Edit (November 2017): Proton Mail also appeared at the end of S03E08 (3.7dont-delete-me.ko). The last scene shows Elliot in his apartment where he checks his inbox and finds an email from Tr3nton, with the subject line “Don’t delete me”.
A few weeks back, we had hundreds of people informing us via Twitter that Proton Mail was being used by Elliot Alderson from this summer’s hit TV show, Mr. Robot. With the highly anticipated season finale airing tomorrow (8/26/2015), we are finally able to share the backstory behind how Proton Mail ended up in Mr. Robot.
Proton Mail was featured in Season 1 of Mr. Robot as the email service used by the main character, Elliot. While the email service used by Elliot might seem like a minor detail, the intensive discussions between our team and the Mr. Robot production team goes to highlight the extreme lengths the Mr. Robot producers have gone for realism.
We have seen many TV shows over the years try to depict hacking in one form or another. We can definitively conclude that Mr. Robot has some of the most realistic portrayals we have ever seen. A large part of our work in building the worlds most secure email service is indeed guarding against hacks of all kind so we have, you could say, some experience in this area.
When the team from Mr. Robot approached us in June, we were quite surprised that they had gone to the lengths of researching secure email services that a character like Elliot would use. This is, after all, a tiny detail that they could have ignored. More surprising though was that they had researched and understood the technical differentiators that make Proton Mail far more secure than other “encrypted” email services. It is hard enough to find people in Hollywood who understand email encryption (looking at you Sony), much less end-to-end encryption. The amount of research they had done was simply astounding.
The story gets far more interesting. Over the course of our discussions with the Mr. Robot team, they mentioned that a security focused person like Elliot would need a way to monitor his own email activity and they asked if this was something Proton Mail supported. Well, we do support this now, you can find the addition of monitoring (logging) in our latest 2.0 release. That’s right, the Mr. Robot team got so deep into their research that they made a product suggestion so good we built it for the hundreds of thousands of security conscious people who use our service.
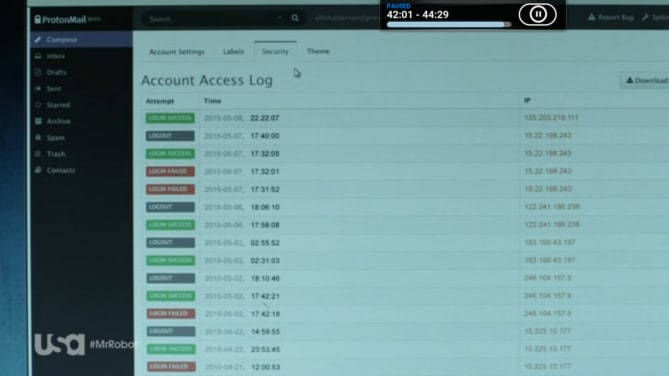 (new window)
(new window)This might be the first recorded case of Hollywood understanding cyber security and privacy so well they influence the development of security software. This attention to detail sets Mr. Robot apart from anything else on TV these days.
If you want to read more about Proton Mail on Mr. Robot, you can also check out this story on Wired(new window) which also features the rest of Elliot’s toolkit. We cannot reveal any details yet, but fans of Proton Mail and Mr. Robot will be happy to know that Proton Mail will be returning to season two of Mr. Robot.