Email protocols explained
IMAP and SMTP are protocols used by email clients to send and receive secure emails. POP3 is a legacy standard that is used less and less often these days.
SMTP
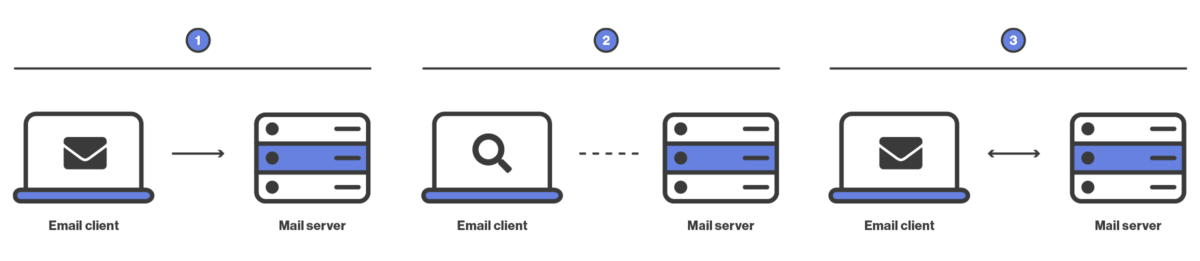
Simple Mail Transfer Protocol (SMTP) is an outgoing email protocol used to send emails from your email client to a mail server. It works as follows:
1. You type your email (and add any attachments) locally in your email client.
2. When you click Send, your email client connects to an SMTP mail server and transfers the email.
3. Once the email is transferred, your email client disconnects from the mail server.
Most mail servers will accept connections over TCP port 587 and TCP port 2525. Different email services may use other ports, although many block outgoing customer connections on TCP port 25 because, while this port is used for communication between SMTP servers, it is often abused for sending spam.
IMAP
IMAP is an incoming email protocol used to retrieve emails from a remote mail server to an email client. IMAP can:
- Group related messages and thread them or place them in folders.
- Determine whether an email has been read, replied to, or deleted.
- Search messages on the mail server.
IMAP works as follows:
1. The email client connects to the mail server (usually over TCP port 993, assuming a secure TLS connection).
2. You view and manage your emails on the server.
3. The email client stays connected to the mail server and continues to update in real-time until you close it.
With IMAP, emails are individually downloaded only when you click to view them. Messages are not deleted from the server (unless you choose to delete them, but even then they will probably be placed in a Trash folder by default rather than deleted outright).
When connected to a mail server using IMAP, any changes you make, such as replying to emails, deleting them, or moving them to other folders, occurs on the mail server. This means when you connect to the server using IMAP on a different device, all changes are synced.
POP3
POP3 is the latest version of the Post Office Protocol(new window) (POP), and is a legacy standard not often used anymore.
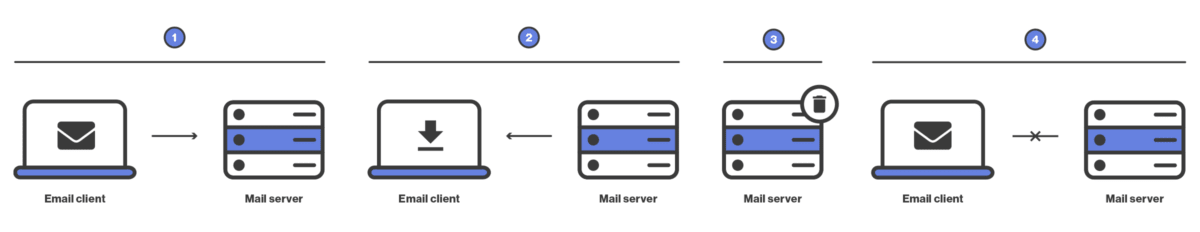
Like IMAP, POP3 is an incoming email protocol, meaning that it is used to retrieve emails from a remote server to an email client. POP3 is a simple protocol that usually works in the following way:
1. The email client connects to the mail server (usually over TCP port 995, assuming a secure TLS connection).
2. Downloads emails.
3. Deletes copies of the downloaded emails from the email server.
4. Disconnects from the server.
POP3 supports various secure authentication methods, and its simplicity is sometimes seen as one of its key strengths. There is very little that can go wrong. The downside of this simplicity is that POP3 offers no advanced email management functions.
Because POP3 deletes emails from the mail servers once they have been retrieved, it is not very useful for synchronizing emails across different devices.
This is partially addressed by an option to not delete emails from the mail server once they have been retrieved, but IMAP handles syncing emails across clients much better.
APIs
In practice, the job of connecting email clients with mail servers is increasingly handled by application programming interfaces(new window) (APIs). These are software programs that likely still use protocols such as SMTP and IMAP, but which hide the internal details in a user-friendly way so you don’t need to do any manual configuration in your email client.
Proton Mail and IMAP, SMTP. and POP3
Proton Mail supports SMTP and IMAP via Proton Mail Bridge. This is an open-source app that allows you to fully integrate your Proton Mail account with any program that supports IMAP and SMTP. This includes Microsoft Outlook, Mozilla Thunderbird, and Apple Mail.
Proton Mail Bridge runs in the background on your computer and seamlessly encrypts and decrypts your email as it enters and leaves your computer. No other email service offers a feature that protects your privacy in this way.
Proton Mail Bridge works with most clients that properly implement SMTP and IMAP. We verify that Proton Mail Bridge works on Apple Mail, Outlook, and Thunderbird, but other email clients should also be compatible. We are working on ensuring greater compatibility with more clients in the future.
Proton Mail Bridge does not support POP3, as Proton Mail wants to ensure a smooth experience across multiple platforms.
Learn more about Proton Mail Bridge
IMAP vs POP3
The first thing to note is that Proton Mail Bridge always uses IMAP, and many other email services (including Gmail) use an API to automatically configure your email client.
If you are manually configuring your email client, choose IMAP. With its advanced email management functions and ease of access across multiple devices, IMAP is by far the best option for most people most of the time.
POP3 is mainly useful if you have a slow or intermittent internet connection, as all emails are downloaded directly to your device. POP3 can also be useful if you have very little storage space on your mail server, as emails are usually deleted from the mail server when downloaded to your device.
Do note, though, that even a Free Proton Mail account comes with 500MB storage, so this is unlikely to ever be an issue when using our service.
TL;DR: Use IMAP.