Email that puts your security first
Our top priority is keeping your data safe.
Need secure email for work? Discover Proton for Business.
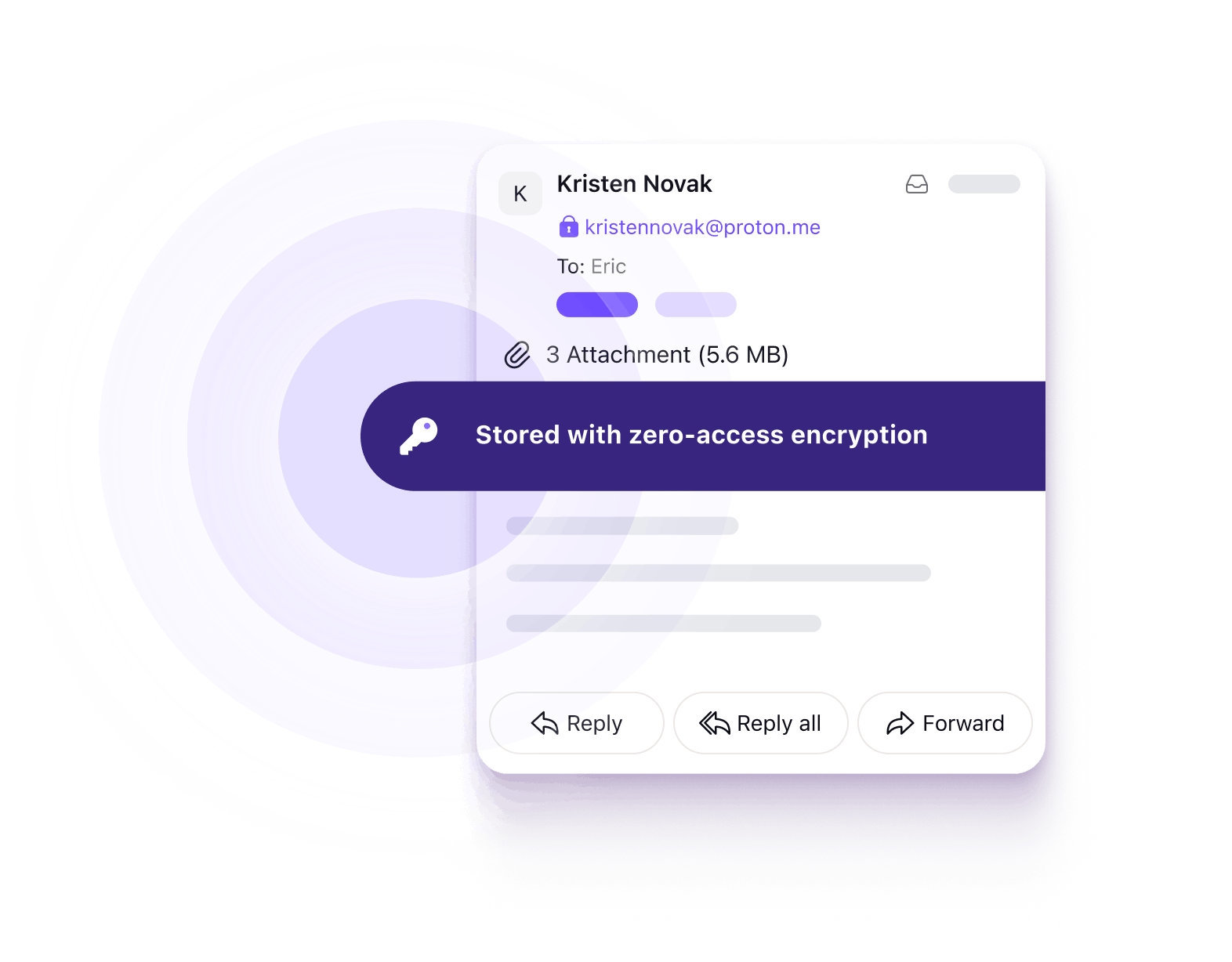
Proton Mail is protected by multiple layers of security and trusted by journalists, security experts, and millions of people around the world.

Strong encryption at all times
Proton believes your data belongs to you. That’s why we use end-to-end encryption and zero-access encryption to ensure that only you can read your emails. We cannot read or give anyone else access to your emails. And this encryption happens automatically — no special software or tech skills required.
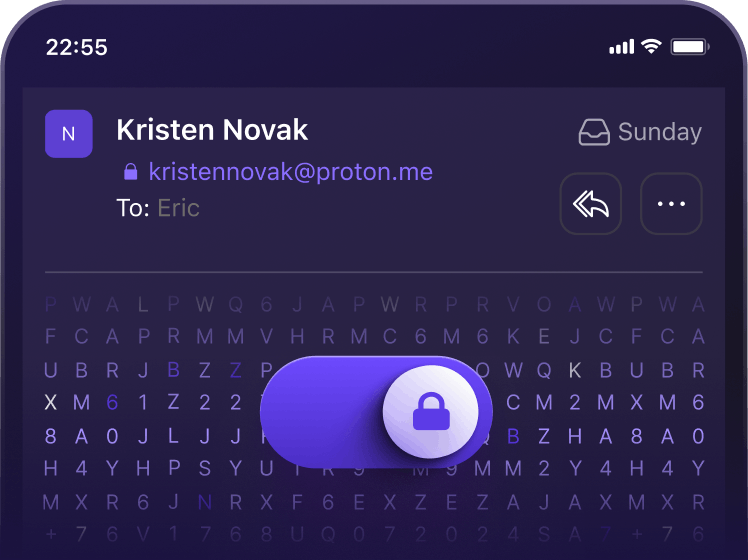
End-to-end encryption
With Proton Mail, emails are encrypted at all times, so we can never access your messages. The content of your emails is encrypted on your device before being sent to our servers, meaning only you and your intended recipient can decrypt it.
You can also use our Password-protected Emails feature to quickly send end-to-end encrypted emails to any email address, not just Proton Mail accounts.
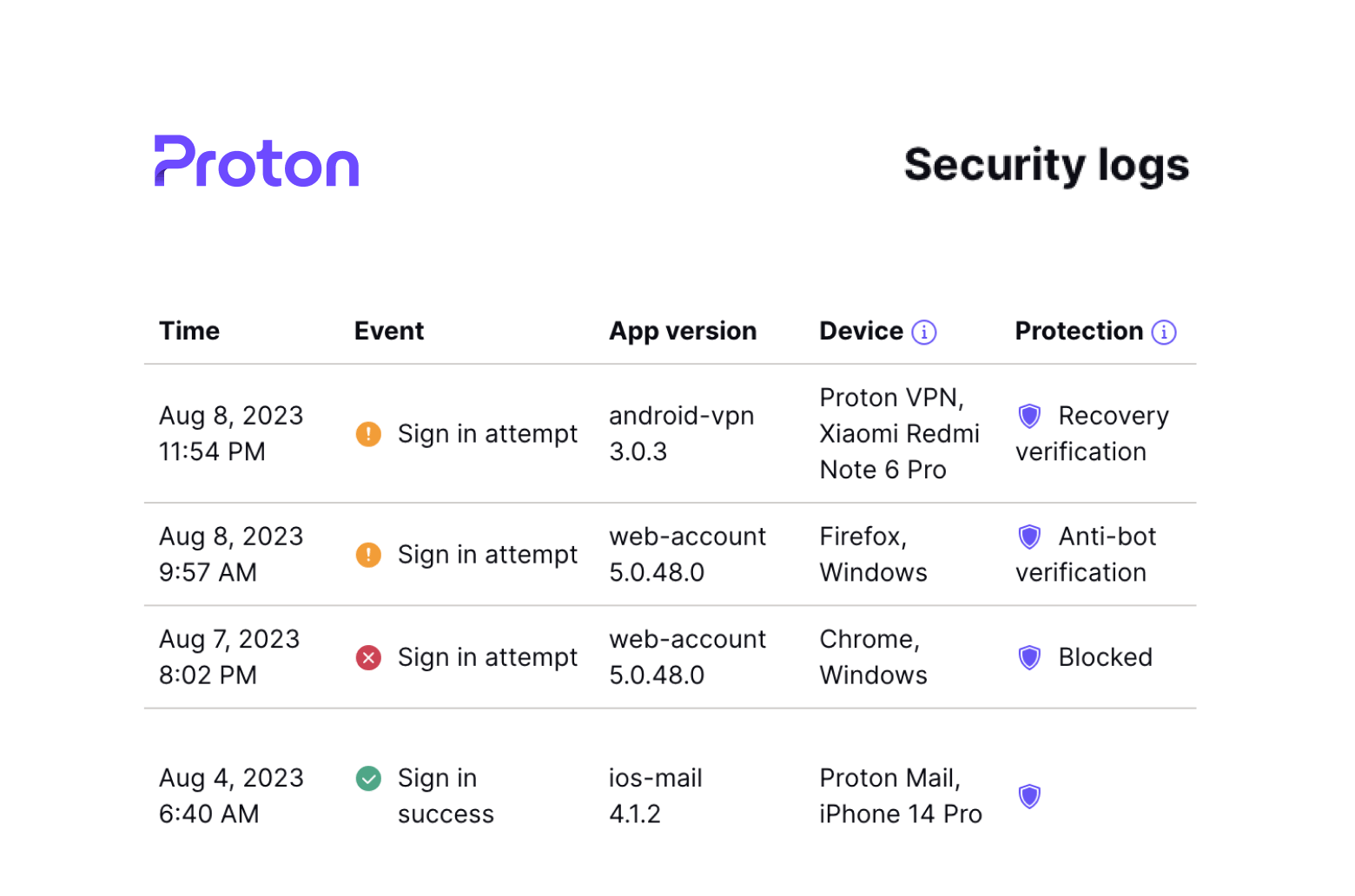
Proton Sentinel
Proton Sentinel is our most advanced account security system, going beyond Proton’s highly secure default protections.
Accounts enrolled in the Sentinel program are monitored 24/7 by our threat detection platform and teams of security analysts who specialize in detecting infiltration and takeover attempts.
By combining AI with human expertise, Proton Sentinel ensures a level of security for people at higher risk of attacks that exceeds what is possible with automated systems alone.
Password-protected Emails
The easiest way to send end-to-end encrypted emails is if both the sender and recipient use Proton Mail. However, you can use our Password-protected Emails feature to send secure emails to people who don’t use Proton Mail.
Simply select a password in the composer before you click send, and your email will be inaccessible to both Proton and your recipient’s email provider.
2FA with hardware security keys
Keep your Proton Account safe. You can use hardware security keys to verify your identity via two-factor authentication (2FA). We support YubiKey and other U2F/FIDO2-compliant keys. Due to their physical nature, security keys are one of the best ways to protect your account, as online attackers cannot get their hands on them. No more reaching for your phone to open an authenticator app either.
Enhanced tracking protection
Your emails belong to you, which is why Proton Mail lets you read them without letting advertisers watch you, build a profile on you, or serve you ads based on your mail activity. Our web app automatically blocks tracking pixels and hides your IP address, so you can read your emails without exposing any personal information.
Zero-access encryption
Proton Mail’s zero-access architecture means we can never access your emails. Emails from other service providers are instantly encrypted on our servers using your public key, meaning we do not have the technical ability to decrypt your messages.
As a result, we cannot hand your emails over to anyone.
Open source and independently audited for transparency
Founded by scientists, we believe transparency and peer review lead to better security for our community. All our apps are open source so that anyone can use and improve them. They have also been audited so that anyone can trust them.
Open source
Every app you use to access your Proton Mail inbox is available for inspection. Open sourcing our code increases the security of our apps because it allows us to leverage the global security community to search for vulnerabilities.

Audited
All Proton Mail code has been independently audited by third-party security experts. The results of those audits are publicly available on our website.
Hardware-level security
We have invested heavily in owning and controlling our own server hardware at several locations within Switzerland, so your data never goes to the cloud. Our data centers are located at highly secure sites that require biometric access. This provides an extra layer of protection by ensuring your encrypted emails are not easily accessible to third parties. On a system level, our servers utilize fully encrypted hard disks with multiple password layers, preserving data security even if our hardware is seized.
Built-in PGP support
Proton Mail users are more secure when they can use end-to-end encryption to communicate with everyone, not just other Proton Mail users. This is why we offer PGP support, which automatically encrypts messages using the public key of your recipient. In fact, you can use Proton Mail to replace your existing PGP client.
Key Transparency
Proton Mail provides a seamless email experience in part because we manage encryption keys behind the scenes. With Key Transparency, Proton automatically checks your contacts’ public keys, so you can be sure you’re emailing the people you intend. This protects you against man-in-the-middle attacks and means you don't have to blindly trust Proton to use the correct keys.
Get your encrypted inbox with Proton Mail
Proton Mail is trusted by tens of millions of people worldwide to keep their communications private.
Unique defenses against attacks
People are the weakest link in any security system, which is why we have added several layers of defense against social engineering attacks and human error. Best of all, these features don’t require any extra steps. Your inbox is secured by default.
Better security through privacy
Better privacy often leads to better security. Proton Mail offers both, empowering you with policies and tools to take control of what information about you is available online.

Based in Switzerland
Proton Mail is based in Switzerland, which means all user data is protected by some of the world’s strictest privacy laws.
Switzerland is politically neutral and is not a party to any foreign intelligence-sharing surveillance networks. Due to the encryption we use, we do not have access to your inbox, and we only respond to official requests from Swiss authorities, which are subject to strong Swiss privacy laws.
Onion address
Proton Mail offers encrypted email over Tor through our onion site(new window) (requires Tor browser).
Connecting to Proton Mail over Tor helps prevent anyone monitoring your network from knowing you are using Proton Mail and provides access to your encrypted email account even if Proton Mail is blocked by your government.
Alternative routing
Sometimes governments attempt to force their citizens to use less secure forms of communication by blocking access to encrypted services.
Alternative routing is another of our anti-censorship features that help ensure you can always access your email. If your connection is being blocked, Proton Mail apps will automatically seek alternative paths to establish a connection with our servers.
Built by and for our community
Thanks to our user-focused business model, Proton is able to work collaboratively to build products that put privacy and security first. This is reflected in the many ways we participate in the security community.
OpenPGP.js
We are the maintainers of the world’s most widely used open-source OpenPGP library in JavaScript.
GopenPGP
We developed and maintain an easy-to-use wrapper library written in Go as well as a fork of the original golang crypto library.
Bug bounty
Because our code is open source, the Proton community benefits from security researchers around the world who participate in our bug bounty program.