When you use the internet at home, connected to everything from fitness equipment to game consoles, smartphones, and laptops, marketing companies could be watching you with a tiny piece of surveillance tech you might not even know about.
We’re talking about WiFi pods provided by companies such as Plume Design Inc., a company that has emerged as a significant player in the mesh WiFi market, with over 60 million homes running its surveillance-enabled products worldwide.
Plume has publicly claimed to champion privacy and built-in protection of user data, taking a strong stance in its messaging that it does not monetize user data. That commitment is echoed in its privacy policy, which offers users options like privacy mode and the promise of significant control over their personal information.
But it appears Plume talks to internet users differently than it talks to internet service providers (ISPs) — its other customers:
- To you, Plume promises enhanced connectivity and better control over your smart home network.
- To ISPs, Plume promises marketing insights based on deep analysis of your online behaviors. What that means is Plume harvests and hoards a tremendous amount of sensitive data about its users — even tracking when they are present in their homes(new window).
It’s no secret that ISPs can monitor which websites you visit and sell this data to advertisers. We’ve explored in a previous blog post(new window) how this practice is practically inescapable, as ISPs handle nearly every one of your internet connections with very little public scrutiny.
This article, however, will explore the lesser-known industry of dedicated surveillance hardware and how data harvesters are now reaching their tentacles into virtually every aspect of your digital life.
In the last section, we’ll also recommend specific ways to defend your privacy against companies desperate to profit off your data.
Plume in your home
Homes are getting smarter. There’s a good chance your home has become a hub of interconnected devices — smartphones, laptops, gaming consoles, and fitness machines all connected to the same smart home network. And no one knows this better than Plume.
Plume proclaims it provides a window into today’s smart home, with more than 60 million homes and more than 3 billion connected devices managed on its global network, it says(new window).
The products at the center of Plume’s global network are the devices known as SuperPods, designed to optimize and enhance your home network. But there’s more to these devices than just boosting your WiFi signal.
At the heart of Plume’s ecosystem is OpenSync(new window), an open-source framework that integrates Plume’s services across various ISPs and hardware platforms. That integration allows Plume’s SuperPods and software to continuously gather comprehensive data on your online activities.
ISPs value this data, because it helps them provide more efficient customer support if they have a detailed view of what’s happening on their customers’ home networks. This information gathered inside your home allows them to reduce maintenance costs, since they don’t have to deal with the research and development of routers and software updates. In the Plume ecosystem, for example, router updates are handled with OpenSync and works with a variety of router hardware vendors.
But while those slick WiFi pods promise to enhance control and personalization of your WiFi experience, it also opens the door to deeper data insights that feed into lesser-known Plume services that scrape this data to help ISPs better market to customers with targeted advertising.
The two faces of Plume
A notable discrepancy exists in how Plume communicates with its two primary audiences: consumers and ISPs.
To the former, the company presents itself as a steadfast guardian of privacy. Plume emphasizes that privacy is core to its mission and states it does not monetize individual user data(new window). Plume promises its customers control over their most sensitive information, offering options like privacy mode and access to their data upon request. The data collected, they claim, is to improve user experience.
To the latter audience, however, Plume offers a powerful tool to harness and leverage user data for strategic marketing advantages. Plume’s own website highlights how ISPs can tap into the data from over 60 million homes to come up with new services.
Plume’s appropriately named Harvest platform offers those service providers a gateway to gathering sophisticated “marketing intelligence” to help them better understand “target audience groups for sales and marketing campaigns(new window)”.

Those conflicting statements raise several privacy concerns, suggesting that even Plume contributes to a broader industry practice of commodifying user data under the guise of service improvement — a practice that contradicts the strong privacy assurances given to consumers. This is privacy washing at its best.
Plume’s ‘Harvest’ operations
Harvest’s website promises to provide businesses with insights as specific as customer interests, engagement with content, unique aspects of their online behavior, brands and models of the connected devices, and typical internet usage on a network of 3 billion connected devices worldwide.
Here is a screenshot of how they pitch the capabilities of Harvest on their website:
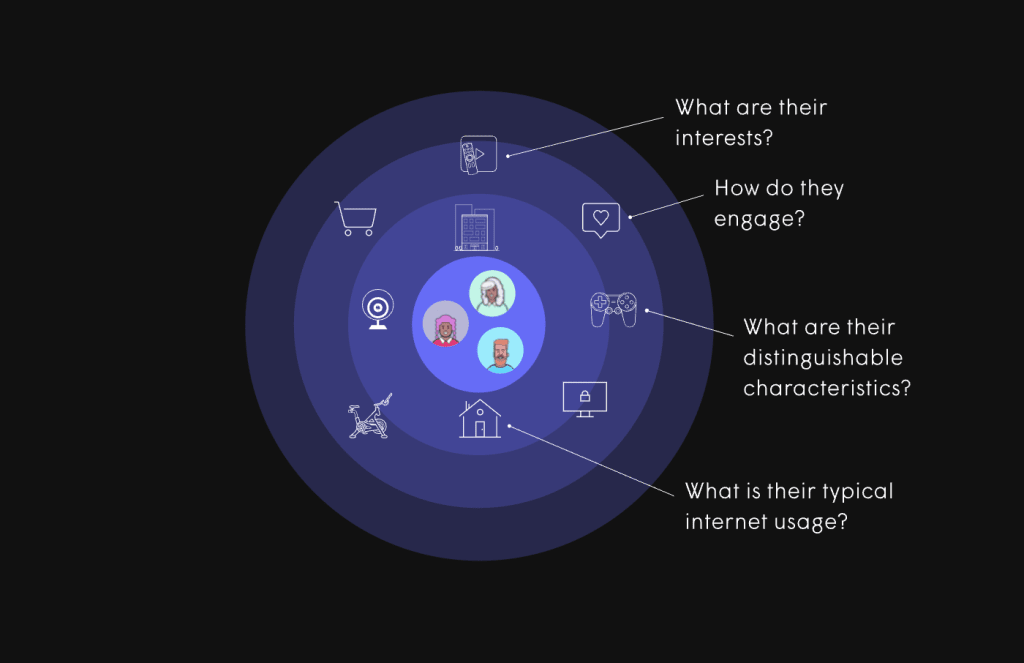
Harvest provides real-time data insights for creating personalized marketing campaigns aimed at acquiring, retaining, and upselling subscribers. Plume emphasizes the importance of knowing the customer base for effective targeting and business growth, suggesting a focus on leveraged subscriber data for marketing purposes rather than direct monetization of individual user data.

Generate(new window), part of Plume’s Harvest suite, offers ISPs advanced tools for detailed customer segmentation, enabling targeted marketing campaigns without needing data science expertise. It allows marketing teams to segment customers by demographics and behaviors for precision marketing. The service is billed as a way to simplify segmentation, bring products to market faster, reduce campaign costs, and increase effectiveness through personalized messaging and syncing with major advertising platforms like Google and Facebook Ads.
While Plume maintains this does not equate to the direct monetization of user data, the functionalities Harvest provides — such as detailed customer segmentation and the synchronization with Google and Facebook Ads (new window)— raise legitimate privacy concerns.
You might call Plume a “pass-through entity” that assists ISPs in leveraging data for profit without directly engaging in the sale of individual user data. That kind of approach appears to allow Plume to maintain that its primary business model is not reliant on monetizing individual user data, which aligns with its privacy policy’s emphasis on user privacy and data control.
A wider industry trend
The US Federal Trade Commission released an extensive report in 2021(new window) that exposed the widespread practice of ISPs collecting data(new window). This is part of a nearly two-decade trend in the tech industry away from a private internet and toward an internet that seeks to exploit users for profit.
The report centered on six major ISPs and three affiliated advertising entities:
- AT&T
- Verizon Wireless
- Charter Communications
- Xfinity
- T-Mobile
- Google Fiber
Some of the FTC’s key findings(new window) included:
- Extensive data collection: ISPs have evolved over time into technology giants capable of swallowing up vast amounts of customer information to target ads or even place users into sensitive categories, such as race and sexual orientation.
- Inadequate privacy protections: “Even though several of the ISPs promise not to sell consumers personal data, they allow it to be used, transferred, and monetized by others and hide disclosures about such practices in the fine print of their privacy policies.”
- Limited consumer control: There is a trend demonstrating how ISPs claim to offer consumers choices with respect to the use of their data, but the options are confusing, potentially leading to low opt-out rates.
While the FTC’s investigation highlighted egregious data collection practices, there appears to be subtle privacy-washing tactics playing out among lesser-known companies, such as Plume, which produces tools that ultimately expand and perpetuate surveillance for profit.
Plume and surveillance capitalism
Plume and similar mesh WiFi systems are part of a larger, data-hungry ecosystem where personal data is turned into a commodity, a trend thoroughly described in Shoshana Zuboff’s book, The Age of Surveillance Capitalism(new window). These systems collect data continuously from everyday activities to optimize services, improve user experience — or target you with ads.
These technologies are often deployed without explicit user consent or awareness, quietly generating hundreds of billions of dollars in ad revenue, powering the profits of Big Tech giants like Microsoft and Google.
Smart homes and hardware are the new frontier: In a 2022 interview with Business Insider(new window), Rob Wilk, Microsoft’s head of advertising, talked of opportunities with properties like Xbox: “just one of the areas we’re going to play in,” he said.
“Imagine a world, not too far off, where all of these pieces are stitched together to make a cleaner, clearer offering for our advertisers,” Wilk said. “And, don’t forget, we’ve also got browsing information and data across gaming and the Microsoft Windows business with billions of users — this gives us a unique advantage to understand intent.”
Wilk dubbed Microsoft’s advertising push a “newfound religion(new window).”
In the case of Plume, its devices can scrape together detailed information from every internet-connected device, no matter the make or purpose. Even household chores can be monetized by companies you may not even be aware of.
This raises important legal and ethical questions about consent, data security, and the extent to which your data can be passed to third parties.
As these technologies become more embedded in our everyday lives, it may seem easy to write off this trend as an inevitability rather than choice. It’s not too late, however, for you to fight against the extensive surveillance that is subtly becoming a pillar of modern life. All it takes is learning how to protect yourself with easy-to-use tools that are more accessible than you might think.
How to protect yourself
If want to to preserve your privacy and protect your data, there are several steps you can take:
- Use Proton VPN(new window) on all capable devices: Install Proton VPN on every device possible — phones, PCs, smart TVs — to encrypt your internet traffic. This prevents ISPs and entities like Plume from monitoring your online activities. Note that using a VPN on your router alone is not sufficient, as smart devices without VPN capabilities, like cameras or smart fridges, may still transmit data to Plume. Proton VPN is based in Switzerland and subject to strict privacy laws that prevent us from being forced to log your data or share it with third parties. VPNs have many additional privacy and anti-censorship benefits(new window). You can even install Proton VPN on routers themselves(new window).
- Look out for Plume products: Bell, the largest ISP in Canada, has offered pods that feature the company’s name on the front(new window). But if you were to flip the pod over for further inspection, you would discover a tiny Plume logo. These free pod devices are often part of “white label” deals ISPs hold with companies like Plume, which is often not explicitly mentioned in the ISP’s branding or disclosures. A “white label” deal refers to a product or service that is produced by one company but is rebranded and sold by another company under its own brand name.

- Use “dumb” WiFi routers: You can reduce data collection by using non-smart WiFi — known as “dumb” routers — that lack the data collection capabilities of common mesh systems, which can gather extensive data on device usage and network interactions to improve network performance and potentially target you with ads. There are various resources and online forums to guide you through purchasing a non-smart router that works best for you.
- Use routers that don’t require a cloud account: These devices operate independently of external servers, meaning they don’t send your usage data or personal information offsite for processing or storage. You can find online resources to help pick the right solution(new window) for you.
- Flash your router: For advanced users, you can better control your network’s privacy settings by installing open-source firmware, such as DD-WRT(new window) or OpenWRT(new window).
If you want to protect your online privacy, you can also urge your local representatives and elected officials to push for new investigations into the ISP industry and pass new laws with your rights in mind.
Big Tech has a bottomless appetite for your most sensitive data with no reservations about using surveillance tactics to track you in your own home. Collective action is crucial in this fight for a future where privacy is the default.
What stories should we tell?
If you have stories about data privacy abuse and surveillance in Big Tech you think we should tell at Proton, we encourage you to reach out. We have set up a private inbox where your privacy concerns can be shared safely and without risk.
In recent months, we have explored Google’s privacy-washing tactics, Big Tech’s mountain of fines, and Outlook’s transformation into Microsoft’s new data collection service.
Email your story ideas to tips@proton.ch and join our mission to protect privacy for all.