In an ever-evolving cyber threat landscape, infostealers — malicious programs designed to gather sensitive information from infected systems and send that information back to an attacker — have emerged as a growing threat to individuals and organizations alike.
According to a report released this year by Constella Intelligence(neues Fenster), more than 500 million devices in 2023 were found to be infected with nearly 2 billion infostealer records, including usernames, passwords, credit card numbers, Social Security numbers, and other sensitive information.
While the rise of infostealers is notable, they are not new. What has changed, however, is the business model and sophistication of the infostealer ecosystem. Previously, malicious groups needed specialized expertise to develop malware. Today, they can simply use malware-as-a-service (MaaS) for a $120 monthly payment. This shift has opened new revenue streams for existing malware developers and a potential doorway for criminals with no particular technical skills.
This blog post will delve into what infostealers are, how they operate, and where the data they collect goes. We will also explore the reliability of infostealer data and how you can protect yourself.
If you are already using Proton Mail and have Proton Sentinel enabled, you automatically have enhanced protection from infostealers, as Proton Sentinel detects logins from malicious actors, even if they have already stolen your credentials. Dark Web Monitoring in Proton Mail and Proton Pass also warns you if it detects that any of your credentials have been leaked onto the dark web.
What are infostealers?
Infostealers are a type of malware designed to steal from a compromised system information including but not limited to:
- Login credentials (usernames/email addresses and passwords)
- Financial information (credit card numbers, bank account details)
- Personal data (Social Security numbers, addresses, phone numbers)
- Browser data (bookmarks, history, cookies)
- Emails and chat logs
- Images and documents
- Crypto wallets
- Screenshots (some infostealers take periodic screenshots and send them back to the attacker)
How do infostealers work?
Infostealers are often used in conjunction with other types of malware to create a more comprehensive attack.
They can be delivered through various means, including phishing emails, malicious websites, and infected software downloads. We can break down their operations into five parts:
- Infostealer delivery
- Data collection
- Data exfiltration
- Data distribution
- Further criminal activity

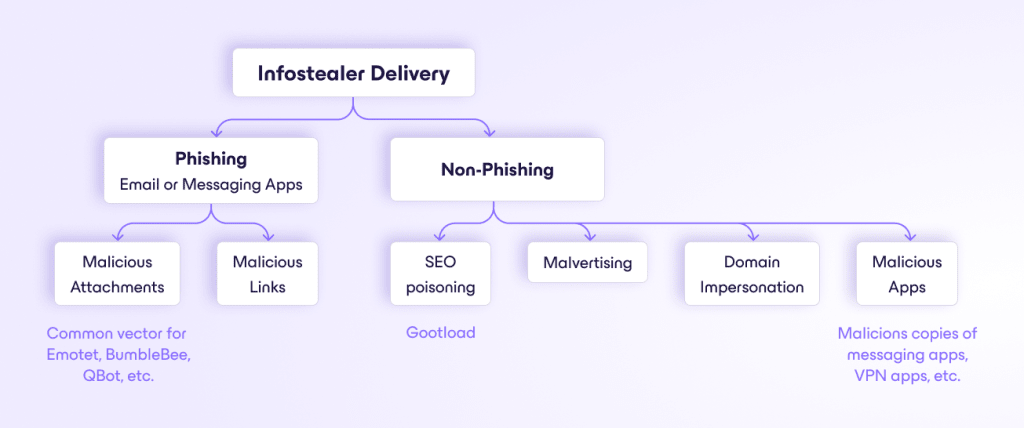
Infostealer delivery
The first step in an infostealer attack is the infection of the target system. This can occur through:
- Phishing emails: Emails containing malicious attachments or links that, when opened, download and install the infostealer.
- Malicious websites: Visiting compromised or malicious websites that exploit vulnerabilities in the user’s browser to install the infostealer.
- Malvertising: Using online advertising to spread malware, often by injecting malicious or malware-laden advertisements into legitimate websites — or even by compromising the social media accounts of companies and using this to create malicious ads.
- Infected software: Downloading and installing software from untrusted sources that contains the infostealer. Typically, an attacker will put up “free” versions of popular software hoping that people will download them, which they often do.
Data collection
Once installed, the infostealer begins to collect data from the infected system. This process can involve:
- Keyloggers: Almost all infostealers have a key logger, which provides attackers with every keystroke a user makes. Attackers can later sift through this data to extract passwords, credit card numbers, and other sensitive personal information.
- Form grabbers: This technique intercepts data submitted through web forms before it is encrypted. It is particularly effective for stealing login credentials, payment details, and other information entered on websites.
- Clipboard hijackers: Infostealers can monitor and alter the clipboard content on an infected device. When a user copies sensitive data like account numbers or passwords, the malware can replace or steal this information.
- Remote access: A more sophisticated type of malware, also commonly referred to as RATs (remote access trojans), this type of malware gives attackers remote access to a user’s machine. Once inside your machine, an attacker has access to everything they need. Famous examples include Agent Tesla, LokiBot, and TrickBot.
- Screen captures: By taking screenshots at crucial moments, such as when a user is entering credentials or viewing personal information, this method bypasses the limitations of text-based data extraction. It captures any data displayed on the screen.
- Browser session hijacking: This method — present in stealers such as RacoonStealer — involves stealing cookies and session tokens from a browser’s memory. Cybercriminals can use this to impersonate the user’s online session, gaining unauthorized access to accounts without needing a username and password.
- File harvesting: The malware searches through files and emails on the computer to gather information, which can include login credentials, images, sensitive documents, communications, and more.
- Crypto wallet harvesters: Some Infostealer malware, such as LokiBot, can search for common crypto-wallet software and attempt to steal private keys. Once in the attacker’s possession, these keys can be used to transfer the victim’s cryptocurrency to attacker-controlled accounts.
Data exfiltration
The collected data is then transmitted to the attacker’s server. This can be done through:
- HTTP/HTTPS requests: Sending the data to a web server controlled by the attacker — or via APIs to reputable file-sharing sites.
- FTP transfers: Uploading the data to an FTP server.
- Email: Sending the data via email to the attacker.
Data distribution
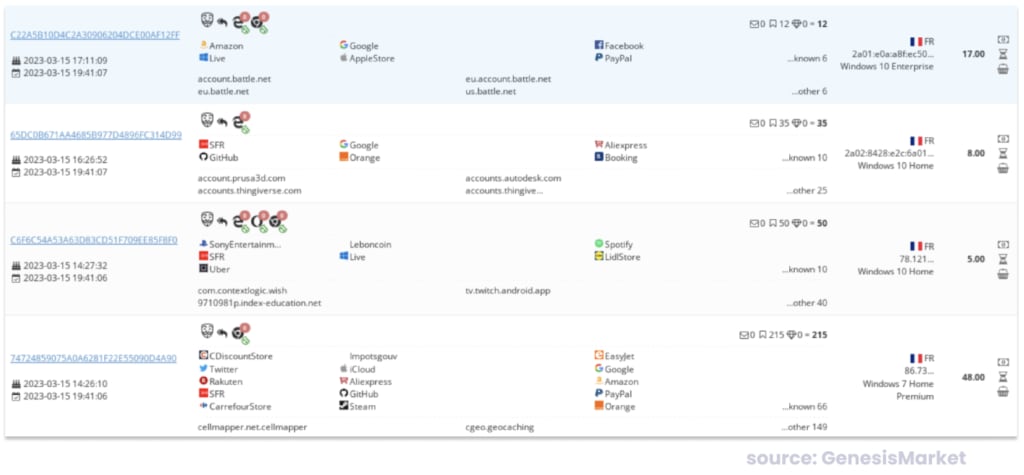
The data collected by infostealers is often sold or traded in one of two places: a centralized marketplace or a decentralized marketplace.
Centralized marketplaces, such as the now defunct Genesis marketplace, provide a one-stop shop for infostealer data.
Decentralized options also exist, such as Telegram bots like the one pictured below. Here, criminals request what they need (credentials used on Lufthansa, for example), and the bot will respond with how many records exist. The attacker can then request those records, pay a price directly, and receive the logs.

Further criminal activity
Cybercriminals can then use this stolen data for various malicious purposes, including:
- Identity theft: Using personal information to impersonate the victim.
- Financial fraud: Using financial information to make unauthorized transactions.
- Phishing attacks: Using the stolen data to craft more convincing phishing emails.
- Ransomware attacks: Using the stolen data to extort the victim.
- Sextortion/blackmail: Gaining access to the user’s files can result in threats to expose their data.
Is infostealer data reliable?
While infostealers can collect a vast amount of data, the reliability of this data is not always guaranteed.
User mistakes
Users can make mistakes when entering data, which can lead to the inclusion of incorrect or irrelevant information. For example, a user might accidentally type a friend’s email address instead of their own when signing up for a service. This mistake can result in the infostealer collecting and transmitting the friend’s email address, potentially leading to the friend being targeted by the attacker instead.
Attacker machine infections
Sometimes what appears to be a new malware infection is actually the result of criminals becoming victims themselves(neues Fenster). A recent study(neues Fenster) found the credentials of 120,000 users on known cybercrime forums.
Here’s how this can happen:
- Cybercriminals who test stolen passwords may have their own computers infected with infostealer malware.
- When these compromised criminals test lists of stolen credentials, the infostealer captures this activity.
- Much of this testing involves old, invalid credentials from previous data breaches found on dark web forums.
- As a result, when someone sees their old password appearing in malware logs, they might incorrectly assume their computer is currently infected.
- In reality, their information may have come from an old data breach where just one password was compromised, rather than from active malware on their system.
In short, it may just be a criminal testing old stolen passwords on their malware-infected computer that creates logs that make it look like many people have malware, when actually those people had their passwords leaked in the past.
Corrupted data
Infostealers can also collect data that is incomplete or corrupted.
For example, a keylogger might not capture all keystrokes, or a file scanner might miss certain types of files. This can lead to gaps in the collected data, making it less useful for the attacker.
How to protect yourself from infostealers
Here are some ways you can protect yourself right now.
- Use a virus scanner to ensure your system is protected from malware.
- Be careful of phishing, using tools like NetShield, which is built into ProtonVPN, to protect yourself from known malicious links; only download attachments from known contacts (and even then be vigilant).
- Clear your cookies and browser data often to minimize the risk of session hijacking(neues Fenster).
- Enable Dark Web Monitoring on your Proton account to detect and respond to threats quickly.
- Monitor account accesses carefully and set up activity alerts with your bank.
A growing threat
Infostealers are a significant threat in the world of cybersecurity, capable of collecting a wide range of sensitive information from infected systems. Understanding how they work and the distribution of the data they collect is crucial for protecting against these threats.
However, it’s also important to recognize that infostealer data is not always reliable due to user mistakes, accidental infections, and data integrity issues. By staying informed and taking proactive security measures, individuals and organizations can better protect themselves from the dangers of infostealers.