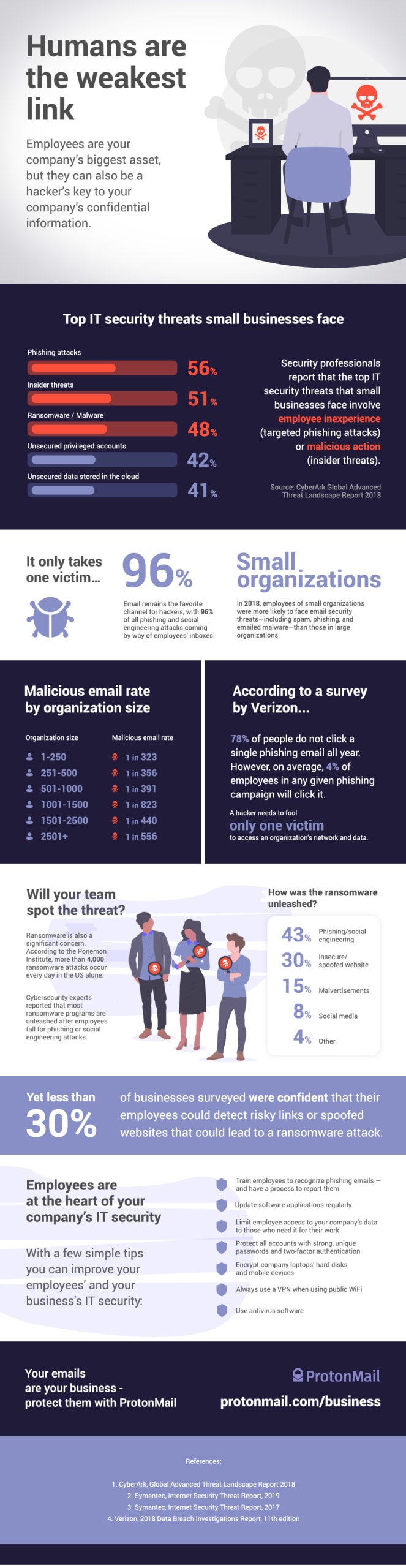
In a previous infographic, we showed that small businesses are prime targets for hackers. One reason is that small businesses often have less capacity to train their employees on IT security. This makes them the perfect target for phishing attacks.
One report even found that most employees were not sure they could spot a phishing email or a spoofed website if they saw one. That leaves your company’s sensitive data vulnerable to theft and ransomware attacks, which threaten to delete your data if you don’t pay the hackers.
References
Cyberark(new window), Global Advanced Threat Landscape Report(new window), 2018
Symantec, Internet Security Threat Report(new window), 2019
Symantec, Internet Security Threat Report(new window), 2017
Verizon, 2018 Data Breach Investigations Report, 11th edition(new window), 2018
Best regards,
The Proton Mail Team
