Determining whether a VPN service is trustworthy(new window) can be complicated. Fortunately, there are a few easy steps you can follow to know if a VPN service can be trusted.
The importance of trust when it comes to VPN services cannot be underestimated. Given the recent surge in interest(new window) in VPN services among the general public, we feel it is in the public interest to discuss the VPN trust issue, especially given the general ignorance on this topic. There are many technical factors that need to be considered when looking for the best VPN service, but without trust, all the technical security is irrelevant. This means trust is actually the biggest security risk with most VPN services.
Crucially, VPNs are not zero-knowledge. By design, when you use a VPN, all of your online traffic passes through the VPN, so the VPN provider sees everything. This means that while using a VPN might hide all of your browsing activity from your Internet Service Provider (ISP), this data is completely accessible to the VPN provider (regardless of whether or not they save logs). In other words, when you use a VPN service, what you are doing is shifting trust from your ISP to your VPN provider.
Why VPN trust matters
For many people, moving your trust from a highly regulated telecommunications company, to a VPN company run by shadowy figures, could be an example of misplaced trust. A malicious VPN provider could be operated by an intelligence agency or actively colluding with repressive governments, putting unwitting users at even greater risk.
Recently, the repeal of Internet privacy rules in the US caused a public outcry because now ISPs are allowed to sell browsing history without customer permission. While this is appalling, such behavior is already commonplace in the VPN industry. For example, free VPNs such as Hola have been found to be selling user browsing data, and even access to user devices(new window).
Now that US ISPs can sell your browsing history, using a VPN makes more sense than ever before, but it is important to first check carefully to find the most trusted VPN service.
How to find the most trusted VPN service
Evaluating whether a software or service is trustworthy can be complicated. However, it is rather simple for VPN services, there are just two main things to look for:
1. Jurisdiction
Jurisdiction refers to which country a VPN service is incorporated in and where it is operated from. This is important because many countries have aggressive legislation which could force VPN providers to conduct active surveillance on VPN users on behalf of government agencies. These laws include the Investigatory Powers Act in the UK, and FISA(new window) in the US.
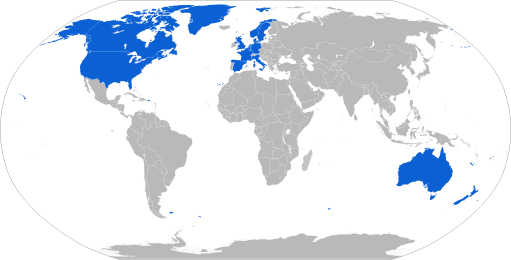
In fact, there are over a dozen countries that collaborate on surveillance. These are collectively known as the Five Eyes and Fourteen Eyes countries(new window) (US, UK, Canada, Australia, New Zealand, Denmark, France, Netherlands, Norway, Germany, Belgium, Italy, Spain, and Sweden). In addition to these, you probably also don’t want to use a Chinese, Russian, or Turkish VPN provider for similar reasons.
 (new window)
(new window)VPN providers from Fourteen Eyes countries should be avoided at all cost because they can be legally compelled to spy on users. A lot of care must be done when performing this check, as many VPN providers go to great lengths to disguise their true jurisdiction. For example, VyprVPN uses a Swiss shell corporation, but is actually based in Austin, Texas, USA(new window). Private Internet Access is operated by a company known as London Trust Media, which sounds like it is based in Europe, but it is actually based in the US (one of the Five Eye countries) and could be legally compelled to spy on users. This type of jurisdiction obfuscation is very common in the VPN industry.
2. Who is operating the VPN service?
Because a VPN provider technically has access to your entire browsing history, a no logging policy is more of a promise than a technical guarantee. Therefore, who exactly is running a VPN service, and their intentions are key components of VPN security. Some VPN services are simply scams(new window), but in the worst case, a VPN service may be actively malicious. Indeed, it was found that 38% of Android VPN apps contained malware(new window).
A good indicator of trustworthiness is the level of transparency around the ownership of a VPN service. Important criteria include:
- Are the individuals operating the VPN service clearly disclosed on the VPN service’s website?
- Are the people behind the VPN service well respected within the security/privacy space and have the necessary technical expertise to operate a service with sensitive security requirements?
- Are you certain the VPN company is not a shell company (e.g. registered to a mailbox in Panama or the Cayman Islands with no actual presence there)?
If the answer is not YES to all of the above questions, then the VPN in question should be avoided because it could be a scam, or worse, working on behalf of state surveillance agencies, spreading malware, or simply insecure.
Can VPNs be fully trusted?
Unfortunately, due to the nature of the technology, there is no way to know with 100% certainty that a VPN service is not spying on you. While this may seem like an extraordinary statement coming from us given that Proton Mail also operates Proton VPN, we really feel that it is in the public interest to shed light on the VPN trust issue. Proton Mail can achieve zero knowledge through end-to-end encryption, but it is technically impossible to build a zero knowledge VPN service(new window). In other words, a VPN service may provide security and privacy, but never anonymity.
However, using a VPN is still essential, because while you cannot be 100% certain that a VPN is trustworthy, you can be 100% sure that your ISP is spying on you and recording your browsing history. By following the two steps outlined above, and also the criteria listed on our guide for how to find the best VPN service, you can have much more certainty about the security of your VPN service.
How about Proton VPN?
Proton Mail is also developing Proton VPN, a free VPN service(new window) that uses innovative technology to provide a higher level of security and trust compared to existing VPN services. You can learn more about what makes Proton VPN different here: https://protonvpn.com(new window)
You can get a free encrypted email account from Proton Mail here.