Email tracking is a form of digital surveillance that has become a serious concern(новое окно) in recent years. Over 50% of emails sent and received daily are tracked.
Working silently in the background, email trackers not only monitor how you respond to messages but can also be used to track you across the web.
In this article we explain how email trackers work, why they threaten your privacy, and how Proton Mail’s enhanced tracking protection stops them.
What is email tracking?
How do email trackers work?
Spy pixels
Tracking links
Why email trackers threaten your privacy
How to block email trackers
1. Get enhanced tracking protection
2. Hide your email with aliases
3. Turn off autoloading images
4. Get a browser extension
5. Use a VPN
Stop email trackers, protect your privacy
What is email tracking?
Email tracking is a form of digital surveillance that can monitor when, how, from where, and with what device you read emails. By inserting email trackers in newsletters and other marketing materials, companies may see whether you opened a message, details about your device, and even your location.
Big Tech companies make money this way, building character profiles about you based on the data they collect, and selling your attention to advertisers who hope to earn money with the precision data the platforms have gathered.
How do email trackers work?
There are two common types of email trackers: spy pixels and tracking links.
Spy pixels
Spy pixels, also known as tracking pixels, are tiny, single-pixel images that are inserted into an email.
When you open a message with a spy pixel, this transparent and usually invisible image is loaded from the source server, sending sensitive information back to the sender or the tracking database.
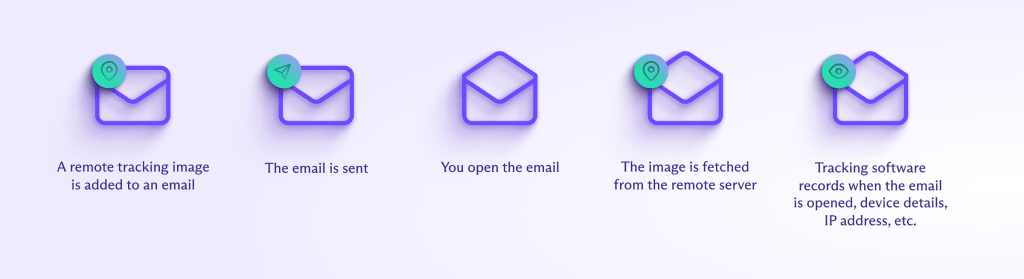
Spy pixels may collect the following information about your online activity:
- Whether you opened an email and how many times
- The date and time you opened it
- What device and operating system you used to open it
- Your internet service provider (ISP) and rough location inferred from your IP address(новое окно)
Some emails contain a single spy pixel to collect limited information for the sender, for example, to measure the email open rate for a marketing campaign. But others may contain several tracking pixels to send information to multiple third parties(новое окно).
Tracking links
Companies also try to track you with tracking links – URLs containing tracking parameters. Designed to track the effectiveness of marketing campaigns, tracking links can track your interactions with websites over time and between apps.
The most common tracking parameters are UTM (Urchin Tracking Module) parameters, which are supported natively by Google Analytics.
Here’s a breakdown of a link with typical UTM tracking parameters.

UTM parameters are often generic. But they can also be customized just for you, depending on the sender’s needs.
Ad and tech companies have also developed custom tracking parameters that aren’t always documented, making it hard to tell what information they collect.
Clicking a tracking link in an email you receive can have a significant impact on your privacy because the advertiser already has your email address, which it can use to tie all your online activity together.
Why email trackers threaten your privacy
The threat email trackers pose to your privacy goes far beyond an individual sender knowing when you opened an email, as a Princeton study of spy pixels(новое окно) has shown.
First, by linking your email address, browser and device fingerprint, and IP address with third-party tracking cookies, email trackers can be used to track your browsing activity across the web.
Second, as trackers can connect email addresses to your browsing histories and profiles, this “leads to further privacy breaches such as cross-device tracking and linking of online and offline activities”, as the Princeton research explains. For example, you could get ads from a store if you had the store’s loyalty card linked to your email address.
Third, emails may contain several trackers that send information to multiple third parties, not just an individual sender. Princeton researchers found that 70% of emails from mailing lists contain at least one tracker.(новое окно) One sample email analyzed sent tracking requests to 24 third parties, including major data brokers(новое окно).
Armed with this data, big tech companies, advertisers, governments, or even criminal attackers can build detailed profiles of you — all without your consent.
At Proton, we’ve found that almost 50% of all emails contain spy pixels. Across the globe, that means over 166 billion emails are sent with trackers every day.
How to block email trackers
There are ways to block spy pixels, though they’re not all equally effective or convenient. Here’s how you can stop email trackers from spying on you:
1. Get enhanced email tracking protection
The easiest way to stop email tracking is to use Proton Mail with enhanced tracking protection.
Enhance tracking protection automatically blocks trackers by:
- Removing known spy pixels every time you receive an email
- Preloading other remote images using a proxy with a generic IP address to hide your IP address and location
- Caching images for a few days for faster, secure access
- “Cleaning” tracking links to remove known UTM or other tracking parameters
Proton Mail tells you when you open an email containing blocked trackers with this tracker icon. The number on the icon (9 in the example below) indicates the total number of trackers (spy pixels) blocked and links cleaned.
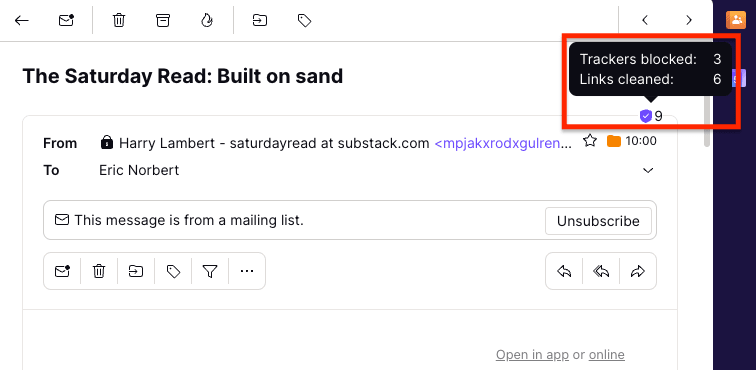
Click the shield icon to learn more about the blocked trackers and cleaned links.

Enhanced tracking protection is enabled by default on the Proton Mail web, iPhone, and iPad apps for all Proton Mail users.
Learn more about enhanced tracking protection
2. Hide your email with aliases
Another way to limit email tracking is to hide your email address. By using email aliases, you can send and receive emails while protecting your personal email address from third-party tracking.
A good email aliasing service, like SimpleLogin by Proton(новое окно), allows you to create random email addresses for different services, keeping your real address private.
Proton Pass creates aliases so you can enter them into online forms and protect your actual email address from being disclosed or leaked. And if your email alias is ever leaked or sold to spammers, you can quickly deactivate it to stop receiving unwanted emails. The unique alias lets you know which company sold your email. At no point is your actual email at risk.
3. Turn off autoloading images
As spy pixels work by loading images, you can block them by stopping images from loading automatically.
Here’s how to stop autoloading images with popular email providers on the web. With most email services, you’ll also need to change the equivalent settings in any desktop or mobile apps you use.
Stop Gmail autoloading images
- Sign in to your account at mail.google.com(новое окно).
- Go to Settings → General → Images.
- Select Ask before displaying external images.
Stop Outlook.com autoloading images
- Sign in to your account at outlook.com(новое окно)
- Go to Settings → General → Images
- Select Always use the Outlook service to load images.
Stop Proton Mail autoloading images
- Sign in to your account at mail.proton.me(новое окно).
- Click Settings → All settings → Proton Mail → Email privacy
- Turn off Auto show remote images.
With Proton Mail, you don’t need to turn off autoloading images because it has enhanced tracking protection enabled by default on the Proton Mail web, iPhone, and iPad apps. Since you can view images without being spied on, remote images are autoloaded by default on these platforms.
4. Get a browser extension
If you use Gmail, you can use third-party extensions, like Ugly Email or PixelBlock, to block email trackers. But these are browser-based and only work with Gmail on the web.
Moreover, adding any third party to your email is always an extra privacy risk as you need to give them full access to your email.
5. Use a VPN
Finally, using a trusted virtual private network (VPN)(новое окно) like Proton VPN(новое окно) can help to beat email trackers. A VPN encrypts your internet traffic and hides your real IP address.
First, masking your IP address makes it more difficult for trackers to link your email activity with your identity.
Second, some good VPNs actively block some trackers. For example, Proton VPN’s NetShield Ad-blocker(новое окно) blocks connection attempts to servers hosting trackers and malware, including email trackers. But email-specific blockers, like Proton Mail’s enhanced tracking protection, will often be more effective as they’re focused on email.
Stop email trackers, protect your privacy
Some trackers may be relatively innocuous, like silent read receipts from companies to measure a single marketing campaign. Others are far more invasive, linking your email activity with your IP address, device details, and browsing history to track you across the web for surveillance-based advertising(новое окно).
By using Proton Mail’s enhanced tracking protection, you can read your emails without being monitored, keeping your inbox secure and your activity private.
Proton Mail also offers a simple-to-use feature called Easy Switch that allows you to seamlessly transition to your new Proton Mail inbox, back up data, and import messages, contacts, and calendars from other email services, such as Gmail.
When you create a Proton Mail account, you are both protecting your most valuable data but helping build a better internet where privacy is the default.
