Betrüger haben viele Wege, deine Identität und Geld zu stehlen, aber es gibt einfache Schritte, die du zum Schutz ergreifen kannst.
Angesichts der wertvollen persönlichen Daten, die wir online speichern, haben Betrüger einen starken Anreiz, diese zu stehlen. Mit nur wenigen persönlichen Details können sie deine Identität stehlen, dein Bankkonto leer räumen, Kreditkartenrechnungen anhäufen oder in deinem Namen Verbrechen begehen.
2022 erhielt die Federal Trade Commission (FTC) in den USA über 1,1 Millionen Meldungen über Identitätsdiebstahl(neues Fenster). Und für die Betroffenen kann der Einfluss verheerend sein.
Über 30% der Opfer von Identitätsdiebstahl im letzten Jahr gaben an, mehr als 10.000 Dollar verloren zu haben, laut dem Identity Theft Resource Center(neues Fenster). Die meisten berichteten auch von negativen Gefühlen und Emotionen oder sogar physischen Problemen als Folge.
Aber es gibt Wege, dich zu schützen. Wir erklären, wie Betrüger deine Identität stehlen können und was du tun kannst, um sie zu stoppen.
Wie Betrüger deine Identität stehlen
Wie du Phishing und Social Engineering erkennst
Was du tun solltest, wenn du Phishing vermutest
10 Wege, um Identitätsdiebstahl zu verhindern
1. Antworte nicht auf Spam!
2. Nutze sichere E-Mail
3. Verberge deine E-Mail mit Aliasen
4. Verwende starke Passwörter und 2FA
5. Installiere gute Antivirensoftware
6. Halte deine Geräte aktuell
7. Sichere deine Daten
8. Nutze ein vertrauenswürdiges VPN
9. Teile nicht zu viele persönliche Daten
10. Schütze deine physischen Dokumente
Bleib sicher mit Proton
Wie Betrüger deine Identität stehlen
Betrüger stehlen persönliche Identifikationsinformationen wie deinen Namen und deine Adresse, Kreditkarten- oder Bankkontonummern oder Sozialversicherungsnummern. Dann können sie mit deiner Kreditkarte einkaufen, auf dein Bankkonto zugreifen, deine Steuerrückzahlung stehlen und mehr, während du die Rechnung bezahlst. Oder sie nutzen deine Identität, um andere Verbrechen zu begehen, so tun als wärst du es.
Hier sind einige Wege, wie Diebe an deine persönlichen Daten kommen, um deine Identität zu stehlen:
Phishing und Social Engineering
Phishing ist ein Online-Betrug, bei dem Angreifer dir gefälschte E-Mails oder SMS senden, um dich dazu zu bringen, sensible Informationen preiszugeben oder Schadsoftware auf deinem Gerät herunterzuladen. Oder sie rufen dich an und bitten um persönliche Details oder nutzen andere Social-Engineering-Tricks(neues Fenster), um dich zu betrügen. Siehe unten, wie man Phishing erkennt.
Hacking und Datenpannen
Bösartige Hacker können auf Organisationen abzielen, die große Mengen persönlicher Daten speichern, wie Banken, E-Mail-Anbieter oder Online-Händler. Sobald deine persönlichen Daten bei einem Datenleck veröffentlicht werden, können sie im Darknet verkauft werden.
Malware
Malware(neues Fenster), wie Spyware oder Trojaner, kann durch Phishing-E-Mails, Softwareinstallationen oder andere Mittel auf dein Gerät heruntergeladen werden. Betrüger können sie nutzen, um persönliche Details wie Anmeldeinformationen zu stehlen oder sogar die Kontrolle über dein Gerät zu übernehmen.
Soziale Medien
Betrüger können viel über dich erfahren, nur durch das, was du online postest, also sei vorsichtig, was du teilst. Sie können auch gefälschte Social-Media-Profile erstellen und darum bitten, sich zu vernetzen, um Zugang zu deinen privaten Posts zu erhalten.
Skimming
Kriminelle können Skimming-Geräte an Geldautomaten, Zapfsäulen oder anderen Zahlungsterminals installieren, um deine Kreditkartendaten zu erfassen. Wenn du deine Karte einsteckst und benutzt, stehlen sie deine Kartennummer und PIN.
Dein Müll
Wenn du sensible Dokumente wie Kontoauszüge oder Rechnungen ohne sie zu schreddern entsorgst oder recycelst, sei gewarnt. Betrüger können deinen Müll durchwühlen, um deine persönlichen Daten zu bergen.
Diebstahl physischer Dokumente
Diebe können auch persönliche Daten aus Dokumenten stehlen, die du herumliegen lässt, also bewahre deine Dokumente sicher auf. Ebenso können sie dein Postfach vor deinem Zuhause ins Visier nehmen, also halte es verschlossen.
Behördenunterlagen
Wenn du in den USA lebst, sind persönliche Daten wie Strafregister, Informationen über Grundstückseigentümer und andere öffentliche Unterlagen frei verfügbar. Jeder kann diese Informationen legal über dich sammeln und an andere weiterverkaufen, einschließlich Betrüger.
Von dir selbst
Wenn du an Umfragen und Wettbewerben teilnimmst oder Produktgarantiekarten auf Papier oder online ausfüllst, kannst du massenhaft persönliche Daten preisgeben. Diese Daten können legal oder im Rahmen eines Betrugs an Dritte verkauft werden.

Wie man Phishing und Social Engineering erkennt
Phishing ist eine der häufigsten Methoden, mit denen Betrüger online angreifen. 2022 erhielt das FBI rund 800.000 Beschwerden über Internetkriminalität in den USA, und über 300.000 davon standen im Zusammenhang mit Phishing(neues Fenster).
Deshalb ist es wichtig zu lernen, wie man Phishing-Versuche erkennt. Phishing-Nachrichten enthalten typischerweise dringende Anfragen, Drohungen oder Versprechen von Preisen und fordern dich auf, sofort zu handeln.
Betrüger könnten:
- Sagen, sie hätten „verdächtige“ Anmeldeversuche bei einem deiner Online-Konten bemerkt und dich bitten, deine Anmeldedaten „zu bestätigen“
- Behaupten, du müsstest deine persönlichen oder finanziellen Daten, wie deine Kreditkartennummer, „verifizieren“, oder dein Konto wird geschlossen
- Sagen, du wurdest für ein „Sonderangebot“, einen „Lotteriegewinn“ oder eine unerwartete „Steuererstattung“ ausgewählt und dann nach deinen Bankdaten fragen, um dir „zu zahlen“
- Dir eine Kontaktanfrage in einem sozialen Netzwerk oder auf einer Dating-Website senden, obwohl du die Person nicht kennst und nicht auf dieser Seite registriert bist
Neben diesen zweifelhaften Inhalten können Phishing-E-Mails weitere betrügerische Anzeichen enthalten, wie gefälschte Absenderadressen, allgemeine Begrüßungen oder verdächtige Links oder Anhänge. Erfahre wie man eine Phishing-E-Mail erkennt.
Was tun, wenn du Phishing vermutest
Obwohl der Inhalt und das Format vieler Phishing-E-Mails sie als „phishy“ entlarven, können einige den Anschein erwecken, von echten Absendern zu stammen, also sei vorsichtig!
Wir empfehlen, die folgenden Schritte zu unternehmen, wenn du eine E-Mail mit einem Button, Link, Anhang oder einer Anfrage nach persönlichen Daten erhältst, besonders wenn sie dringend erscheint:
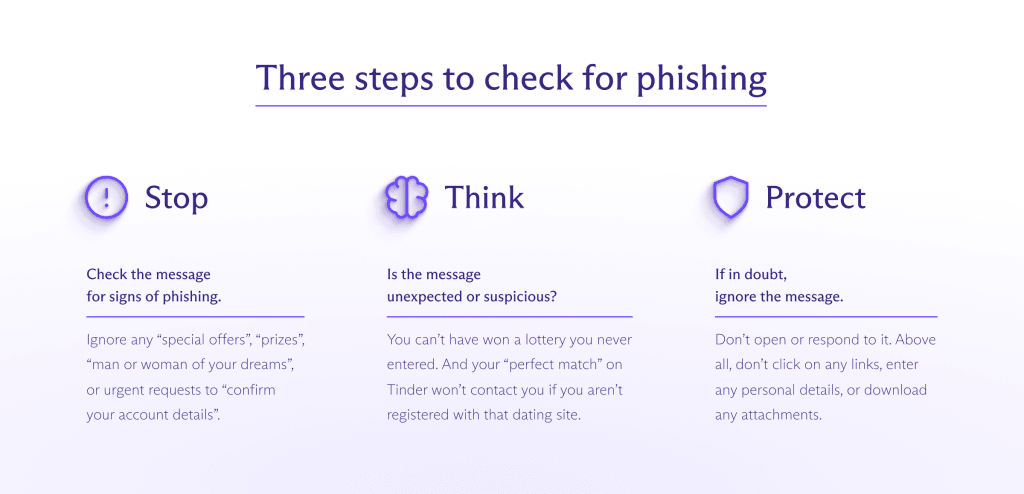
Wenn du dir bei einer Nachricht, die von deiner Bank zu stammen scheint, unsicher bist, kontaktiere die Bank direkt oder logge dich in dein Konto ein, um zu überprüfen. Verwende aber nicht die Kontaktdaten oder Login-Links aus der Nachricht.
10 Wege, um dich gegen Identitätsdiebstahl zu schützen
Sich des Phishings bewusst zu sein, ist nur eine Möglichkeit, dich zu schützen. So stellst du sicher, dass du keine Statistik zum Identitätsdiebstahl wirst:
1. Antworte nicht auf Spam!
Öffne oder antworte nicht auf Spam oder verdächtige (phishy!) E-Mails. Klicke vor allem nicht auf Links oder Anhänge und antworte nicht auf Anfragen nach persönlichen Daten. Gelöscht.
2. Nutze sichere E-Mail
Nutze Ende-zu-Ende-verschlüsselte E-Mail, wie Proton Mail, mit intelligenter Spamfilterung und dem fortschrittlichen Phishing-Schutz PhishGuard. PhishGuard sortiert und kennzeichnet verdächtige E-Mails in deinem Posteingang und warnt dich vor Phishing-Versuchen.
3. Verberge deine E-Mail mit Aliasen
Nutze E-Mail-Aliase, um deine persönliche E-Mail-Adresse privat zu halten. Ein guter E-Mail-Alias-Dienst, wie SimpleLogin von Proton(neues Fenster), ermöglicht es dir, für verschiedene Dienste eine einzigartige E-Mail-Adresse zu erstellen. So kannst du leicht die Quelle von Spam- oder Phishing-E-Mails zurückverfolgen und den Alias widerrufen, wenn er missbraucht wird.
4. Nutze starke Passwörter und 2FA
Erstelle starke Passwörter und besorge dir einen guten, Open-Source-Passwortmanager, wie Proton Pass, um deine Konten zu sichern. Und aktiviere Zwei-Faktor-Authentifizierung (2FA), wo immer du kannst. Mit 2FA können Betrüger deine Konten nicht zugreifen, selbst wenn deine Anmeldeinformationen einmal durchsickern.
5. Installiere gute Antivirensoftware
Installiere eine seriöse Antivirensoftware, die deinen Computer oder dein Handy auf Malware überprüfen kann, die dazu verwendet wird, deine Daten zu stehlen. Antivirensoftware bietet auch Echtzeitschutz und überwacht E-Mails, Anhänge und Webinhalte, um potenzielle Phishing-E-Mails oder Software-Schwachstellen zu markieren.
6. Halte deine Geräte auf dem neuesten Stand
Stelle sicher, dass die Betriebssysteme deines Computers und Handys sowie andere Apps auf die neuesten Versionen mit Sicherheitsupdates aktualisiert sind. Das schützt dich vor Malware, die Software-Schwachstellen ausnutzt.
7. Sichere deine Daten
Erstelle regelmäßig Backups deiner Daten, einschließlich Offline-Backups mit einem verschlüsselten externen Laufwerk. Das verhindert zwar keinen Identitätsdiebstahl, hilft dir aber, deine Daten von einem sauberen Backup wiederherzustellen, falls dein Gerät jemals mit Ransomware oder Spyware(neues Fenster) infiziert wird.
8. Nutze ein vertrauenswürdiges VPN
Besorge dir ein vertrauenswürdiges virtuelles privates Netzwerk (VPN)(neues Fenster) wie Proton VPN(neues Fenster). Ein VPN verschlüsselt deinen Internetverkehr und schützt alle sensiblen Informationen, die du über unsichere Netzwerke wie öffentliches WLAN teilst. VPNs verbergen auch deine IP-Adresse und deinen Standort, was es Cyberkriminellen erschwert, dich online zu verfolgen.
9. Teile nicht zu viele persönliche Daten
Sei vorsichtig mit dem, was du in sozialen Netzwerken postest. Gib keine sensiblen Details wie dein Geburtsdatum und deine Heimadresse preis. Und vermeide es, in Umfragen, Wettbewerben, Produktgarantiekarten oder anderen Formularen Unmengen von persönlichen Daten preiszugeben.
10. Schütze deine physischen Dokumente
Wenn dein Briefkasten außerhalb deines Hauses ist, schließe ihn ab. Das verhindert, dass Kriminelle deine Post mit sensiblen Informationen stehlen.
Bleib sicher mit Proton
Identitätsdiebe haben viele Möglichkeiten, deine persönlichen Daten zu stehlen, aber die oben genannten Schritte sollten sie fernhalten.
Aber egal, wie vorsichtig wir sind, Fehler passieren uns allen. Selbst erfahrene IT-Profis können auf eine Phishing-E-Mail hereinfallen oder ihre Daten in einem Datenleck finden.
Bei Proton ist es unsere Mission, jedem Privatsphäre und Sicherheit online zu bieten. Wir haben Proton Mail so gestaltet, dass du die besten Chancen gegen Phishing und Identitätsdiebstahl hast, einschließlich:
- Ende-zu-Ende- und Nullzugriff-Verschlüsselung, um deine Informationen bei einem Datenleck zu schützen
- PhishGuard fortgeschrittener Phishing-Schutz, um dich vor möglichen Phishing-E-Mails zu warnen
- Intelligente Spam-Erkennung und benutzerdefinierte Filter, um Spam automatisch zu filtern
- Link-Bestätigung, um die URL in Links zu überprüfen, bevor du sie öffnest
- 2FA mit Authenticator-Apps und Sicherheitsschlüssel, um dein Konto zu sichern
- Adressüberprüfung, um zu bestätigen, dass Absender in Ende-zu-Ende-verschlüsselten E-Mails echt sind
- Aliase, um deine persönliche Adresse vor Spammern und Betrügern zu verbergen
- Unser Offiziell-Abzeichen, um es dir leicht zu machen, zu erkennen, welche E-Mails von Proton stammen
Alle Proton-Tarife beinhalten Ende-zu-Ende-verschlüsseltes Proton Mail, Proton Calendar, Proton Drive und Proton VPN(neues Fenster), um deine Internetverbindung überall zu sichern. Also hol dir Proton Mail kostenlos und bleib sicher!