Sender Policy Framework (SPF) is an email authentication method that verifies that a message has been sent from an authorized mail server. Learn how it works and how it helps to protect your email domain.
Used with DKIM and DMARC, SPF is one of the main ways internet service providers (ISPs) and email platforms identify and block spam and phishing attacks.
We explain SPF, how it works, and why you need it to help protect your domain and ensure your messages are delivered.
What is Sender Policy Framework (SPF)?
What is SPF used for?
How SPF differs from DKIM and DMARC
How does SPF work?
What is an SPF record?
SPF and mail forwarding
Why use SPF?
Beat spammers and scammers
Improve email deliverability
Boost your domain reputation
Easy SPF authentication with Proton Mail
What is Sender Policy Framework (SPF)?
Sender Policy Framework (SPF) is an email authentication protocol that allows you to specify the servers authorized to send mail from your domain, making it harder for fraudsters to spoof (forge) your address.
If you send email from a custom domain (for example, @yourdomain.com), you can list the IP addresses(new window) of the mail servers authorized to send your mail. By checking your list of IP addresses, email services and ISPs can identify whether the message came from a trusted server.
What is SPF used for?
SPF is one of the main methods email servers use to authenticate emails. It helps email providers identify spoofed addresses and block spam and phishing emails.
However, SPF alone isn’t enough to spot spoofed messages because the sender’s address (From field) can be forged. By using SPF with DKIM and DMARC, email providers can verify that the sender’s domain matches the From field, confirming that the address isn’t spoofed.
How SPF differs from DKIM and DMARC
SPF, DKIM, and DMARC are email authentication protocols that are used to verify that emails are sent from a legitimate sender, but they all work differently. Here’s how they work together:
- SPF (Sender Policy Framework) verifies that an email has been sent from an IP address authorized to send emails from the sender’s domain.
- DKIM (DomainKeys Identified Mail) cryptographically verifies that the sender’s address and message contents haven’t been changed in transit.
- DMARC (Domain-based Message Authentication, Reporting, and Conformance) ensures that the domain in DKIM and SPF checks matches the sender’s domain in the From field. It also specifies how email service providers should deliver a message that fails both DKIM and SPF — accept, reject, or mark it as spam.
Learn how to set up SPF, DKIM, and DMARC with Proton Mail
How does SPF work?
SPF checks whether an incoming email has been sent from a mail server authorized to send mail from that domain.
First, you must create an SPF record that lists the IP addresses of the mail servers authorized to send mail from your domain. Then you’re ready to send messages with SPF as follows:
- You send an email, for example, from the address you@yourdomain.com. Suppose the message is sent from one of your authorized email servers with the IP address 185.70.40.111.
- When the email arrives, the receiving mail server checks the sender’s address in the Return-Path (also known as MAIL FROM) field of the email header and looks up the SPF record for your domain (in this example, yourdomain.com).
- The receiving mail server checks whether the IP address from which the mail was sent (185.70.40.111) is listed in your SPF record.
- If the IP address is listed, the message passes SPF; if it isn’t, it fails.
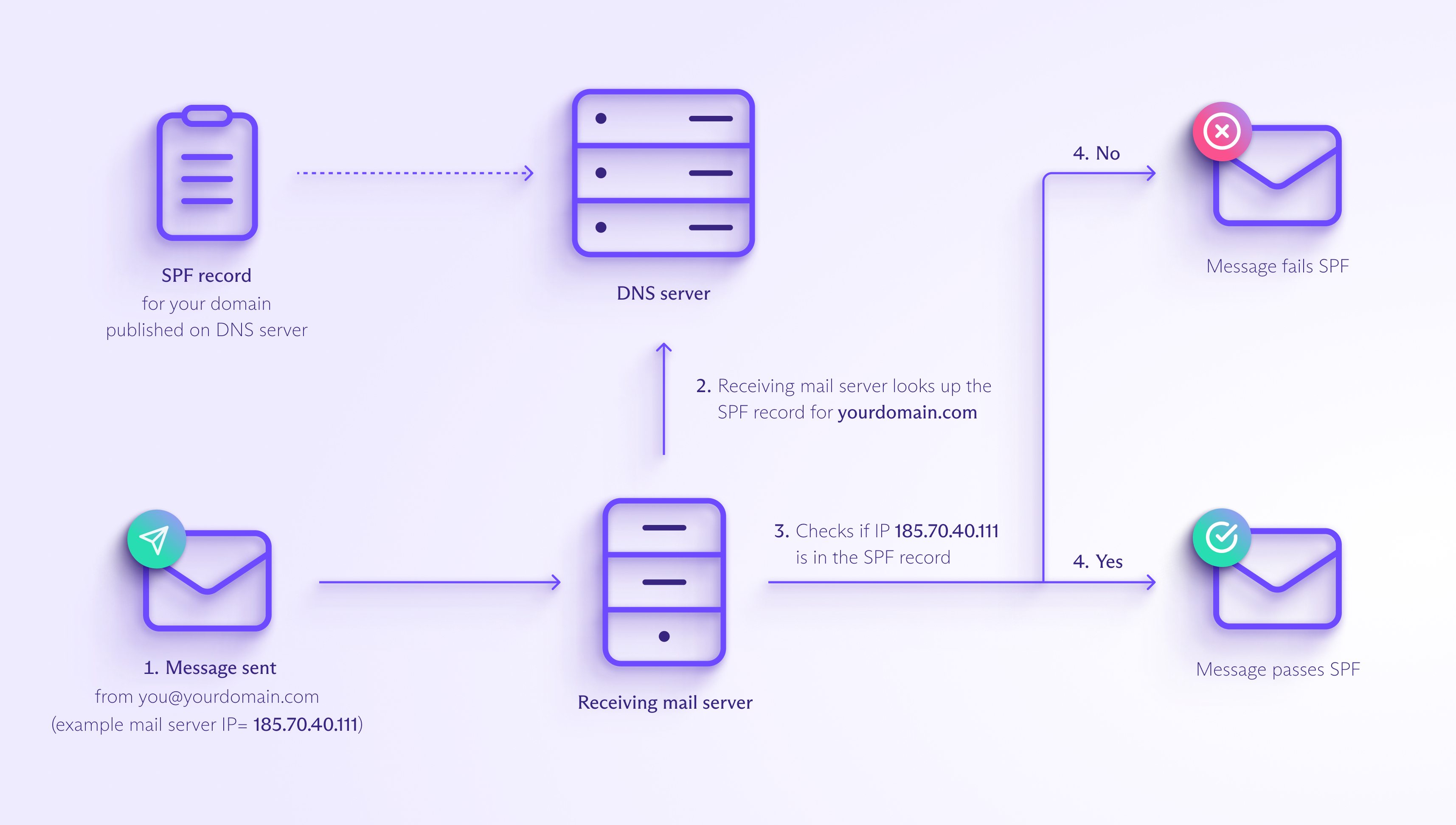
Note that in step 2. the receiving mail server looks up the SPF record for the domain in the Return-Path field, which doesn’t need to be the same as the domain in the From field. Even if the domain in the From address is spoofed and differs from that in the Return-Path, a message can pass SPF.
That’s why you need DMARC to verify that the domain in the SPF and DKIM checks matches the sender’s address in the From field.
What is an SPF record?
An SPF record is a type of DNS text record(new window) that lists the IP addresses of the servers authorized to send email from a particular domain. SPF records are published on the domain’s DNS server, so any receiving mail server can look up the list to check whether an email has been sent from a trusted server.
SPF record example
Here’s an example of an SPF record with an explanation of what it means below:

v=spf1 ip4:185.70.40.111 include:_spf.protonmail.ch mx ~all
- v=spf1: The SPF version number. Every SPF record must begin with this tag.
- ip4: The IP address(es) of the servers authorized to send email from your domain. They can be IPv4 or IPv6 addresses(new window); IPv6 addresses use the tag ip6.
- include: Instructs the server to check the SPF records of the additional domain mentioned. In this example, the server would look up _spf.protonmail.ch and add the IP addresses found there to the list of authorized addresses.
- mx: Any IP addresses that match the mail servers listed in the MX records(new window) of the sending domain. For example, Proton Mail uses mail.protonmail.ch and mailsec.protonmail.ch.
- ~all: Tells receiving email servers what to do if an email doesn’t pass SPF. The three most common all tags are:
- ~all: Mark the message as suspicious
- –all: Reject the message
- ?all: Receiving email server decides (neutral recommendation)
However, since the introduction of DMARC, many email providers, including Proton Mail, no longer use these all tags. Apart from checking that the From field matches the domain in SPF and DKIM checks, DMARC tells servers what to do with messages that fail these checks, making the all tags redundant.
In the example above, the SPF record authorizes mail to be sent from:
- 185.70.40.111
- The IP addresses found in _spf.protonmail.ch
- The IP addresses of the mail servers listed in the domain’s MX records
If an email from this domain is received from an IP address not listed above, the message fails SPF and is treated as suspicious.
SPF and mail forwarding
One limitation of SPF is that it doesn’t work reliably with forwarded emails.
When forwarding a message, if the sending mail server replaces the original sender’s email address in the Return-Path (MAIL FROM) field with the forwarder’s address, the receiving server will check the SPF record of the forwarder’s domain. In this case, the message should pass SPF.
But not all email platforms rewrite the Return-Path field when forwarding. If the mail server preserves the original sender’s address in the Return-Path field, the receiving mail server will check the original sender’s SPF record. As this doesn’t include the IP address of the forwarding server, the message fails.
Fortunately, if an email fails SPF, it may still pass the DKIM check because DKIM verifies a message’s content, not its sending IP address. As long as you don’t change the content and structure of the original message, it should pass DKIM.
Why use SPF?
Along with DKIM and DMARC, SPF is one of the main ways you can protect your domain and ensure your emails get delivered. Here’s why you should use it:
Beat spammers and scammers
SPF makes it harder for cybercriminals to send messages pretending to be from your domain (email spoofing). Specifying trusted mail servers with SPF helps to prevent fraudsters from using your domain for spam and phishing attacks.
Improve email deliverability
SPF helps ISPs and email platforms identify legitimate emails. So using SPF increases the chances of your messages being delivered instead of ending up in the spam folder.
Boost your domain reputation
The more your emails pass authentication checks like SPF, the more you improve your domain’s reputation with email platforms. So SPF can help improve your emails’ deliverability in the long run.
Easy SPF authentication with Proton Mail
If you have your own domain, we strongly recommend setting up SPF, together with DKIM and DMARC, to improve your email security and deliverability.
Implementing all three is easy if you have a Proton Mail paid plan. We explain how to set up your custom domain and DKIM, SPF, and DMARC with a simple wizard.
Get Proton Mail Plus for a single domain, or get Proton Unlimited with support for three domains, 15 addresses, 500 GB of storage, and unlimited hide-my-email aliases.
If you have a business, you can secure your email with Proton for Business.
Or if you just want to try an intuitive, secure email service that respects your privacy, get Proton Mail for free. All Proton plans include end-to-end encrypted Proton Mail, Proton Calendar, Proton Drive, and Proton VPN(new window). So join us, and stay secure!
