Since we released paid plans last month, many users have supported us by upgrading to paid plans. Proton Mail does not serve ads or abuse your privacy, so revenue from paid plans is essential for Proton Mail to continue operating(new window). When paid accounts were launched, credit card was the only accepted payment method. Now for the first time, we are accepting PayPal for upgrades to paid accounts.
PayPal Support
Proton Mail has had a contentious history with PayPal(new window), starting when PayPal froze funds during our crowdfunding campaign. Since then, we have been told that PayPal has improved their policies so we are willing to give PayPal another chance. However, the fees for PayPal are much higher, and we are still a bit wary of PayPal so credit card is still our preferred payment method. To pay with PayPal, simply select PayPal as the payment method from our payment page when upgrading your account.

Signatures for Custom Domain Addresses
Proton Mail Paid account users have the ability to add custom domain addresses, or additional Proton Mail address to their primary account. Starting in version 3.1.4 we’ve added the ability to edit and customize the Display Name and Signature for each address in your account.
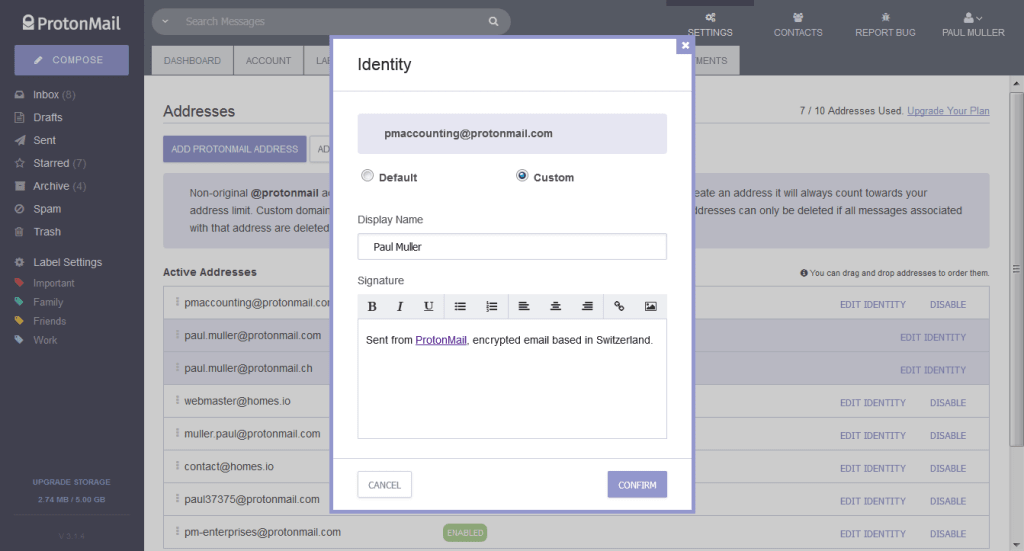
To edit your addresses, simply go to Settings –> Addresses and click on Edit Identity
