DKIM is an email authentication method that verifies that a message hasn’t been tampered with in transit. Learn how it works and why you need it to protect your email domain.
Along with the other main email authentication methods, SPF and DMARC, DKIM helps prevent email spoofing (messages with forged sender addresses), spam, and phishing attacks.
We explain DKIM, how it works, and why you need it to protect your domain and ensure your messages are delivered.
What is DKIM?
What is DKIM used for?
What’s the difference between DKIM, SPF, and DMARC?
How does DKIM work?
What is a DKIM signature?
What is a DKIM record?
What is a DKIM selector?
Why use DKIM?
Protect your domain
Improve email deliverability
Build your domain reputation
Easy DKIM setup with Proton Mail
What is DKIM?
DKIM (DomainKeys Identified Mail) is an open standard for email authentication that cryptographically “signs” an email, helping verify that its sender’s address hasn’t been forged (spoofed) and its message hasn’t been tampered with in transit.
DKIM ensures that an email sent from your domain (for example, @yourdomain.com) is signed with an encryption key owned by your domain. This verifies that it came from a legitimate email server, not an attacker’s server that spoofed your domain.
What is DKIM used for?
DKIM is one of the main methods email servers use to authenticate emails. Together with SPF and DMARC, email platforms use DKIM to identify spoofed addresses, helping to sort and prevent spam and potential phishing emails.
If you send emails from your own domain (for example, yourname@yourdomain.com), you should use DKIM to help prevent attackers from spoofing it. If you don’t use DKIM, messages from your domain could be marked as spam or rejected by receiving mail servers.
What’s the difference between DKIM, SPF, and DMARC?
DKIM, SPF, and DMARC are email authentication methods that are used together to verify that emails are genuine. Here are the different roles they play:
- DKIM (DomainKeys Identified Mail) cryptographically verifies that the sender’s address and email contents haven’t been changed in transit.
- SPF (Sender Policy Framework) verifies that an email has been sent from an IP address authorized to send emails from the sender’s domain.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance) makes sure that the domain in DKIM and SPF checks matches the sender’s domain in the From field. It also specifies how email service providers should deliver a message that fails both DKIM and SPF: They can accept, reject, or mark it as spam.
Learn how to set up DKIM, SPF, and DMARC with Proton Mail
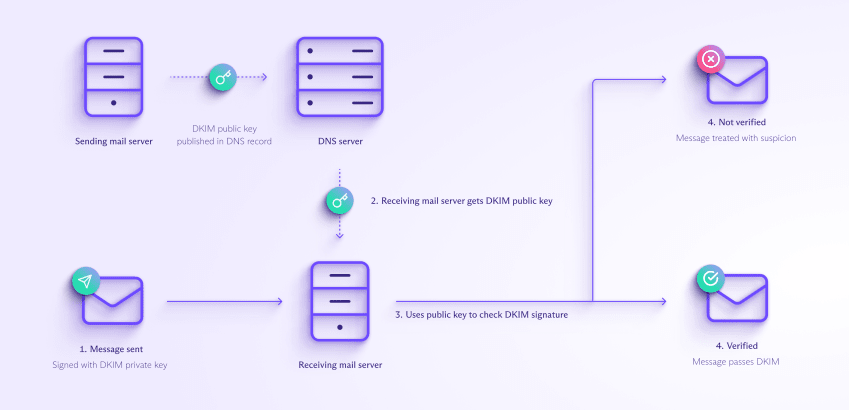
How does DKIM work?
DKIM uses public-key cryptography(new window) to add a digital signature to an email.
The server sending the email uses its DKIM private key to “sign” the email. When the message arrives, the server receiving the mail verifies the signature using the corresponding DKIM public key.
Here’s what happens when you send an email with DKIM:
- The sending mail server creates a hash of the email contents (the From field, subject, message body, etc.) and encrypts it using a private key that only trusted sending mail servers know.
- The server adds the hash to the email header in a DKIM signature.
- When the email arrives, the receiving mail server looks up the corresponding public key in your domain’s DNS records and decrypts the hash in the DKIM signature.
- The receiving mail server then generates its own hashes from the message body and the fields in the email and compares them with the decrypted hashes in the DKIM signature.
- If the hashes match, this verifies that the email hasn’t been changed while being sent, and it passes DKIM.
In short, if an email passes DKIM, we learn that:
- The message was sent from the domain in the DKIM signature
- The message hasn’t been tampered with in transit
If a message fails DKIM, the email is treated as suspicious: The receiving server may send it to the recipient’s spam folder or reject it.
What is a DKIM signature?
A DKIM signature is a digital signature that’s added to an email header to allow the receiving server to verify cryptographically that the message hasn’t been tampered with.
A DKIM signature consists of a series of tags, like v=1, a=rsa-sha256, etc., as in this example:

Here’s what the main tags mean:
| DKIM signature tag | Meaning | Required? |
|---|---|---|
| v=1 | DKIM version number (should always be v=1) | Yes |
| a | Algorithm used to create the digital signature | Yes |
| d | Domain name (used with the DKIM selector to locate the public key) | Yes |
| s | DKIM selector (used to locate the public key — see below) | Yes |
| t | Signature time | No |
| x | Expiration time | No |
| bh | Hash of the message body | Yes |
| h | List of the header fields included in the signature (separated by colons) | Yes |
| b | The digital signature generated from bh and h and signed with the private key | Yes |
When a sent email arrives, here’s how the DKIM signature is checked:
- The receiving mail server uses the DKIM selector (s) and domain name (d) to locate and fetch the public key and decrypt the digital signature (b).
- The server then creates its own hash from the message body and checks it matches the hash in the bh field. Then it creates a hash of the headers (including the DKIM signature containing the bh field) and compares that hash with the digital signature it decrypts using the public key.
- If these hashes match, this verifies that the email hasn’t been altered and the message passes DKIM.
What is a DKIM record?
A DKIM record is where the DKIM public key is stored. The DKIM record is published and publicly available on a domain’s DNS server, so any receiving mail server can retrieve it to verify a DKIM signature.
A DKIM record includes:
- The DKIM selector
- The email domain
- The public key
By looking for a particular DKIM selector and domain name, a receiving email server can find the corresponding public key to check a DKIM signature.
What is a DKIM selector?
A DKIM selector is a unique name that indicates where the public key is stored in a domain’s DNS server. It’s stored together with your domain name in a DKIM record.
When you send an email with DKIM, the DKIM selector is included in the DKIM signature as an s= tag. In the example below, the DKIM selector is protonmail2

You can see the DKIM selector for your domain by emailing yourself and checking the DKIM signature in the email header.
Why use DKIM?
If you have your own domain name, we strongly recommend implementing DKIM, SPF, and DMARC. Here’s why:
Protect your domain
DKIM makes it hard for attackers to send emails pretending to be from your domain (email spoofing). Enabling DKIM will help to prevent bad actors from using your domain for spam or phishing attacks.
Improve email deliverability
Emails with a DKIM signature appear more legitimate and can be verified by a receiving mail server. So implementing DKIM for emails you send reduces the chances of them ending up in the spam folder.
Build your domain reputation
The more you send emails that pass DKIM and other authentication checks, the more you improve your domain’s sending reputation with internet service providers (ISPs) and email providers. So DKIM can help improve your emails’ deliverability over the long term.
Easy DKIM setup with Proton Mail
If you have your own domain, it’s easy to set up email authentication to protect it with a Proton Mail paid plan. We take you step by step through the process of setting up your custom domain with DKIM, SPF, and DMARC authentication.
Set up a single domain with Proton Mail Plus or get Proton Unlimited with support for three domains, 15 addresses, 500 GB of storage, and unlimited hide-my-email aliases.
If you have a business, secure your email with Proton for Business. If you don’t have a domain and just want secure email that respects your privacy, get our Proton Free plan.
All Proton plans include end-to-end encrypted Proton Mail, Proton Calendar, Proton Drive, and Proton VPN(new window).
So join us, and stay secure!
