Proton Wallet is a digital asset wallet that currently supports self-custody on-chain Bitcoin. In this article, we review the key features and security architecture that make Proton Wallet a private and secure wallet that is as easy to use as email.
Building a secure Bitcoin wallet
This section goes over two major design decisions that give Proton Wallet a robust and secure foundation.
Custodial vs. self-custodial
Multiple solutions allow you to hold Bitcoin, and they exist on a spectrum, with dependency on third parties on one end and self-sovereignty on the other. For example, if you have Bitcoin in an ETF or exchange, you are entirely trusting one or more companies to hold Bitcoin for you. These centralized custodial solutions put you at risk of losing your Bitcoin to hacks (Mt. Gox), poor management (FTX), or even regulatory or legal action. These custodial solutions are generally not designed for transacting with Bitcoin and are legally required to surveil your financial activities.
On the self-sovereignty side of the spectrum are self-custodial wallets where you are the only one with access to your Bitcoin. You have full control of your Bitcoin and do not need to trust a third party. Self-custodial wallets allow you to store and use Bitcoin as it was designed: peer-to-peer and censorship-resistant. This means all transactions are saved on the Bitcoin blockchain forever, and the transferred BTC goes directly from sender to recipient without any intermediary taking control.
We designed Proton Wallet to be the most self-sovereign and trust-minimized solution. It uses end-to-end encryption on the keys that control your Bitcoin and your wallet metadata before they’re stored. This means even Proton cannot confiscate your Bitcoin or track your financial activities.
Local vs. server storage
Many self-custodial wallets only store data locally on one computer or phone. If you lose that device, any data not stored on the blockchain, like notes, is lost forever. We wanted to make the wallet experience more reliable and available across multiple devices, like what you expect from other important apps.
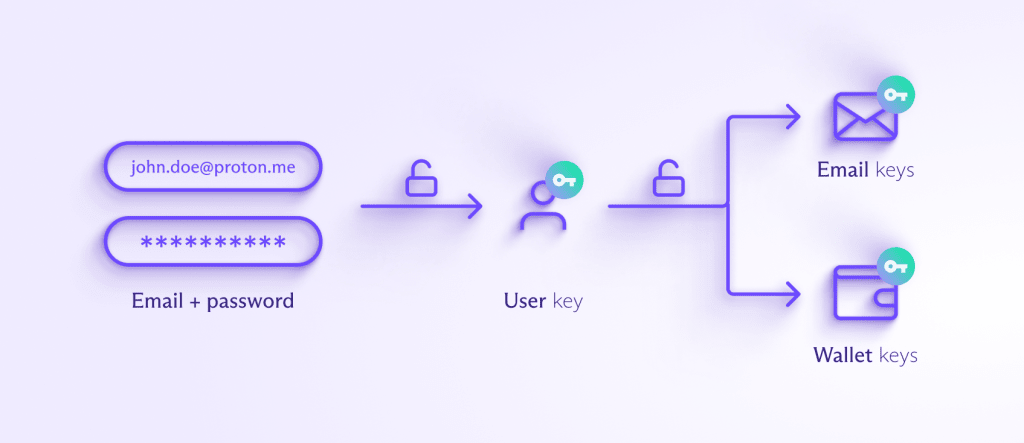
We achieve this by using Proton servers to store encrypted data and serve them to your client apps after successful login. Proton Wallet shares the same login process as the rest of the Proton ecosystem. Your password never leaves the client apps and is not stored on Proton servers because we utilize a hardened version of the Secure Remote Password (SRP) protocol for logins.
Read more about how Proton uses SRP
Your password is also used to encrypt and decrypt your Proton user key on the client, and the encrypted user key is stored on Proton servers. This means your user key can only be decrypted on the client with the correct password. The user key is then used to encrypt and decrypt product-specific keys, like ones for email and wallets. Proton Wallet offers multiple means of access, with open-source mobile and web apps.
Proton Wallet data
In this section, we review the important data associated with wallets. We use end-to-end encryption as much as possible to encrypt sensitive data on the client apps before storing on Proton servers. This allows you to benefit from our online services without giving up your privacy.
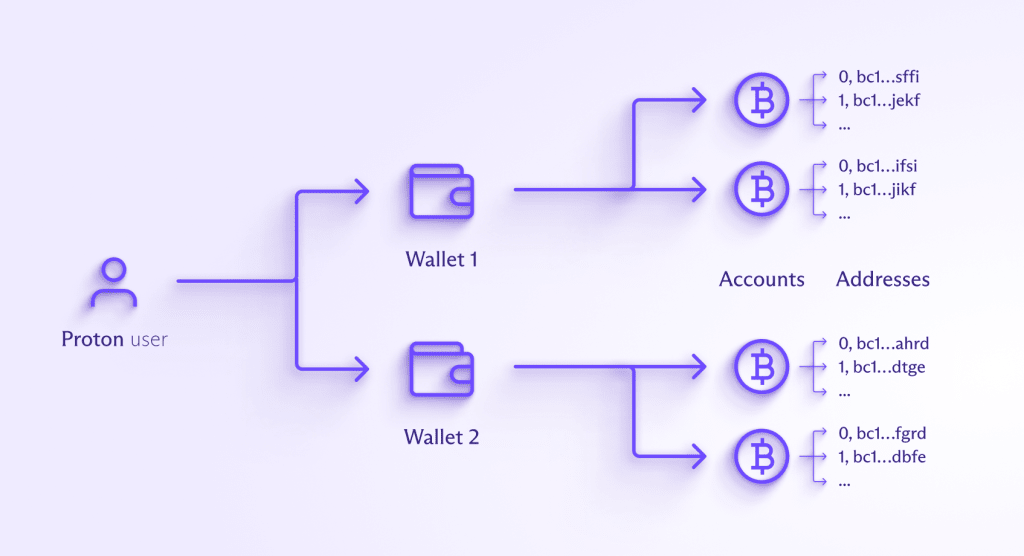
A Proton Wallet user can have multiple wallets, and Proton Wallet will generate a wallet key on the client side for each one. This wallet key is then used to encrypt and decrypt any sensitive data that needs to be stored on Proton servers with end-to-end encryption. The server never has access to the wallet keys as they are encrypted on the client with the user key.
Wallet data includes:
- Wallet and account names — The names you give to each wallet and each Bitcoin account inside the wallet are encrypted and then stored. The Bitcoin accounts deterministically generate Bitcoin addresses, which can then receive BTC.
- Wallet seed phrase — These 12 or more words (along with the optional wallet passphrase) are basically the master key of each wallet. They are used to deterministically generate the private and public keys that control a wallet’s Bitcoin accounts. Users are highly encouraged to write them down and safely store them in case they ever lose access to Proton. This mnemonic seed phrase is BIP39 compatible so it can be imported on other wallet services.
The wallet seed phrase is encrypted on the client and then stored.- The optional passphrase is never stored and users must enter it every time to unlock their wallet.
- Bitcoin addresses
- Bitcoin addresses are deterministically derived from the public key of the wallet’s Bitcoin account. We don’t store Bitcoin change addresses nor manually generated receive addresses.
- For any wallet account with Bitcoin via Email enabled, the client automatically generates a pool of Bitcoin addresses, signs them with the PGP private key of the email, and stores the pool of addresses and signatures on Proton servers. Proton servers can then give each sender a unique Bitcoin address. After a Bitcoin address from the pool has been used, we delete it from our servers to better protect your privacy.
- Wallet and account balances — These are calculated client side by deriving the Bitcoin addresses of each wallet account and asking Proton’s full nodes for transaction history. While Proton servers can see which addresses are queried, we don’t store these queried addresses or any balances on Proton servers.
- Transaction metadata — Proton Wallet doesn’t store the amounts and unspent transaction outputs (UTXOs) on Proton servers for either receiving or sending transactions. For sending transactions, Proton servers must temporarily have the transaction data to broadcast them to the Bitcoin network, but at no point does Proton have control of your Bitcoin. Transaction IDs, exchange rate ID, optional From name, and optional notes to self are all encrypted and then stored.
- Proton Wallet transactions that use Bitcoin via Email also have a sender email, recipient email, and optional message. These are all encrypted and then stored. During Bitcoin via Email sending, Proton servers know the sender and recipient emails but do not store them.
Bitcoin via Email, unlike any other wallet
In this section, we review the major challenges of transacting securely and privately with Bitcoin on-chain and how Proton Wallet makes it easy with our Bitcoin via Email feature.
Traditionally, for someone to receive Bitcoin in a self-custodial way on the blockchain, they must generate a Bitcoin address with their wallet and share it with the sender through some secure channel. This is error-prone and adds a lot of friction for both the sender and recipient. For better privacy, the recipient should also generate a new address for each transaction because addresses can be looked up and traced on the blockchain.
To minimize friction, people accepting payments or donations in Bitcoin may just generate one address and tell everyone to send BTC to it. However, this isn’t great for privacy because anyone can see how many BTC were received at that address, where they came from, and where they were later sent to.
Combining encrypted email with Bitcoin
The unique feature built into Proton Wallet is sending Bitcoin to an email address in a low-friction, private way without reusing Bitcoin addresses. We can do this by leveraging the Proton Mail encrypted email system that has been serving over 100 million accounts since 2014.
Bitcoin via Email works like this:
- Bob signs up for Proton Wallet with his existing email, bob@gmail.com. After verifying he owns bob@gmail.com, Bob’s Proton Wallet app generates a PGP key for his email.
- Note, Bob could also sign up with a Proton Mail email address, such as bob@proton.me, which would be even more private and secure. If Bob already has a Proton Mail account, he could use it with Proton Wallet.
- Bob’s Proton Wallet app will automatically generate a pool of Bitcoin addresses from his main wallet account, sign them with the PGP private key linked to bob@gmail.com, and store the BTC addresses and signatures on Proton’s servers.
- Alice’s email is alice@proton.me, and she wants to send BTC to bob@gmail.com. Her Proton Wallet app asks Proton’s servers to give her one of the unused BTC addresses from Bob’s pool along with the signature.
- Alice’s app uses the PGP public key of bob@gmail.com to verify the signature is correct and indeed belongs to Bob.
- Alice has to trust Proton to give her the correct public key of Bob, but this trust can be minimized in the future with security features such as Trusted Key and Key Transparency, which are discussed below in the threat model.
- Alice then sends BTC to Bob’s BTC address, along with an optional message from Alice. This message is end-to-end encrypted with Bob’s PGP public key so that only he can decrypt and read it in his Wallet app.
Proton Wallet generates and maintains a pool of unused Bitcoin addresses for each wallet account that has Bitcoin via Email enabled, so privacy is ensured. For instance, if Eve, an attacker, attempts to send BTC to bob@gmail.com, she will receive a new, empty BTC address from Bob’s pool that’s different from the one Alice used. Eve therefore won’t learn anything about Bob’s previous transactions.
Threat model
In this section, we review potential threats that Proton Wallet users should be aware of and the best practices to improve security.
Forgotten password and self-recovery
As a self-custodial wallet, Proton doesn’t have custody of your digital assets or access to the keys that control them. This means if you forget your Proton Account password and lose your recovery phrase or kit, there’s nothing we can do to help you. This is why it’s important you backup your recovery methods and store them somewhere safe (for example, some people keep their recovery phrase in a safe) before you add digital assets to your wallet.
The first recovery method you should back up is the Proton recovery phrase, which is used to recover your Proton Account if you forget your Proton password. This is a 12-word phrase that encodes your user key and logs you back into your Proton account with all encrypted data still accessible. You will be asked to create a new password.
The second recovery method is your wallet seed phrase, the 12-word phrase that encodes your wallet key. You should back up this for each wallet you create. You should only use this if the first recovery method did not work and you cannot get into your Proton Account. In this case, all your encrypted metadata, such as notes and messages, will be lost, but you can recover your digital assets by importing the wallet using the seed phrase. You can even use this recovery method on another wallet service if you cannot access Proton anymore.
Finally, if you decide to set an optional passphrase on any of your wallets, you should also back it up just like the two recovery methods. You can think of the optional passphrase as an extra password of the wallet seed phrase, but unlike the seed phrase, which is stored encrypted on Proton servers, the passphrase is never stored. This means the Proton Wallet app can never remind you what it is.
Proton account compromise
This mainly affects users without two-factor authentication since attackers just need the email and password of the account to get in. One common way for an attacker to get the password is by sending a phishing email to the user and trying to trick them into entering their Proton password on the attacker’s phishing website. Another way is the attacker will look for previous password leaks from other services, and if the user reused that leaked password on Proton, then the attacker can log in.
Once an attacker logs in to Proton Wallet, they can view the wallet seed phrase or send all the assets to their own wallet. A wallet with an optional passphrase (which is never stored by Proton) would prevent the attacker from accessing the wallet and draining the assets. However, if set, the passphrase must also be used along with the wallet seed phrase to recover wallets. This extra complexity and risk of forgetting the passphrase is why Proton Wallet doesn’t support setting a passphrase on your first wallet. Once you understand the trade-offs, you can create a second wallet with a passphrase.
Other ways for users to defend against account compromise is to set up 2FA, use strong unique passwords for each service, and be careful with phishing emails.
Since this is the most common way that users get hacked, Proton has also built sophisticated systems operated by global 24/7 teams that filter phishing emails and block suspicious logins. We have also developed an advanced account protection program for high-profile users and an easy-to-use password manager.
User device compromise
If an attacker has access to the device running the Proton apps, they can access the apps running on that device or add a keylogger to capture the email and password when you log in. Users should lock their screen when they step away from their computer, consider using lockdown mode on Apple devices, keep their operating system and apps updated, and be careful when downloading and opening files. While Proton Sentinel can offer protection in some cases of user device compromise, Proton’s ability to protect you is rather limited if the devices you use to access Proton are compromised.
Blockchain privacy compromise
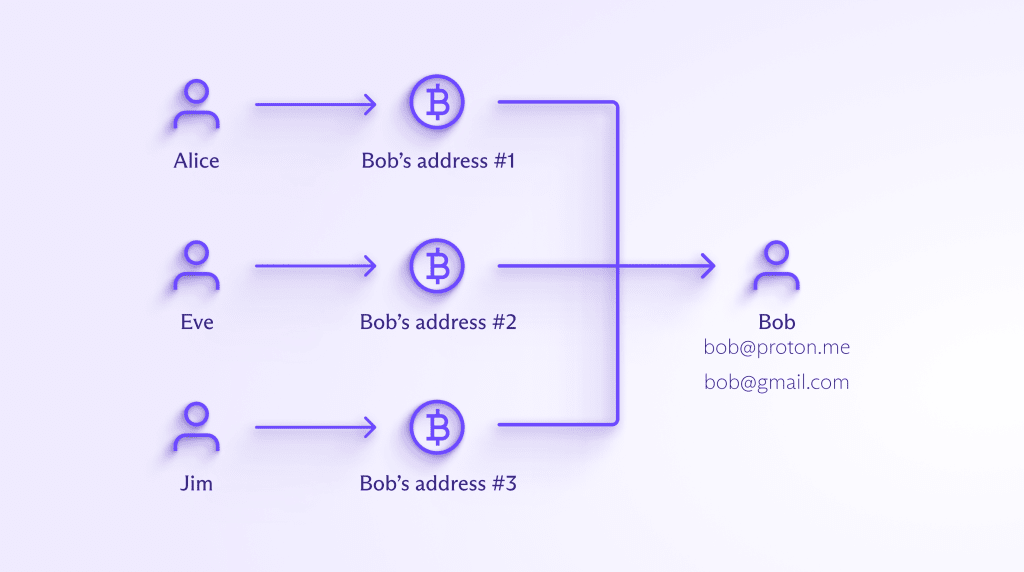
As mentioned above, attackers can trace on-chain Bitcoin transactions once an address is associated with you. Continuing from the example above:
- Alice sent BTC from address A to Bob’s BTC address, B1.
- Eve sent BTC from address E to Bob’s other BTC address, B2.
- So far, Alice and Eve do not know about Bob’s other transactions.
- Now Bob sends all his BTC in a single transaction to another recipient, perhaps an exchange with address X.
- Eve can now see that BTC address B2 sent Bitcoin to address X, as did BTC address B1. She can assume BTC address B1 also belongs to Bob and see that address A also sent BTC to Bob.
While being tracked on the blockchain isn’t as bad as losing assets for most users, it could be a big threat for users who need the most financial privacy. Looking at the example above, Bob might be a human rights activist who is getting donations from residents of a country run by a corrupt dictator. Eve may be working for the corrupt dictator, trying to track who is donating to Bob, which would mean Alice may be at risk.
Users like Alice and Bob who need the most privacy may want to consider using a third-party coinjoin service before and after their transactions to mix their Bitcoin with others and break the link in the blockchain history.
Proton server compromise
Proton products all use end-to-end encryption to minimize the data on Proton servers, so even if attackers get into Proton servers, they will have limited data to steal. The fact that Proton servers never have custody of users’ BTC also makes them less attractive as a target.
In the unlikely event that an attacker gains access to Proton’s web servers, they may attempt to change the JavaScript code that is served to web app users. Malicious code may try to steal users’ passwords, keys, and BTC. If you’re worried about this risk, you can use the Proton Wallet mobile apps, which can notify you before updating to new code.
In the unlikely event that an attacker gains access to Proton’s key servers, they may also try to change email PGP keys and signatures used for Bitcoin via Email. To reduce this risk and reduce trust in Proton servers providing the right public keys, we are incorporating Proton’s Address Verification system, which will allow the Wallet apps to warn users if a Trusted Key changes. An automated extension of this, Proton’s Key Transparency system, will also be added to Proton Wallet in the future.
Proton inaccessible
The last risk we will cover is if you cannot reach Proton servers anymore. This might be due to your government blocking internet access to Proton’s websites and domains. First, you can try connecting to a VPN, such as our free Proton VPN service(nyt vindue), which has built-in anti-censorship technology. But if that fails, as long as you have backed up all your wallet seed phrases, you can use those 12 words to recover your digital assets on any Bitcoin wallet service. Metadata such as notes and Bitcoin via Email will be lost, but the transactions on the blockchain can be recovered and your Bitcoin will remain safe and accessible.
Proton Wallet vs. hardware wallets
It’s recommended that users with a lot of value stored in digital assets keep most of their assets in self-custodial hardware wallets, which keep the cryptographic keys offline on a dedicated device. Hardware wallets are considered the most secure, but ultimately, users still have to trust the wallet makers with their software updates and desktop apps that are needed to use the hardware wallets. Hardware wallets are also limited in what metadata they can store and hard to use for on-the-go transactions.
Proton Wallet aims to be a free and easy-to-use wallet that is secure enough for most users who don’t want the added complexity and expense of managing a hardware wallet. For those with a lot of BTC, Proton Wallet is not designed to replace hardware wallets but rather a secure complement to them. For example, you can use a hardware wallet to store BTC you don’t need to access regularly and use Proton Wallet for the BTC you want to transact with.
Defending privacy and freedom
With the launch of Proton Wallet, we want to offer an open and decentralized alternative to fragile financial intermediaries and gatekeepers. By giving individuals easy control of their own encryption keys and digital assets, we are building an internet where financial privacy and freedom is accessible to all.
We believe financial privacy and freedom are critical for a free and fair society where everyone can be economically connected and empowered. If you would like to financially support our mission, please upgrade to a paid Proton Wallet plan.