Kryptering forklaret
Kryptering er nøglen til sikkerhed på internettet. Det holder dine personlige oplysninger private og sikre ved at blande dem sammen til det, der ser ud som tilfældig tekst. Læs videre for at få mere at vide om kryptering, hvorfor det er vigtigt, og hvordan Proton bruger kryptering til at beskytte dit digitale liv.

Hvad er kryptering?
Kryptering er den matematiske proces med at omdanne information til en ulæselig kode, så ingen kan tyde den, medmindre de har den korrekte kryptografiske nøgle. Uden kryptering kunne enhver opsnappe, læse eller ændre dine følsomme data, herunder billeder, adgangskoder og beskeder.

Hvad betyder kryptering?
Sagt enkelt betyder det, at dine data er ulæselige uden den korrekte nøgle. Det holder dine oplysninger sikre mod nysgerrige blikke.
Hvordan fungerer kryptering?
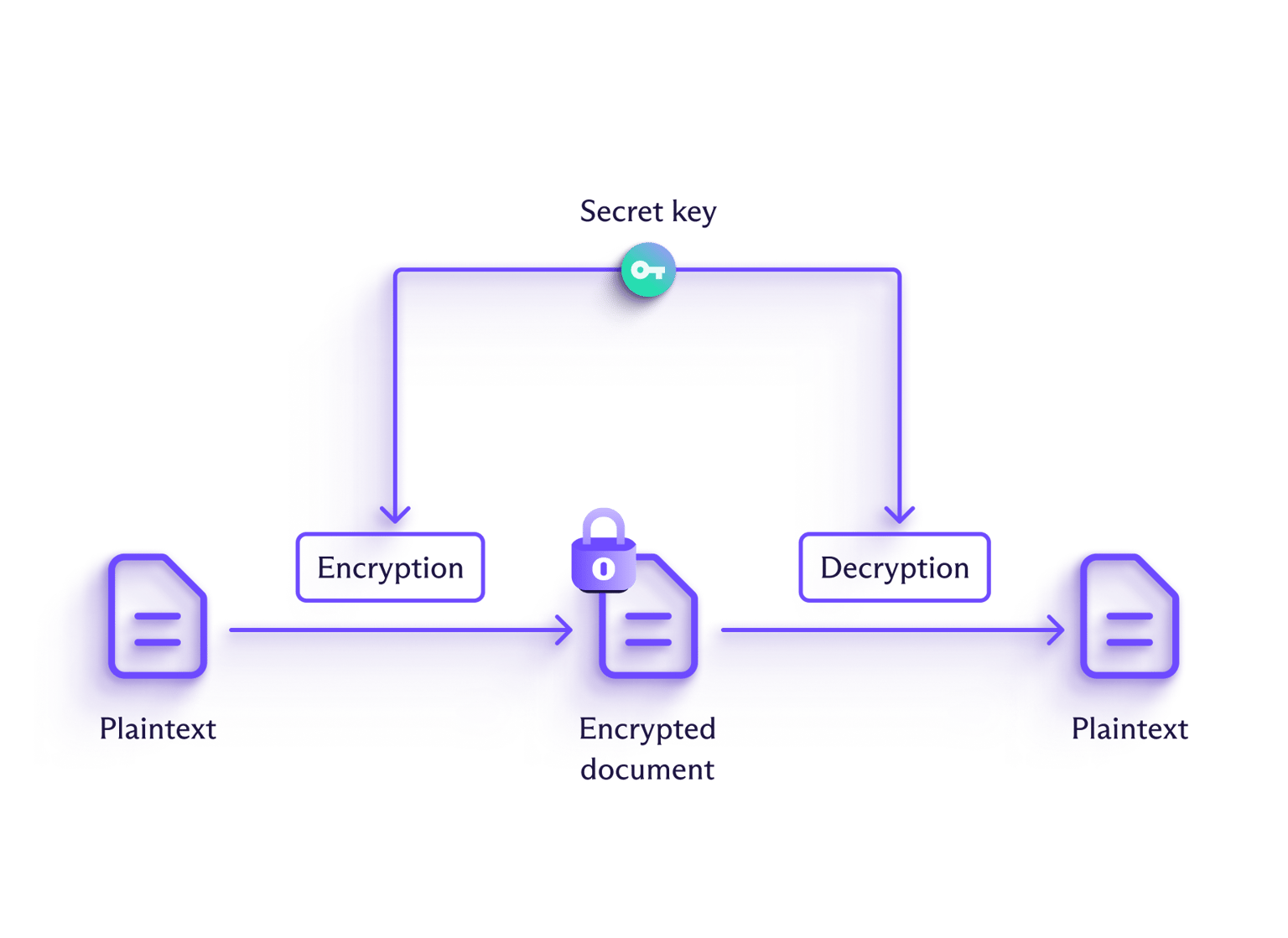
Den mest almindelige måde at kryptere information på er at omdanne den læsbare tekst, kendt som klartekst, til ulæselig tekst, kaldet chiffertekst, ved hjælp af matematiske operationer kendt som algoritmer. Disse algoritmer bruger en kryptografisk nøgle, eller et sæt af delte matematiske værdier (som primtal eller elliptiske kurver), til at forvrænge en fil. Kun den matchende nøgle kan dechifrere filen og konvertere den tilbage til dens oprindelige format.
For en person uden den korrekte kryptografiske nøgle ser en krypteret fil ud som tilfældige data, men kryptering følger logiske, forudsigelige regler. Det er den nødt til, for ellers ville dekryptering være umulig.
Sikkerheden ved en krypteringsalgoritme afhænger af dens kompleksitet. Moderne kryptering bruger komplekse algoritmer og stærke nøglestørrelser, så selv de stærkeste supercomputere ikke kan gætte alle mulige svar inden for en rimelig tidsramme.
Data er typisk krypterede, når de er lagret (“i hvile”), og når de bliver sendt mellem enheder (“under overførsel”).
Eksempel på kryptering
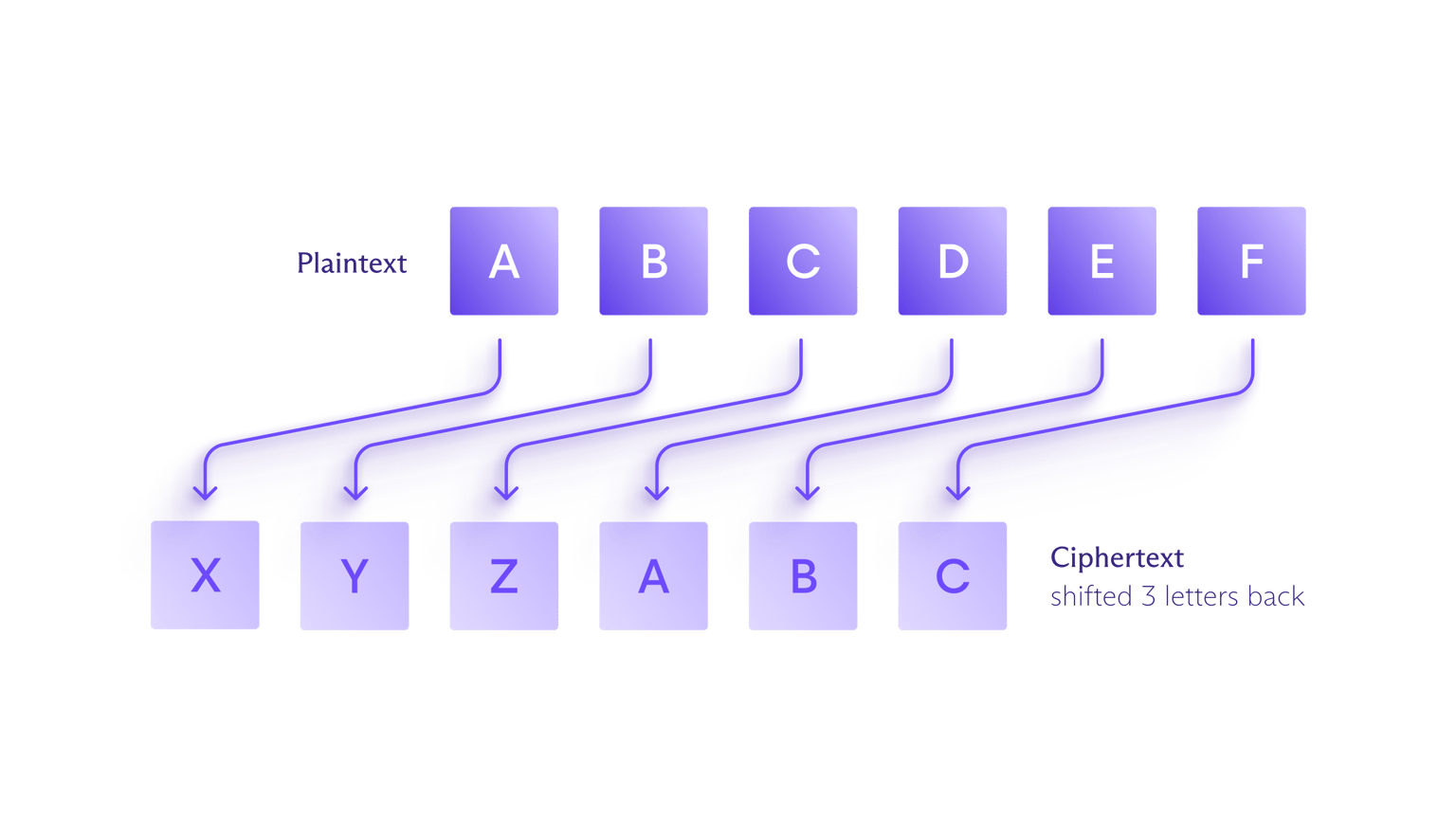
Et af de mest kendte eksempler på kryptering er Cæsarkoden, der blev brugt af Julius Cæsar til at holde sine beskeder private. I denne kode erstattes hvert bogstav i den oprindelige tekst af et andet bogstav, der er flyttet et fast antal pladser op eller ned i alfabetet. Ved f.eks. at flytte tre pladser tilbage bliver "A" til "X" i chifferteksten, "B" bliver til "Y" og så videre.
Koder (en specifik algoritme, der bruges til kryptering) har selvfølgelig siden udviklet sig til at blive langt mere komplekse, hvilket gør dem meget sværere at knække. Moderne kryptering håndteres af komplicerede algoritmer, der kan kryptere klartekst og derefter dekryptere chiffertekst på millisekunder, så du ikke behøver at ofre bekvemmelighed for sikkerhed.
Typer af kryptering
Overordnet set findes der to typer kryptering: symmetrisk og asymmetrisk. Hver har styrker og svagheder.
Symmetrisk kryptering
Ved symmetrisk kryptering bruges den samme nøgle til at kryptere klarteksten og dekryptere cifferteksten. Cæsar-koden er et historisk eksempel på symmetrisk kryptering.
Symmetrisk kryptering er meget hurtigere end asymmetrisk kryptering, men det har en stor ulempe: Hvis en angriber opsnapper både nøglen og beskeden, vil vedkommende være i stand til at læse indholdet. For at beskytte nøglen under overførsel bliver symmetriske kryptografiske nøgler ofte selv krypteret ved hjælp af asymmetrisk kryptering.
Asymmetrisk kryptering
Med asymmetrisk kryptering bruges forskellige nøgler til at kryptere og dekryptere informationen. Disse nøgler er parret: Afsenderen bruger en offentlig nøgle til at kryptere information, og modtageren bruger en privat nøgle til at dekryptere den. Enhver kan bruge den offentlige nøgle til at kryptere information (hvilket er grunden til, at dette også kaldes public key-kryptering), men kun personen med den tilsvarende private nøgle vil være i stand til at dekryptere den.
Tænk på det som at have en brevsprække i din dør: Enhver kan smide breve ind, men du har brug for en speciel nøgle til at åbne postkassen og læse dem. Dette gør det muligt for alle at sende dig en besked uden at udveksle en hemmelig nøgle på forhånd.
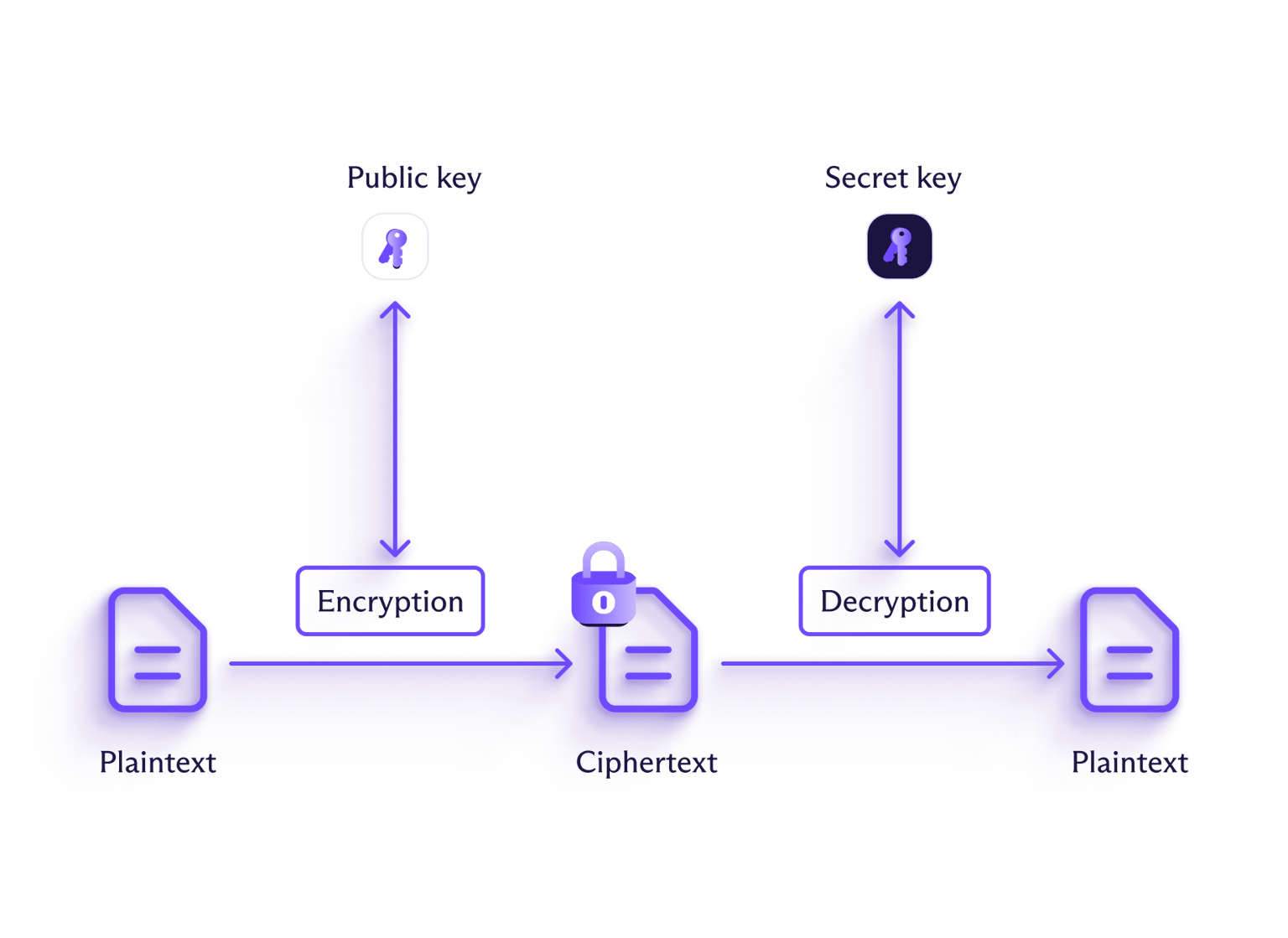
Sammenlignet med symmetrisk kryptering anses asymmetrisk kryptering generelt for at være mere sikker, da det fjerner vanskeligheden ved sikkert at dele krypteringsnøglen. Det har dog også en tendens til at være meget langsommere, hvilket gør det til en mindre attraktiv mulighed for at kryptere større mængder data.
Hvad er krypteringsalgoritmer?
Når du bruger en tjeneste, der krypterer data, håndteres krypteringen af algoritmer, som er komplicerede matematiske formler. De to hovedkategorier er symmetriske og asymmetriske algoritmer.
En krypteringsnøgles sikkerhed er knyttet til dens længde, som måles i bits. Vanskeligheden ved at knække en nøgle vokser eksponentielt, i takt med at dens længde øges.
For eksempel har en 1-bit nøgle kun to mulige værdier (1 eller 0), hvilket gør den let at gætte. En 128-bit nøgle ville derimod have 340 sekstillioner mulige kombinationer (det er 340 med 36 nuller bagved), hvilket gør brute-force-angreb stort set umulige.
Generelt ses symmetriske krypteringsnøgler på 256 bit som sikre, men asymmetriske nøgler skal nogle gange være tusindvis af bits lange for at give lignende sikkerhedsniveauer.
Symmetriske krypteringsalgoritmer
Symmetriske algoritmer krypterer normalt information enten bit for bit (kaldet stream ciphers) eller i blokke af flere bytes (kaldet block ciphers).
Den største fordel ved at bruge symmetrisk kryptering er, at det er hurtigt, hvilket gør det til et godt valg til ting som fuld diskkryptering eller VPN-trafik.
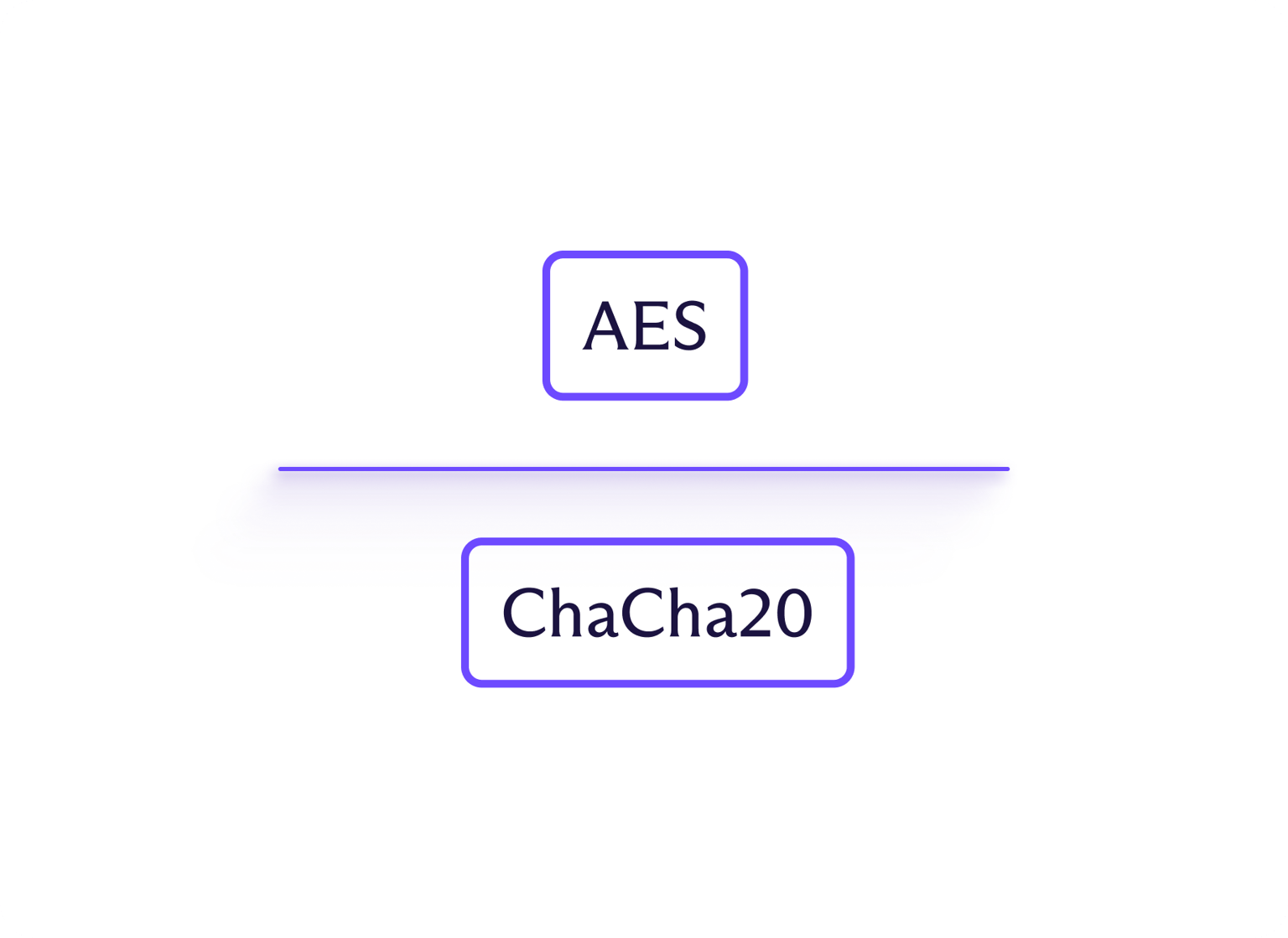
Eksempler på symmetriske krypteringsalgoritmer er AES (Advanced Encryption Standard) og ChaCha20.
Asymmetriske krypteringsalgoritmer
Asymmetrisk kryptering er langsommere end symmetrisk kryptering på grund af den matematik, den skal udføre for at kryptere og dekryptere ciffertekst. Selvom forsinkelsen kan måles i millisekunder, løber det op, når der er tale om store filer.
Det betyder, at asymmetrisk kryptering oftest bruges til at håndtere nøgleudvekslinger, ikke kryptering af store datamængder. En symmetrisk krypteringsnøgle bruges generelt til at kryptere dataene, og derefter anvendes asymmetrisk kryptering (som at kryptere den med modtagerens offentlige nøgle), så den sikkert kan transporteres over åbne netværk som internettet.
Almindelige asymmetriske krypteringsalgoritmer omfatter RSA-kryptosystemet (Rivest–Shamir–Adleman) og ECDH (Elliptic-curve Diffie–Hellman), som bruges til sikkert at blive enige om krypteringsnøgler.
ECDH er en bestemt type elliptisk kurvekryptografi (ECC). ECC er afhængig af strukturen af elliptiske kurver (afbilledet) for at opnå større sikkerhed uden at kræve længere nøgler, hvilket gør det nyttigt til applikationer, hvor ressourcerne er begrænsede, såsom beskeder.
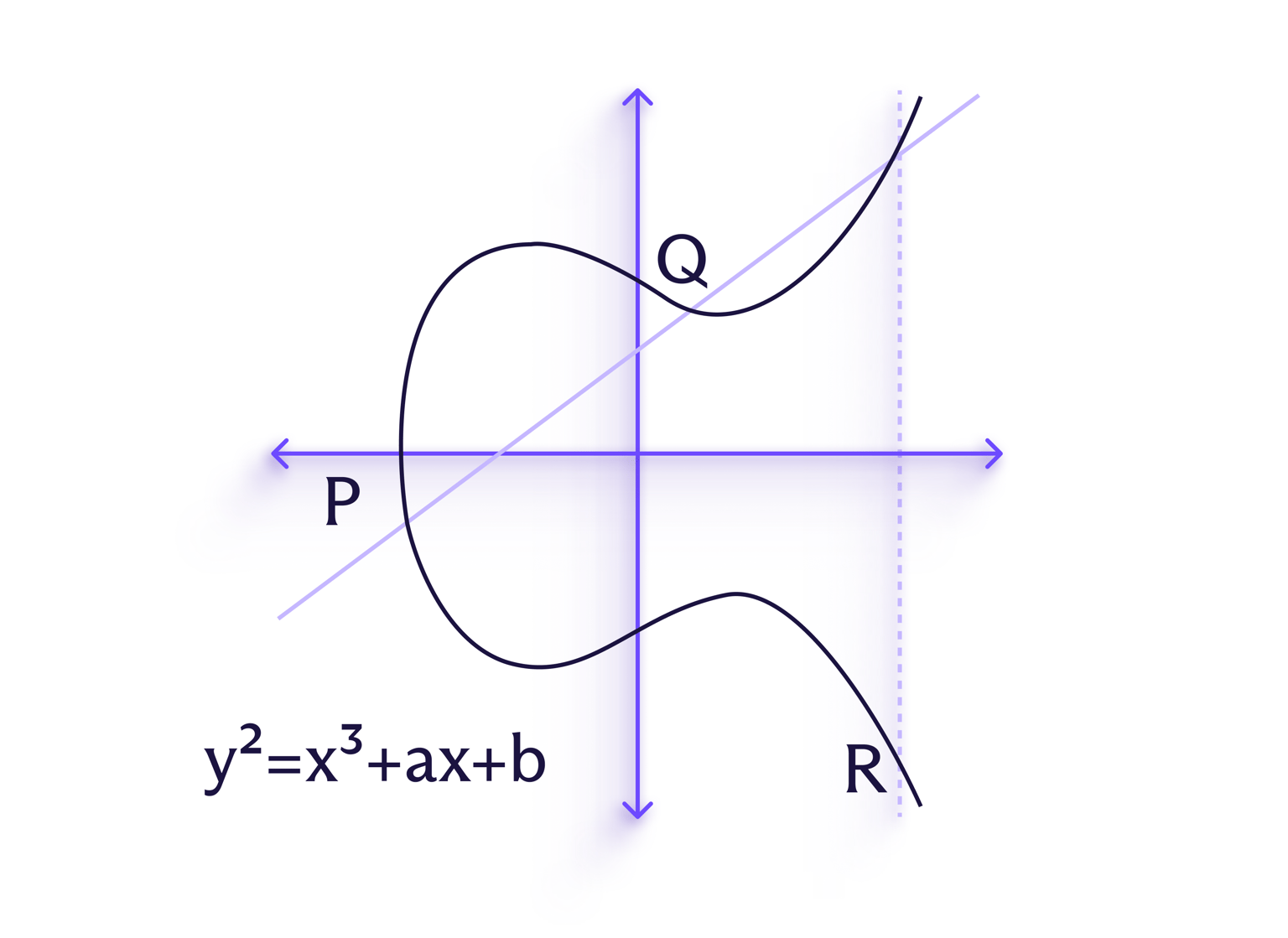
Symmetrisk vs. asymmetrisk kryptering: Forskelle
Symmetrisk kryptering | Symmetrisk kryptering | Asymmetrisk kryptering |
|---|---|---|
Metode | Bruger en enkelt nøgle til både kryptering og dekryptering | Bruger to forskellige nøgler — en offentlig nøgle til at kryptere og en privat nøgle til at dekryptere |
Hastighed | Hurtig | Langsom |
Nøglelængde | Normalt 128-256 bit | Normalt ≥2048 bit for RSA, ≥256 bit for ECC |
Almindelig anvendelse | Beskyttelse af store datamængder, såsom lokale systemer og databaser | Sikring af beskeder og anden kommunikation |
Eksempler | AES, ChaCha20 | RSA, ECDH |
Hvorfor er kryptering vigtigt?
Den største fordel ved kryptering er at sikre, at information forbliver privat, især når den bevæger sig gennem internettet. Kryptering er blevet meget mere almindeligt online, især på besked-apps og tjenester, der håndterer følsomme data, som f.eks. bank-apps.
Faktisk er stort set alle websteder nu beskyttet af TLS (angivet ved “https” i begyndelsen af URL'en). TLS bruger asymmetrisk kryptering til sikkert at udveksle en symmetrisk krypteringsnøgle og skifter derefter til symmetrisk kryptering for at beskytte dine data under sessionen.
Stærk kryptering er især vigtig for virksomheder, da kraftfuld databeskyttelse er afgørende for overholdelse af dataregulativer såsom HIPAA (der regulerer sundhedsdata i USA), GDPR (der regulerer generel databeskyttelse i Europa) og PCI DSS (der regulerer betalingssystemer på verdensplan).
Hvordan bruger Proton kryptering?
Hos Proton kommer dit privatliv og din sikkerhed i første række, og derfor designer vi vores apps til at bruge end-to-end kryptering (E2EE) og brancheførende kryptografi.
Hvor det er relevant, bruger vores apps E2EE, hvilket betyder, at dine data er krypteret på din enhed og ikke bliver dekrypteret, før de når destinationsenheden.
Sammenlign dette med din standard e-mail- eller tjeneste til lagerplads i skyen, som traditionelt krypterer din besked eller fil under overførsel, dekrypterer den ved ankomsten til dens servere og derefter genkrypterer den til lagring — alt sammen ved hjælp af krypteringsnøgler, som den kontrollerer. Dette er i sagens natur mindre sikkert, da udbyderen af tjenesten har de nøgler, den skal bruge for at få adgang til dine beskeder eller filer til enhver tid.
For at anvende E2EE bruger vi OpenPGP-standarden, som kombinerer hastigheden ved symmetrisk kryptering med sikkerheden ved asymmetrisk kryptering, svarende til TLS. Derudover er OpenPGP open source, hvilket betyder, at alle kan analysere det for at validere og forbedre dets sikkerhed.
Hver Proton-tjeneste anvender kryptering forskelligt, afhængigt af hvordan tjenesten bruges. Her er, hvordan vi bruger kryptering for at sikre, at du har kontrol over dine data:
Vores mail-app end-to-end-krypterer e-mails, der sendes fra en Proton Mail-bruger til en anden. E2EE kan aktiveres for e-mails fra Proton Mail til ikke-brugere med funktionen Adgangskodebeskyttede e-mails.
Alle beskeder i Proton Mail lagres med nuladgangskryptering.
Med Proton VPN er al internettrafik krypteret med enten ChaCha20 eller AES-256, to sikre algoritmer.
Derudover bruger Proton VPN kun cifferkoder og protokoller, der understøtter perfect forward secrecy; selvom fremtidige VPN-sessioner bliver kompromitteret, forbliver dine tidligere sessioner sikre.
Skylagring har aldrig været mere sikker. Takket være vores E2EE, som bruger OpenPGP-standarden og ECC, kan ingen andre få adgang til dine Proton Drive-filer uden tilladelse.
Dette gælder også fildeling, så du nemt kan dele dine Proton Drive-billeder, mapper og andre aktiver med privatliv og ro i sindet.
Alle dine brugernavne og adgangskoder er krypteret med E2EE i vores sikre adgangskodeadministrator.
Gennem 256-bit AES-GCM-kryptering opbevares alle lagrede elementer i bokse, der er krypteret med tilfældigt genererede 32-byte nøgler, som ikke kan brute-forces, hvilket holder alle dine legitimationsoplysninger sikre.
Proton Calendar bruger OpenPGP-standarden og ECC til at end-to-end-kryptere dine begivenheder og kontakter. Når du inviterer nogen til en begivenhed, krypteres deres oplysninger, så ingen kan kende deres identitet.
Delte kalenderinvitationer er kryptografisk verificerede, så deltagere kan være sikre på, at det var dig, der inviterede dem.
Beskyt dig selv med Proton-kryptering
Nu hvor du ved, hvordan kryptering fungerer, så tag det i brug. Beskyt dine data med Proton.
Ofte stillede spørgsmål om kryptering
- Er al kryptering lige sikker?
- Er kryptering fremtidssikret?
- Hvis nogen stjæler min krypteringsnøgle, kan de så læse alle mine tidligere beskeder?
- Har jeg brug for kryptering til hverdagsbrug?
- Hvordan beskytter kryptering mod hackere?
- Er kryptering det samme som en adgangskode?
- Sænker kryptering ydeevnen?
- Kan jeg dele mine krypterede data med andre?
- Kan regeringen eller politiet få adgang til end-to-end krypterede beskeder?
- Er kryptering lovligt?