As the world is grappling with a sharp rise in the number of COVID-19 cases, fraudsters are trying to capitalize on the state of panic and even the goodwill of others.
More than 1,400 coronavirus-related domains(new window) were registered over the past three months, many used for phishing scams, misinformation, or as an interface for fraudulent sales of counterfeit goods such as masks or hand sanitizers. In the UK, victims of online scams(new window) have lost £960,000 in 105 coronavirus-linked cases since the beginning of February.
Proton Mail has implemented a number of long-standing features to protect(new window) both your personal and business communications. However, there is no such thing as a perfect system — that’s why in this post we’ll describe the most common COVID-19 scams and remind you how to protect against data or financial theft.
Types of coronavirus email scams
Most phishing attempts impersonate a legitimate organization that is offering a benefit (money, products, or information) or is asking for donations or support. As a general rule, scammers try to create a sense of urgency so that you will act without thinking too much. The first warning sign is the alarmist tone, which official institutions wouldn’t use to avoid spreading panic.
According to the UK’s National Fraud Intelligence Bureau, one of the most common coronavirus email scams is sent by criminals pretending to be the US Centers for Disease Control and Prevention(new window) (CDC). The emails claim to provide the victim with a list of active infections in their area. To access the information the victim needs to either:
- click on a link which redirects them to a credential-stealing page, or
- make a donation of support to a fake account
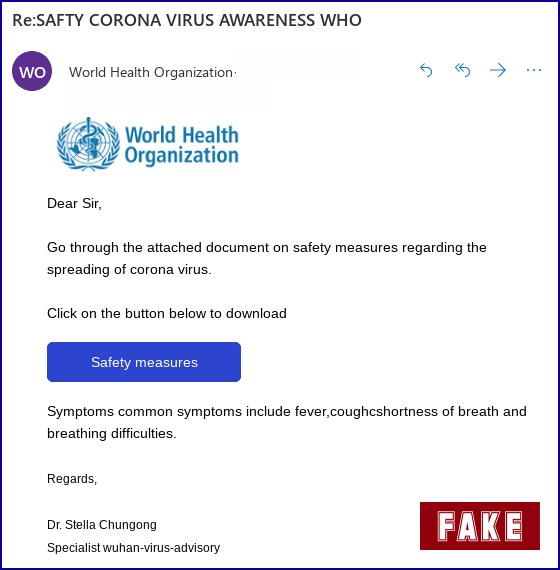
The World Health Organization (WHO)(new window) also alerted people of criminals impersonating the organization to steal money or sensitive information. One of the emails contained a purported document with tips on preventing the spread of the virus, redirecting users to a website taking their credentials.
Other victims received a link to a fake map that delivered malware by imitating the real coronavirus map(new window) created by Johns Hopkins University.
The US Security and Exchange Commission has warned since February of a number of so-called pump-and-dump s(new window)c(new window)hemes(new window) trying to lure inexperienced investors into buying stocks, particularly of smaller companies. They claim the company’s products or services can prevent, detect, or cure coronavirus and cite fake research reports that predict a high stock price.
In Italy, online sales jumped by 75%(new window) in the first weeks of the coronavirus, providing an opportunity for fraudsters trying to sell tests, treatments, or prevention. Sales of counterfeit face masks and hand sanitizers have been reported across the world, with some even containing ingredients banned(new window) for human use or others simply failing to arrive at their destination.
A fake email from the UK tax authority, HMRC, has also reached mailboxes in recent weeks. The scam asks users to click on a link to claim a tax refund(new window). In the US, the FTC has been notified of similar scams(new window) related to the checks program.

Companies and organizations have also been attacked. While companies may be targeted for financial and data purposes, government employees are at risk too. The Brno University Hospital in the Czech Republic was hit by a cyberattack(new window) right as the COVID-19 outbreak erupted.
Protect your data and your wallet
With the number of data breaches tripling in the 10 years prior to 2019, Proton Mail has invested from the start in strong security systems that detect and filter out spam or potential attacks.
All email accounts benefit from anti-spoofing protection (with SPF, DKIM, and DMARC) and link confirmation. There are extra steps you can take to avoid receiving spam emails. You can add a “+” alias to your Proton Mail address when registering new accounts; then if you receive an email to a non-alias address, you know to be on alert for scams. You can also use spam filters, whitelists, and blacklists.
However, you are always the best spam filter. You can avoid the vast majority of spam and phishing attempts by following these simple steps:
- Never respond to unsolicited messages that ask for your personal or financial details, and never share your username or password to access information.
- Verify the sender’s email address and compare it with the official website URL before opening attachments or clicking any links from unknown senders. If you cannot verify it, notify the organization and Proton Mail of a possible phishing attempt.
- Research before making online donations. If you are based in the US, review the Federal Trade Commission’s page on Charity Scams(new window) for more information, or check the organization on GuideStar(new window).
- Don’t accept prizes, grants, or funding from unknown senders.
- Generally, do not accept help from cold-callers. Contact local authorities if you need help to obtain food or medicines.
- Research before making online purchases, especially from companies or people you don’t know or trust. Use a credit card for the purchase. Most credit card providers insure online purchases.
- Install the latest software and app updates to protect your devices from the latest threats.
- Be wary of emails containing spelling and grammar mistakes, using generic greetings, and those demanding immediate action.
Official sources of information on Covid-19
For up-to-date, fact-based information about the coronavirus, follow official websites such as the Centers for Disease Control and Prevention(new window) and the World Health (new window)Organization(new window).
You can also find out the latest local news by visiting the websites of your local authorities. For example, each country’s Ministry of Health website should include a link to an authoritative source or a section about the coronavirus.
Thank you for your support. Stay safe,
The Proton team
You can get a free secure email account from Proton Mail here.
We also provide a free VPN service(new window) to protect your privacy.
Proton Mail and Proton VPN are funded by community contributions. If you would like to support our development efforts, you can upgrade to a paid plan. Thank you for your support.
Feel free to share your feedback and questions with us via our official social media channels on Twitter(new window) and Reddit(new window).
