El rastreo de correo electrónico es una forma de vigilancia digital que se ha convertido en una seria preocupación(nueva ventana) en los últimos años. Más del 50 % de los correos electrónicos enviados y recibidos diariamente son rastreados.
Trabajando silenciosamente en segundo plano, los rastreadores de correo electrónico no solo monitorean cómo responde a los mensajes, sino que también pueden usarse para rastrearle a través de la web.
En este artículo explicamos cómo funcionan los rastreadores de correo electrónico, por qué amenazan su privacidad y cómo la protección mejorada contra el rastreo de Proton Mail los detiene.
¿Qué es el rastreo de correo electrónico?
¿Cómo funcionan los rastreadores de correo electrónico?
Píxeles espía
Enlaces de rastreo
Por qué los rastreadores de correo electrónico amenazan su privacidad
Cómo bloquear los rastreadores de correo electrónico
1. Obtenga protección mejorada contra el rastreo
2. Oculte su correo electrónico con alias
3. Desactive la carga automática de imágenes
4. Obtenga una extensión de navegador
5. Use una VPN
Detenga los rastreadores de correo electrónico, proteja su privacidad
¿Qué es el rastreo de correo electrónico?
El rastreo de correo electrónico es una forma de vigilancia digital que puede monitorear cuándo, cómo, desde dónde y con qué dispositivo lee los correos electrónicos. Al insertar rastreadores de correo electrónico en boletines y otros materiales de marketing, las empresas pueden ver si abrió un mensaje, detalles sobre su dispositivo e incluso su ubicación.
Las grandes empresas tecnológicas ganan dinero de esta manera, creando perfiles de usted basados en los datos que recopilan y vendiendo su atención a los anunciantes que esperan ganar dinero con los datos de precisión que las plataformas han reunido.
¿Cómo funcionan los rastreadores de correo electrónico?
Hay dos tipos comunes de rastreadores de correo electrónico: píxeles espía y enlaces de rastreo.
Píxeles espía
Los píxeles espía, también conocidos como píxeles de rastreo, son imágenes diminutas de un solo píxel que se insertan en un correo electrónico.
Cuando abre un mensaje con un píxel espía, esta imagen transparente y generalmente invisible se carga desde el servidor de origen, enviando información confidencial de vuelta al remitente o a la base de datos de rastreo.
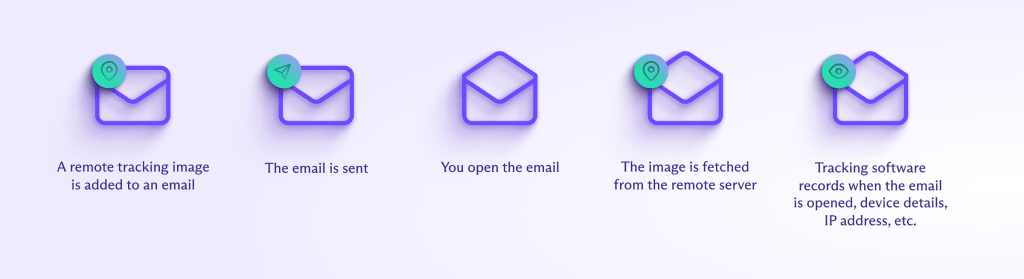
Los píxeles espía pueden recopilar la siguiente información sobre su actividad en línea:
- Si abrió un correo electrónico y cuántas veces
- La fecha y hora en que lo abrió
- Qué dispositivo y sistema operativo utilizó para abrirlo
- Su proveedor de servicio de internet (PSI) y ubicación aproximada inferida de su dirección IP(nueva ventana)
Algunos correos electrónicos contienen un solo píxel espía para recopilar información limitada para el remitente, por ejemplo, para medir la tasa de apertura de correo electrónico para una campaña de marketing. Pero otros pueden contener varios píxeles de rastreo para enviar información a múltiples terceros(nueva ventana).
Enlaces de rastreo
Las empresas también intentan rastrearle con enlaces de rastreo: URL que contienen parámetros de rastreo. Diseñados para rastrear la efectividad de las campañas de marketing, los enlaces de rastreo pueden rastrear sus interacciones con sitios web a lo largo del tiempo y entre aplicaciones.
Los parámetros de rastreo más comunes son los parámetros UTM (Urchin Tracking Module), que son soportados nativamente por Google Analytics.
Aquí hay un desglose de un enlace con parámetros de rastreo UTM típicos.

Los parámetros UTM suelen ser genéricos. Pero también pueden personalizarse solo para usted, según las necesidades del remitente.
Las empresas de publicidad y tecnología también han desarrollado parámetros de rastreo personalizados que no siempre están documentados, lo que dificulta saber qué información recopilan.
Hacer clic en un enlace de rastreo en un correo electrónico que recibe puede tener un impacto significativo en su privacidad porque el anunciante ya tiene su dirección de correo electrónico, que puede usar para vincular toda su actividad en línea.
Por qué los rastreadores de correo electrónico amenazan su privacidad
La amenaza que los rastreadores de correo electrónico representan para su privacidad va mucho más allá de que un remitente individual sepa cuándo abrió un correo electrónico, como ha demostrado un estudio de Princeton sobre píxeles espía(nueva ventana).
Primero, al vincular su dirección de correo electrónico, huella digital de navegador y dispositivo y dirección IP con cookies de rastreo de terceros, los rastreadores de correo electrónico se pueden usar para rastrear su actividad de navegación a través de la web.
Segundo, dado que los rastreadores pueden conectar direcciones de correo electrónico a sus historiales de navegación y perfiles, esto “conduce a más violaciones de la privacidad, como el rastreo entre dispositivos y la vinculación de actividades en línea y sin conexión”, como explica la investigación de Princeton. Por ejemplo, podría recibir anuncios de una tienda si tuviera la tarjeta de fidelización de la tienda vinculada a su dirección de correo electrónico.
Tercero, los correos electrónicos pueden contener varios rastreadores que envían información a múltiples terceros, no solo a un remitente individual. Los investigadores de Princeton descubrieron que el 70 % de los correos electrónicos de listas de correo contienen al menos un rastreador.(nueva ventana) Un correo electrónico de muestra analizado enviaba solicitudes de rastreo a 24 terceros, incluidos los principales corredores de datos(nueva ventana).
Armadas con estos datos, las grandes empresas tecnológicas, los anunciantes, los gobiernos o incluso los atacantes criminales pueden crear perfiles detallados de usted, todo sin su consentimiento.
En Proton, hemos descubierto que casi el 50 % de todos los correos electrónicos contienen píxeles espía. En todo el mundo, eso significa que más de 166.000 millones de correos electrónicos se envían con rastreadores todos los días.
Cómo bloquear los rastreadores de correo electrónico
Hay formas de bloquear los píxeles espía, aunque no todas son igual de efectivas o convenientes. Así es como puede detener a los rastreadores de correo electrónico para que no le espíen:
1. Obtenga protección mejorada contra el rastreo de correo electrónico
La forma más fácil de detener el rastreo de correo electrónico es usar Proton Mail con protección mejorada contra el rastreo.
La protección mejorada contra el rastreo bloquea automáticamente los rastreadores al:
- Eliminar los píxeles espía conocidos cada vez que recibe un correo electrónico
- Precargar otras imágenes remotas usando un proxy con una dirección IP genérica para ocultar su dirección IP y ubicación
- Almacenar imágenes en caché durante unos días para un acceso más rápido y seguro
- “Limpiar” los enlaces de rastreo para eliminar los parámetros UTM u otros parámetros de rastreo conocidos
Proton Mail le avisa cuando abre un correo electrónico que contiene rastreadores bloqueados con este icono de rastreador. El número en el icono (9 en el ejemplo a continuación) indica el número total de rastreadores (píxeles espía) bloqueados y enlaces limpiados.
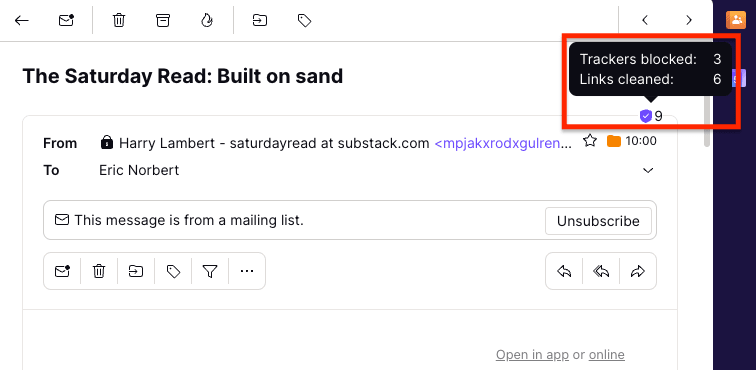
Haga clic en el icono del escudo para obtener más información sobre los rastreadores bloqueados y los enlaces limpiados.

La protección mejorada contra el rastreo está activada por defecto en la web de Proton Mail y en las aplicaciones para iPhone y iPad para todos los usuarios de Proton Mail.
Más información sobre la protección mejorada contra el rastreo
2. Oculte su correo electrónico con alias
Otra forma de limitar el rastreo de correo electrónico es ocultar su dirección de correo electrónico. Al usar alias de correo electrónico, puede enviar y recibir correos electrónicos mientras protege su dirección de correo electrónico personal del rastreo de terceros.
Un buen servicio de alias de correo electrónico, como SimpleLogin by Proton(nueva ventana), le permite crear direcciones de correo electrónico aleatorias para diferentes servicios, manteniendo su dirección real privada.
Proton Pass crea alias para que pueda ingresarlos en formularios en línea y proteger su dirección de correo electrónico real para que no sea revelada o filtrada. Y si su alias de correo electrónico alguna vez se filtra o se vende a spammers, puede desactivarlo rápidamente para dejar de recibir correos electrónicos no deseados. El alias único le permite saber qué empresa vendió su correo electrónico. En ningún momento su correo electrónico real está en riesgo.
3. Desactive la carga automática de imágenes
Como los píxeles espía funcionan cargando imágenes, puede bloquearlos deteniendo la carga automática de imágenes.
Aquí se explica cómo detener la carga automática de imágenes con proveedores de correo electrónico populares en la web. Con la mayoría de los servicios de correo electrónico, también deberá cambiar la configuración equivalente en las aplicaciones de escritorio o móviles que utilice.
Detener la carga automática de imágenes en Gmail
- Inicie sesión en su cuenta en mail.google.com(nueva ventana).
- Vaya a Ajustes → General → Imágenes.
- Seleccione Preguntar antes de mostrar imágenes externas.
Detener la carga automática de imágenes en Outlook.com
- Inicie sesión en su cuenta en outlook.com(nueva ventana)
- Vaya a Ajustes → General → Imágenes
- Seleccione Usar siempre el servicio Outlook para cargar imágenes.
Detener la carga automática de imágenes en Proton Mail
- Inicie sesión en su cuenta en mail.proton.me(nueva ventana).
- Haga clic en Ajustes → Todos los ajustes → Proton Mail → Privacidad del correo electrónico
- Desactive Mostrar imágenes remotas automáticamente.
Con Proton Mail, no necesita desactivar la carga automática de imágenes porque tiene la protección mejorada contra el rastreo activada por defecto en la web de Proton Mail y en las aplicaciones para iPhone y iPad. Como puede ver las imágenes sin ser espiado, las imágenes remotas se cargan automáticamente por defecto en estas plataformas.
4. Obtenga una extensión de navegador
Si usa Gmail, puede usar extensiones de terceros, como Ugly Email o PixelBlock, para bloquear los rastreadores de correo electrónico. Pero estas se basan en el navegador y solo funcionan con Gmail en la web.
Además, agregar a cualquier tercero a su correo electrónico siempre es un riesgo de privacidad adicional, ya que debe darles acceso completo a su correo electrónico.
5. Use una VPN
Finalmente, usar una red privada virtual (VPN)(nueva ventana) de confianza como Proton VPN(nueva ventana) puede ayudar a vencer a los rastreadores de correo electrónico. Una VPN cifra su tráfico de internet y oculta su dirección IP real.
Primero, enmascarar su dirección IP hace que sea más difícil para los rastreadores vincular su actividad de correo electrónico con su identidad.
Segundo, algunas buenas VPN bloquean activamente algunos rastreadores. Por ejemplo, NetShield Ad-blocker(nueva ventana) de Proton VPN bloquea los intentos de conexión a servidores que alojan rastreadores y malware, incluidos los rastreadores de correo electrónico. Pero los bloqueadores específicos de correo electrónico, como la protección mejorada contra el rastreo de Proton Mail, a menudo serán más efectivos ya que se centran en el correo electrónico.
Detenga los rastreadores de correo electrónico, proteja su privacidad
Algunos rastreadores pueden ser relativamente inocuos, como las confirmaciones de lectura silenciosas de las empresas para medir una sola campaña de marketing. Otros son mucho más invasivos, vinculando su actividad de correo electrónico con su dirección IP, detalles del dispositivo e historial de navegación para rastrearle a través de la web con fines de publicidad basada en la vigilancia(nueva ventana).
Al usar la protección mejorada contra el rastreo de Proton Mail, puede leer sus correos electrónicos sin ser monitoreado, manteniendo su bandeja de entrada segura y su actividad privada.
Proton Mail también ofrece una función fácil de usar llamada Easy Switch que le permite hacer una transición fluida a su nueva bandeja de entrada de Proton Mail, hacer una copia de seguridad de los datos e importar mensajes, contactos y calendarios de otros servicios de correo electrónico, como Gmail.
Cuando crea una cuenta de Proton Mail, protege sus datos más valiosos y ayuda a construir un internet mejor donde la privacidad es el valor por defecto.
