Email spoofing is a technique attackers use to make a message appear to be from a legitimate sender — a common trick in phishing and spam emails.
Learn how spoofing works, how to identify spoofed messages, and how to protect yourself from spoofing attacks.
Email spoofing definition
Spoofing vs. phishing
Email spoofing examples
How does email spoofing work?
How to identify email spoofing
How to prevent email spoofing
Protect your domain against email spoofing
Email spoofing definition
Email spoofing is when attackers forge (“spoof”) the sender of an email to make it look like it came from another sender.
For example, they can change the From field of a message to make it appear from a person or organization you trust. Spoofing emails is one tool attackers use to launch phishing attacks, distribute spam or malware(new window), or commit other types of cybercrime.
Spoofing vs. phishing
Spoofing is sometimes confused with phishing, but they’re not the same. Spoofing means forging fields in an email to make it look like it’s from someone else.
Phishing means sending emails or other messages that try to trick you into clicking a malicious link or downloading malware, often leading to identity theft, credit card fraud, or other cybercrime.
Spoofing is one method attackers use in phishing emails to lull you into a false sense of security. If you know the sender, you’re more likely to click a malicious link, download an attachment, or otherwise respond to a phishing email.
Email spoofing examples
Here’s an example of an email with a spoofed display name in the From field:

While the display name says security@paypal.com, the domain in the subsequent email address is @paypat4835761.com, which isn’t the official @paypal.com — one of many signs of phishing in this email.
Highly personalized spoofing can be used in phishing emails to imitate someone you know personally. For example, you might get a spoofed email “from your company CEO” aiming to trick you into taking action — an attack known as spear phishing.
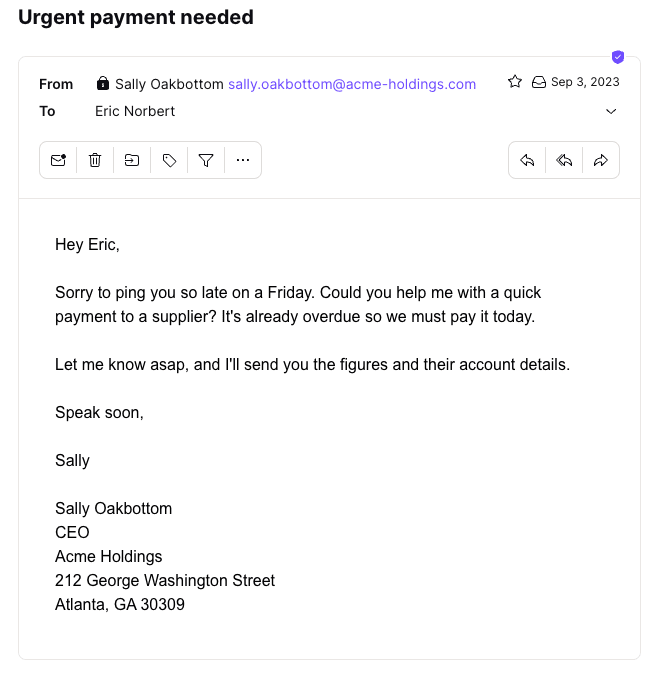
In the example above, both the display name and the address are forged, and the message looks real. But would your boss Sally do something like that? Is that her usual greeting, writing style, and sign-off?
If in doubt, call or message her to find out, or you could end up sending cash to fraudsters. Spear phishing is one of the main methods cybercriminals use for business email compromise (BEC)(new window).
How does email spoofing work?
When you send an email, the SMTP (Simple Mail Transfer Protocol) is used to transfer your message across the internet. It travels in a series of “hops” between SMTP servers before being delivered to your recipient.
However, SMTP doesn’t have built-in authentication, so it’s relatively easy for an attacker to use an SMTP server to spoof the fields in email headers. Email headers are the hidden part of emails containing vital information to identify and authenticate messages (learn how to read email headers).
Here are some fields attackers often spoof:
- From: This is the address the email was sent from, the most commonly spoofed field. By forging this field, an attacker can make the message appear from a trusted source.
- Reply-To: This is an optional address for recipients to reply to. An attacker can redirect your reply to a fraudulent source by spoofing this field.
- Return-Path: Also known as a “bounce address”, this is where an email that can’t be delivered should be returned, like a return address in regular mail.
- Received: For every “hop” on a message’s journey, the IP address of each SMTP server is included in a Received field. Advanced attackers can spoof the IP address to make a message look like it’s from a specific location, though it’s not always easy. For example, with Proton Mail, our mail server adds the latest Received header, so the IP address here is unlikely to be spoofed.
As spoofed emails appear legitimate, you may be tricked into revealing sensitive information, clicking malicious links, or taking other harmful actions.
For example, you may get a message from a company asking you to “confirm” certain personal details. However, if you hit Reply and the Reply-To field is spoofed, you could send sensitive details straight to fraudsters.
How to identify email spoofing
You can tell a spoofed message by checking its content and headers. Here are four ways to spot a spoofed email.
1. Check the display name and sender
Does the display name match the email address at the top? In the example below, the display name says “UPS”, but the domain in the following address (@bmwsetkani.cz) clearly has nothing to do with the shipping company — a sure sign the message is fake.

2. Verify the content
Apart from the display name and email address in the From field, check the rest of the message. Do the contact details (email address, telephone number, and postal address) match what you can find online for this company or sender?
Does the message have other signs of phishing, like obviously fake company logos, a generic greeting, grammar or spelling mistakes, urgent requests, threats, or offers of prizes? If you’re using a computer, you can hover your mouse over links (don’t click them!) to check the URLs look genuine.
3. Inspect the main header fields
If the display name and From field match and look genuine and you still have doubts, check the email header.
First, do the addresses in the From, Return-Path, and optional Reply-To fields match? For example, in the message below, the display name is “Jerry Burns”, and the email address is “jerryburns770@yahoo.com”, which matches the address in the Return-Path.
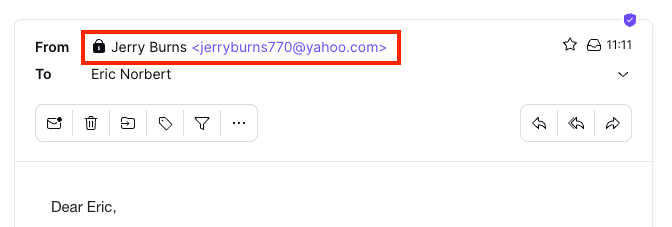

Note that automated transaction emails often use a Return-Path address that doesn’t exactly match the From address so they can attribute the undelivered message to a particular recipient. In these cases, check that the base domain (yahoo.com) matches.
Second, does the domain in the Received field look legitimate? Each SMTP server will add a Received field to the top of the headers, so check the first Received field nearest the bottom.
For example, the base domain in the SMTP server address above is yahoo.com, which matches the email domain in the From field. However, bear in mind that companies often use third parties to send emails, so you might see a server from a bulk email service like SendGrid or Mailchimp here. If in doubt, search for the server addresses online to check they’re genuine.
4. Check the authentication results
While inspecting the email header, check the Authentication-Results field. If the sender is using SPF, DKIM, or DMARC to authenticate emails, these fields should show “pass”:
- spf=pass
- dkim=pass
- dmarc=pass
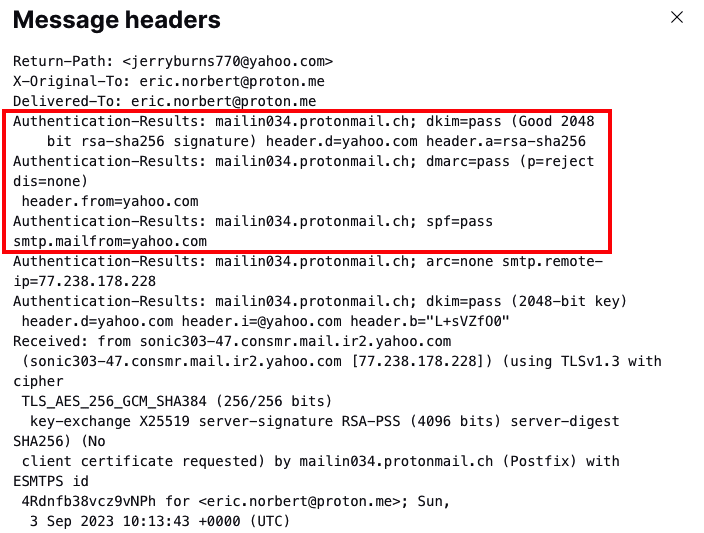
If the email has been forwarded and features ARC authentication, you can also check the ARC-Authentication-Results field to see if the original message passed SPF, DKIM, and DMARC.
By using the above methods, you should be able to identify if a message has been spoofed.
How to prevent email spoofing
You can fall victim to email spoofing in two ways:
- You can receive a spoofed email, for example, as in a phishing attack.
- If you have an address with your own domain (such as you@yourdomain.com), attackers can spoof your domain to use for spam, phishing, or other malicious purposes.
Whether you have a domain or not, here’s how to protect yourself against email spoofing.
Use a secure email provider
Switch to a private and secure email service, like end-to-end encrypted Proton Mail. With Proton Mail, you get advanced spam filtering and other security features to protect your account from unwanted messages out of the box.
Implement email authentication
If you have your own domain, it’s essential to implement the main email protocols to protect your domain from spoofing:
- SPF (Sender Policy Framework) verifies that an email has been sent from an IP address authorized to send emails from the sender’s domain.
- DKIM (DomainKeys Identified Mail) cryptographically verifies that the sender’s address and message contents haven’t been changed in transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance) ensures that the domain in DKIM and SPF checks matches the sender’s domain in the From field, an essential check for spoofing.
With Proton Mail, you can easily set up these anti-spoofing measures with a simple wizard.
Report suspicious emails
Most major email services, like Gmail, Proton Mail, and Outlook, have automatic spam filters that send suspicious messages to the spam or junk mail folder.
If you see a spoofed email in your inbox, report it as spam or move it to the spam folder. That way, the spam filter should catch future messages from that sender. If it looks like phishing, most major email providers also give you a way to report phishing.
Block and filter spam
If you get persistent unwanted emails with a spoofed address, you can always block the address to remove them from your inbox and reduce the risk of responding to them.
Major email providers, like Proton Mail, also allow you to filter emails, so you can send suspected spoofed emails to spam or another folder to review later.
Check for signs of spoofing
Above all, beware of all emails from unknown senders. Check the ways to identify spoofing above before responding to them, clicking on links, or downloading attachments.
And as always, follow the usual security advice to protect yourself if you do fall victim to a spoofed phishing email:
- Use strong passwords and two-factor authentication (2FA).
- Keep your operating systems, apps, and antivirus software updated to block or remove malware(new window).
Protect your domain against email spoofing
To sum up, follow the tips above to ensure you don’t fall victim to email spoofing. Above all, watch out for signs of spoofing and phishing, and if in doubt, don’t respond in any way! Report the message as spam or phishing, or just delete it.
If you have your own domain, using DMARC with SPF and DKIM authentication is the most effective way to prevent abuse of your domain.
Setting up DMARC can be tricky because it depends on successfully implementing SPF and/or DKIM, but it’s easy with a Proton Mail paid plan. We take you step by step through setting up your custom domain with DKIM, SPF, and DMARC.
With Proton Mail, you also get automated anti-abuse and account security and Proton Sentinel, an advanced high-security program for those who need maximum account protection and support.
So join us, protect yourself from spoofing, and stay secure!
