The best free password manager
Securely store, share, and autofill your credentials with Proton Pass, the end-to-end encrypted password manager trusted by millions.
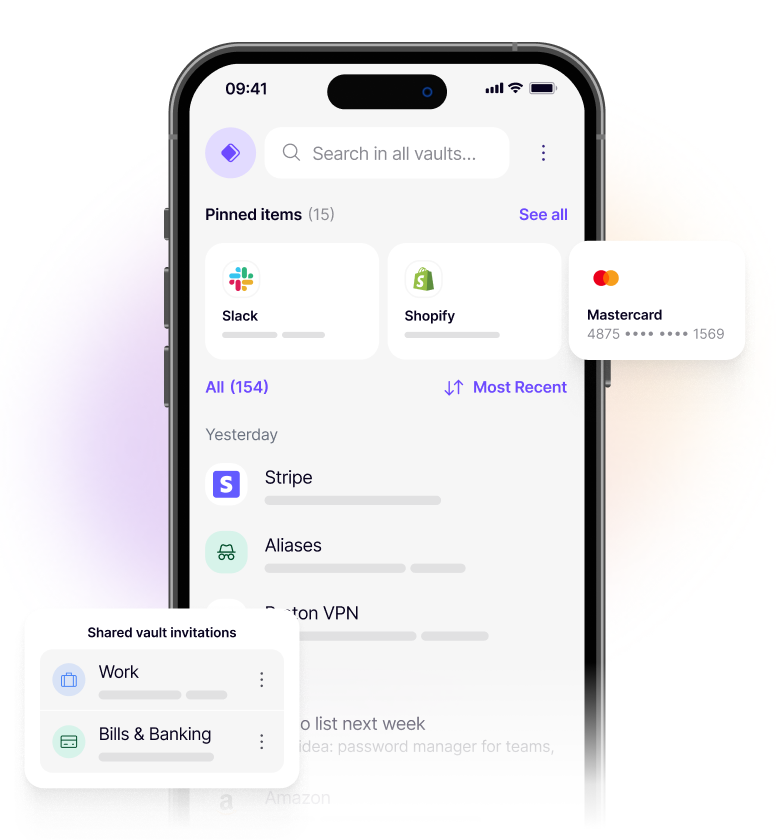
Take control of your digital world.
Keep your passwords safe and sign in instantly with autofill across every device.
Empower your team to work securely.
Manage credentials, control access, and safeguard your organization.
Enterprise‑level security for everyday life
Protected by end-to-end encryption
Protect passwords, passkeys, and credit cards with zero-knowledge, end-to-end encryption. That means no one else, not even Proton can access your sensitive information unless you share them.
Log in faster with autofill
Access your data from anywhere
Safeguard team collaboration
Stay ahead of threats
Trusted by over 100 million people and businesses

ZDNET
“Best free password manager for privacy. Proton Pass is a well-designed and highly secure password manager with a handful of unique features.”

Linus Tech Tips
"Proton has a password manager that got really good, and really quickly. It has support for making burner emails, or aliases, two-factor support, passkey support, and recently, gained the ability to lock your account with a different password than your account password."

Digital Trends
"Overall, I'd recommend Proton Pass as the best password manager, especially if you're looking for a free or low-cost paid plan that's the most intuitive and offers the easiest sharing."
Built to stop breaches before they start
Protect emails with aliases
Automatically create unique email aliases to safeguard corporate addresses, reduce spam, and block phishing attempts.

Simplify two-factor authentication
Securely store, autofill, and display 2FA codes for your team, saving time while keeping accounts protected.
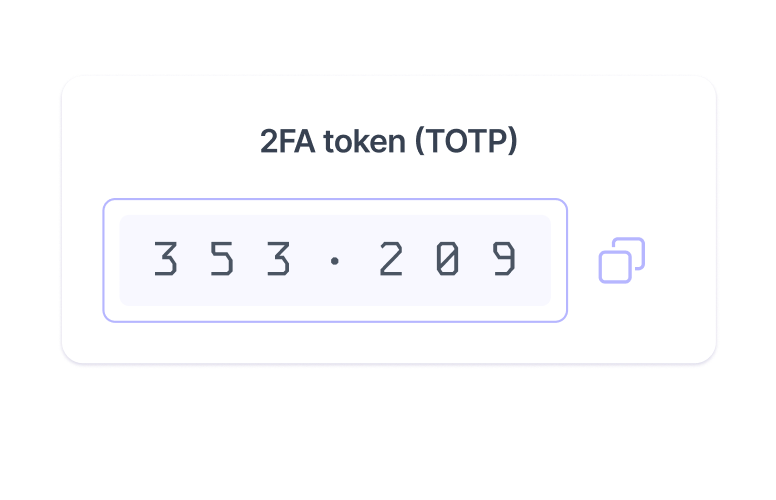
Safely share sensitive information
Send passwords, notes, or credit cards individually or in encrypted digital containers, without losing control of your data.
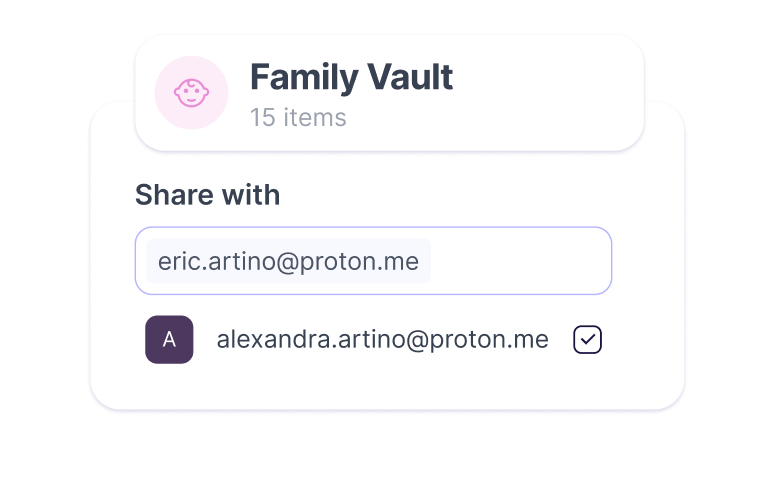
Organize information in one place
Attach files or documents to your stored credentials so that you can access account-related information quickly and securely.
Stay alert to data breaches
Receive immediate notifications if your credentials appear in a third-party data leak, enabling rapid action to protect business data.
Reduce risks with passkeys
Log in securely with phishing-resistant passkeys and enjoy a safer online experience without traditional passwords.
Support compliance and reporting
Monitor usage, flag potential risks, and track your team’s activity to ensure everyone meets your business’s security standards.
Streamline access with SSO
Log in to Proton Pass and all your business tools using a single password, simplifying your team’s workflow and reducing password fatigue.
Define and enforce security policies
Protect business data by controlling what can be shared outside your network and enforcing your own cybersecurity standards.
Switch in one click
Easily import passwords from your browser or any existing password manager to Proton Pass.

Trusted by teams to stay secure with ease
Elemnta, Australia
50-200 employees
“It's really the activity logs that are important for me, and the granular control. The shift to using Proton Pass has greatly benefited us.”
GILAI, Switzerland
Managing IT of 1000+ employees
"We needed a password manager that would be easy to use for the end user and easy to manage for the administrator. I didn't need to do any specific documentation, or any demo except for the provisioning of the account because it's really, really user friendly."
Novalytica AG, Switzerland
11-50 employees
"Onboarding was very easy. Everyone is using it and it works, and no one wants to go back to writing passwords by hand in a sheet or in a notebook."
Morning
350 employees
"I wanted the UX to be beautiful. I think it's important that when you migrate 300 or 400 users, you should choose a solution that isn't too difficult to use or unpleasant to look at. I think it's important for commercial teams to have something user-friendly. That was the case with Proton Pass."
Frequently asked questions
- What is a password manager?
- Is Proton Pass secure?
- I already use my browser to remember my passwords (Chrome, iCloud Keychain, etc.). Why is Proton Pass better?
- Does Proton Pass work on my iPhone or Android phone?
- I already use another password manager. How can I easily switch to Proton Pass?
- How does Proton Pass improve business security?
- How does Proton Pass improve your team’s productivity?