Google Drive makes it easy to share files and folders, but you may have wondered at some point whether the people you’ve shared a folder with can see your other folders. We answer this question below and also share some tips for truly secure link sharing.
If I share a folder in Google Drive, can they see my other folders?
No, when you share a folder in Google Drive, the people you share it with cannot see your other folders or what’s in them. Google Drive links only display the file or folder they link to, nothing else.
However, you should be aware that the link will display any and all files and subfolders in the folder you shared. If there’s anything in that folder you don’t want to share, you need to move it to an unshared folder. Google Drive doesn’t let you exclude files or subfolders from folders you share.
This is why you double-check your Google Drive links before you share them. If you send a link to the wrong folder or parent folder, the recipient can see all its contents. When you share a folder, always make sure you’re not accidentally sharing its parent and double-check its contents.
Revoking Google Drive permissions
If you do make a mistake and share a folder you shouldn’t have, Google Drive makes it easy to unshare it. To revoke permissions to a Google Drive folder, all you need to do is go into the sharing settings and change the share settings back to Restricted.
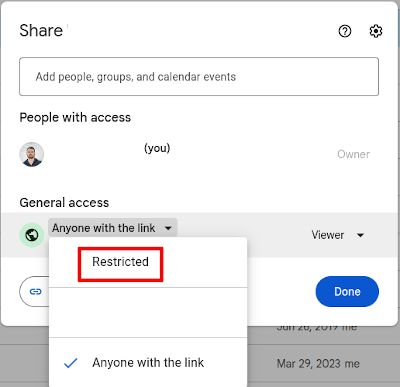
A more secure way to share
Revoking access to a shared folder this way is great, but having more control over who can access your folders makes collaborating much easier. With this in mind, we developed Proton Drive, a secure Google Drive alternative with features built into our file-sharing links that let you control who can access your files and when.
For example, in Proton Drive, you can set expiration dates on all links, meaning you decide when your files will no longer be accessible; Google Drive does not allow this. You can also password protect links, further restricting access and making sure no unauthorized person has access to your folders.
Proton Drive further distinguishes itself from Google Drive with its focus on security and privacy. Google Drive encrypts your files in such a way that Google always has access to them, meaning you must trust Google not to violate your privacy. (Something it doesn’t have the greatest record with.)
Learn how — and why — to leave Google
Proton Drive, on the other hand, uses end-to-end encryption, a type of security that ensures all data is encrypted at all times. All of Proton’s services have it as a default, meaning that nobody, not even us, can see your files.
Like Google, Proton also offers a way to create and collaboratively edit documents that can be stored within your Drive. The difference is that everything you write using Docs in Proton Drive is protected with end-to-end encryption by default. You’ll be able to write freely without concern that your private information will be collected, shared or monetized.
We can protect your information in this way because we’re entirely funded by you, our community. Unlike tech giants like Google, who receive funding from third parties with their own interests, the only interest we represent is that of our users. If this kind of customer-first approach sounds like something you’d want to be a part of, create a free Proton Account today and get up to 5 GB of storage for free. Or deGoogle your life for just $1.