If you’re one of the 2.5 billion people who use Gmail(nuova finestra), you need to be particularly careful when going through your emails. Google recently acknowledged a surge in effective and convincing phishing attacks(nuova finestra) targeting Gmail and Google Workspace users.
The latest wave of phishing uses information from a massive data breach of one of Google’s Salesforce databases(nuova finestra). Though no passwords were leaked, this breach contained general data like customer and company names that attackers have used to make their phishing and vishing attempts more persuasive.
Google’s latest data breach
On August 5, Google published a blog post(nuova finestra) detailing how the hacker group known as ShinyHunters broke into one of its Salesforce databases that stored information about small and medium-sized businesses. They were able to gain access by impersonating a company’s IT support desk on a phone call and tricking an employee into uploading malicious software. ShinyHunters then used that software to exfiltrate data on millions of users.
Google is far from ShinyHunters’ only victim. The group is accused of being behind the massive breaches of Salesforce databases for the Australian airline Qantas(nuova finestra), the insurance company Allianz Life(nuova finestra), Cisco(nuova finestra), Louis Vuitton(nuova finestra), and Adidas(nuova finestra). And that’s just this year.
Gmail security warning
According to Google’s threat research team, phishing and vishing attacks now account for 37% of successful account takeovers across Google services and can take several forms. Some use Gmail “suspicious sign in prevented” emails(nuova finestra) or other emails that appear to come from Google itself.
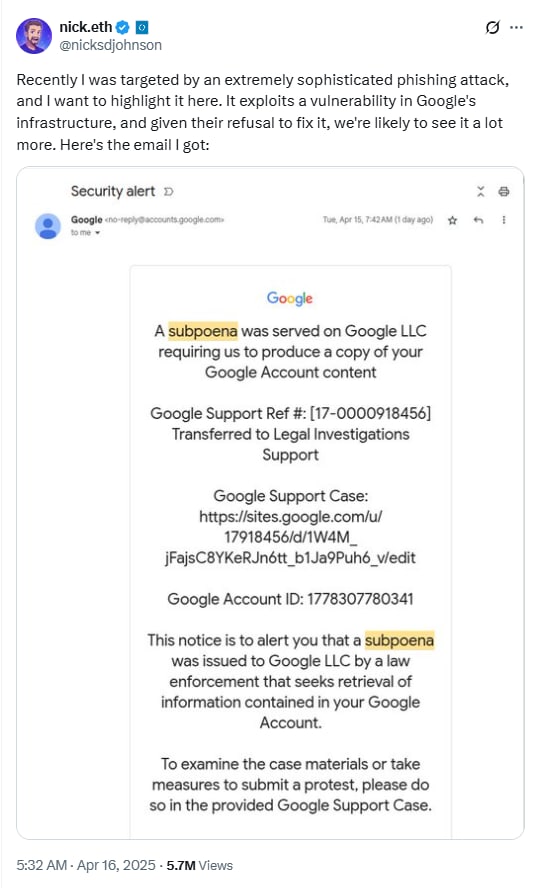
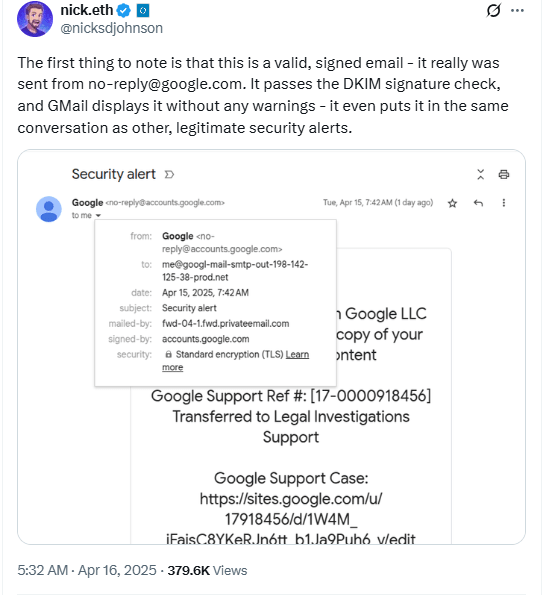
Others involve phone calls from people pretending to be Google support staff(nuova finestra) trying to fool people into sharing their password. A typical vishing phone call works as follows:
- A person claiming to be a Google employee will contact you by phone (typically using a phone number with a 650 area code) and inform you that suspicious access attempts were detected on your Gmail account.
- Then the person attempts to get you to reset your password under the guise of keeping your account secure.
- Once this is done, the scammer can lock you out of your Gmail account.
The attackers even managed to manipulate Google’s AI responses(nuova finestra) to make it harder to identify their social engineering attempts.
The easiest way to avoid falling for a vishing attack is to ignore them. Google will never call you unprompted to warn you about a security issue. If you receive one of these calls, simply hang up.
There’s also a “dangling bucket(nuova finestra)” attack that specifically targets Google Cloud users. While this doesn’t affect Gmail directly, it highlights the growing sophistication of cloud-targeted phishing. In this case, the scammers use outdated access addresses to inject malware into your Google Cloud project, taking it over. Preventing these attacks is more complicated, but Google has a guide on how to securely manage storage buckets(nuova finestra).
How to protect your Gmail account now
To protect your Gmail account (and everything tied to it), here are four steps you should take today:
- Set a new, strong password.
- Set up a non-SMS form of two-factor authentication (2FA).
- The best solution to secure Gmail is to set up a passkey.
- Use Google’s Advanced Protection Program(nuova finestra).
Choose Proton for stronger protection
You can’t prevent data breaches, but you can choose end-to-end encrypted services that give you control of your data:
- Proton Pass, our secure password manager, helps you create, manage, and share secure passwords and passkeys.
- Proton Authenticator, our 2FA authenticator app, gives you a private way to use 2FA, no account required.
- Proton Mail our encrypted email, helps prevent account takeovers with our PhishGuard phishing filter, link confirmation, and Proton Sentinel.
Proton Mail also lets you use hide-my-email aliases, which make it harder for attackers to link your different accounts together. While this won’t prevent a data breach, it drastically reduces the damage that can be done by keeping your real email private. If an alias is exposed in a data breach or begins receiving phishing attacks, you can simply turn it off or replace it with a different alias without affecting the rest of your accounts.
Switch from Google to Proton today and move all your data with one click.






