servers aren’t open source). Unlike Signal, there is no need to register a phone number, so the app can be used without a SIM card.
Also unlike Signal (and most other messaging apps), Olvid keeps no centralized user directory. This means there is no contact discovery, but it also makes it impossible for anyone but your chosen contacts to discover your public key. Olvid describes this as end-to-end authentication, meaning that you must authenticate your contacts yourself.
Almost all metadata is encrypted. The Olvid website states that all metadata is encrypted, but Olvid uses centralized servers that could log your IP address when you connect to them. Olvid says it keeps no such logs, but servers can be compromised. You can easily mitigate this issue by using a VPN.
The use of centralized servers is not otherwise a concern. The servers act as “dumb” drop boxes, using public-key cryptography (public/private key pairs) to ensure only you and your intended recipient(s) can access your messages. Your encrypted message is stored on Olvid servers using one-time symmetric keys with a double-ratchet protocol.
Olvid notifies your recipient about your message, which only they can decrypt (on their own device). Olvid then deletes your message from its server. The use of public/private key pairs guarantees authentication, ensuring only your intended recipient(s) can open your message.
Olvid has published a detailed white paper(neues Fenster) explaining the cryptography it uses, which has undergone multiple formal verifications(neues Fenster). Olvid’s cryptography has also received certifications from the French National Agency for the Security of Information Systems(neues Fenster) (ANSSI). The full reports for these are openly available on the Olvid website.
Like most other messengers here, Olvid also relies on Apple and Google for push notifications, although Android users can opt to use a permanent WebSocket connection to Olvid’s message distribution server instead.
Olvid offers secure group chats with audio calls, multiple profiles, ephemeral messages, and remote deletion of messages. You can also make secure three-way video calls. The basic service for individuals is free and includes most features except the ability to make outgoing voice calls. Enterprise plans are available with advanced group management, MDM and SSO integration, and more.
Session
Pros
- Free, but with optional premium tier
- Based on Signal
- Requires no phone number or email to sign up
- Decentralized onion network
- All IP addresses hidden
- Collects minimal metadata
- Audited (in 2021)
- Headquartered in Switzerland
- Group chats
- Voice messaging, disappearing messages, voice and video calls (beta)
Cons
- Buggy
- No group video or voice calls
- Blockchain/crypto aspect may put some people off
Session(neues Fenster) is a fork of Signal, and on paper, it offers many advantages over Signal. You don’t need a phone number to sign up — instead, you are issued a unique, randomly-generated Session ID that you can share with your contacts.
Session also greatly improves anonymity by using an onion routing system (similar to Tor) to send messages through multiple volunteer-run nodes. This ensures neither the Swiss-based not-for-profit Session Technology Foundation (STF)(neues Fenster) (which replaced the Australia-based Oxen Privacy Tech Foundation(neues Fenster) — OFTF — in October 2024) nor the recipient can see your IP address when you send messages.
The decentralized nature of the Session network also greatly improves its resistance to censorship and ensures there’s no one point of failure.
Somewhat controversially, this decentralization is achieved using blockchain technology. Until May 2025, Session ran on the Oxen Service Node Network(neues Fenster) with the Oxen cryptocurrency. Since then, it has migrated to the new Session Network(neues Fenster), which uses its own ecosystem token, SESH, to incentivize node operators and support optional premium features. It’s developers are keen to point out to crypto-skeptics that there is no need for users to interact with the cryptocurrency if they don’t want to.
Session leaks minimal metadata. A white paper(neues Fenster) is available that explains its technical security, and the app underwent a security audit(neues Fenster) in 2021. It’s important to note that if you enable push notifications, which most people will, the server sending the push notifications will know your real IP address.
The app supports E2EE closed group chats of up to 100 people at once (which are more stable(neues Fenster) than previously), disappearing messages, and file attachments. You can also host large public or semi-public group chat spaces inside Session, know as Communities that can accommodate thousands of participants. However, these are not end-to-end encrypted.
One-to-one voice and video calls are now a standard feature, but group calls are not yet supported. Early concerns about IP leaks during the beta phase have been addressed.
This is all great, but Session is still often very buggy in use. Notably, message notifications often arrive late (or never at all), and messages can take hours to arrive.
It’s also worth noting that while Session continues to offer a free tier, a premium Session Pro Beta plan offers higher message character limits, more pinned conversations, higher group member limits, and more.
SimpleX Chat
Pros
- Free
- Requires no phone number, email, or username to sign up
- No persistent identifiers — strongest anonymity of any messenger
- Encrypts both messages and metadata (including timestamps)
- Extensively independently audited
- Supports voice and video calls, ephemeral messages, and large file transfers
- Tor integration and optional hidden profiles for advanced anonymity
Cons
- Small user base
- Less user-friendly than mainstream apps
- Still evolving, with occasional bugs and rough edges
- Its strong anonymity features have attracted misuse by extremist groups
SimpleX Chat(neues Fenster) is a new messaging contender, notable for radical focus on privacy. Unlike almost every other messenger, it requires no phone number, email address, or even username to create an account. Instead, every connection is established using one-time invitation links or QR codes, meaning no central directory of users exists. This design makes it impossible to correlate activity between accounts, even if servers are compromised (a white paper(neues Fenster) explains this in detail).
SimpleX Chat does rely on servers to relay messages, but these servers are untrusted, stateless, and only act as temporary “dumb” message brokers. Messages are stored in encrypted form using ephemeral queues and deleted once delivered. This means servers cannot build lasting metadata about who is communicating with whom. It’s fully open-source code has undergone a number of independent audits(neues Fenster).
SimpleX Chat is based in the UK, and is therefore subject to intrusive surveillance laws(neues Fenster). However, because SimpleX doesn’t maintain user identifiers or contact directories, it has little or no useful data to disclose. The company has says that the UK Online Safety Act does not apply(neues Fenster) to SimpleX, as it doesn’t host user-generated content in a conventional sense.
The multi-platform app supports disappearing messages, multiple profiles, secure voice and video calls, and integrates with Tor for added anonymity. Android users can also use a WebSocket connection instead of Google or Apple push notifications.
As with many of the promising options discussed in this article, SimpleX Chat suffers from being very niche compared to the likes of Signal or Telegram. Unfortunately, though, it’s use has gained some traction among extremist groups(neues Fenster). Its unusual design may also be somewhat unintuitive for new users.
Choose a chat app for privacy
As a replacement for WhatsApp as a general-purpose messenger that genuinely respects your privacy, Signal remains an obvious choice in 2023. Being hosted on AWS servers remains a concern in light of its reliance on SGX, but easy contact discovery and a wealth of advanced features make Signal the app you are most likely to convince your friends and family to use.
The security concerns around Telegram make it harder to recommend as a simple messenger, although its “channels” feature remains a powerful tool for organizing resistance in restrictive countries.
Session looks very promising on paper, but its many reliability issues mean that, for most people, it simply isn’t ready for prime time just yet. This may change, but it faces a strong challenge from newcomer SimpleX, which, while sill very niche, sports impressive privacy credentials without Session’s reported reliability problems..
The other apps discussed above all offer useful features that will appeal to those who need them, whether it’s anonymous signup, business collaboration tools, or server federation. Element/Matrix is a particularly strong choice for privacy enthusiasts, although its niche user base severely hampers its practicality as a WhatsApp replacement. Olvid is also notable for the care it takes to minimize metadata and end-to-end authentication (albeit at the cost of easy contact discovery).
An alternative for secure communication is end-to-end encrypted email(neues Fenster). Proton Mail is based in Switzerland and open source. And with Proton Mail’s Password-protected Emails, you don’t need your recipient to use the same messenger service to benefit from end-to-end encryption. You can send end-to-end encrypted messages to anyone who has an email address.
As you take back your privacy in the digital age, anything you do to move more of your personal data behind strong encryption is an important step toward building an internet that puts people first.
WhatsApp alternatives: FAQs
What are the dangers of using WhatsApp?
Since 2016, WhatsApp has shared the vast majority of its users’ transactional data and metadata(neues Fenster) with Meta (Facebook). This only came to light in 2021, when WhatsApp issued an updated privacy policy. Existing users had to accept the terms of the policy or lose access to their accounts.
Information shared by WhatsApp with Meta includes your IP address, device ID, operating system, browser details, mobile network information, who you message, how long and how often you interact with them, transaction and payment data, and more.
Is WhatsApp chat private?
Messages in WhatsApp are end-to-end encrypted using the Signal protocol. This means only you and the intended recipient(s) can read your actual messages. So WhatsApp is secure. It does, however, collect a lot of metadata that is damaging to your privacy (see above).
What is the safest messaging app?
All the apps listed here are highly secure (with the possible exception of Telegram).
How can WhatsApp be free?
WhatsApp is owned by Meta (Facebook), which makes a huge amount of money by invading users’ privacy to target them with personalized ads. WhatsApp adds to the data Meta knows about you by sending a great deal of metadata regarding your use of WhatsApp to Meta.
As Signal and some of the other apps discussed in this article show, it is possible to offer a free messaging app without invading users’ privacy in this way.
Footnotes:
1. All Telegram apps are open source, but the backend isn’t. This would not really be an issue if all communications were E2EE, but they are not by default (and no group chat is E2EE).
2. By default, Telegram chats are not end-to-end encrypted. Only client-to-client “secret chats” are. Secret chats are not available for groups or channels.
3. The 2015 audit of MTProto protocol was not very favorable. MTProto 2.0 has been formally verified to be cryptographically sound.
4. The Element apps and the Matrix protocol have not been formally audited. However, the Olm and Megolm protocols that underpin Matrix have.
5. But E2EE voice chat is available for up to 3 people. Only premium users can initiate voice calls.
6. Available in beta at time of writing, Doesn’t hide participants’ IP addresses
7. Element and/or Matrix don’t actually own their own servers, but new Matrix servers can be set up within minutes on any server platform (or can be self-hosted). It is therefore almost impossible to shut down or block access to the Matrix platform.
8. Olvid is uses servers hosted on AWS, but this should have no impact on the security of the service.
9. Uses a decentralized onion network of volunteer-run nodes
10. Wire is based in Switzerland, and all users outside the United States are subject to Swiss law. US users, however, are subject to US law.
11. Matrix is a community-developed open-source platform whose federated servers can be hosted anywhere in the world.
12. Messages are stored in encrypted form using ephemeral queues and deleted once delivered
13. Shouldn’t matter, as little or no useful data is exposed
Feel free to share your feedback and questions with us via our official social media channels on Twitter(neues Fenster) and Reddit(neues Fenster).